Suricata/Snort master SID disablesid.conf
-
I appreciate the tips, but with a new pfSense and Snort installation, I think I'm still missing something fundamental here: Why are we adding rules like 119:2 — rules marked "not-suspicious" — to the suppression list at all?
Unless I'm completely misunderstanding something, this and similar rules are inserted by one of the preprocessors, and have already been annotated as rules that don't on their own imply suspicious traffic when triggered, so why is Snort adding firewall rules when they're triggered? Is there no option to simply have Snort not add firewall rules when traffic triggers a rule marked "not-suspicious"?
I ask, because after a couple weeks of running Snort with the default "connectivity" IPS rule set as well as some of the more targeted ET rulesets, the only problems I've had are with rules marked "not-suspicious" or "unknown". It seems like an unnecessary hassle to manually add these rules to a suppression list when they're already marked as something that doesn't directly imply problematic traffic.
I had some time during the Christmas break and upgraded from 2.3.2 to 2.4.2-RELEASE-p1 and experienced this same problem. At first it seemed like non-HTTPS sites were affected so I thought it might be a Squid cache issue but then I found I was able to load many other HTTP sites. It was tough to identify as Snort seemed to continue running for quite a while after being stopped, but it was obvious when I finally looked at the alerts page. I tried re-installing snort and was unable to get the disablesid list to function. I also tried redoing this setting and was unsuccessful there as well. I've added my list to the suppress list for the time being and will leave it there unless I notice performance issues.
-
I did some awk/sed scripting and added descriptions for most of the disabled SIDs in Asterix' master list above.
Attached here in case anyone else finds it useful. The SIDs without descriptions were not present in the latest VRT and ET rulesets I have.
# disabled SIDs, https://forum.pfsense.org/index.php?topic=56267.75 1:536 # "DELETED NETBIOS SMB D$ share access" 1:648 # "INDICATOR-SHELLCODE x86 NOOP" 1:653 # "DELETED SHELLCODE x86 0x90 unicode NOOP" 1:1390 # "INDICATOR-SHELLCODE x86 inc ebx NOOP" 1:2452 # "POLICY-SOCIAL Yahoo IM ping" 1:8375 # "BROWSER-PLUGINS QuickTime Object ActiveX clsid access" 1:11192 # "FILE-EXECUTABLE download of executable content" 1:12286 # "FILE-OTHER PCRE character class heap buffer overflow attempt" 1:15147 # "BROWSER-IE Microsoft Internet Explorer malformed iframe buffer overflow attempt" 1:15306 # "FILE-EXECUTABLE Portable Executable binary file magic detected" 1:15362 # "INDICATOR-OBFUSCATION obfuscated javascript excessive fromCharCode - potential attack" 1:16313 # "FILE-EXECUTABLE download of executable content" 1:16482 # "BROWSER-IE Microsoft Internet Explorer userdata behavior memory corruption attempt" 1:17458 # "FILE-OTHER BitDefender Internet Security script code execution attempt" 1:20583 # "BROWSER-FIREFOX Mozilla multiple location headers malicious redirect attempt" 1:23098 # "FILE-MULTIMEDIA Adobe Flash Player MP4 sequence parameter set parsing overflow attempt" 1:23256 # "FILE-EXECUTABLE Armadillo v1.71 packer file magic detected" 1:24889 # "FILE-FLASH Adobe Flash