VPN DNS (i.e. PIA or NordVPN) and/or DNS over TLS - Which way to go?
-
They might get together in their super-secret squirrel cabal meetings in the Louisiana swamps and aggregate all the data.
In that manner, I might as well go back to Chrome and use all their 'services'.
Anyway... I've decided to come at this DNS delema another way. I've realized there is no (theoretical) way to configure two separate VPN services and keep DNS encrypted as you would have to ensure every DNS request passes to the correct/corresponding DNS server for either VPN (Not something I even want to consider attempting).
Also, I admit, i was having issues getting both VPN services working well together. Temporarily... sure. After a bit, I wouldn't be able to connect to Amazon, my bank, etc., w/o rebooting pfSense or 'resetting' something. Clearly, I was having DNS issues.
I had a choice. Drop one of the VPN services (PIA or NordVPN) -or- give DNS over TLS another shot. I decided to give TLS another shot.
At this point, it seems like it's working. All DNS states are '853'. Browsing is actually a bit snappier (faster DNS servers probably). Time will tell if I have issues.
TLS validation (https://dnssec.vs.uni-due.de/) is still failing. Which is the most concerning. It requires Java, so I don't know if I should be too concerned. I'm looking for another way to confirm TLS is working like it should, but no luck yet.
Not trying to make this a personal story. I figure there are others that would like their DNS "as secure as possible" with pfSense, while also using a VPN service, or even TWO VPN services!.
-
The easiest way to do that is to move your local caching resolver off the firewall, as was already stated. But people are generally not willing to make things as secure as possible since that involves sacrificing some convenience.
-
to answer this question at least: Anyone out there have pfSense configured with both DNSSEC AND a public VPN service, like PIA, NordVPN, ExpressVPN, etc?
i run Airvpn and Mullvad. 2 different tunnels obviously
i use the DNS resolver to 9.9.9.9 and cloudfare. i set it up with these instructions: https://www.netgate.com/blog/dns-over-tls-with-pfsense.html
then statically use Mullvad's server of 193.138.219.228 for the Mullvad tunnels. and they pass DNS leaks and DNSSEC.
Airvpn since you have to use 10.4.0.1 or the gateway for the Tunnel you connect to doesn't pass DNSSEC. but if fully passes all the leaks
you could probably use another provider for the DNSSSEC. but then you would not pass DNS leaks tests. since its "encrypted" it should not matter
this stuff is way over my head. but after a few years of tinkering my setup passes everything i want it to so i have left it alone
-
At least for now, this is what I've decided to do:
- I stopped using the PIA DNS servers. (Not NordVPN DNS either)
- I'm now using Cloudflare and Quad9 servers and configured pfSense for DNS over TLS (and DNSSEC ;).
- DNS request are set to ONLY go out on WAN1 or WAN2, not the VPN tunnels.
- Add firewall rule blocking all (non-domain) connections to UDP/TCP 53 Destination.
- Add firewall rule allowing domain subnet any (internal) UDP/TCP 53 connections.
Working well so far.
I've been able to get most of the DNS over TLS validation sites to return A-OK. All DNS servers only connect to TCP 853 in the states table. I struggled to get validation for quite some time. I think it's because I'm running a MS AD domain in my network. The final key was adding firewall rule(s) to block external UDP 53 access. Otherwise, my AD DNS servers would cause any test to fail.
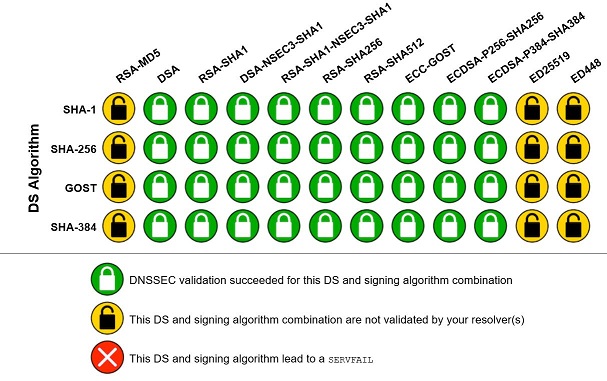
I've found this site to be most assuring test: https://rootcanary.org/test.html
(Which is 'phase 2' of http://dnssectest.sidnlabs.nl )One reason for this decision is the PIA DNS servers are pinging at 45ms. The NordVPN DNS are even worse. As you know, Quad9 and Quad1 servers are closer to 4ms. I've already noticed my browsing is a bit snappier now but that could be my imagination.
