ACME 0.5 update (TLS-ALPN, BuyPass, and more)
-
New ACME pkg version 0.5 is on the way. It will be available with the next 2.4.5 snapshot run. If it tests OK, I'll make it available for 2.4.4 users.
Included in the ACME 0.5 Update:
- TLS-ALPN support, replaces old TLS-SNI support, binds to a local port (e.g. 443), similar to standalone for HTTP on port 80. If you must use this, bind to an alternate port and forward WAN:443 to the alternate port to avoid a conflict with the GUI web server.
- New alternate certificate authority: BuyPass (experimental), to be used instead of Let's Encrypt. This CA has different policies than LE, for example the certificates are valid for 180 days instead of 90, and has a different chain of trust. It still uses the ACME protocol. See https://www.buypass.com/ssl/products/acme for more info.
- New providers
- Exoscale
- Linode v4 API (split from existing Linode option code)
- Various bug fixes from acme.sh upstream.
In case you missed what was new in 0.4, see https://forum.netgate.com/topic/138729/acme-0-4-update
I still want to try using the Namecheap code from 0.4 but though I applied for API access on December 18th and should only take two business days to be enabled, it has yet to be approved. I suspect the person over the API approvals has taken an extended holiday break.
-
This will be rolling out to 2.4.4(-pX) users today.
-
Was spam-hitting 'refresh packages' since.
Got it :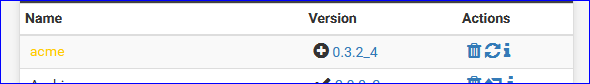
Thanks !
edit
Wow ...
The version number took a hit :
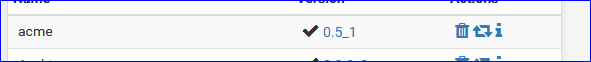
edit again : never mind : saw the change log.
-
I bugged Namecheap since my API access still had not been approved and they manually approved it. I tested the Namecheap API code and found a bug. It is fixed in pkg version 0.5.1 which will show up to install shortly.
With that, I was able to successfully obtain a certificate using the Namecheap DNS API.
-
I'm using 0.5.1 fro several days now, works great.
I noticed one big visual change. Before, when acme finished (manually, me hitting the button) renewing, I saw this huge big green text bloc with 'log results'.
Now, all I see is this :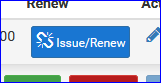
which means : "all ok". Right ?
-
I still get the same green text box output I did before, at least with the methods I used/tested (nsupdate and namecheap). Are you sure nothing changed in your browser? Any different ad/script blockers?
-
This post is deleted! -
I have been trying to issue certs with the TLS-ALPN method, but getting failures:
"type": "tls-alpn-01",
"status": "invalid",
"error": {
"type": "urn:acme:error:connection",
"detail": "Timeout during connect (likely firewall problem)",
"status": 400Firewall setings are good but i looked through the logs as I see the line to start the server with openssl:
openssl s_server -www -cert /tmp/acme/example.com-cert//xample.com/tls.validation.cert -key /tmp/acme/example.com-cert//xample.com/tls.validation.key -accept 443 -4 -alpn acme-tls/1
When running this manually I get :
unknown option -4
usage: s_server [args ...]editing acme.sh:2174: __S_OPENSSL="$__S_OPENSSL -4"
to acme.sh:2174: __S_OPENSSL="$__S_OPENSSL"
and certificates are issued fine
-
@bigbrett said in ACME 0.5 update (TLS-ALPN, BuyPass, and more):
When running this manually I get :
So, locally, it passes.
But LetsEnscrypt comes in from the outside, and it hit the wall. -
No it is not firewall related at all but the fact that acme.sh is putting in the '-4' flag on the command line to start the TLS-ALPN server, which is not supported by the current openssl version.
The TLS-ALPN server does not in fact start so LE cannot connect to it, even though the firewall rules are correct. Maybe there needs to be a check to make sure the server is started successfully before proceeding?Cheers,
Brett
-
I fixed this a different way (that didn't require editing acme.sh):
https://github.com/pfsense/FreeBSD-ports/commit/b7024a0b261280d456317f37c3e1deff8290d682
Should be up for download shortly.
-
great work as always :)