Suricata/Snort master SID disablesid.conf
-
Since the past few months I have been re-evaluating my Suricata disabled.conf list. I found a lot of deprecated and old sig ids which were no longer relevant. I found the best course of action to rectify this was to start from scratch. First I started with IPS Policy and used the most light version of “connectivity” and then after careful evaluation first suppressed and then started disabling the false positives. Tested for 3 weeks then I moved to “balanced” policy to repeat the same process, then “security”, then “maximum” and finally fully loaded all rules. I have the below new list which is working 99.5% of the time with no issues. I do get an odd ball here and there once or twice a week but for this is a perfect daily driver.
I now have all the below rules disabled automatically on Suricata startup using SID Mgmt.
1:2010645
1:2012141
1:2013031
1:2012810
1:2015820
1:2016149
1:2016150
1:2016777
1:2016778
1:2016879
1:2018959
1:2023883
1:2025104
1:2025107
1:2025275
1:2200024
1:2200036
1:2200078
1:2200094
1:2210016
1:2210039
1:2210042
1:2210044
1:2210050
1:2210054
1:2210055
1:2221010
1:2221028
1:2221033
1:2230010
1:2230015
1:2522456
1:2522462
1:2522464
1:2522468
1:2522470
1:2522472
1:2522476
1:2522478
1:2522482
1:25522480 -
@asterix is that applicable to snort ?
-
It should work but I haven’t done intensive tests with Snort in ages.
-
What rulesets do you have enabled on Suricata , Asterix?
-
@chigh09 read my post above you will have your answer with detailed explanation :-)
-
@asterix I have started my pfsense suricata journey, and I have started to use your SID list. Have you updated this list with any new finds from your use? Thanks again for posting this list.
-
@themadsalvi said in Suricata/Snort master SID disablesid.conf:
@asterix I have started my pfsense suricata journey, and I have started to use your SID list. Have you updated this list with any new finds from your use? Thanks again for posting this list.
Are you using IPS mode? If so, I advise against using any of the lists above. Even using Legacy mode I would want to keep many of those rules enabled. One example:
1:2402000 - This rule alone is responsible for blocking 75%+ of attacks on a daily basis. Here's the top 10 alerts over a recent 24 hour period:
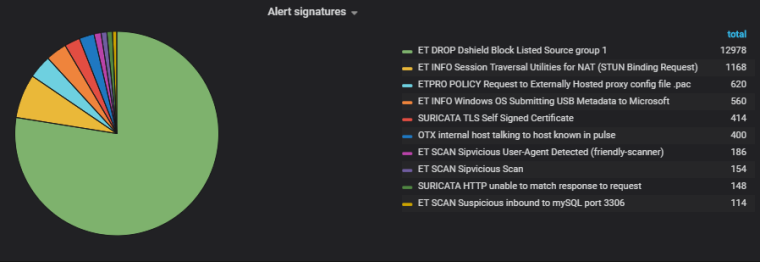
If you're simply alerting and not blocking with IPS/Legacy then you may not want to see all 13,000 of those attacks. But blocking? You definitely want the Dshield rules in place (even if you're already using pfBlocker). The same goes for all of the CINS/compromised host rules.
There are tons of rules in the lists above that will protect you. If you don't want to block traffic and prefer just to see alerts, then I would still want a huge number of those rules. Some more examples:
1:2013031 # "ET POLICY Python-urllib/ Suspicious User Agent" --
I want to know if the urllib or requests python libraries are being used with generic User-Agents because that likely means I'm not making the request. If you're running something that does use the generic UAs, then you could either change that User-Agent to something else or write a pass rule specifically for that traffic.1:2017364 # "ET INFO SUSPCIOUS Non-standard base64 charset used for encoding" --
This is traffic I would definitely want to investigate.Were I you, rather than suppressing or disabling SIDs, I would write pass rules, use the modify SID options, or generally find a way to keep most of those alerts in place without the spam.
-
@boobletins I just took a look at the numbers that you mentioned above, and it appears as though the most recent list also has the 1:2402000, and 1:2017364 SIDs removed from it. This sets me more at ease, as the way that you explain it, Intrusion detection systems would be less effective with them disabled. I will take a look at getting the 1:2013031 re-enabled. I have taken a look at my logs, and have been fortunate to not get any blocks from that when I previously used Snort. I am primarily a home user, who is paranoid enough to want and IDS/IPS system in place for my network. Thank you for the help.