Player Action InitArray stack overflow attempt" 1:2000334 # "ET P2P BitTorrent peer sync" 1:2000418 # "ET POLICY Executable and linking format (ELF) file download" 1:2000419 # "ET POLICY PE EXE or DLL Windows file download" 1:2002878 # "ET POLICY iTunes User Agent" 1:2003195 # "ET POLICY Unusual number of DNS No Such Name Responses" 1:2007727 # "ET P2P possible torrent download" 1:2008120 # "ET TFTP Outbound TFTP Read Request" 1:2008578 # "ET SCAN Sipvicious Scan" 1:2008989 # "ET POLICY Internal Host Retrieving External IP via showmyip.com - Possible Infection" 1:2010516 # "ET WEB_CLIENT Possible HTTP 403 XSS Attempt (External Source)" 1:2010525 # "ET WEB_CLIENT Possible HTTP 500 XSS Attempt (External Source)" 1:2010935 # "ET POLICY Suspicious inbound to MSSQL port 1433" 1:2010937 # "ET POLICY Suspicious inbound to mySQL port 3306" 1:2011716 # "ET SCAN Sipvicious User-Agent Detected (friendly-scanner)" 1:2012078 # "ET POLICY Windows-Based OpenSSL Tunnel Outbound" 1:2012086 # "ET DELETED Possible Call with No Offset TCP Shellcode" 1:2012087 # "ET SHELLCODE Possible Call with No Offset UDP Shellcode" 1:2012088 # "ET SHELLCODE Possible Call with No Offset TCP Shellcode" 1:2012089 # "ET SHELLCODE Possible Call with No Offset UDP Shellcode" 1:2012141 # "ET POLICY Protocol 41 IPv6 encapsulation potential 6in4 IPv6 tunnel active" 1:2012252 # "ET SHELLCODE Common 0a0a0a0a Heap Spray String" 1:2012758 # "ET INFO DYNAMIC_DNS Query to *.dyndns. Domain" 1:2013028 # "ET POLICY curl User-Agent Outbound" 1:2013031 # "ET POLICY Python-urllib/ Suspicious User Agent" 1:2013222 # "ET DELETED Excessive Use of HeapLib Objects Likely Malicious Heap Spray Attempt" 1:2013414 # "ET POLICY Executable served from Amazon S3" 1:2013504 # "ET POLICY GNU/Linux APT User-Agent Outbound likely related to package management" 1:2014472 # "ET INFO JAVA - Java Archive Download" 1:2014518 # "ET INFO EXE - OSX Disk Image Download" 1:2014520 # "ET INFO EXE - Served Attached HTTP" 1:2014726 # "ET POLICY Outdated Flash Version M1" 1:2014734 # "ET P2P BitTorrent - Torrent File Downloaded" 1:2014819 # "ET INFO Packed Executable Download" 1:2015561 # "ET INFO PDF Using CCITTFax Filter" 1:2015744 # "ET INFO EXE IsDebuggerPresent (Used in Malware Anti-Debugging)" 1:2015820 # "ET INFO Suspicious Windows NT version 7 User-Agent" 1:2016360 # "ET INFO JAVA - ClassID" 1:2016877 # "ET POLICY Unsupported/Fake FireFox Version 2." 1:2017364 # "ET INFO SUSPCIOUS Non-standard base64 charset used for encoding" 1:2018959 # "ET POLICY PE EXE or DLL Windows file download HTTP" 1:2019416 # "ET POLICY SSLv3 outbound connection from client vulnerable to POODLE attack" 1:2022913 # "ET INFO WinHttp AutoProxy Request wpad.dat Possible BadTunnel" 1:2100366 # 1:2100368 # 1:2100651 # 1:2101390 # 1:2101424 # 1:2102314 # 1:2103134 # 1:2103192 # 1:2200075 # 1:2210000 # 1:2210007 # 1:2210020 # 1:2210036 # 1:2210042 # 1:2210044 # 1:2210045 # 1:2210050 # 1:2210054 # 1:2221028 # 1:2230010 # 1:2402000 # "ET DROP Dshield Block Listed Source group 1" 1:2403323 # "ET CINS Active Threat Intelligence Poor Reputation IP UDP group 12" 1:2403344 # "ET CINS Active Threat Intelligence Poor Reputation IP TCP group 23" 1:2406003 # 1:2406067 # 1:2406069 # 1:2406424 # 1:2500050 # "ET COMPROMISED Known Compromised or Hostile Host Traffic TCP group 26" 1:2500056 # "ET COMPROMISED Known Compromised or Hostile Host Traffic TCP group 29" 1:2520199 # 1:2520205 # 1:2522614 # "ET TOR Known Tor Relay/Router (Not Exit) Node TCP Traffic group 308" 1:2522618 # "ET TOR Known Tor Relay/Router (Not Exit) Node TCP Traffic group 310" 1:100000230 # 3:14772 # "FILE-IMAGE libpng malformed chunk denial of service attempt" 3:19187 # "PROTOCOL-DNS TMG Firewall Client long host entry exploit attempt" 3:21355 # "PROTOCOL-DNS potential dns cache poisoning attempt - mismatched txid" 119:2 # "HI_CLIENT_DOUBLE_DECODE" 119:4 # "HI_CLIENT_BARE_BYTE" 119:7 # "HI_CLIENT_IIS_UNICODE" 119:14 # "HI_CLIENT_NON_RFC_CHAR" 119:31 # "HI_CLIENT_UNKNOWN_METHOD" 119:32 # "HI_CLIENT_SIMPLE_REQUEST" 119:33 # "HI_CLIENT_UNESCAPED_SPACE_IN_URI" 120:2 # "HI_SERVER_INVALID_STATCODE" 120:3 # "HI_SERVER_NO_CONTLEN" 120:4 # "HI_SERVER_UTF_NORM_FAIL" 120:6 # "HI_SERVER_DECOMPR_FAILED" 120:8 # "HI_CLISRV_MSG_SIZE_EXCEPTION" 120:9 # "HI_SERVER_JS_OBFUSCATION_EXCD" 120:10 # "HI_SERVER_JS_EXCESS_WS" 122:19 # "PSNG_UDP_PORTSWEEP" 122:21 # "PSNG_UDP_FILTERED_PORTSCAN" 122:22 # "PSNG_UDP_FILTERED_DECOY_PORTSCAN" 122:23 # "PSNG_UDP_PORTSWEEP_FILTERED" 122:26 # "PSNG_ICMP_PORTSWEEP_FILTERED" 123:10 # "FRAG3_IPV6_BAD_FRAG_PKT" 124:3 # "SMTP_RESPONSE_OVERFLOW" 125:2 # "FTPP_FTP_INVALID_CMD" 137:1 # "SSL_INVALID_CLIENT_HELLO" 138:2 # "SENSITIVE-DATA Credit Card Numbers" 138:3 # "SENSITIVE-DATA U.S. Social Security Numbers (with dashes)" 138:4 # "SENSITIVE-DATA U.S. Social Security Numbers (w/out dashes)" 138:5 # "SENSITIVE-DATA Email Addresses" 138:6 # "SENSITIVE-DATA U.S. Phone Numbers" 141:1 # "IMAP_UNKNOWN_CMD" #END disabled SIDs from PFSense Forum -
Here are some new additions in Suricata. They are still in my suppress list as I give them at least 3 months before considering them to be permanently disabled. Most of these blocked my smartTV from reaching the internet.
#ET SCAN Sipvicious User-Agent Detected (friendly-scanner)
suppress gen_id 1, sig_id 2011716#ET SCAN Sipvicious Scan
suppress gen_id 1, sig_id 2008578#ET DROP Dshield Block Listed Source group 1
suppress gen_id 1, sig_id 2402000#ET CINS Active Threat Intelligence Poor Reputation IP group 65
suppress gen_id 1, sig_id 2403364#ET CINS Active Threat Intelligence Poor Reputation IP group 3
suppress gen_id 1, sig_id 2403302#ET CINS Active Threat Intelligence Poor Reputation IP group 82
suppress gen_id 1, sig_id 2403381 -
Another addition to the list. I noticed that APT is whitelisted, but not YUM:
1:2013505 # "ET POLICY GNU/Linux YUM User-Agent Outbound likely related to package management" -
Since the past few months I have been re-evaluating my Suricata disabled.conf list. I found a lot of deprecated and old sig ids which were no longer relevant. I found the best course of action to rectify this was to start from scratch. First I started with IPS Policy and used the most light version of “connectivity” and then after careful evaluation first suppressed and then started disabling the false positives. Tested for 3 weeks then I moved to “balanced” policy to repeat the same process, then “security”, then “maximum” and finally fully loaded all rules. I have the below new list which is working 99.5% of the time with no issues. I do get an odd ball here and there once or twice a week but for this is a perfect daily driver.
