Problems in address distribution in DHCP
-
@jknott What do mean by "filter page"?
-
@ronron555 said in Problems in address distribution in DHCP:
@jknott What do mean by "filter page"?
In pfSense, click on Firewall > Rules. It's where you create the rules to filter traffic.
-
@itay1787 said in Problems in address distribution in DHCP:
This pfsense is designed for school and I want to create a separation between the teachers and the students because of this i need lan (teachers) will have different rules and different ip addresses.
This done via VLAN... PERIOD!!! If your AP does not support vlans, then get new AP that does.. Or just use different AP for each vlan.. Same goes for switches - you need vlan capable switches unless all of your clients are wireless.
If what you want to do is allow different users to access different internet pages, this can be done with proxy, and or restrictions can be done with captive portal, etc.
-
I would do this one of two different ways: 2 separate physical interfaces, or 2 separate virtual interfaces.
Put all teachers on one interface, put all students on the other interface. You can then DHCP and work with the pile of MAC & IP addresses all you want, for each interface. If you want traffic to cross-over from one interface to the other, simply write the proper firewall rules on pfsense.
Do NOT use bridging.
Jeff
-
@jknott Hey, after the new changes I made to pfsense on your advice it seems that the problem was gone, everything works great.
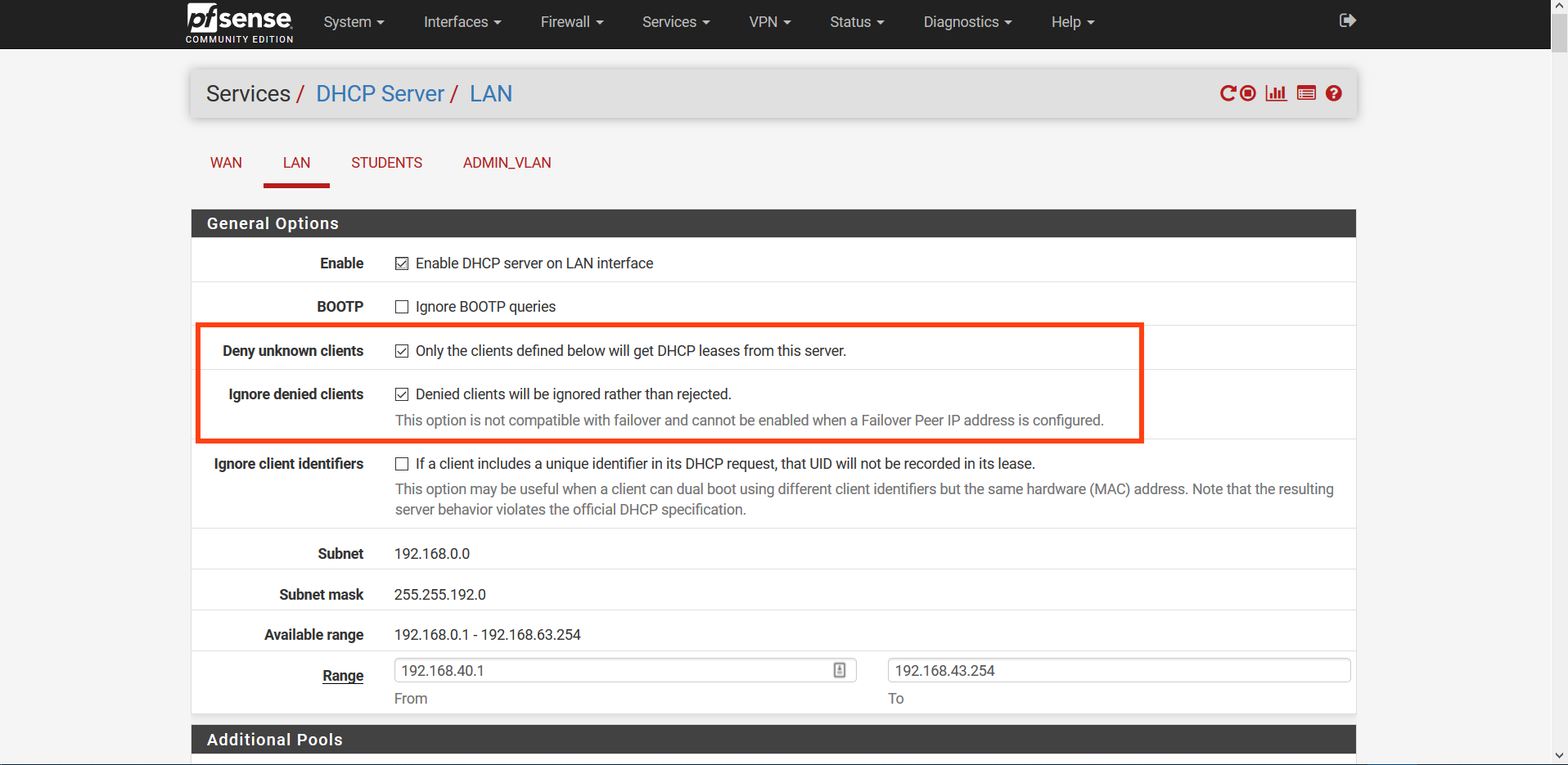
There is only one problem - I have to block all "STUDENTS_Network" from "LAN"
Meaning that they would have access only to the Internet and nothing else.
