XG-7100 not passing untagged LAN traffic on internal vlan other than 4091
-
https://www.netgate.com/resources/videos/configuring-netgate-appliance-integrated-switches-on-pfsense-244.html
-Rico
-
I reviewed the video and didn't find any information relating to the issue I am describing. That said, It is definitely good material for understanding how to configure the integrated switch XG-7100.
-
Maybe I understand wrong what you are doing... but on my XG-7100 I totally wiped VID 4091 and everything is working smooth so there can't be anything hardcoded.
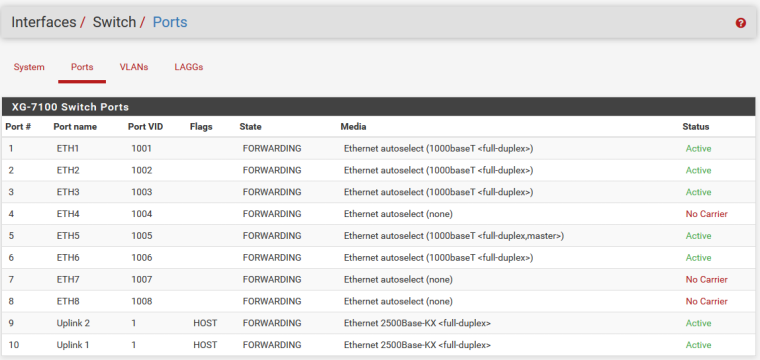
-Rico
-
All I can say is that if I change the LAN interface to operate on lagg0.3000 and also change ETH3/ETH7 (my switch uplinks, STP is blocking one of these) to be VID 3000 then it stops passing traffic. Screenshots of the current config are below. In the end I'm mostly just trying to do my part for the community by reporting this issue. I will be trying to link my LAN to the firewall tagged instead of untagged over the next few days and if that works properly then this will be a non-issue for me.
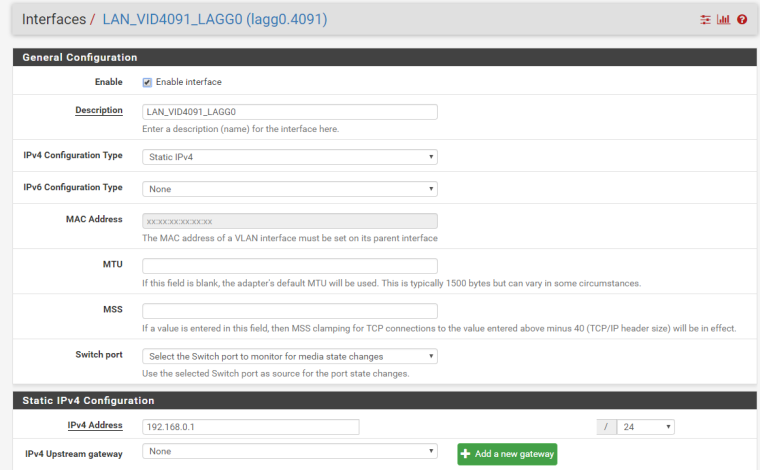
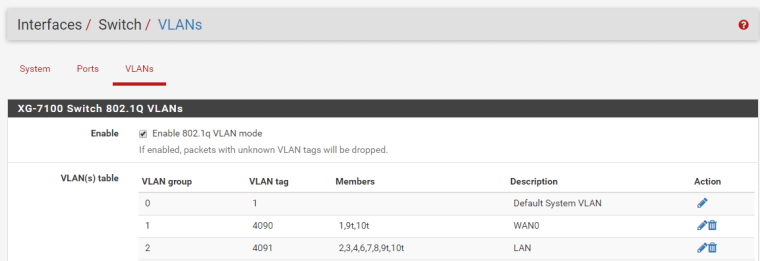
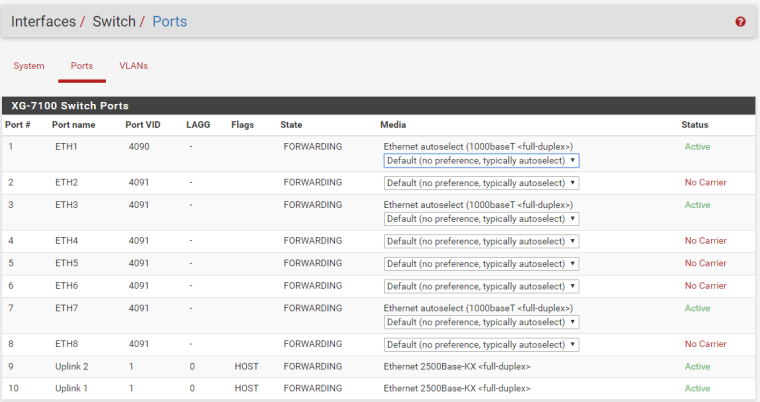
-
How about you show the switch config when it doesn't work. That looks like the default config.
