Home LAN IPSec VPN to my Office LAN and IPSec remote access (route all), can't see Home LAN
-
I have pfsense on both my home network and office network. Home is 192.168.0.0 and Work is 172.16.1.0. Both sides see each other just fine (FIOS Gigabit on both sides)
I've got IPSec remote access set up on the office pfsense on a 10.254.69.0 (route all). Works great. Remote access from Win 10 laptop gives me access to all work resources.
Problem: from my remote laptop I can't use any of the resources on my home network.
Do I need additional phase 2's? I did some searching and that's all I came up with. I try not to be a helpless poster (although at times I am)
Thanks,
Roveer
-
I’m guessing you’re tunnelling everything over the VPN rather than specific routes.
Check your P2 settings.
-
Sounds like you need an additional P2 between the office and home for 10.254.69.0 <=> 192.168.0.0.
It looks like you are aware of the advantages of using somewhat-random RFC1918 choices but it would not surprise me if you ended up with occasions where the mobile IPsec client's local network was 192.168.0.0/24 which would be problematic.
Devices on your home network will also need to have their firewalls allow connections from "foreign" networks. If you can access them over the VPN from the office, it should work for mobile connections into the office too.
-
@derelict said in Home LAN IPSec VPN to my Office LAN and IPSec remote access (route all), can't see Home LAN:
Sounds like you need an additional P2 between the office and home for 10.254.69.0 <=> 192.168.0.0.
It looks like you are aware of the advantages of using somewhat-random RFC1918 choices but it would not surprise me if you ended up with occasions where the mobile IPsec client's local network was 192.168.0.0/24 which would be problematic.
Devices on your home network will also need to have their firewalls allow connections from "foreign" networks. If you can access them over the VPN from the office, it should work for mobile connections into the office too.
I had a little time to mess around but couldn't get it to work.
I'm going to need a little more help on this one. My brain has been away from pfsense for a while, so it takes me a little longer.
First: Am I going to need P2's on both firewalls (Office and home)? I'm thinking yes
Second: Where do I add the P2, to the WAN P1 or the MOBILE P1? I'm thinking the WAN P1
Third: Anything additional needed on the mobile client?So I tried adding P2's to the WAN P1's on both Firewalls and it didn't work. Of course I could have had something wrong or missing, but I'll need to know if I was doing it correctly before trying again.
This is really just convenience. I've got the home firewall set up for remote access as well, but I usually connect to the work firewall and stay connected all day. I'd like to have the same level of access as if I were a workstation at work. Plus, I'm learning something new and I like to challenge my brain.
I searched a bit but haven't come across anything definitive.
-
Consider the mobile IPsec to be just another interface on the work firewall.
So you would add the new P2 to the work and home firewalls.
Yes, you need to put it on both sides (the reciprocal of each other.)
-
@derelict said in Home LAN IPSec VPN to my Office LAN and IPSec remote access (route all), can't see Home LAN:
Consider the mobile IPsec to be just another interface on the work firewall.
So you would add the new P2 to the work and home firewalls.
Yes, you need to put it on both sides (the reciprocal of each other.)
So here's what I've done
and it does not appear to work.It did work. Read post below. Have I placed these in the correct places? Do I need any additional firewall rules? I did try adding allows on both sides, but that did not work either. I noticed that my phone (which I'm using to tether my laptop in order to get an outside internet connection) is giving a 192.168.142.x address. I'm going to test at another location that will give a non 192 address.Work:
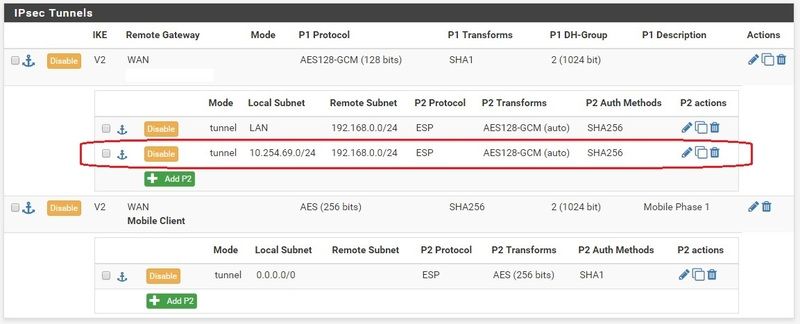
Home:
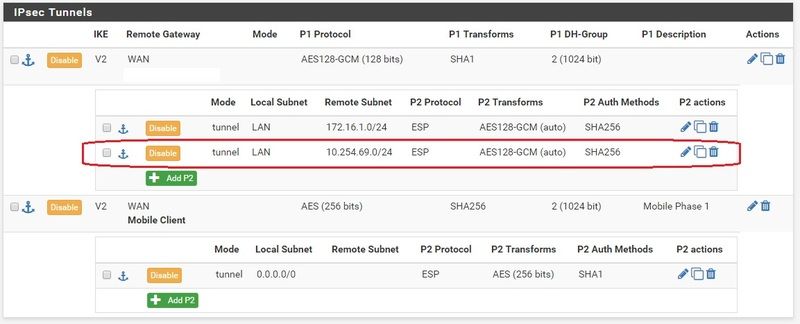
-
-----UPDATE-----
I decided to reboot the work firewall. I've seen instances where a reboot would implement something that I thought would be dynamic and for whatever reason would not.
After the reboot. I tethered laptop to phone, verified internet, connected vpn and was able to access resources on both work and home network.
Going to try at remote location later today, but it would appear this has been a success.