Sonos speakers and applications on different subnets (VLAN's)
-
@tim-mcmanus In my setup(s) I do not use VMware at the moment, so I cannot advise. In theory the switch should not play a part, when it is in the private (RFC1918) subnet(s) and pfSense is controlling these subnets. So IGMP snooping should not be needed, the IGMP proxy or PIMD should do that part.
Have you checked what multicast is send (wireshark)? That's how I analyzed that 239.255.255.0 was used by Sonos and that native IGMP proxy used by pfSense did not traversed it over the subnets. -
@tim-mcmanus yes, promiscuous mode is enable on vmware NIC, anyway I haven't problems with unicast, I can ping and have conectivity across vlans inside and outside of the vmware. So I don't understand were the multicast cannot be routed
-
@qinn thank you, I'll try to disable IGMP on these switches later on, I let you know if it's work.
-
@bull said in Sonos speakers and applications on different subnets (VLAN's):
Hi Qinn I'll try to using your guide with pim to configure a similar problem in my network with google devices and Logitech Media server, I hope that this works.
Thanks.
BullBtw could you give a description of your setup?
-
@qinn said in Sonos speakers and applications on different subnets (VLAN's):
Btw could you give a description of your setup?
I have a ISP router on bridge mode conecting directly to a vmware nic (MODEM LAN 192.168.0.1/24) this interface works as PPPOE and route to modem network. (EM1)
the other nic i have created to vnic both in vlan 4095, the first one EM0 is de MGMT Lan (192.168.1.1/24) and the other vnic EM2 is configured as vlan 4095 and I've been created 5 port in the following tagged Vlan (10,20,30,40 and 50) from 192.168.10 to 50.1 subnet.
this nic is connected to a Netgear GPT110PT in port 6 vlan 10,20,30,40,50 as tagged an 1 untagged, I have a LAGG vlan 20 too connected to a NAS. from this switch is connected another one in port 1 vlan 10,20,30,40,50 as tagged an 1 untagged to port 8.
In port 5 from this second switch, I have a Ubiquiti AP with some wifi ssid configured with vlans 30,40,50, this port also configured with vlans as 10,20,30,40,50 as tagged an 1 untagged
both swicthes have IGMP Snooping enabled, configured IGMP vlan configuration for vlan 1,30,50 (testing at the moment) with querier enable and queriers enable and configured with vlan 1,30 and 50 pointing to each router ip subnet address 1,1 for vlan 1 30.1 for vlan 30...
May be this is a little confuse without a diagram but I don't have any software to have a grafical view of my network.
Many thanks
Bull -
@bull said in Sonos speakers and applications on different subnets (VLAN's):
I don't have any software to have a grafical view of my network.
There is plenty of free software or even just websites that would allow you to draw your network.
Here are 2 you can do it in pure ascii
https://textik.com/
http://asciiflow.com/Here is decent one
https://www.gliffy.com/
another
https://creately.com/lp/network-diagram-software-onlineActual download software
https://www.yworks.com/products/yed
http://dia-installer.de/Lets not forget the office type apps that are free, openoffice, LibreOffice that have drawing - even google draw ;)
Or you take out a crayon and and a napkin and then snap a photo of it with your phone!
-
@johnpoz said in Sonos speakers and applications on different subnets (VLAN's):
Or you take out a crayon and and a napkin and then snap a photo of it with your phone!
Thanks for the suggestions, I tried to do the best I know.
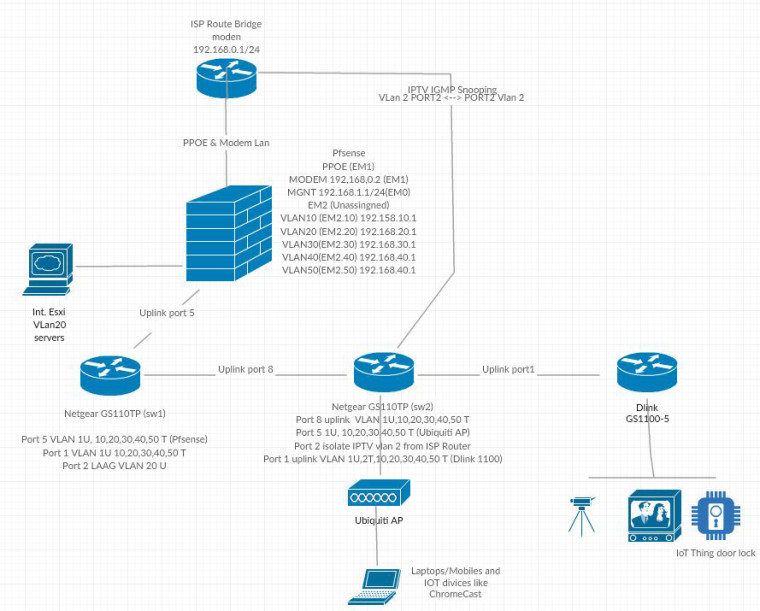 W
W -
Disable IGMP Snooping on physical Switches didn't change anything.
