IPSec connection established and trafic is outgoing, but no ongoing response
-
Hi,
I have an IPSec connection between a my firewall (pfsense 2.4) and a third party server.
My IPSec configuration is working fine and connexion established, but when I try to telnet the third pardy subnet address, I can't get any response from them. They are confirming that they receive my packets and I see also the packets going out from my server !My IPSec configuration is :
Local machine (192.168.50.12) <--> Firwall (pfsense) <--> Third party firwall(Cisco) <--> Thier local machine (192.168.127.80)When I see on Diagnostics > States > States and filter by third party local machine subnet I haev :
LAN tcp 192.168.50.12:42276 -> 192.168.127.80:8082 CLOSED:SYN_SENT 3 / 0 180 B / 0 B
IPsec tcp 192.168.113.12:42276 (192.168.50.12:42276) -> 192.168.127.80:8082 SYN_SENT:CLOSED 3 / 0 180 B / 0 BPS : In my Phase 2 configuration, I've set up a NAT/BINAT translation to 192.168.113.12
PS 2 : My firewall rules are :
LAN :
IPv4 * 192.168.50.12 * 192.168.127.80 * * none
IPSec :
IPv4 * 192.168.127.80 * 192.168.50.12 * * noneAny advice please !
-
Hey
https://www.netgate.com/docs/pfsense/vpn/ipsec/connecting-to-cisco-ios-devices-with-ipsec.html -
@konstanti thank you for your response. I don't think is an IPSec configuration issue. We have already a IPSec tunnel (using pfsense 2.1.5) with the same third party and same configuration and it's working fine.
-
@lmhaydii if the packets reach 192.168.127.80 and do not return, you should look for the problem in cisco
Show the output of commands
show crypto map
show crypto ipsec sa
show ip route -
@lmhaydii I would disable NAT / BINAT on the Pfsense side
-
@konstanti our local subnet 192.168.50.0/24 is already used in thier system, so I'm obligated to use a NAT / BITNAT option.
-
@lmhaydii OK
often more problems are due to MSS
Try reducing it on the cisco side to 1360
https://www.cisco.com/c/en/us/support/docs/ip/generic-routing-encapsulation-gre/25885-pmtud-ipfrag.html#anc16 -
@konstanti They did the debugging on their part and they confirm that the answer is back to me
-
@lmhaydii
Pfsense ipsec settings
VPN/IPSEC/Advanced
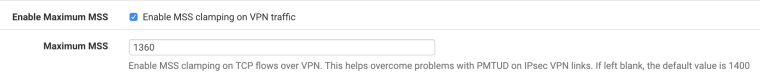
-
@konstanti Alredy tried, but not working :/
-
@lmhaydii and ping passes between hosts ?
-
@lmhaydii You can still see what's going on using the packet capture.
Diagnostics/Packet Capture
Interface IPSEC
and show here what happens at the moment of connection -
@konstanti No ping, no telnet. Telnet reach thiier server but i can't get thier response back.
When I do a telnet, pckets captured are :
12:50:05.113719 (authentic,confidential): SPI 0xc5431e8c: IP 192.168.50.12.44276 > 192.168.127.80.8082: tcp 0
12:50:06.117304 (authentic,confidential): SPI 0xc5431e8c: IP 192.168.50.12.44276 > 192.168.127.80.8082: tcp 0
12:50:08.133382 (authentic,confidential): SPI 0xc5431e8c: IP 192.168.50.12.44276 > 192.168.127.80.8082: tcp 0And Diagnostic > States are :
Packets Bytes
LAN tcp 192.168.50.12:44274 -> 192.168.127.80:8082 CLOSED:SYN_SENT 3 / 0 180 B / 0 B
IPsec tcp 192.168.113.12:44274 (192.168.50.12:44274) -> 192.168.127.80:8082 SYN_SENT:CLOSED 3 / 0 180 B / 0 B -
@lmhaydii The solution to the problem should be sought from Cisco side
Ip packets in its party leave and do not return -
@lmhaydii
Here's what it looks like to me
15:59:50.636268 (authentic,confidential): SPI 0xc4b93af1: IP XX.XXX.70.141 > XX.XXX.236.39: GREv0, length 174: IP 192.168.1.96.51731 > 208.123.73.199.443: tcp 118
15:59:50.856954 (authentic,confidential): SPI 0xc8365d06: IP XX.XXX.236.39 > XX.XXX.70.141: GREv0, length 56: IP 208.123.73.199.443 > 192.168.1.96.51731: tcp 0 -
@konstanti Thank you for your help, I will try from another server without NAT / BITANT and see if that will work
-
Hi again,
After several attempts, I come back to you, maybe I can find a solution.
