Can't make Netgate SG-1100 into Pure Router
-
- I am trying to temporarily turn off all firewall functions and use Netgate SG-1100 as a pure router.
- My configuration is (cable modem)->Netgate SG-1100.
- There are two networks:
WAN: 192.168.15.x/24 connected to cable modem
LAN: 192.168.1.x/24 connected to switch/host - I tried using the Advanced->Firewall & NAT->Disable Firewall option. When I turn it on:
4.1 Pinging from host in 192.168.1.x subnet gets to 192.168.15.x hosts but the pings to public addresses do not return.
4.2 Netgate SG-1100 console interface can ping hosts on either private lan. - This scenario is for use when I need a fast upload of something and then drop back down to filtered traffic later.
- Searched all mentions of "Disable all packet filtering" in forums and find no answers.
- I suspect this is a static route problem, but not sure what static route to add for public addresses
What am I doing wrong?
-
You can't disable the firewall because that also disables NAT. You need NAT to get out to the internet.
If you wanted to do it without NAT, whatever is upstream of your WAN would need a route for 192.168.1.0/24 with a gateway of whatever the pfSense WAN address is on 192.168.15.X.
So it's not not something you need to do on pfSense, but on the upstream device.
The upstream device would also need to know to NAT for 192.168.15.X and 192.168.1.X.
-
Derelict,
Thanks. The upstream device is a Netgear C7000 cable modem that does NOT do NAT for anything other than its OWN internal subnets. There are no configurable parameters to setup NAT on the device.
-
What about loading the RouteD package and manually adding routes on the SG-1100 using RIP?
-
How should RIP be configured to do this?
-
If RIP wouldn't work, can OSPF be used instead?
I thought it might be just a routing problem.
Forgive my ignorance on the subject. I am a datacom engineer with a BS in electrical engineering and 34 years experience but never learned much about NAT so far.
On a more positive note:
-
I'm quite pleased with the Netgate SG-1100 device so far. You get a lot of value for the money.
-
Your choice of hardware was a good one: Espresso.bin Version 7
https://www.globalscaletechnologies.com/p-72-marvell-espressobin.aspx -
I read your response on hardware encryption and how you are still working on a driver for it. That can't come soon enough!
https://forum.netgate.com/topic/139983/sg-1100-crypto-hardware -
I did some testing with the device with the firewall turned on and found that the UTM throughput of the device is about 10Mbits/sec up and down by using HTTP and running a test at http://speedtest.net. That's considerably below the published specs described at:
https://www.netgate.com/blog/netgates-new-sg-1100-punches-way-above-its-weight.html
The above test was not limited by my ISP, because they provide 85Mbits/sec down and 35Mbit/sec up with a Docsis 3.0 bonded channel with four uplinks.
The claims in the above article are obviously based on conditions that a typical user would not use. A 923 Mbit/sec throughput on the SG-1100 with 1500byte packets must be using the Marvell switch between two ports, not UTM going through the actual firewall. That would be called the Firewall Throughput, not the UTM throughput. The UTM throughput is what you should really talk about in the above article and compare it to your other higher priced products. That is the throughtput that most users REALLY care about, not the Firewall Throughput. You also don't publish THAT, and I hope that isn't because you wanted to spin the article as propaganda.
10Mbit/sec up and down UTM throughput isn't bad compared to your more expensive products or even your competitor produces, but it isn't anywhere near the marketing hype in the above article. High UTM throughput, I am finding, is VERY hard to come by and VERY expensive. To compare other competitors, see the UTM specs on Newegg at:
https://www.newegg.com/Product/ProductList.aspx?Submit=ENE&DEPA=0&Order=BESTMATCH&Description=firewall&N=-1&isNodeId=1I am new to firewalls and am enjoying the learning and your incredible and excellent documentation. Keep up the great work. If nothing else, its a great and inexpensive learning tool. I chalk the price up to "tuition".
Thanks so far for your help.
Joshua777
-
-
SOMETHING is doing NAT since there are private addresses on all pfSense interfaces.
If you are only getting 10Mbit/sec through the 1100 you are doing something else wrong.
No. Nothing is going to route your private networks to the internet without someone performing NAT.
-
Derelict,
Thanks. I'd sure like to know what I'm doing wrong. Its a stock factory configuration with the only changes as follows:
- Installed pfBlocker and used DNSBL.
- Installed Ntopng
- Not doing VPN because you don't have the crypto hardware drivers yet.
- Disabled "Block private networks and loopback addresses" for the WAN interface under "Interfaces->WAN"
- Running 2.4.4-RELEASE-p2 (arm64). Just got the thing days ago.
- No additional firewall rules beyond the above.
- Uninstalling ntopng doesn't increase performance.
- Max data rate indicated on Traffic Graphs on the Dashboard is 1.2M under the heaviest load possible.
Otherwise, its stock.
Any ideas? My only explanation is that the Speedtest.net numbers are BYTES rather than BITS, even though they read "Mbits/sec".
As far as NAT, I already mentioned the C7000 Cable Modem is doing it, but only for its own interfaces. Not for other devices.