Is possible that the problem is that I'm using default vlan 1 as default router ip network and this vlan don't work as spected with multicasting?
I think so from vmware point of view the configuration of the vnic on vlan 4095 is correct.
many thanks
Bull -
4095 on a vswitch will pass all tags to the VMs connected to the switch.
To be honest not a fan of dicking with multicast like to feed it into other Layer 2 networks. If the companies want to be so short sighted to think that their users don't run multiple segments and a way for access through a firewall and different segments then either don't use them.. I mean how hard would it be to let the app put in the IP, and clearly lists what ports need to be allowed, etc.
Or if you really want to use them, then just put all the devices on that L2... I do this with printer - its on the one wireless network.. So if you want to print you just need to make sure your on that SSID.. Not really a big deal... For example when want to control my roku devices with my phone or tables I join the roku vlan.
-
@johnpoz I'm agree with you but looking for the future where more and more IOT devices could be connected in a home lan without any "security" control, would be necesary that the developers that works in security bring to those people that want more security in their home a tool that would be it posible. The company or solution that bring that, win the battle.
I know that is not normal that the mayority of the people had segmented the lan network in their home to have a better view/control of their devices, but how many people had an antivirus installed in their system some years ago?
I'm not want to desviate from the thread, unfortunatly this morning the multicast was working with google devices, I don't know how, I leave home and shutdown the laptop and now I cannot see the chromecast, so... I don't know where my problem is.
-
@Qinn ,only to compare with your confg. this is normal situation with "no traffic" states in the upd/multicast ?
LAN pim 192.168.1.1 -> 224.0.0.13 NO_TRAFFIC:SINGLE 148 / 0 7 KiB / 0 B LAN udp 192.168.1.240:3073 -> 255.255.255.255:6524 NO_TRAFFIC:SINGLE 451 / 0 22 KiB / 0 B LAN udp 192.168.1.240:3074 -> 255.255.255.255:35344 NO_TRAFFIC:SINGLE 451 / 0 22 KiB / 0 B LAN udp 192.168.1.100:56669 -> 192.168.1.255:32414 NO_TRAFFIC:SINGLE 315 / 0 15 KiB / 0 B LAN udp 192.168.1.100:55444 -> 192.168.1.255:32412 NO_TRAFFIC:SINGLE 315 / 0 15 KiB / 0 B LAN udp 192.168.1.104:9956 -> 192.168.1.255:9956 NO_TRAFFIC:SINGLE 79 / 0 30 KiB / 0 B ------------------------------------------------------------------- IOT udp 192.168.50.220:9956 -> 224.0.0.113:9956 NO_TRAFFIC:SINGLE 300 / 0 32 KiB / 0 B IOT udp 192.168.50.21:5353 -> 224.0.0.251:5353 NO_TRAFFIC:SINGLE 327 / 0 86 KiB / 0 B IOT udp 192.168.50.22:5353 -> 224.0.0.251:5353 NO_TRAFFIC:SINGLE 293 / 0 79 KiB / 0 BThx
Bull -
Thank you Qinn for posting this! PIMD worked for me after hours and hours of work trying to get my HEOS (Denon's version of "Sonos") working across VLANs.
Is there anything that I need to do to ensure that PIMD loads with the correct settings everytime my pfSense restarts or is updated?
-
@nick13 PIM isn't needed (or desired) for HEOS. All that is needed for HEOS is Avahi with reflection enabled. Following discovery, which is mdns based, HEOS is point to point rather than multicast.