I tried several configurations, but still the same issue : Tunnel connexion establisheed, telnet request go out, but can't catch the response. The responder server guys confirm that they are getting my requests and they return a response. But the response is lost somehwere and I can't determine where !
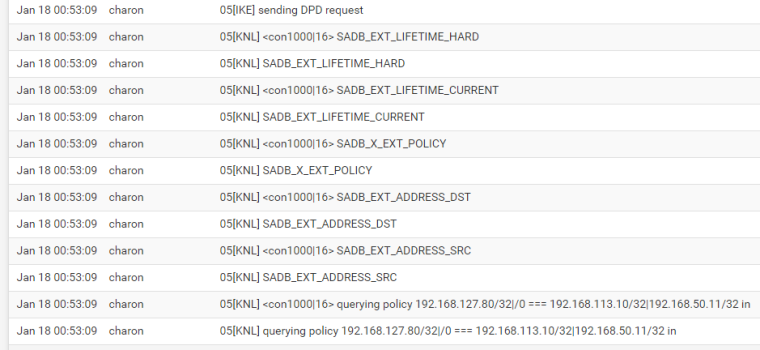
I've tried all pfsense log level on IPSec advenced options : but found nothing that can help, except when setting Kernel Interface on highest I can see :
(
This is a resume of my debbuging:
the tunnel is up and request are going out :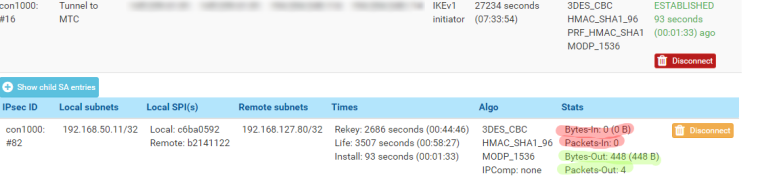
The connexion states are closed !
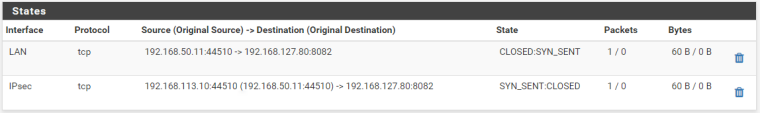
Packet captures with 0 bytes !
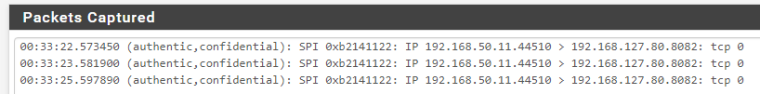
And netstat with 0 packet error !
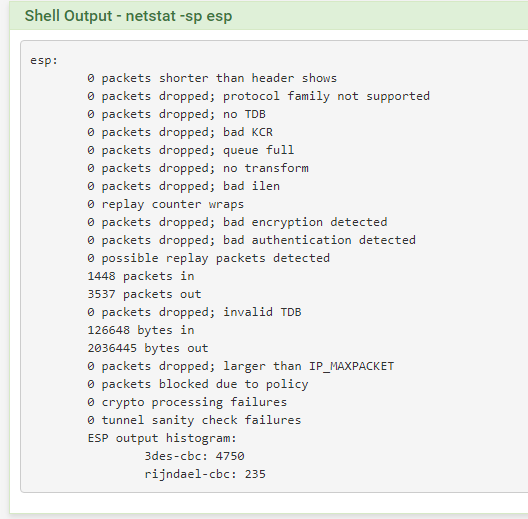
-
If the reply is not arriving on your IPsec interface there is nothing you can do about it. They have to fix it on their side.
-
Tcp 0 is the SYN packet to establish the connection, this is normal .
The bad thing is that the answer is not from the second side
It is necessary to deal with the second side
Ask them to show the answer log
Can they ping your host 192.168.50.11 ?
Can you ping their host 192.168.127.80 ? -
@derelict thank you. How can I determine with certitude that thier response or thier request are not arriving to my firewall ? There is any command to show up that ?