Playing with fq_codel in 2.4
-
@rasool said in Playing with fq_codel in 2.4:
@uptownvagrant
Thank you for confirming that. So that means if CoDel+FQ_CoDel limiter is selected directly (not the child queue) in floating rules, the traffic will be controlled by CoDel algorithm.Yes, that would be my assumption too, but then I tested and the output is almost identical to DropTail. It appears that the AQM selection for the limiter is not being obeyed in pfSense. This does not appear to be a WebUI issue as the ipfw limiter.rules file looks to show the AQM and scheduler selected properly.
I can say, to avoid any possible problems when configuring fq_codel using current WebUI, the limiter child queue method should be used (with DropTail selected for both the limiter and child queue).
Yes, this is what I have found but again, it does not appear to be an issue with the WebUI. IMO, having the child queue is a functional requirement at this time and I'm not sure if it's related to the pf patch that pfSense is using to direct traffic to dummynet pipes and queues. Maybe kernel?
Now we have to figure out which part(s) causes performing issues. I think we have to compare the results (pps, CPU %utilisation, throughput) when using limiter with DropTail+FIFO (limiter only) and DropTail+FQ_CoDel (using child queue method).
We certainly can do that but there appears to be multiple issues with limiters and pfSense that we've identified in this thread and I'm wondering if the performance limitations may be a result. I've tested with FreeBSD and ipfw dummynet limiters and the performance issues did not surface.
-
Here are the two issues I think we've identified. If others can respond that they are able to reproduce the issues I will file bug reports for 2.4.4.
Issue 1:
Using limiters on an interface with outgoing NAT enabled causes all ICMP ping traffic to drop when the limiter is loaded with flows. I can reproduce this issue with the following configuration.- limiters created (any scheduler). One limiter for out and one limiter for in.
- create a single child queue for the out limiter and one for the in limiter.
- floating match IPv4 any rule on WAN Out using the out limiter child queue for in and in limiter child queue for out.
- floating match IPV4 any rule on WAN In using the in limiter child queue for in and out limiter child queue for out.
- load the limiter with traffic (most recently I've been using a netserver v2.6.0 on the WAN side and a Flent client on the LAN side running RRUL test)
- start a constant ping from the client to the server during the RRUL test
Both the flent.gz output and the constant ping will show a high rate of ICMP packets getting dropped. If NAT is disable you will not see ICMP drops.
Issue 2:
If a limiter pipe, not queue, is used in a floating match rule, FQ-CoDel will not be used even if selected and verified in /tmp/rules.limiter. I can reproduce this issue with the following configuration.- limiters created (FQ-CoDel scheduler with default settings). One 90Mbps limiter for out and one 90Mbps limiter for in.
- floating match IPv4 any rule on WAN Out using the out limiter for in and in limiter for out.
- floating match IPV4 any rule on WAN In using the in limiter for in and out limiter for out.
- using a netserver v2.6.0 on the WAN side and a Flent client on the LAN side, run the RRUL test on the client and inspect the output flent.gz. Server and client have GigE connectivity to pfSense.
You will notice that latency under load reflects a default 50 slot DropTail queue size and not what is expected from the default FQ-CoDel configuration. Adding a DropTail child queue to each limiter, updating the floating rules to use the queues instead of pipes, and rerunning the Flent RRUL test will show expected latency under load when FQ-CoDel with the default settings are in play.
-
@uptownvagrant said in Playing with fq_codel in 2.4:
Issue 1:
Using limiters on an interface with outgoing NAT enabled causes all ICMP ping traffic to drop when the limiter is loaded with flows.I can confirm this is happening. Using Rasool's steps outlined in post "@rasool said in Playing with fq_codel in 2.4"
I set a continuous ping going to 1.1.1.1, then start up speedtest.net and perform a speed test. All pings while the connection is being tested will time out. Disable the limiters and test again, ping doesn't drop packets.
-
@uptownvagrant said in Playing with fq_codel in 2.4:
Issue 1:
Using limiters on an interface with outgoing NAT enabled causes all ICMP ping traffic to drop when the limiter is loaded with flows. I can reproduce this issue with the following configuration.limiters created (any scheduler). One limiter for out and one limiter for in.
create a single child queue for the out limiter and one for the in limiter.
floating match IPv4 any rule on WAN Out using the out limiter child queue for in and in limiter child queue for out.
floating match IPV4 any rule on WAN In using the in limiter child queue for in and out limiter child queue for out.
load the limiter with traffic (most recently I've been using a netserver v2.6.0 on the WAN side and a Flent client on the LAN side running RRUL test)
start a constant ping from the client to the server during the RRUL testBoth the flent.gz output and the constant ping will show a high rate of ICMP packets getting dropped. If NAT is disable you will not see ICMP drops.
