When creating self signed certificate, no prompts
-
@johnpoz Unfortunately simply renaming doesn't fly.
root/: /usr/local/etc/rc.d/mini_httpd.sh start
34381057080:error:0906D06C:PEM routines:PEM_read_bio:no start line:/builder/pfsense-234/tmp/FreeBSD-src/secure/lib/libcrypto/../../../crypto/openssl/crypto/pem/pem_lib.c:696:Expecting: ANY PRIVATE KEY
34381057080:error:140B0009:SSL routines:SSL_CTX_use_PrivateKey_file:PEM lib:/builder/pfsense-234/tmp/FreeBSD-src/secure/lib/libssl/../../../crypto/openssl/ssl/ssl_rsa.c:635: -
I do not run that... But what I can tell you is the file you export is PEM... simple enough to test it with openssl.
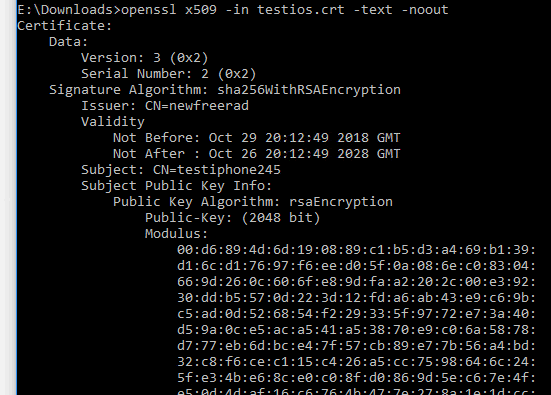
Here I just created a cert for another thread.. Tested it..
-
Combine the cert and key in one file:
-----BEGIN PRIVATE KEY----- keydatakeydatakeydatakeydatakeydatakeydatakeydatakeydata -----END PRIVATE KEY----- -----BEGIN CERTIFICATE----- certdatacertdatacertdatacertdatacertdatacertdatacertdatacertdata -----END CERTIFICATE-----At least that's what it looks like it's expecting.
Steve
-
@stephenw10 Thanks Steve, even tho freebsd “openssl verify ...” said the pem was bad that did the trick.
-
It's been a while since I tested this but co-incidentally did today and in fact every browser I tested is able to detect a captive portal redirect and trigger some alert to login without some huge error screen. It won't do that with a port forward lik you're doing here.
Kind of scary from a security view but makes it slick for end users.You would have to use it in some inverse way though. White-list all clients and remove those who need to see the redirect.
Steve
-
@markn6262 said in When creating self signed certificate, no prompts:
said the pem was bad that did the trick.
Then you got a bad copy or something in your download..
-
Maybe I wasn't clear enough in my last post. Combining the cert and key files into a pem file works with mini_httpd as stephen suggested. I'm golden! It's just that freebsd openssl verify reports the pem file as bad, oddly enough. I've never got a pem to report good creating from a freebsd comand line or from within PfSense GUI.
-
Report good from where... I just showed you checking a pem file that was downloaded from the gui.. I don't use whatever app your using... But sure they can be finicky... Trying to get plex to use different cert for its domain was a whole freaking learning curve in itself..
"Custom certificate encryption key"
Thought they wanted the path to the key - no they wanted the "password" you put on the p12 file that you combined the cert and key file in, etc..But have had zero issues using the CA manager and export certs and keys from it. I use the certs from there in multiple things. My switches, my unifi controller, my plex box, etc. etc. Certs for my windows machines for RDP, etc.. Its a great overall CA.. only thing is wish you could put passwords on your p12 when you export them..
-
@johnpoz I was wondering if I needed to use to p12. I didn't and it worked fine simply combining the CERT and KEY in a PEM file with the mini_httpd daemon. The PEM file PfSense creates reports bad from PfSense command prompt using "openssl verify fiiename.pem", try it. I'm not using some app to check PEM integrity. Until this thread, I had no idea the PfSense Cert Manager could make them for apps other than PfSense itself. That's good to know.
-
where is the rest of your command? the pems you create are going to be your private CA.. so no its not going to be able to just the verify command you would have to call out the CA..
So for example checking the freerad server pem, with the CA file..
openssl verify -CAfile ca_cert.pem server_cert.pem server_cert.pem: OK -
@johnpoz Google searches showed me the syntax I used. Apparently doesn't work for PfSense generated certs. The only cert files I find on the PfSense drive is for OpenVpn, nothing for Httpd. An OpenVpn folder has server2.ca .cert & .key. So I don't know how to translate your command to my situation. The only thing I know to try, as far as verification goes, is "openssl verify /etc/ssl/mini_httpd.pem" which reports;
/etc/ssl/mini_httpd.pem: CN = 127.0.0.1 CA
error 18 at 0 depth lookup:self signed certificate
OK -
All certs are stored in the XML... if you want to verify a cert, then you will also need to download the ca cert..
I used the files in the freerad dir because it couple other hot threads going on about it and certs an crls.
For openvpn.. the .ca is the ca.pem an serverX.cert is the server .pem
So for example
[2.4.4-RELEASE][root@sg4860.local.lan]/var/etc/openvpn: openssl verify -CAfile server1.ca server1.cert
server1.cert: OKNo offense but you might want to understand the tools your using a bit more before you say stuff doesn't work ;) pem file can have any ext on it does not have to be .pem ;)