NAT a Windows share from WAN?
-
Hi,
I'm trying to NAT a Windows share from a external (WAN) IP to a LAN host . I've done this before with RDP without a problem but for some reason a windows share isn't. ideas?NAT settings:
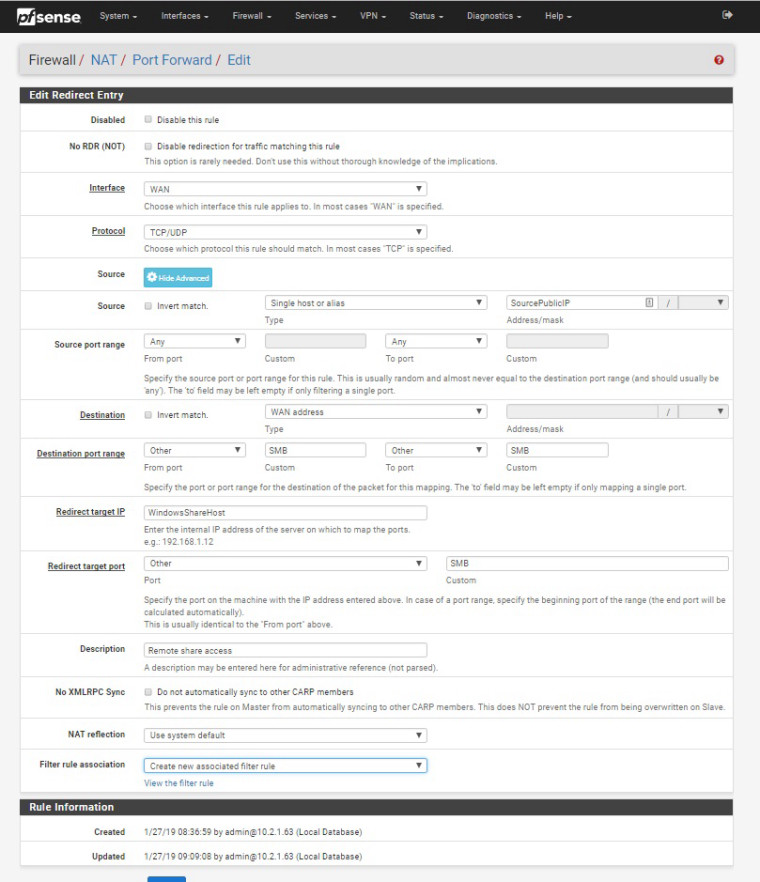
SMB alias is set to 137, 138, 139, and 445
-
TCP 445 should be enough.
Did you check the Windows Firewall?
Better use some VPN anyway.-Rico
-
445 is normally blocked over the public internet... Many an ISP blocks this, shoot some cable modems block it on their own settings... There is like zero reason this should ever be used over the public internet.
-
@dennis100
1 show wan rules
2 diagnostics/packet capture
interface lan
address family ipv4
protocol any
host WindowsShareHost ip
port 137 or 138 or 139This type of access is not secure
it is better to use vpn -
Problem happens with firewall on remote on or off. Both sites have a pfsense firewall. As best I can tell, the packets are being blocked at one ISP or the other.
This is for an automated process (backup). I've been using rules on the firewall to limit to a specific IP when I'm not using a VPN. Could pfsense redirect ports at each end so I end up with something like 445 - 2567 - 445?
-
sure you could do that... Again 445 over the public internet is just not viable.. If you want to backup from one location to another via smb... Why would you not just fire up a vpn connection between the two and then do whatever protocol you want through the vpn.
-
It is an automated process so the connection would need to be done without user interaction. I've avoided using a site to site VPN as I don't want anyone on either site to have access to the other site. Using a rule with a specific IP seems to be easier to control which ports are allowed and what systems they're allowed from. Also, since this is a backup speed is important and skipping all the encryption for a VPN would help maintain speed. Anything that's sensitive is already encrypted.
So to do this what would I do? Set up a NAT on the source and another on the destination? Maybe a howtosomewhere?
-
With pfSense you have the same control using Firewall Rules how the traffic is allowed to flow in site to site VPNs.
You can lock everything down beside IP A to IP B port 445 for example.-Rico
-
How would I do that? I'd like to restrict all access to the site 2 site VPN from my LAN to only a specific group of LAN IPs (alias). Do I block the OpenVPN port (1195 for this VPN server) to all and add an exception all on the LAN interface? How would I restrict it to specific ports?
-
Its a site to site, simple thing to do is just block the access on the actual interface on the sites that the users are connected too.
So on lan of site A for example you would put in a block to the remote network on site B. Above that you would put in the rules for the IPs you want to allow from and 2 and the port(s) involved.
Firewall rules are evaluated as traffic enters an interface from the network its attached too, first rule to trigger wins - no other rules are evaluated. Its that simple!
Lets say site A is 192.168.1/24 and site B is 192.168.2/24
On site A you allow say
src 192.168.1.42 dest 192.168.2.100 port 445
below that rule
src lan net, dest 192.168.2.24
Below that would be your default any any rule of the internet default lan rule.You could just block
top rule
Block src lan net, dest 192.168.1/24If you do not want site B to talk to anything on site A.
-
I see. Even though the VPN traffic is passed through port 1195 that is transparent as far as setting rules on the LAN interface.
-
Your actual box behind pfsense is not talking to 1195, pfsense would be talking to other pfsense on that port to create the tunnel.
Your traffic is then routed down that tunnel.