-
@dennypage I've had Avahi installed with reflection enabled and have been unable to get it to work until I also turn on PIMD. When I kill PIMD the HEOS app quits recognizing my receivers on the other vlan.
Do you have any thoughts why that might be?
As a side note, I figured out the answer to my question that I posted by adding the PIMD start command to the config.xml file.
-
Check these things:
You have firewall interfaces in both the client subnet (where your iPhone is) and the server subnet (where the HEOS device is).
You have Avahi (2.0.0_2) with the allowed interfaces set to include both the client subnet and the server subnet.
You have "Enable" and "Enable reflection" checked in the Avahi configuration.
You do not have "Disable IPv4" checked in the Avahi configuration.
You do not have anything defined in the "Advanced settings" section of the Avahi configuration.
You have added rules to allow ptp packets from the clients to the HEOS device you are trying to control.
You have restarted or disconnected/reconnected both HEOS clients and servers after changing the any of the above.
-
@nick13 said in Sonos speakers and applications on different subnets (VLAN's):
Thank you Qinn for posting this! PIMD worked for me after hours and hours of work trying to get my HEOS (Denon's version of "Sonos") working across VLANs.
Is there anything that I need to do to ensure that PIMD loads with the correct settings everytime my pfSense restarts or is updated?
Nice that it helped you, the config file that PIMD is using will probably be removed once you update pfSense.
-
2 questions...
I have PFsense running in an esxi environment and I don't have my network adapter in promiscuous mode. I have the pcie ethernet adapter as a directpath i/o dedicated device. Essentially vmware doesnt even see the device anymore and it as if it's native to the pfsense host machine. This should be good from my understanding?
question 2: Has anyone tried this with a network cablecard tuner? I'm trying to get my hdhomerun to work with igmpproxy and pfsense doesnt seem to be sending any of the multicast traffic.
-
First of all, huge thanks to Qinn and others for figuring this out and providing instructions!
Second, I've read and followed all the instructions here and in other threads w/o any success. So, after days of trials and errors I'd like to ask for some help.
My configuration is slightly different - I need to traverse multicast for Sonos between a real no-VLAN subnet and a dedicated VLAN subnet within. I.e. there's a regular LAN where no-VLAN devices live (it's actually a Default VLAN 1 on the switch, but untagged), bound to "igb1" interface. That's where controller resides in the form of an Android app. And there's a dedicated tagged VLAN 10 for Sonos devices, bound to "igb1.10" interface. LAN on igb1 is 192.168.0.0/24 and VLAN10 on igb1.10 is 192.168.10.0/24. pfSense is 192.168.0.1 and 192.168.10.1 on each interface. Both subnets have DHCP server, both are fully open in Firewall - I can ping and send unicast traffic between those 2 subnets fine.
Now, when I configure PIMD on igb1 and igb1.10, it reports that subnet for the second one is 192.168.10, while subnet for the first one is 192.168. Which leads me to believe that PIMD somehow considers VLAN10 to be "shadowed" inside LAN, not a separate subnet and refuses to retransmit multicast between them.
I tried different combinations of "altnet" configuration specified w/o much success. After a while I see some other Android devices joining multicast groups reported by PIMD, but Sonos still doesn't work - an Android controller app on LAN can't find any Sonos device on VLAN10.
I'd like to avoid the need to tag everything on LAN to make it a dedicated VLAN subnet. Essentially that would mean VLAN 1 as a real subnet, start tagging everything, create "igb1.1" interface for it and close LAN "igb1" down. Supposedly, that would work, as reported by others - VLAN1 <-> VLAN10, igb1.1 <-> igb1.10. Unfortunately, that means extra work, lots of gear configuration and some downtime to my network.
So, I would appreciate any suggestions and ideas for how to make it work with the setup I have right now - LAN <-> VLAN10, igb1 <-> igb1.10. Thanks in advance and please let me know what you think!
-
@denix Could you post the messages you receive from PIMD and could you post the config file of PIMD
A VLAN that is not tagged is not a VLAN ;) , but tagging or not should not really matter as tagging happens when it leaves the subnet and traverses the switch.
-
@Qinn sorry if my explanation wasn't very clear. Yes, I was trying to say that LAN carries both VLAN-tagged traffic, as well as untagged.
Originally I had all Sonos speakers in a separate VLAN10 tagged subnet, while other devices including Android controller app in untagged LAN.