-
Really hard to say but with all of that configured the throughput of the 1100 will far exceed 10Mbit/sec.
Maybe reset to factory defaults and check throughput before installing a bunch of packages, though none of those should be too bad. Then add one thing at a time and test again.
10Mbit/sec is REALLY low though. Maybe a duplex mismatch between the port and the modem or something like that.
-
-
Its not a duplex mismatch. See attached.
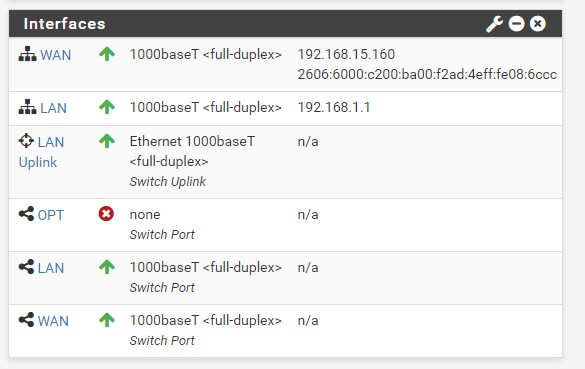
-
WAN port is connected directly to the Netgear C7000 Cable modem and its running full speed full duplex at 1G.
-
Workstation doing the speedtest is on the 192.168.1.X subnet and going through the firewall. It is running a 10G network interface (Intel 540-T2) and connected to a 10G network switch (Planet 28040GW).
-
Are there any logs I can provide that might pinpoint the problem?
-
Here's the speedtest attached.
!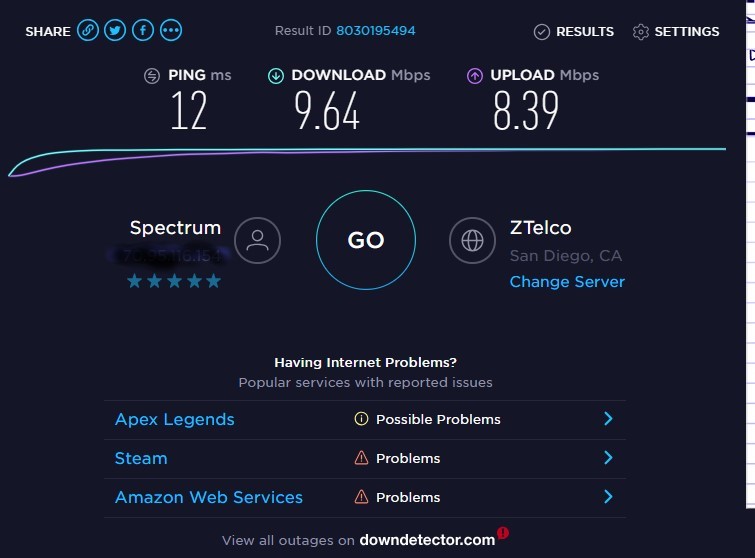
I could REALLY use the speed increase you are saying should exist.
-
-
As I stated before, someone is performing IPv4 NAT. You state there is none but there obviously is, because 192.168.15.160 is not a routable address.
What ISP is this?
-
- As my previous post of the speed test indicates in the graphic, its Spectrum.
- The SAME speed test was run BEFORE inserting the firewall, and it read 36Mbits up and 85Mbits down. So I'm losing a LOT of bandwidth by using the SG-1100
- Changing the Server as indicated in the above speed test does not significantly change the result.
- I stated that the C7000 Cable modem WAS doing NAT but nothing about it was configurable through the user interface.
-
Right. I don't doubt that. But there is something else at play here. This is what I just got through an SG-1100 placed on the inside of my network. pf enabled, etc.
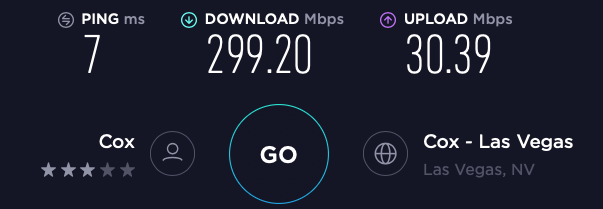
That is a 300/30 WAN.
So there is something else going on in your environment that is causing the slowdowns you are seeing. What that problem is will probably be pretty tricky to diagnose from remote. I would double-check everything you can, try different cables etc.
You can ssh to the unit (or connect to the serial console), use menu option 8, and run this:
pkg install py27-speedtest-cliThen:
rehashThen:
speedtest-cliRetrieving speedtest.net configuration... Testing from Cox Communications (68.X.Y.Z)... Retrieving speedtest.net server list... Selecting best server based on ping... Hosted by ServerPoint (Las Vegas, NV) [11.67 km]: 40.684 ms Testing download speed................................................................................ Download: 286.01 Mbit/s Testing upload speed................................................................................................ Upload: 29.99 Mbit/sThat will allow you to test from the firewall itself to isolate if the issue is on the inside or not.
Type
exitto return to the console menu. -
That's helpful.
- I logged in through the serial/USB port.
- Selected menu 8
- Installed speedtest package as indicated.