I now have all the below rules disabled automatically on Suricata startup using SID Mgmt.
1:2010645
1:2012141
1:2013031
1:2012810
1:2015820
1:2016149
1:2016150
1:2016777
1:2016778
1:2016879
1:2018959
1:2023883
1:2025104
1:2025107
1:2025275
1:2200024
1:2200036
1:2200078
1:2200094
1:2210016
1:2210039
1:2210042
1:2210044
1:2210050
1:2210054
1:2210055
1:2221010
1:2221028
1:2221033
1:2230010
1:2230015
1:2522456
1:2522462
1:2522464
1:2522468
1:2522470
1:2522472
1:2522476
1:2522478
1:2522482
1:25522480 -
@asterix is that applicable to snort ?
-
It should work but I haven’t done intensive tests with Snort in ages.
-
What rulesets do you have enabled on Suricata , Asterix?
-
@chigh09 read my post above you will have your answer with detailed explanation :-)
-
@asterix I have started my pfsense suricata journey, and I have started to use your SID list. Have you updated this list with any new finds from your use? Thanks again for posting this list.
-
@themadsalvi said in Suricata/Snort master SID disablesid.conf:
@asterix I have started my pfsense suricata journey, and I have started to use your SID list. Have you updated this list with any new finds from your use? Thanks again for posting this list.
Are you using IPS mode? If so, I advise against using any of the lists above. Even using Legacy mode I would want to keep many of those rules enabled. One example:
1:2402000 - This rule alone is responsible for blocking 75%+ of attacks on a daily basis. Here's the top 10 alerts over a recent 24 hour period:
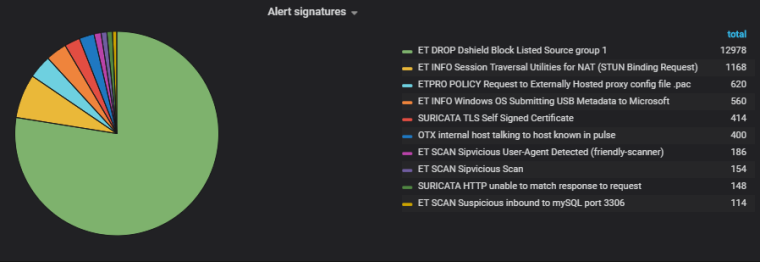
If you're simply alerting and not blocking with IPS/Legacy then you may not want to see all 13,000 of those attacks. But blocking? You definitely want the Dshield rules in place (even if you're already using pfBlocker). The same goes for all of the CINS/compromised host rules.
There are tons of rules in the lists above that will protect you. If you don't want to block traffic and prefer just to see alerts, then I would still want a huge number of those rules. Some more examples:
1:2013031 # "ET POLICY Python-urllib/ Suspicious User Agent" --
I want to know if the urllib or requests python libraries are being used with generic User-Agents because that likely means I'm not making the request. If you're running something that does use the generic UAs, then you could either change that User-Agent to something else or write a pass rule specifically for that traffic.1:2017364 # "ET INFO SUSPCIOUS Non-standard base64 charset used for encoding" --
This is traffic I would definitely want to investigate.Were I you, rather than suppressing or disabling SIDs, I would write pass rules, use the modify SID options, or generally find a way to keep most of those alerts in place without the spam.
-
@boobletins I just took a look at the numbers that you mentioned above, and it appears as though the most recent list also has the 1:2402000, and 1:2017364 SIDs removed from it. This sets me more at ease, as the way that you explain it, Intrusion detection systems would be less effective with them disabled. I will take a look at getting the 1:2013031 re-enabled. I have taken a look at my logs, and have been fortunate to not get any blocks from that when I previously used Snort. I am primarily a home user, who is paranoid enough to want and IDS/IPS system in place for my network. Thank you for the help.
-
@asterix Hi man, if you can do full update then i am thankful. (and create new post then link to where you help pp with Suricata/Snort SID disableid.conf, so that will be the best and easy for someone new like me.)
