Redirect DNS to localhost stopped working
-
Hi!
Since a couple versions back I've done a redirect of DNS queries trying to go out from the LAN. So a NAT rule redirecting UDP/TCP 53 from LAN, dest !LAN to 127.0.0.1:53. This has worked as intended, no DNS queries can leave the network and are redirected to the local unbound.
Clients, LAN.
I'm not sure when this stopped working as most machines does pickup the DHCP DNS provided to them and use that one.
So, when doing some test the other day I tried setting an external DNS 1.1.1.1 and 8.8.8.8, and got no answers. The redirect doesn't work any longer.Unbound is assigned to ALL on incoming and outgoing.
Tried resolving the issue by redirecting (LAN NAT) to the LAN address instead, pfsense LAN interface address, and everything started working as before. No matter what DNS the clients use the queries are resolved locally.
So, why has my, untoched, redirect for DNS stopped working? Any bright ideas?
Brgs,
-
@iorx Did you check that localhost is selected in dns resolver Outgoing Network Interface setting?
-
@iorx said in Redirect DNS to localhost stopped working:
Unbound is assigned to ALL on incoming and outgoing.
Hi!
"Unbound is assigned to ALL on incoming and outgoing."
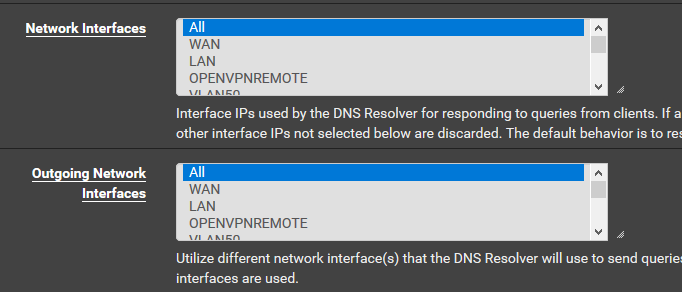
I presume that All includes all the interfaces listed below. Should I test Ctrl+click All and localhost maybe.
No, just tried that. All and localhost selected. No go.Brgs
-
Post screenshots of your firewall rules, if you get no answer then there is a rule blocking it.
-
Here we go:
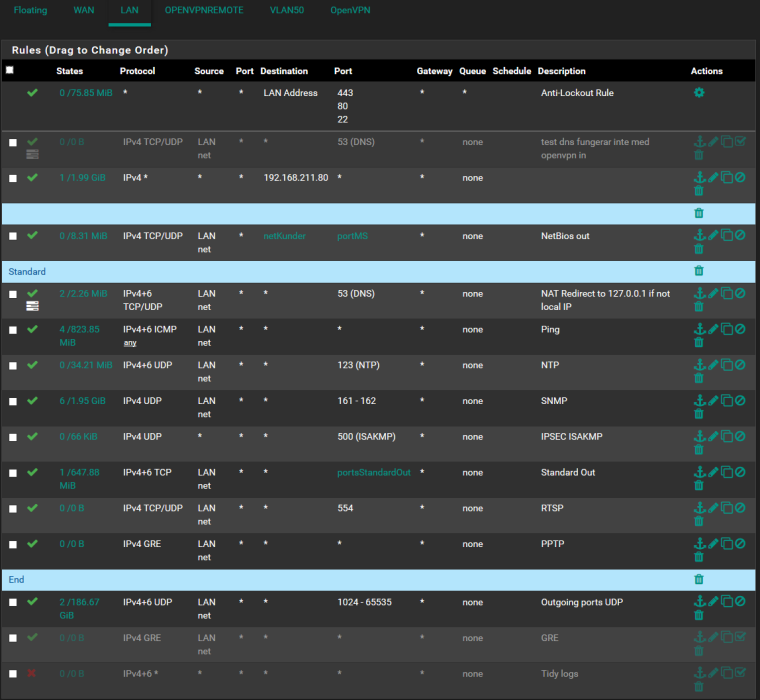
and the NAT rule (now pointing to LAN-address, which works, instead of localhost that don't work)
-
@iorx Unable to reproduce. Works as documented
https://www.netgate.com/docs/pfsense/dns/redirecting-all-dns-requests-to-pfsense.html
-
Why all the nonsense, so block outbound on handful of ports?? Just pointless if you ask me... Really you need PPTP outbound?? Those rules just seem utterly meaningless... To what stop a handful of ports under 1024?
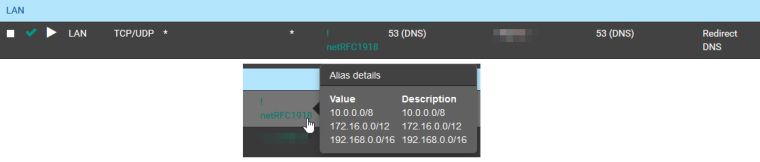
You blurred out your local address? rfc1918?
Where exactly do you have that NAT rule -- looks like a floating rule? When it should be in your port forward section..
-
Hi!
Thank you for answering.
The utterly pointless rules, whitelist rather than blacklist. And to have an overview if any traffic not destined for outside under <1024 were initiated.
NAT rule is in specified in the pictures attached. The LAN-NAT which correspond to the documentation linked by gjaltemba (thank you, that was the one I looked at creating in it initially).
So, what made me post this to the forums? It has worked before and by checking logs and config I couldn't figure out why it had stopped and reached out for some tips here.
Blurred out local address. It's not important to the problem. RFC1918 (https://en.wikipedia.org/wiki/Private_network), as the attached picture shows, redirecting DNS if not the destination address falls into that category. Still want DNS queries to go unaffected to a couple of subnets and OpenVPN/IPSec tunneled networks.
PPTP (and the disabled GRE), an old test with a clients machine which still used that. To be removed.
For your future, you may think of having a little more humble way of responding, this type of answer Why all the nonsense, so block outbound on handful of ports?? doesn't help and just make the author of the initial post feel dumb. Maybe there is a thought behind it.
The knowledge of users in the community have a very wide spectrum, as of mine I think I've got some experience with pfsense, firewalls and networks. But you never stop to learn new thing and new ways of doing stuff.I'll backup and recreate my NAT and rule set to make sure everything is as documented and preferred. Will, if I find out why, reply to this thread with the results.
Brgs,
Live and prosper my dear friends. -
@iorx said in Redirect DNS to localhost stopped working:
And to have an overview if any traffic not destined for outside under <1024 were initiated.
Yeah UDP only? And your not logging it so how would you know? Your block rule there at the bottom doesn't log.. And looks like your moving GBs worth through that rule.. So P2P would be my guess.
Be you like my wording or not... Those rules make no sense..
-
Default logging of blocked traffic catch the traffic. The block rule at the bottom is disabled. Logs go to a syslog-server and are analyzed there.
UDP Only. No, TCP-ports covered in the port-alias. 80,443, 1024:65535 among other standard ports for outgoing traffic.
I would really like the rule set to make sense. Some basics in firewalling is to open on a needed basis. The rule set does just that, and prevents external DNS queries.
P2P, not so much. UDP traffic originates from two sources. OpenVPN and a hosted backup solution for customers.
Brgs,