DNS leak test now show MANY servers, instead of just one, as before. However, they are all Quad9 servers. (I guess that's intentional, right?) I'm not going to worry about a bunch of servers showing in a DNS leak test, but only as long as they all appear to be Cloudflare or Quad9 servers.
Logically, I would probably rather keep all DNS queries go to an overseas VPN service, like NordVPN. However, the added latency is the final decision point.
Option 1 - I can trust a single (secure) VPN tunnel with my DNS requests, supposedly no logs are kept. Latency of 50ms+
Option 2 - I can trust a cluster of (secure) DNS over TLS servers (Quad9 & Quad1), supposedly no logs are kept. Latency of <4msEither way, all 'non DNS' traffic i sent through a VPN tunnel.
(Side note - I'm using pfBlockerNG, so separate DNS resolvers would be a nightmare, if not impossible)
The ultra-paranoid would probably be better off sending DNS queries over their VPN tunnel. I think the trust variance is purely suspicion at this point, while the performance benefit is clearly measurable.https://rootcanary.org/test.html - results with my setup...
-
I'd like to add - Early in my testing, I observed the PIA DNS servers responded to TCP 853. So, I thought maybe they enabled DNS over TLS w/o announcing it. I tried using the PIA DNS servers and also pointing the pfSense DNS resolver to PIA. It didn't work. I could only get DNS over TLS to validate outside of a VPN tunnel (OpenVPN).
I still don't know whether VPN services simply choose not to support DNSSEC/TLS or that OpenVPN is incompatible with DNS over TLS. (If someone answered that above, sorry, I missed it.) I found one VPN service advertise that they support both 'VPN' and 'DNS over TLS'. However, it sounded more like 'either / or' -not- both. It just sounded like their DNS servers would support TLS, but it wasn't clear that it was through their VPN service (more like they inferred it was outside their VPN service).
I can see their point (the VPN services). The VPN tunnel makes TLS redundant. Then again, going back to the difference between DNS over TLS and DNSSEC, the VPN tunnel only 'encrypts' the DNS message, it doesn't validate it. Wouldn't that imply that the combination of DNS over TLS (encryption) -and- DNSSEC (validation) trumps VPN (encryption only)?
I could be off my rocker here but thought the conversation is worth having.
-
@bcruze said in VPN DNS (i.e. PIA or NordVPN) and/or DNS over TLS - Which way to go?:
to answer this question at least: Anyone out there have pfSense configured with both DNSSEC AND a public VPN service, like PIA, NordVPN, ExpressVPN, etc?
i run Airvpn and Mullvad. 2 different tunnels obviously
i use the DNS resolver to 9.9.9.9 and cloudfare. i set it up with these instructions: https://www.netgate.com/blog/dns-over-tls-with-pfsense.html
then statically use Mullvad's server of 193.138.219.228 for the Mullvad tunnels. and they pass DNS leaks and DNSSEC.
Airvpn since you have to use 10.4.0.1 or the gateway for the Tunnel you connect to doesn't pass DNSSEC. but if fully passes all the leaks
you could probably use another provider for the DNSSSEC. but then you would not pass DNS leaks tests. since its "encrypted" it should not matter
this stuff is way over my head. but after a few years of tinkering my setup passes everything i want it to so i have left it alone
I can be a bit dense sometimes. I didn't see this the first time I read it. Rereading your post, you're saying you send your DNS queries THROUGH the VPN, then out the other side to Quad9 or Quad1? What's the latency on that? If it truly works, it kinda seems like you're doubling up (TLS) encryption on top of (VPN) encryption. I have no problem with that, except that I'd think the latency would be horrendous. No?