I can confirm to a certain extent this. Here's my ping trace:
Reply from 1.1.1.1: bytes=32 time=5ms TTL=58
Reply from 1.1.1.1: bytes=32 time=5ms TTL=58
Reply from 1.1.1.1: bytes=32 time=6ms TTL=58
Request timed out.
Request timed out.
Request timed out.
Reply from 1.1.1.1: bytes=32 time=5ms TTL=58
Request timed out.
Reply from 1.1.1.1: bytes=32 time=7ms TTL=58
Reply from 1.1.1.1: bytes=32 time=14ms TTL=58
Reply from 1.1.1.1: bytes=32 time=12ms TTL=58
Reply from 1.1.1.1: bytes=32 time=8ms TTL=58
Reply from 1.1.1.1: bytes=32 time=6ms TTL=58
Reply from 1.1.1.1: bytes=32 time=11ms TTL=58
Reply from 1.1.1.1: bytes=32 time=8ms TTL=58
Reply from 1.1.1.1: bytes=32 time=11ms TTL=58
Reply from 1.1.1.1: bytes=32 time=14ms TTL=58
Reply from 1.1.1.1: bytes=32 time=7ms TTL=58
Reply from 1.1.1.1: bytes=32 time=5ms TTL=58
Reply from 1.1.1.1: bytes=32 time=5ms TTL=58
Reply from 1.1.1.1: bytes=32 time=5ms TTL=58The first 3 replies are prior to Speedtest. The next 3 timeout replies are whilst Speedtest is testing the Download, and the 1 ping is whilst it finishes and recovers. However, the next 1 timeout ping is whilst it starts the Upload test, but the next 9 pings are whilst it's still within the Upload test, and the final few are once finished.
i.e. it appears to swamp the NAT interface on Download testing but not on Upload testing. -
I've managed to get around the dropped pings problem by creating a floating rule with:
MATCH on WAN, any direction, ICMP (any subtypes), default gateway and no In/Out Pipes.
Then having it as the very first rule in floating.It doesnt fix the cause of the issue, but should at least allow pings to get through normally.
-
Another workaround to the ping issue, I have posted twice now, is to not create a floating rule at all. Instead apply the queue to the the default LAN rule out to the internet.
-
@askmyteapot Yes! IMHO this is the best workaround option for ICMP and limiters at the moment. One note though is that if you place the rule first you will want to check the quick option in the rule. Otherwise, place the ICMP match rule under your In/Out pipe rules - floating rules are last match wins when quick is not checked.
-
@uptownvagrant FYI, I first came to this thread with a similar issue that wasn't just ICMP related. I lost VoIP and Sonos audio streams on our office pFsense...
https://www.reddit.com/r/PFSENSE/comments/9kfo4k/codelq_setup/ -
@pentangle OK. So are you saying VoIP and Sonos don't work when you apply FQ-CoDel limiters on WAN but they do work when you apply the same limiters to LAN? When don't they work - when the limiter is filled with traffic or? The ping issue comes down to pfSense dropping echo replies coming back into WAN/NAT when the limiter is full. What's going on with your traffic?
-
@uptownvagrant Sorry I wasn't clear. I'm saying that it's not just ICMP traffic that gets dropped with a speedtest and floating rules on pFsense. I was seeing both streaming Sonos traffic and VoIP call RTP dropping at the same time as the ICMP dropped.
i.e. I think the bug issue for pFsense is a little more than just ICMP, but it might be ALL traffic that's affected when you get to a saturation with floating rules? -
udp is being dropped also. Unless this is yet another badmodems.com bug?
-
Perhaps a packet size rather than protocol issue
-
I have an APU2C4 and 150/150 FiOS. It looks like I hit about 30 - 40% CPU usage when several clients are downloading from steam using the fq_codel limiter setup mentioned earlier in the thread. I was looking at top and it appears like the load gets spread across all 4 cores of my processor.
Will this always be the case or could the limiters actually cause me to become CPU bound on one core in certain instances? I am moving to 200/200 speed soon. The APU2 runs at 1GHz. I was considering moving to a Celeron J3455 @ 2.3GHz but only if it was needed to handle running fq_codel.
I appreciate any feedback.
-
@rasool said in Playing with fq_codel in 2.4:
@strangegopher Excellent work!