-
@asterix Hi man, if you can do full update then i am thankful. (and create new post then link to where you help pp with Suricata/Snort SID disableid.conf, so that will be the best and easy for someone new like me.)
Last upadated @25/MAR/2019 by asterix (please give us full from "begin" to "the end" of disableid.conf)
1:536
1:648
1:653
1:1390
..
..
..
1:25522480NOT LIKE THIS...
asterix Aug 19, 2017, 4:24 AM
Here is my current/updated list from disablesid.conf. I switched to suricata last year so your experience with these in snort may vary.
...then: asterix Jan 3, 2018, 6:48 AM
Here are some new additions in Suricata. They are still in my suppress list as I give them at least 3 months before considering them to be permanently disabled. Most of these blocked my smartTV from reaching the internet.
...asterix Aug 15, 2018, 12:03 AM
I now have all the below rules disabled automatically on Suricata startup using SID Mgmt.
1:2010645
1:2012141
1:2013031
1:2012810
1:2015820
1:2016149
1:2016150
1:2016777
1:2016778
1:2016879
1:2018959
1:2023883
1:2025104
1:2025107
1:2025275
1:2200024
1:2200036
1:2200078
1:2200094
1:2210016
1:2210039
1:2210042
1:2210044
1:2210050
1:2210054
1:2210055
1:2221010
1:2221028
1:2221033
1:2230010
1:2230015
1:2522456
1:2522462
1:2522464
1:2522468
1:2522470
1:2522472
1:2522476
1:2522478
1:2522482
1:25522480You can do that but at the end please give us some link to go to the full disableid.conf.
Many, many, THANKS. and if you have more full guide (how to configs snort/suricata from begin. please add on as well. Wow, it will be perfect) -
@danielt said in Suricata/Snort master SID disablesid.conf:
disableid.conf
You have to create a disableid.conf file and add the above list to it. There is no direct link to a file as it has to be created locally on pfSense. Once created select the file in the "Interface SID Management List Assignments" under "Disable SID List" dropdown.
-
@danielt said in Suricata/Snort master SID disablesid.conf:
@asterix Hi man, if you can do full update then i am thankful. (and create new post then link to where you help pp with Suricata/Snort SID disableid.conf, so that will be the best and easy for someone new like me.)
Last upadated @25/MAR/2019 by asterix (please give us full from "begin" to "the end" of disableid.conf)
1:536
1:648
1:653
1:1390
..
..
..
1:25522480NOT LIKE THIS...
asterix Aug 19, 2017, 4:24 AM
Here is my current/updated list from disablesid.conf. I switched to suricata last year so your experience with these in snort may vary.
...then: asterix Jan 3, 2018, 6:48 AM
Here are some new additions in Suricata. They are still in my suppress list as I give them at least 3 months before considering them to be permanently disabled. Most of these blocked my smartTV from reaching the internet.
...asterix Aug 15, 2018, 12:03 AM
I now have all the below rules disabled automatically on Suricata startup using SID Mgmt.
1:2010645
1:2012141
1:2013031
1:2012810
1:2015820
1:2016149
1:2016150
1:2016777
1:2016778
1:2016879
1:2018959
1:2023883
1:2025104
1:2025107
1:2025275
1:2200024
1:2200036
1:2200078
1:2200094
1:2210016
1:2210039
1:2210042
1:2210044
1:2210050
1:2210054
1:2210055
1:2221010
1:2221028
1:2221033
1:2230010
1:2230015
1:2522456
1:2522462
1:2522464
1:2522468
1:2522470
1:2522472
1:2522476
1:2522478
1:2522482
1:25522480You can do that but at the end please give us some link to go to the full disableid.conf.
Many, many, THANKS. and if you have more full guide (how to configs snort/suricata from begin. please add on as well. Wow, it will be perfect)You can copy the contents of any file (so long as it is plain text) onto the clipboard and then either paste that into the text box on the SID MGMT tab's Edit List dialog, or you can save the file on your PC and use the Import/Upload feature to upload a list to the box.
-
@asterix
Could you share for us your last disablesid.conf ? maybe you have some NEWS. and that can use for snort and suricata ? or only suricata? Do you have any new post of config suricata for WAN and snort for LAN? Thanks for your help.Best Regards,
Daniel T