-
Well, that's no different than visiting TLS web sites over the VPN. You have to encrypt the traffic or the VPN provider will spy on you just like your evil, evil ISP.
-
@talaverde said in VPN DNS (i.e. PIA or NordVPN) and/or DNS over TLS - Which way to go?:
@bcruze said in VPN DNS (i.e. PIA or NordVPN) and/or DNS over TLS - Which way to go?:
to answer this question at least: Anyone out there have pfSense configured with both DNSSEC AND a public VPN service, like PIA, NordVPN, ExpressVPN, etc?
i run Airvpn and Mullvad. 2 different tunnels obviously
i use the DNS resolver to 9.9.9.9 and cloudfare. i set it up with these instructions: https://www.netgate.com/blog/dns-over-tls-with-pfsense.html
then statically use Mullvad's server of 193.138.219.228 for the Mullvad tunnels. and they pass DNS leaks and DNSSEC.
Airvpn since you have to use 10.4.0.1 or the gateway for the Tunnel you connect to doesn't pass DNSSEC. but if fully passes all the leaks
you could probably use another provider for the DNSSSEC. but then you would not pass DNS leaks tests. since its "encrypted" it should not matter
this stuff is way over my head. but after a few years of tinkering my setup passes everything i want it to so i have left it alone
I can be a bit dense sometimes. I didn't see this the first time I read it. Rereading your post, you're saying you send your DNS queries THROUGH the VPN, then out the other side to Quad9 or Quad1? What's the latency on that? If it truly works, it kinda seems like you're doubling up (TLS) encryption on top of (VPN) encryption. I have no problem with that, except that I'd think the latency would be horrendous. No?
no i don't think i am that brilliant...
i have dhcp computers going over the default tunnel of Airvpn. it uses 9.9.9.9
then i created rules for certain computers to use Air and others to use Mullvad tunnel
then under services - dhcp server. i am using static dns settings for those clients to resolve over the mullvad DNS servers others using Airvpn DNS servers. so they pass DNS leak tests.
-
@bcruze said in VPN DNS (i.e. PIA or NordVPN) and/or DNS over TLS - Which way to go?:
@talaverde said in VPN DNS (i.e. PIA or NordVPN) and/or DNS over TLS - Which way to go?:
@bcruze said in VPN DNS (i.e. PIA or NordVPN) and/or DNS over TLS - Which way to go?:
to answer this question at least: Anyone out there have pfSense configured with both DNSSEC AND a public VPN service, like PIA, NordVPN, ExpressVPN, etc?
i run Airvpn and Mullvad. 2 different tunnels obviously
i use the DNS resolver to 9.9.9.9 and cloudfare. i set it up with these instructions: https://www.netgate.com/blog/dns-over-tls-with-pfsense.html
then statically use Mullvad's server of 193.138.219.228 for the Mullvad tunnels. and they pass DNS leaks and DNSSEC.
Airvpn since you have to use 10.4.0.1 or the gateway for the Tunnel you connect to doesn't pass DNSSEC. but if fully passes all the leaks
you could probably use another provider for the DNSSSEC. but then you would not pass DNS leaks tests. since its "encrypted" it should not matter
this stuff is way over my head. but after a few years of tinkering my setup passes everything i want it to so i have left it alone
I can be a bit dense sometimes. I didn't see this the first time I read it. Rereading your post, you're saying you send your DNS queries THROUGH the VPN, then out the other side to Quad9 or Quad1? What's the latency on that? If it truly works, it kinda seems like you're doubling up (TLS) encryption on top of (VPN) encryption. I have no problem with that, except that I'd think the latency would be horrendous. No?
no i don't think i am that brilliant...
i have dhcp computers going over the default tunnel of Airvpn. it uses 9.9.9.9
then i created rules for certain computers to use Air and others to use Mullvad tunnel
then under services - dhcp server. i am using static dns settings for those clients to resolve over the mullvad DNS servers others using Airvpn DNS servers. so they pass DNS leak tests.