Tired of trying to make it work, I ended up placing WiFi devices into own VLAN40 tagged subnet. Now testing PIMD with VLAN10 <-> VLAN40 and still no luck.
VLAN10 = 192.168.10.0/24 (Sonos speakers)
VLAN40 = 192.168.40.0/24 (Android control app)pfSense has IP of x.x.x.1 on each interface. Both subnets are fully open to each other for unidirectional traffic.
Here's my config (tried many different variants of enabling/disabling different options):
phyint igb0 disable phyint igb1 disable phyint igb2 disable phyint igb3 disable phyint igb1.10 enable phyint igb1.20 disable phyint igb1.30 disable phyint igb1.40 enable bsr-candidate priority 5 rp-candidate time 30 priority 20 group-prefix 224.0.0.0 masklen 4 spt-threshold packets 0 interval 100Starting pimd -d:
debug level 0xffffffff (dvmrp_detail,dvmrp_prunes,dvmrp_routes,dvmrp_neighbors,dvmrp_timers,igmp_proto,igmp_timers,igmp_members,trace,timeout,packets,interfaces,kernel,cache,rsrr,pim_detail,pim_hello,pim_register,pim_join_prune,pim_bootstrap,pim_asserts,pim_cand_rp,pim_routes,pim_timers,pim_rpf) 22:58:33.455 pimd version 2.3.2 starting ... 22:58:33.455 Got 262144 byte send buffer size in 0 iterations 22:58:33.455 Got 262144 byte recv buffer size in 0 iterations 22:58:33.455 Got 262144 byte send buffer size in 0 iterations 22:58:33.455 Got 262144 byte recv buffer size in 0 iterations 22:58:33.455 Getting vifs from kernel 22:58:33.455 Installing igb0 (x.x.x.x on subnet x.x.x/24) as vif #0 - rate 0 22:58:33.455 Installing igb1 (192.168.0.1 on subnet 192.168) as vif #1 - rate 0 22:58:33.455 Installing igb2 (192.168.13.1 on subnet 192.168.13) as vif #2 - rate 0 22:58:33.455 Installing igb3 (192.168.255.1 on subnet 192.168.255) as vif #3 - rate 0 22:58:33.455 Installing igb1.10 (192.168.10.1 on subnet 192.168.10) as vif #4 - rate 0 22:58:33.455 Installing igb1.20 (192.168.20.1 on subnet 192.168.20) as vif #5 - rate 0 22:58:33.455 Installing igb1.30 (192.168.30.1 on subnet 192.168.30) as vif #6 - rate 0 22:58:33.455 Installing igb1.40 (192.168.40.1 on subnet 192.168.40) as vif #7 - rate 0 22:58:33.455 Getting vifs from /var/etc/pimd.conf 22:58:33.455 Local Cand-BSR address 192.168.40.1, priority 5 22:58:33.455 Local Cand-RP address 192.168.40.1, priority 20, interval 30 sec 22:58:33.455 spt-threshold packets 0 interval 100 22:58:33.455 Local static RP: 169.254.0.1, group 232.0.0.0/8 22:58:33.455 IGMP query interval : 12 sec 22:58:33.455 IGMP querier timeout : 41 sec 22:58:33.455 Interface igb0 is DISABLED; vif #0 out of service 22:58:33.455 Interface igb1 is DISABLED; vif #1 out of service 22:58:33.455 Interface igb2 is DISABLED; vif #2 out of service 22:58:33.455 Interface igb3 is DISABLED; vif #3 out of service 22:58:33.455 Interface igb1.10 comes up; vif #4 now in service 22:58:33.456 query_groups(): Sending IGMP v3 query on igb1.10 22:58:33.456 Send IGMP Membership Query from 192.168.10.1 to 224.0.0.1 22:58:33.456 SENT 36 bytes IGMP Membership Query from 192.168.10.1 to 224.0.0.1 22:58:33.456 SENT 46 bytes PIM v2 Hello from 192.168.10.1 to 224.0.0.13 22:58:33.456 Interface igb1.20 is DISABLED; vif #5 out of service 22:58:33.456 Interface igb1.30 is DISABLED; vif #6 out of service 22:58:33.456 Interface igb1.40 comes up; vif #7 now in service 22:58:33.456 query_groups(): Sending IGMP v3 query on igb1.40 22:58:33.456 Send IGMP Membership Query from 192.168.40.1 to 224.0.0.1 22:58:33.456 SENT 36 bytes IGMP Membership Query from 192.168.40.1 to 224.0.0.1 22:58:33.456 