Please look at the picture I attached.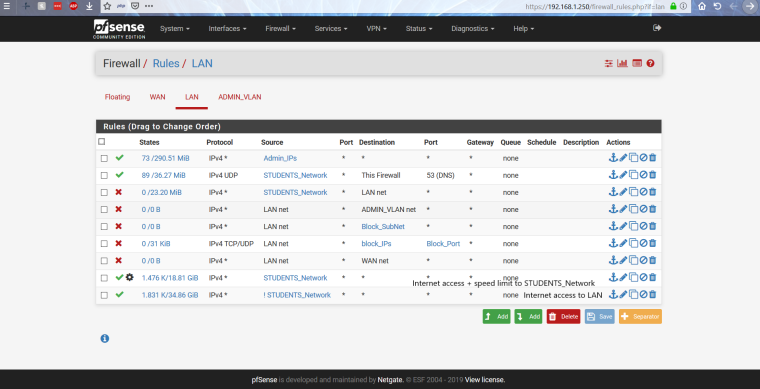
-
Where is this students network - I only see lan and admin_vlan
Where is the students vlan?
-
@johnpoz There is no vlan. This is alias
-
In that configuration any student who wants to can just set a static IP address on the teacher LAN and be on it.
That is implementing almost no security at all. Or, worse, just an illusion of security.
If that is a business requirement, someone is going to have to buy some gear that supports 802.1q. Or duplicate the layer 2 gear for two separate LANs with different router interfaces.
-
@derelict We know that VLANs will be much more secure
But as soon as the network is built, it's the thing we found that will work. We may soon be switching AP. And with that happening, we'll make sure they have VLANs and replace everything with VLANs.But right now we have a problem with setting up one of the rules as I said above.
-
You can not stop people on network A from talking to other people on network A... The firewall/router is NOT involved in these discussions.
Why do you think we stated the only way to do this is with vlans.
-
Because DHCP server is not designed to do that. It is designed to serve the interface subnet scope. You will probably have to use a different DHCP server.
-
You can not build a network with junk ;) you need to either isolate your networks at the physical layer with different switches and AP for each network you want. Or you need switches and AP that support vlans - its that simple = PERIOD!
-
@johnpoz I thought so.
So can not you just block one subnet from everyone ??
And with not like it sounds we'll move on to VLANs faster than I thought. -
@derelict We tried it. Did not work properly at all !!!!
-
@johnpoz Question: I have one switch which is the main and it supports VLANs Can I take out VLAN tagging. Then from AP (which is after some other "dumb" switches) will it work without affecting the rest of the network ??
-
@itay1787 said in Problems in address distribution in DHCP:
@johnpoz Question: I have one switch which is the main and it supports VLANs Can I take out VLAN tagging. Then from AP (which is after some other "dumb" switches) will it work without affecting the rest of the network ??
If you remove the VLAN tags, you'll not have VLANs. I assume you're asking if you can put the AP on just one VLAN? If so, yes. Assign an access port, on that managed switch to that VLAN and then connect the AP to it. The AP will then only connect to that one VLAN. Those dumb switches, between the AP and managed switch, will also be on that same VLAN. However, that means only one group can use WiFi.
-
You can downstream dumb switches from a smart switch sure... And all devices connected to that dumb switch will be in vlan X that thet upstream smart switch puts that switch in.
You can then use specific dumb AP and connect them to specific vlans depending on where you plug them in. Or if you want clients that are on different vlans to use the same AP then the AP needs to support vlans, and it needs to be connected to a switch that supports vlans.
This can be done very cheaply depending on how many ports you need and how many wifi clients you have and how spread out you need your network to be. A 8 port smart switch can be had for like 40$ an AP that support AC and Vlans say the unifi AC-Lite model is like 70$
-
I mean if I can set up VLAN from a switch that supports it and set it in tagging and then take the VLAN tagging from the AP and the AP is connected to the dumb switch and it will not affect the devices that are connected to the other ports in the dumb switch
Right? Because that's what vlan tagging should do.
-
VLAN tagging will pass through dumb switches. However, if your AP doesn't handle VLANs, which is what I thought you said, it wouldn't work. VLANs are just a way to logically separate networks. If you want an AP to support multiple SSIDs, which is necessary to separate users, then it must support VLANs. You'd also need VLAN support on pfSense or a managed switch to handle those VLANs.
-
While it is possible to pass vlan tags across a dumb switch - since it doesn't understand the tags.. There will be no isolation on that switch... All broadcast will go over all ports no matter the vlan it is suppose it suppose to be in.
Just because a dumb switch might not actually strip a tag, doesn't mean its good idea to run vlans over such a device...
If your going to use vlans than all your devices should support vlans - other than you can leverage dumb switches that are access level switches where only clients in the same vlan will be connected, and the only vlan that will go to that end switch is in a specific vlan... Ie as a downstream switch from a smart switch.. But no other vlans should cross over that switch.