I installed pfSense and was able to setup fq_codel correctly (without CoDel) using just the WebUI. Here are the steps:1- Create "out" limiter
- Tick Enable
- Name: pipe_out
- Set the bandwidth
- Queue Management Algorithm: Tail Drop
- Scheduler: FQ_CODEL
2- Add new Queue
- Tick "Enable"
- Name: queue_out
- Queue Management Algorithm: Tail Drop
- Save
3- Create "in" limiter
- Tick Enable
- Name: pipe_in
- Set the bandwidth
- Queue Management Algorithm: Tail Drop
- Scheduler: FQ_CODEL
4- Add new Queue
- Tick "Enable"
- Name: queue_in
- Queue Management Algorithm: Tail Drop
- Save
5- Add limiter in firewall rule
- Configure floating rule (as normal)
- In / Out pipe: queue_in / queue_out
I believe these steps prevent "config_aqm Unable to configure flowset, flowset busy!" error and no need for rebooting pfSense.
Could you please test the above setup?
what's the normal way to configure floating rule? can I have more detail about it? like what direction and interface ? also Quick option should be tick ?
-
@knowbe4
I meant by "as normal" as per the youtube video https://youtu.be/o8nL81DzTlU?t=801. Btw, I am not a pfSense expert. I learned how to use the basic features just to help in this forum ;) -
@rasool Thank you very much, I really appreciate it. Keep up the good work


-
@pentangle I can't recreate your results with VoIP. I'm using a cloud provider for VoIP and signaling uses (UDP/5060), RTP (media) uses (UDP/10,000-30,000). DTMF Mode RFC 2833 Payload type 101 and G.711 a-law. I can run an rrul test across pfSense, placing all traffic, except for ICMP, in the 90Mbit in/out FQ-CoDel limiter queues and I place a call during the test. Call quality remains excellent during a 5 minute rrul test.
Did you see any "fq_codel_enqueue over limit" messages in syslog during the speedtest where VoIP and Sonos was cutting out?
Are your using the FQ-CoDel defaults of?
target: 5
interval: 100
quantum: 1514
limit: 10240
flows: 1024 -
@uptownvagrant do you mind sharing your current fq_codel setup ?
-
This is for a very heavily utilized 100/100 Mbps circuit. Hardware is C2758, 8 GB RAM, igb interfaces (Intel I354).
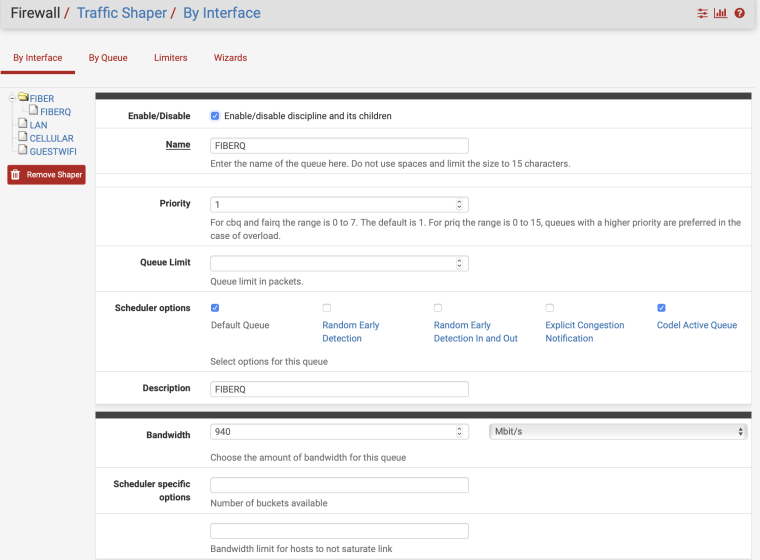
In my testing I may move limiters to other interfaces without recreating them and renaming them. In my examples IN=ingress and OUT=egress. From the perspective of the WAN port, IN is traffic coming into the interface from the Internet and OUT is traffic leaving the interface to the Internet.