Oh, I see. I thought you meant you were passing the DNSSEC tests (and leak tests).
-
@derelict said in VPN DNS (i.e. PIA or NordVPN) and/or DNS over TLS - Which way to go?:
Well, that's no different than visiting TLS web sites over the VPN. You have to encrypt the traffic or the VPN provider will spy on you just like your evil, evil ISP.
Well the ISPs blatantly admit they are collecting, logging and selling our each and every move. The (better) VPN services claim they don't and don't appear to be. Nor are the DNS over TLS providers (i.e. Quad1 or Quad4). If you know of any stories/articles where a VPN service handed over user logs, I'd be very interested. Same with the DNS over TLS services.
-
@talaverde With Quad9 and DNS over TLS, how do I verify the server reported in dnsleaktest.com is Quad9 server?
-
@gjaltemba said in VPN DNS (i.e. PIA or NordVPN) and/or DNS over TLS - Which way to go?:
@talaverde With Quad9 and DNS over TLS, how do I verify the server reported in dnsleaktest.com is Quad9 server?
When I do an extended test from https://www.dnsleaktest.com/ I get a WHOLE BUNCH of servers listed but they are all either named 'Cloudflare' or 'Woodynet', (which looks to be owned by Quad9, based on Internet searches.) If I ended up with a bunch of random names, I'd be concerned. It seems pretty obvious who they belong to.
-
@talaverde said in VPN DNS (i.e. PIA or NordVPN) and/or DNS over TLS - Which way to go?:
When I do an extended test from https://www.dnsleaktest.com/ I get a WHOLE BUNCH of servers listed but they are all either named 'Cloudflare' or 'Woodynet', (which looks to be owned by Quad9, based on Internet searches.) If I ended up with a bunch of random names, I'd be concerned. It seems pretty obvious who they belong to.
Maybe I am not setup correctly. In my General Setup for DNS I have 9.9.9.9 and the gateway is my VPN.
In DNS Resolver I check
Enable DNSSEC support
Enable Forwarding Mode
Use SSL/TLS for outgoing DNS Queries to Forwarding ServersWhen I look in dnsleaktest.com it shows internet.exchange points as DNS. What is wrong?
-
How are you routing out the VPN? Policy Routing?
As I have already explained, you cannot policy route traffic generated on the firewall, which is why the single, best solution is a caching DNS resolver (or two or three) inside the firewall so the queries they make can be policy routed like the rest of the traffic. But nobody wants to make that effort.
Set your client to use 9.9.9.9 as its DNS server (either static or in DHCP for that inside network (you can only set it for one client with a static entry)) and you will see it works fine.
-
@derelict I tried routing out VPN in System->General Setup->DNS Server Settings. No good?

-
No. That has nothing to do with how traffic is routed.
-
@derelict said in VPN DNS (i.e. PIA or NordVPN) and/or DNS over TLS - Which way to go?:
No. That has nothing to do with how traffic is routed.
But then what does setting the DNS Server gateway to my VPN interface do? I was thinking that it is the equivalent of setting Outgoing Network Interface in DNS Resolver.
-
That might work for you but you will break DNS for the whole firewall if the VPN is down.
Honestly, the best way to ensure you don't "leak" DNS is to tell your clients to use the outside DNS providers, policy route that traffic, and forget the on-firewall resolver exists.
Or, again, put an off-firewall DNS resolver together that can be policy routed like the client traffic on its way into LAN.
-
@derelict I am just starting to get your point but what I am getting at is when Quad9 goes via my VPN, dnsleaktest.com reports internet.exchange ip for DNS and not woodynet. Is this normal?
-
You'll have to post real, contrasting "leak test" results. I have no idea what you're trying to ask.