Restrict access for certain VPN users?
-
Look at freeradius to hand out fixed ip addresses, you can then have firewall rules based on ip addresses.
There is quite a bit more work to enable this.
https://forum.netgate.com/topic/115795/guide-ikev2-ipsec-per-user-firewall-rule-settings-with-freeradius
-
Okay, so with default IPSec, there's no chance to hand out fixed IP addresses and therefore no possibility to attach specific access rights?
I'll probably stick to the simple enable-on-request solution then. Thanks! -
@luas
There is such an opportunity for Road Warriors
What authentication method is used ?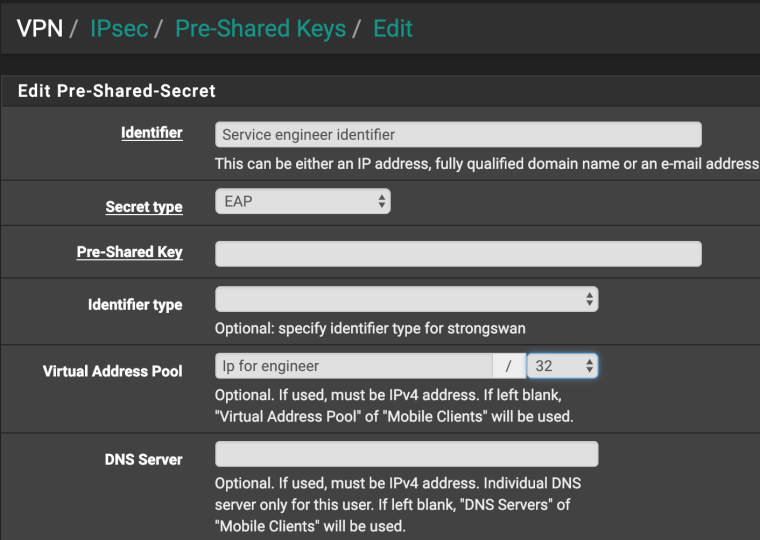
-
We authenticate via Active Directory. "Pre-Shared Keys" as in your screenshot is empty in our pfsense config.
-
It doesn't matter
You can fill in this field with any characters, as long as the user ID matches
This creates a config for the user "engineer" and assigns the required ip address -
@luas For example
I have authorization configured on the certificates
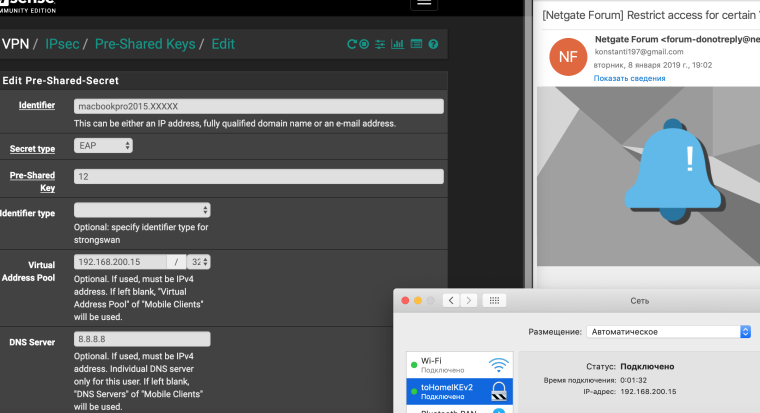
-
@Konstanti Thanks!
I tried this, but with no luck.
I used "username" or "username@domain.local" as Identifier, entered a Pre-Shared-Key and a specific IP-Adress with mask /32.
But I will still get an address from the default pool.I also tried to configure a unique PSK for the engineer in the given dialog, but then the tunnel won't come up at all.
Any other idea?
-
@luas Hey
Show me how you filled in these fields
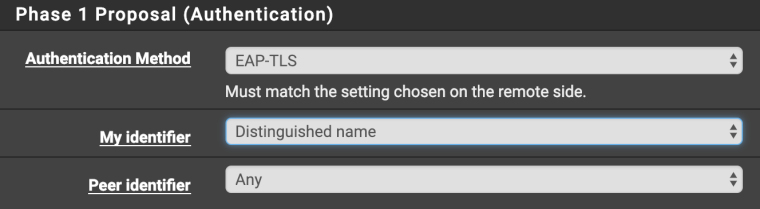
And what is the ID of the engineer ?