- Remove a port from VLAN group 2, say port 8. VLAN group 2 should look like this: 2,3,4,5,6,7,9t,10t
- Create VLAN Group 3, set the VLAN tag to 3000, add these ports: 8,9t,10t
- Edit the switch ports. Click on the Port VID for port 8 and change it to 3000
- Add a pfSense VLAN 3000 on LAGG0
- Create a NEW pfSense interface assigned to VLAN 3000 on lagg0
- Edit the new interface, enable it, and give it a new numbering like 192.168.2.1/24.
- Enable a DHCP server on the new interface with a pool in the right scope.
- Add a firewall rule on the new interface to pass traffic from those hosts. (Copy the LAN rule and change the interface and source subnet.)
Connect a DHCP workstation to switch port 8. What happens?
After you verify that is working you can move switch ports to either untagged VLAN (4091 or 3000) by changing the VLAN Group and the Port VID to reflect what you want.
-
Unfortunately this system is already in production so I cannot make changes on this hardware until scheduled downtime in a few weeks. I can say that I have already attempted the configuration you are describing but I did not have lagg0.3000 and lagg0.4091 operating at the same time. I only had one or the other. Each time I tried switching between the two I would completely remove the VLAN and the LAN interface and start from scratch. I even tried rebooting the system after removing the VLAN and interface so I was rebuilding it from a clean boot.
I will be setting up a new site on the same hardware this Sunday and can try to replicate the issue then and can explicitly follow your suggested instructions.
-
Well then you have to do the change from WAN Port VID 4090.
You can‘t be connected to LAN 4091 while you change the whole group, this will cut you off.-Rico
-
Not to sound rude, but if you had done that exact configuration it would have worked. Even with only VLAN 3000.
The very reason I suggested this method is because you could perform this test without impacting the users on VLAN 4091 as long as there is an unused switchport to test with. I chose port 8 because it is No carrier in the last screen shots.
Like with any switch, it is possible to lock yourself out while configuring from an interface being changed. Making these changes logged in via WAN or VPN, or out-of-band, is always a preferred method.
What are the first three digits of the serial number of the XG-7100 in question?
-
No worries, no rudeness received. I understand that you believe it would have worked and I also believe it should have worked which is why I was initially suggesting that this could be a bug. Working with pfSense and VLANs is far from a new thing for me but I also don't consider myself above making stupid mistakes.
The larger issues with making the suggested changes is that I don't have IT staff on site until the aforementioned scheduled downtime so I don't have anyone present to plugin a laptop.
Changes have been done via WAN and/or an OpenVPN connection going out of the WAN.
I should be able to re-check this issue on the exact same hardware at a different site that I'm bringing up on Sunday and can provide exact screenshots of the problematic config (I'll grab the XML config while I am at it) as well as have someone plugin a laptop to a switch port on the device while VID 4091 and VID 3000 are coexisting. As I mentioned before I never had both VLANs coexisting while I came across this issue so I will also be testing without the VLANs coexisting as that is when I previously experienced the issue.
-
So I'm bringing up my other site now and was able to reproduce my issue on different but identical hardware. The serial number of the firewall at this site begins with 143.
Again I switched lagg0.4091 to lagg0.3000 and switched the VID configured on the internal switch to 3000. Again I lost connectivity to the external switch plugged in to ETH2. A laptop plugged in to ETH3 also could not contact the firewall nor get a DHCP lease. I noticed on the ports tab of the internal switch configuration that 4091 was still listed as the port VID for all ports. I updated the VID there to be 3000 and things started working.
I was under the assumption that setting a port to be untagged on a VLAN on the internal switch configuration VLAN tab would automatically update the port VID but that assumption looks like is incorrect. This is definitely not a bug and was a config issue on my end. That said, why wouldn't the port VID be updated when I set a port to be untagged on a VLAN in the VLAN tab? I think the configuration for this may be able to be simplified a bit.
Thanks for everyone chiming in and sorry to waste time on this.
-
Some switches do that and some don't.
This requires them both to be set to create an untagged port.
There are certain circumstances where having them be different can be beneficial. For instance you can use "asymmetric VLANs" to create isolated switch ports so there needs to be a way to set them differently.