2 LANs cannot communicate
-
vlan/physical network - its all the same..
See here
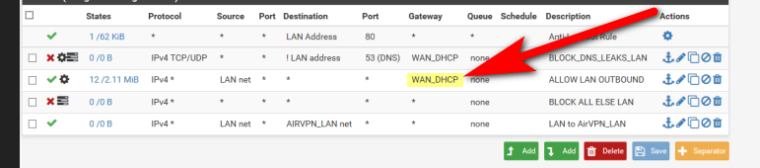
How exactly are you suppose to get to your other networks if your forcing traffic out your wan?? Why would you setup that rule?
Rules are evaluated top down, first rule to trigger wins... That rule that allows lan net to get to airvpn_lan net will never be evaluated because you have a any any rule from lan net that sends everything out your wan.
Why would you do such a thing?
This guide told you to do that?? I find that almost impossible to believe - they can not be that stupid?
-
@johnpoz this is the guide I followed from airvpn https://airvpn.org/topic/11245-how-to-set-up-pfsense-21-for-airvpn/
Second LAN Firewall Rule:
"ALLOW LAN OUTBOUND"
1.) Go to: Firewall > Rules
http://192.168.1.1/firewall_rules.php
-or-
https://192.168.1.1/firewall_rules.php
and select your "LAN" interface.2.) Click the [+] on the right to "Add New Rule" and create a rule we will title "ALLOW LAN OUTBOUND" (Note: There may already be a rule titled " Default Allow LAN Outbound" or similar. You certainly can just edit that entry to these settings, or delete and create this.)
3.) Set as follows:
Action = [ Pass ▼]
Interface = [LAN ▼]
TCP/IP Version = [IPv4 ▼]
Protocol = [Any ▼]
Source = [] Not (UNCHECKED)
Type: [ LAN Subnet ▼]
Address: [] (BLANK)
Destination = [] Not (UNCHECKED)
Type: [ Any ▼]
Address: [__] (BLANK)
Description = [✎ ALLOW LAN OUTBOUND]
*****IMPORTANT STEP: [ADVANCED FEATURES] > GATEWAY = [ WAN_DHCP ▼]4.) Click [ SAVE ]
5.) Click [ Apply Changes ]
.) Go to Firewall > Rules
http://192.168.1.1/firewall_rules.php
-or-
https://192.168.1.1/firewall_rules.php
and Select your "LAN" interface.2.) The order of the rules we just created is important!
They should appear in this following order when viewed:
BLOCK DNS LEAKS LAN
ALLOW LAN OUTBOUND
BLOCK ALL ELSE LANENSURE THE RULES ARE IN THIS PRECISE ORDER, IF THEY ARE NOT, ORGANIZE THEM AS NECCESSARY!
-
@perfectdark said in 2 LANs cannot communicate:
*****IMPORTANT STEP: [ADVANCED FEATURES] > GATEWAY = [ WAN_DHCP ▼]
Just Moronic!!!
And clearly doesn't take into account or mention if you have other networks.
How exactly do they expect dns to work even? Your client has to ask some public dns?
-
@johnpoz you are 100% right (thank you) and funny thing is that guide was for 3 NICs (1 WAN, 1 for VPN LAN and 1 for LAN)
I moved my rule to the top and both subnets can communicate now. Thank you for your assistance in pointing this out.
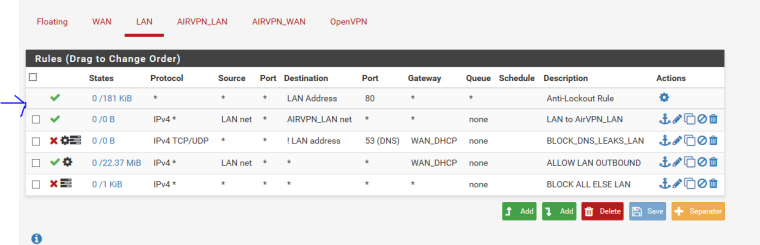
-
How you going to resolve anything locally? Since you can not ask pfsense for dns per those rules.
What is the point of the last rule? There is a default deny on all interfaces... There is zero reason for that last rule..
-
@johnpoz I’m still trying to understand all the rules , I just followed the guide to get things going. Then I can spend some time learning what means what.
I’ve tested both my subnets and both are working and resolving websites. My airVPN LAN also has no DNS leaks. The LAN subnet uses the Public Open DNS and the AirVPN LAN is using the DNS static provided by airvpn and assigned to each device via the airvpn dhcp server.
-
And how exactly do you resolve a host on on the other network to access it by name?
Why would you not just let your resolver resolve through the vpn connection, and have your local devices ask your local resolver?
-
@johnpoz i don’t have the DNS resolver active , I’m using the DNS Forwarder
-
Again no reason for that.. Resolve through your vpn connection, that way your not sending all your queries to your VPN dns.. But guess its ok, they don't log anything <rolleyes>
-
@johnpoz lol “roll eyes” I’ll look into this as I’m not sure what changes I need to make
-
Generally what you are doing is not best practice.
Unless you need your two subnets isolated from eachother, its much better to use only one LAN port on your pfSense device, and use a hardware switch to manage multiple devices.
pfSense is also a pretty lousy WiFi access point, so I wouldn't do that AirVPN thing at all. Get a dedicated Wireless AP instead.
pfSense is just about the best firewall and router setup you can get yourself, but it is essentially an enterprise tool, and not intended to replace the traditional consumer router.
In enterprise settings you usually have dedicated routers/firewalls and separate hardware switches and hardware Wireless Access Points.
This is how it is designed to work.
You CAN bridge ports and have them talk to eachother, but performance will not be good. Its much better to use a switch for this. They are cheap, and that is what they are designed for.
-
@mattlach I think you are misunderstanding my setup
I am not using pfsense as an Access Point. I have eero behind my LAN port for that.
AirVPN is my VPN provider. The reason for two LANs is one subnet routes directly to ISP and other subnet through VPN for privacy.Example my Xbox and XB6 STBs will go through ISP via LAN and my wifi traffic , Torrents etc will go through VPN for privacy.
My switch is located behind the pfsense firewall