Create Limiters:
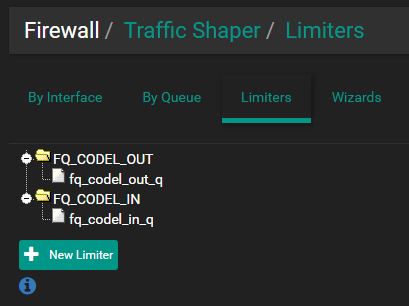
1.) Create "Out" limiter
- Tick "Enable"
- Name: FQ_CODEL_OUT
- Bandwidth: 96907 Kbit/s
- Mask: None
- Queue Management Algorithm: Tail Drop
- Scheduler: FQ_CODEL
- target: 5
- interval: 100
- quantum: 300
- limit: 10240
- flows: 20480
- Click Save/Apply Changes
2.) Add "Out" queue
- Tick "Enable"
- Name: fq_codel_out_q
- Mask: None
- Queue Management Algorithm: Tail Drop
- Click Save/Apply Changes
3.) Create "In" limiter
- Tick "Enable"
- Name: FQ_CODEL_IN
- Bandwidth: 83886 Kbit/s
- Mask: None
- Queue Management Algorithm: Tail Drop
- Scheduler: FQ_CODEL
- target: 5
- interval: 100
- quantum: 300
- limit: 10240
- flows: 20480
- Click Save/Apply Changes
4.) Add "In" queue
- Tick "Enable"
- Name: fq_codel_in_q
- Mask: None
- Queue Management Algorithm: Tail Drop
- Click Save/Apply Changes
Floating Rules:
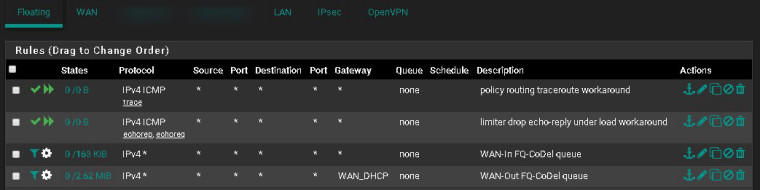
1.) Add quick pass floating rule to handle ICMP traceroute. This rule matches ICMP traceroute packets so that they are not matched by the WAN-Out limiter rule that utilizes policy routing. Policy routing breaks traceroute.
- Action: Pass
- Quick: Tick Apply the action immediately on match.
- Interface: WAN
- Direction: out
- Address Family: IPv4
- Protocol: ICMP
- ICMP subtypes: Traceroute
- Source: any
- Destination: any
- Description: policy routing traceroute workaround
- Click Save
2.) Add quick pass floating rule to handle ICMP echo-request and echo-reply. This rule matches ping packets so that they are not matched by the limiter rules. See bug 9024 for more info.
- Action: Pass
- Quick: Tick Apply the action immediately on match.
- Interface: WAN
- Direction: any
- Address Family: IPv4
- Protocol: ICMP
- ICMP subtypes: Echo reply, Echo Request
- Source: any
- Destination: any
- Description: limiter drop echo-reply under load workaround
- Click Save
3.) Add a match rule for incoming state flows so that they're placed into the FQ-CoDel in/out queues
- Action: Match
- Interface: WAN
- Direction: in
- Address Family: IPv4
- Protocol: Any
- Source: any
- Destination: any
- Description: WAN-In FQ-CoDel queue
- Gateway: Default
- In / Out pipe: fq_codel_in_q / fq_codel_out_q
- Click Save
4.) Add a match rule for outgoing state flows so that they're placed into the FQ-CoDel out/in queues
- Action: Match
- Interface: WAN
- Direction: out
- Address Family: IPv4
- Protocol: Any
- Source: any
- Destination: any
- Description: WAN-Out FQ-CoDel queue
- Gateway: WAN_DHCP
- In / Out pipe: fq_codel_out_q / fq_codel_in_q
- Click Save/Apply Changes
Update 2018/01/04: After additional research and testing, I have made changes to FQ-CoDel quantum, limit, and flows in my environment where a 500 Mbps symmetric circuit is in use. I have also made changes to state timeouts on a firewall that consistently averages over 55k filter states.
- Quantum - setting this to 300 will give some priority to smaller packet flows like VoIP. As a reference, a quantum of 300 is used in the OpenWRT sqm scripts and is noted on bufferbloat.net and the mailing list as a good option. Note: Setting quantum below 300 is not advised.
- Limit - if your system is not severely memory constrained, setting this to 20480 packets, which is the max, will further protect against the "fq_codel_enqueue over limit" error. Depending on the flows, in my testing this error typically fires right before pfSense starts to drop many packets and in some instances causes pfSense to become unstable and/or reboot. Note: Setting this over-large packet limit can lead to bad results during slow starts for certain flows.
- Flows - if your system is not severely memory constrained, setting this to 65535 will allow very good flow separation up to 65535 flows. The default 1024 is pretty low for a network with more than a few clients doing anything other than basic web browsing. Note: while the ipfw man page does specify that the maximum acceptable value is 65536, you will find that if you use this max value the firewall will enter a boot loop and you will have to restore a previous configuration. Also, I'm still testing and observing but it appears that on my hardware, each 10240 increase in flows equals about 1ms of added latency under load.
- State Timeouts - under System / Advanced / Firewall & NAT, I set 'Firewall Optimization Options' to Aggressive and 'TCP Established' to 86400.
-
I have a gigabit link on my SG-3100. This is what I'm using and get all A+ on DSLReports. No rules, just the shaper on my main WAN connection.