SENT 46 bytes PIM v2 Hello from 192.168.40.1 to 224.0.0.13 22:58:33.456 Interface register_vif0 comes up; vif #8 now in service Virtual Interface Table ====================================================== Vif Local Address Subnet Thresh Flags Neighbors --- --------------- ------------------ ------ --------- ----------------- 0 x.x.x.x x.x.x/24 1 DISABLED 1 192.168.0.1 192.168 1 DISABLED 2 192.168.13.1 192.168.13 1 DISABLED 3 192.168.255.1 192.168.255 1 DISABLED 4 192.168.10.1 192.168.10 1 DR NO-NBR 5 192.168.20.1 192.168.20 1 DISABLED 6 192.168.30.1 192.168.30 1 DISABLED 7 192.168.40.1 192.168.40 1 DR NO-NBR 8 192.168.10.1 register_vif0 1And here's a sample output from running pimd with -d option when there's a traffic:
Candidate Rendezvous-Point Set =============================================== RP address Incoming Group Prefix Priority Holdtime --------------- -------- ------------------ -------- --------------------- 192.168.40.1 8 224/4 20 50 169.254.0.1 0 232/8 1 65535 ------------------------------------------------------------------------------ Current BSR address: 192.168.40.1 22:37:31.848 Cache miss, src 192.168.40.10, dst 239.255.255.250, iif 7 22:37:31.848 create group entry, group 239.255.255.250 22:37:31.848 create source entry, source 192.168.40.10 22:37:31.848 move_kernel_cache: SG 22:37:32.326 Cache miss, src 192.168.10.16, dst 239.255.255.250, iif 4 22:37:32.326 create source entry, source 192.168.10.16 22:37:32.326 move_kernel_cache: SG 22:37:32.340 Cache miss, src 192.168.10.15, dst 239.255.255.250, iif 4 22:37:32.340 create source entry, source 192.168.10.15 22:37:32.340 move_kernel_cache: SG 22:37:32.660 Cache miss, src 192.168.10.14, dst 239.255.255.250, iif 4 22:37:32.660 create source entry, source 192.168.10.14 22:37:32.660 move_kernel_cache: SG 22:37:32.916 Cache miss, src 192.168.10.13, dst 239.255.255.250, iif 4 22:37:32.916 create source entry, source 192.168.10.13 22:37:32.916 move_kernel_cache: SG 22:37:33.005 Cache miss, src 192.168.10.21, dst 239.255.255.250, iif 4 22:37:33.005 create source entry, source 192.168.10.21 22:37:33.005 move_kernel_cache: SG 22:37:33.185 Cache miss, src 192.168.10.17, dst 239.255.255.250, iif 4 22:37:33.185 create source entry, source 192.168.10.17 22:37:33.185 move_kernel_cache: SG 22:37:34.274 Cache miss, src 192.168.40.10, dst 239.255.255.250, iif 7 Virtual Interface Table ====================================================== Vif Local Address Subnet Thresh Flags Neighbors --- --------------- ------------------ ------ --------- ----------------- 0 x.x.x.x x.x.x/24 1 DISABLED 1 192.168.0.1 192.168 1 DISABLED 2 192.168.13.1 192.168.13 1 DISABLED 3 192.168.255.1 192.168.255 1 DISABLED 4 192.168.10.1 192.168.10 1 DR NO-NBR 5 192.168.20.1 192.168.20 1 DISABLED 6 192.168.30.1 192.168.30 1 DISABLED 7 192.168.40.1 192.168.40 1 DR NO-NBR 8 192.168.10.1 register_vif0 1 Vif SSM Group Sources Multicast Routing Table ====================================================== --------------------------------- (*,*,G) ------------------------------------ Number of Groups: 0 Number of Cache MIRRORs: 0 ------------------------------------------------------------------------------The log above clearly shows some traffic where 192.168.10.13-17 are Sonos speakers and 192.168.40.10 is my Android phone with Sonos control app trying to find them. I still get "We can't connect to Sonos". And somehow Multicast Routing Table is empty anyway.
Any ideas? Thanks!