- Ran speed test with "speedtest-cli" with the following result:
[2.4.4-RELEASE][root@SHOMEFW1]/root: speedtest-cli
Retrieving speedtest.net configuration...
Testing from Spectrum (xx.xx.xx.xx)...
Retrieving speedtest.net server list...
Selecting best server based on ping...
Hosted by ScaleMatrix (San Diego, CA) [12.85 km]: 34.732 ms
Testing download speed................................................................................
Download: 160.12 Mbit/s
Testing upload speed................................................................................................
Upload: 9.36 Mbit/s
[2.4.4-RELEASE][root@SHOMEFW1]/root:
-
As far as your test above, that only tested the speed on the WAN side of the 1100 and bypassing the firewall function. Therefore, it only tells you what your wan throughput is and ignores the UTM speed of the firewall.
-
My first test earlier above ran through the firewall from the LAN side and a Windows 10 Pro client. It reflects the UTM throughput, not the raw WAN throughput going to the ISP and bypassing the firewall.
-
I thought you said your WAN was 80Mbit/sec down. How did you get 160?
The speedtest.net result I posted above was THROUGH the 1100, not FROM it.
My results are actually slower from the firewall itself since the firewall CPU is running the speedtest instead of just processing packets.
I would continue to look for something local that is the cause of the slowdown you are seeing. I know it's easy to say "When I install this device it slows down" but it there is obviously another element to this problem.
-
Have you reset to default as suggested and tested without installing any additional packages?
-
- Apparently, the ISP speed either fluctuates or is faster than we remembered.
- Backed up the config.
- Did a factory reset from the Console port.
- Initialized the WAN interface to 192.168.15.160 and added a default gateway of 192.168.15.1.
- Reinstalled the speedtest package from the console
- Did another speedtest from the command line with the following result:
[2.4.4-RELEASE][root@pfSense.localdomain]/root: speedtest-cli
Retrieving speedtest.net configuration...
Testing from Spectrum (xx.xx.xx.xx)...
Retrieving speedtest.net server list...
Selecting best server based on ping...
Hosted by Spacelink (San Diego, CA) [12.85 km]: 37.95 ms
Testing download speed................................................................................
Download: 227.87 Mbit/s
Testing upload speed................................................................................................
Upload: 23.35 Mbit/s
[2.4.4-RELEASE][root@pfSense.localdomain]/root:
-
Also did a speedtest through the Chrome browser with the following result:
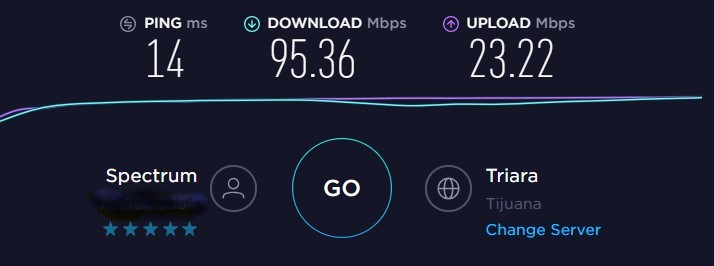
-
There was obviously something REALLY flaky with the setup or the intial configiruation when I got it. The new numbers are a lot closer to yours. I'm glad I went through this exercise.
-
Maybe test from something other than Tijuana.
-
-
Testing from ZTelco as before produces:
98.90 Mbits/sec down
23.20 Mbits/sec up -
The numbers I am seeing now are REALLY close to what they were WITHOUT the SG-1100.
I'M ECSTATIC! THANKS!
It's like the firewall isn't even there anymore speed wise.
-
Now I'm going to readd the other packages and see what happens to the speed.
-
Added pfBlocker without configuring and got the following results:
Chrome speedtest: 108.44Mbits/sec down, 23.13Mbits/sec up
Speedtest-cli: 134.95Mbits/sec down, 23.56Mbits/sec up- Then added ntopng without configuring and got the following results:
Chrome speedtest: 110.16Mbits/sec down, 23.42Mbits/sec up
Speedtest-cli: 212.10Mbits/sec down, 22.80Mbits/sec up- Then turned on pfBlocker, turned on DNSBL, and specified ALL available options under Firewall->pfBlocker->DNSBL->DNSBL Easylist->Categories. At this point the firewall rules list shows EMPTY.
Chrome speedtest: 104.17Mbits/sec down, 23.34Mbits/sec up
Speedtest-cli: 192.51Mbits/sec down, 23.40Mbits/sec upI'm completely baffled at this point. The firewall rules list should NOT be empty after turning on pfBlocker and DNSBL. DNS Resolver is enabled and pfBlocker DNSBL is set to "Unbound" for the Easylist rules so pfBlocker should be working.
By uninstalling and reinstalling pfBlocker, enabling DNSBL, and then doing a Firewall->pfBlocker->Update->Select 'Force' option->Reload, the firewall rules were readded. With everything now working properly, the data rate remains the same as item 6 above.
Everything is working great and at full wire speed now. Thanks!
-
-
Seems there needs to be some sort of handle there on what is actually expected throughput.