IPSec VPN from pfSense to Cisco 1941 dropping connection (redacted)
-
Hello again.
I'll try again to clarify
Pfsense is also Ikev1 main mode ?
Cisco Ikev1 quick (aggresive ) mode ? -
@konstanti Yes to both.
-
@thewhitewing01
I beg your pardon
Friday afternoon
Do not look back
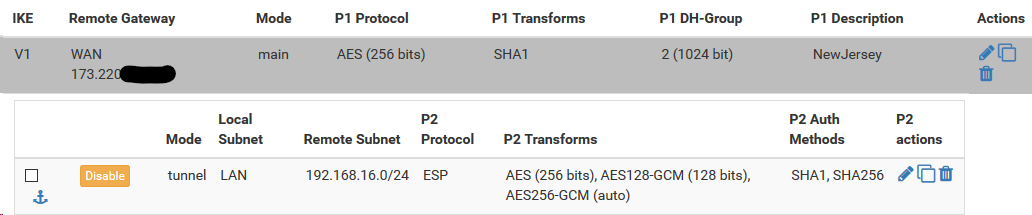
phase 1 is fine.
For some reason , problems with the phase 2 -
@thewhitewing01
Phase2
if you change the hash algorithm to sha256 on both sides
will anything change ? -
@konstanti I will try right now.
-
@konstanti Negative. No change in status. I am confused as to why the second pfSense is able to maintain connection with zero issues while this one cannot, despite using the same settings.
-
@thewhitewing01
can you send me a picture like this when the connection is established ?
Ideally, you need pictures from two pfssense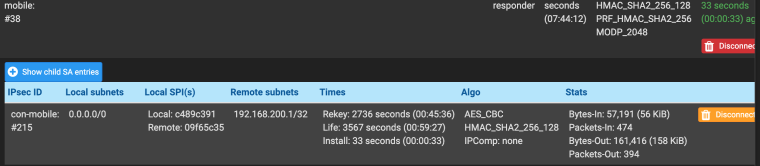
-
@thewhitewing01
See more here
I wonder what information is provided by ciscohttps://www.cisco.com/c/en/us/support/docs/security-vpn/ipsec-negotiation-ike-protocols/5409-ipsec-debug-00.html
On one of forums I read that the problem can be in mismatch of param
eters of lifetime pf / Cisco or dpddelay, dpdtimeout pfsense (keepalive Cisco)
You can try to enable/disable DPD on the cisco side
For example ,
crypto isakmp keepalive 10 5 (enable )
or
no crypto isakmp keepalive -
@thewhitewing01
Even as an option - you're blocking all incoming packets on the ipsec interface or WAN interface (500,4500 udp or ESP) of pfsense is also and cisco believes that PF is not available, and breaks the connection
What are the rules on IPSEC interface and WAN interface? -
Jan 11 10:21:26 charon 05[NET] <con1000|17> received packet: from 173.220.x.x[500] to 50.196.x.x[500] (380 bytes)
Jan 11 10:21:26 charon 05[ENC] <con1000|17> parsed QUICK_MODE request 3356035729 [ HASH SA No KE ID ID ]
Jan 11 10:21:26 charon 05[ENC] <con1000|17> received HASH payload does not match
Jan 11 10:21:26 charon 05[IKE] <con1000|17> integrity check failed
Jan 11 10:21:26 charon 05[ENC] <con1000|17> generating INFORMATIONAL_V1 request 3233859265 [ HASH N(INVAL_HASH) ]
Jan 11 10:21:26 charon 05[NET] <con1000|17> sending packet: from 50.196.x.x[500] to 173.220.x.x[500] (76 bytes)
Jan 11 10:21:26 charon 05[IKE] <con1000|17> QUICK_MODE request with message ID 3356035729 processing failed
Jan 11 10:21:26 charon 05[NET] <con1000|17> received packet: from 173.220.x.x[500] to 50.196.x.x[500] (92 bytes)
Jan 11 10:21:26 charon 05[ENC] <con1000|17> parsed INFORMATIONAL_V1 request 2703109558 [ HASH D ]
Jan 11 10:21:26 charon 05[IKE] <con1000|17> received DELETE for IKE_SA con1000[17]
Jan 11 10:21:26 charon 05[IKE] <con1000|17> deleting IKE_SA con1000[17] between 50.196.x.x[50.196.x.x]...173.220.x.x[173.220.x.x]
Jan 11 10:21:26 charon 05[IKE] <con1000|17> IKE_SA con1000[17] state change: ESTABLISHED => DELETING
Jan 11 10:21:26 charon 05[IKE] <con1000|17> IKE_SA con1000[17] state change: DELETING => DELETING
Jan 11 10:21:26 charon 05[IKE] <con1000|17> IKE_SA con1000[17] state change: DELETING => DESTROYINGYour side does not like the traffic selector in the P2 being sent by the other side.
Please send the output from each of these on each node - the one that's working and the one that isn't:
swanctl --list-connsswanctl --list-sascat /var/etc/ipsec/ipsec.confSend them in chat or I can send you a nextcloud upload link.