-
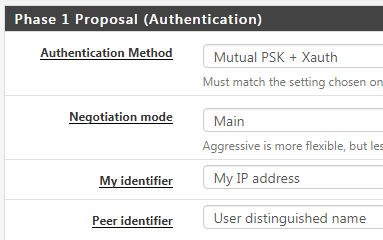
-
@luas Hey
If the problem is still relevant, I think I know how to solve it -
@konstanti Yes, I'm still interested!
-
@luas
t's easy , but you need to work with your hands a little .- create a file on the firewall , for example, /usr/local/tmp/ip.sh
make it executable, chmod +x ip.sh)
Write on there such the text
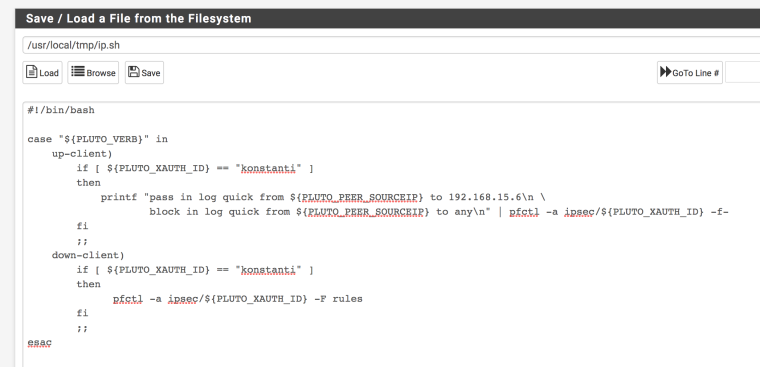
Save
-
/diagnostics/edit file/ etc/inc/vpn.inc
Find here is such a string
if (isset($ph1ent['mobile')])) {
Adding here is such the text
$ipsecfin .="\tleftupdown=sh /usr/local/tmp/ip.sh\n";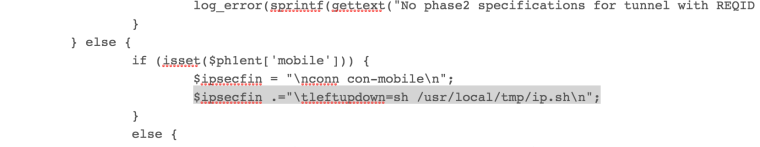
Save
-
vpn/ipsec/ mobile client /phase 1/ not to change anything . Click Save, exit
-
/diagnostics/edit file /var/etc/ipsec.ipsec.conf
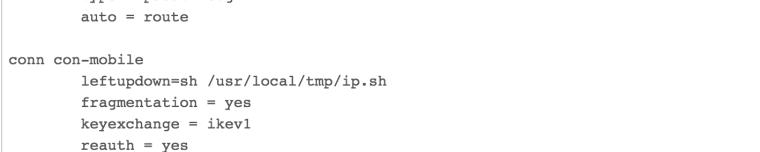
Make sure that everything is correct
As a result at us at an input of the user "konstanti" the script which gives it the rights of connection only to a host 192.168.15.6 works , other traffic is blocked. No matter what virtual ip it gets.
Other users work without restrictions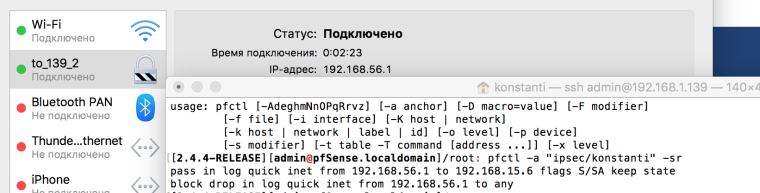

In your case , we change the username to "engineer ID" and adjust the rules so that it has limited access.
This can be done for any user
The only caveat that we need to know .
With every system update , the file vpn.inc will be overwritten and changes will need to be made again - create a file on the firewall , for example, /usr/local/tmp/ip.sh
-
Or you could just use FreeRadius like I suggested and not have to mess about with text files.