Last upadated @25/MAR/2019 by asterix (please give us full from "begin" to "the end" of disableid.conf)
1:536
1:648
1:653
1:1390
..
..
..
1:25522480NOT LIKE THIS...
asterix Aug 19, 2017, 4:24 AM
Here is my current/updated list from disablesid.conf. I switched to suricata last year so your experience with these in snort may vary.
...then: asterix Jan 3, 2018, 6:48 AM
Here are some new additions in Suricata. They are still in my suppress list as I give them at least 3 months before considering them to be permanently disabled. Most of these blocked my smartTV from reaching the internet.
...asterix Aug 15, 2018, 12:03 AM
I now have all the below rules disabled automatically on Suricata startup using SID Mgmt.
1:2010645
1:2012141
1:2013031
1:2012810
1:2015820
1:2016149
1:2016150
1:2016777
1:2016778
1:2016879
1:2018959
1:2023883
1:2025104
1:2025107
1:2025275
1:2200024
1:2200036
1:2200078
1:2200094
1:2210016
1:2210039
1:2210042
1:2210044
1:2210050
1:2210054
1:2210055
1:2221010
1:2221028
1:2221033
1:2230010
1:2230015
1:2522456
1:2522462
1:2522464
1:2522468
1:2522470
1:2522472
1:2522476
1:2522478
1:2522482
1:25522480You can do that but at the end please give us some link to go to the full disableid.conf.
Many, many, THANKS. and if you have more full guide (how to configs snort/suricata from begin. please add on as well. Wow, it will be perfect) -
@danielt said in Suricata/Snort master SID disablesid.conf:
disableid.conf
You have to create a disableid.conf file and add the above list to it. There is no direct link to a file as it has to be created locally on pfSense. Once created select the file in the "Interface SID Management List Assignments" under "Disable SID List" dropdown.
-
@danielt said in Suricata/Snort master SID disablesid.conf:
@asterix Hi man, if you can do full update then i am thankful. (and create new post then link to where you help pp with Suricata/Snort SID disableid.conf, so that will be the best and easy for someone new like me.)
Last upadated @25/MAR/2019 by asterix (please give us full from "begin" to "the end" of disableid.conf)
1:536
1:648
1:653
1:1390
..
..
..
1:25522480NOT LIKE THIS...
asterix Aug 19, 2017, 4:24 AM
Here is my current/updated list from disablesid.conf. I switched to suricata last year so your experience with these in snort may vary.
...then: asterix Jan 3, 2018, 6:48 AM
Here are some new additions in Suricata. They are still in my suppress list as I give them at least 3 months before considering them to be permanently disabled. Most of these blocked my smartTV from reaching the internet.
...asterix Aug 15, 2018, 12:03 AM
I now have all the below rules disabled automatically on Suricata startup using SID Mgmt.
1:2010645
1:2012141
1:2013031
1:2012810
1:2015820
1:2016149
1:2016150
1:2016777
1:2016778
1:2016879
1:2018959
1:2023883
1:2025104
1:2025107
1:2025275
1:2200024
1:2200036
1:2200078
1:2200094
1:2210016
1:2210039
1:2210042
1:2210044
1:2210050
1:2210054
1:2210055
1:2221010
1:2221028
1:2221033
1:2230010
1:2230015
1:2522456
1:2522462
1:2522464
1:2522468
1:2522470
1:2522472
1:2522476
1:2522478
1:2522482
1:25522480You can do that but at the end please give us some link to go to the full disableid.conf.
Many, many, THANKS. and if you have more full guide (how to configs snort/suricata from begin. please add on as well. Wow, it will be perfect)You can copy the contents of any file (so long as it is plain text) onto the clipboard and then either paste that into the text box on the SID MGMT tab's Edit List dialog, or you can save the file on your PC and use the Import/Upload feature to upload a list to the box.
-
@asterix
Could you share for us your last disablesid.conf ? maybe you have some NEWS. and that can use for snort and suricata ? or only suricata? Do you have any new post of config suricata for WAN and snort for LAN? Thanks for your help.Best Regards,
Daniel T