[SOLVED] IPSEC VPN NAT - ADD NETWORK TO VPN
-
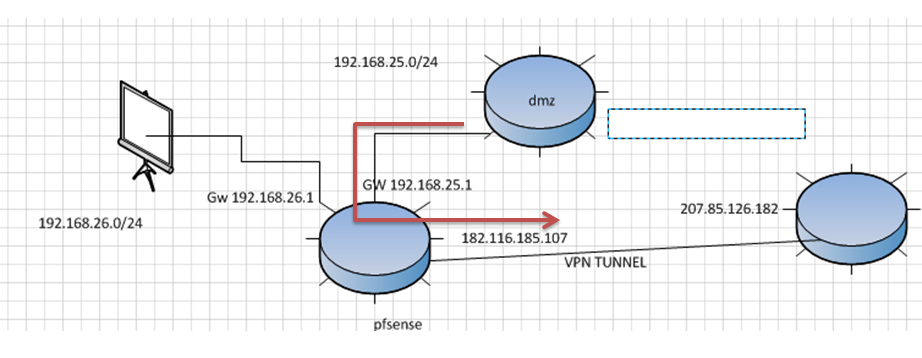
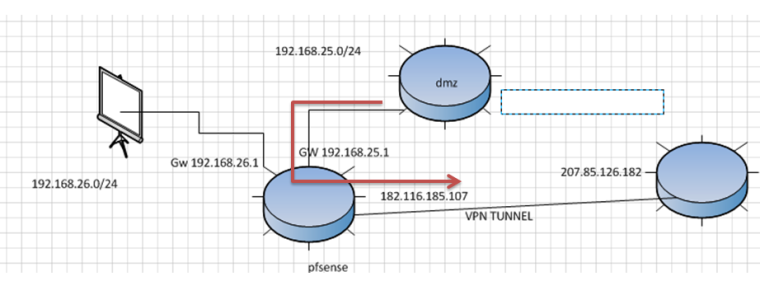
Hello, I have a network as seen in the graph, where it is at first only had the network 192.168.25.0 connects to my Pfsense and is one to a VPN Tunnel through IPSec to another network, the problem that I now have is I have another segment of red 192.168.26.0 and I also want this pass through the tunnel, but you can not because the VPN only negotiates with IPs of the red 192.168.25.0, how can I solve it?
Note: within the policies on the other side of the tunnel only one segment of the tunnel is included so it is not possible to add the red 192.168.26.0.
Can anybody help me?
-
Add another Phase 2 entry with the new networks. This has to be done on both sides.
-
@derelict do not add new network for politics the other side VPN
-
You are going to have to post exactly what you are trying to do then.
What networks are on each side and what needs to talk with what.
-
@derelict said the other side to TUNNEL is 192.168.1.0/24 network, need connect to devices to 192.168.26.0/24 internal network to TUNNEL but only accept devices to 192.168.25.0/24 configured into TUNNEL, noted the other side to TUNNEL only accept one network for politic to the company. do not add to other subnetwork
-
What?
What traffic selectors does the other side expect to see?
Local 192.168.1.0/24 <-> 192.168.25.0/24 Remote ???
What traffic selectors do you expect to see?
Local 192.168.26.0/24 <-> 192.168.1.0/24 Remote ???
Or both:
Local 192.168.25.0/24 <-> 192.168.1.0/24 Remote
Local 192.168.26.0/24 <-> 192.168.1.0/24 RemoteIf the former, it's easy. If the latter you can't do that without changes to the other side.
pfSense will not NAT a larger network to a smaller pool of addresses. You can BINAT 1:1 or NAT to a single address. Natting to a single address would also require they change their tunnel to that /32.
-
@derelict
Local 192.168.25.0/24 <-> 192.168.1.0/24 Remote
Local 192.168.26.0/24 <-> 192.168.1.0/24 Remote
expect traffic.
Local 192.168.25.0/24 <-> 192.168.1.0/24 Remote
is functionally
Local 192.168.26.0/24<->TO REPRESENTATIVE IP 192.168.25.0/24 <-> 192.168.1.0/24 Remote -
Phase 2:
Local Network: Network 192.168.26.0 /24
NAT: Network 192.168.25.0 /24
Remote Network: Network 192.168.1.0 /24And you're done.
Connections from, say, 192.168.26.191 to 192.168.1.0/24 will appear to them to come from 192.168.25.191
Connections from them to 192.168.25.195 will arrive on 192.168.26.195 on your side.
They should establish one traffic selector for traffic:
Local 192.168.1.0/24 <-> 192.168.25.0/24 Remote
-
Oh!!! Genius... Thank you... Problem solved.