SG-1100 No VLAN Communication
-
Those firewall rules should certainly allow communication between the interfaces.
What errors are actually reported when you run those pings?
I assume you can reach the webgui from the LAN subnet client since you posted screenshots. Can you ping the WAN interface from the LAN client?
Try going to Diagnostics > Ping in the webgui. Ping the LAN client with the default settings. If that succeeds try changing the source IP to one of the other interfaces. If that fails there is probably a subnet mismatch somewhere. The firewall will never block that so if the pings don't return it is either the client not responding (a local firewall on the client perhaps) or it is unable to respond as it has no route or a bad route.
Steve
-
@stephenw10 From VPN to LAN: no errors are reported. From LAN to VPN, an ICMP request timeout occurs.
Pinging from the webgui, identical results happen there. Firewall to VPN results in return pings. From Firewall to LAN, I receive the replies. Verified the subnet for a 192.168 address which would be /24.
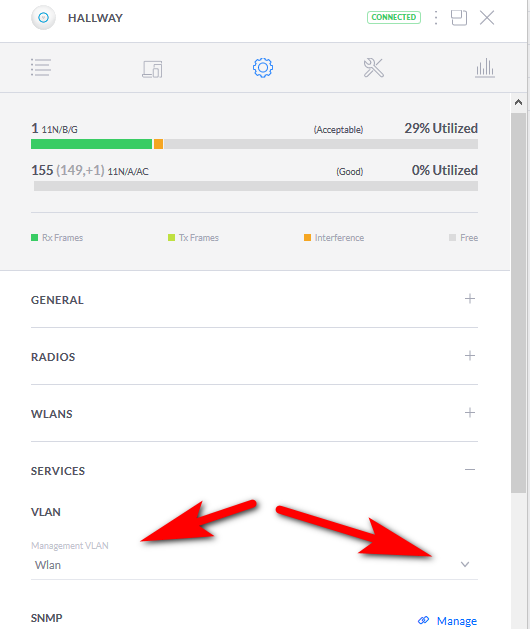
For some reason, I have a feeling that the LAN VLAN is not properly tagging its VLAN but I don't have definitive proof of that. I'll grab a PCAP and see what the packets say.
Edit: Grabbed a PCAP. Just a preface, I'm still working through my SANS503/practicing so excuse any of my ignorance and feel free to correct me.
Looking at the Link Layer, there definitely is no VLAN being tagged which explains why it is not being routed properly. The source MAC is followed directly by the type 0x0800 (IPv4 Header) rather than 0x8100 (VLAN Header0. This both makes sense and doesn't make sense since I would assume a VLAN Header would still have to be present in how the firewall is setup (each port is separated by a VLAN).
My next question is, how do I fix that? I could make another VLAN for the main network that would be the LAN and it should work (VLANs can ping other VLANs which I just tested by pinging the VPN VLAN to the IOT VLAN) but that seems a little sloppy.
-
I'm beginning to think that the VLAN tag for the LAN also needs to be on the switch (now that I type that, I feel a tad bit dumb that I didn't think of that sooner). Problem being, Ubiquiti only allows VLANs up to 4009 on their switch which suggests that my only option is to create another VLAN (for instance name it MainNet with a VLAN tag of 14) give it a different IP range and then use that as the "LAN". Reason I feel this is the best option is because, by changing the VLAN tag in the Switch or the VLAN Assignment tab, it will effectively lock out the firewall since there would be a VLAN mismatch between either the Switch tab or the VLAN Assignment tab and not be able to route any communications to the LAN.
@stephenw10 mind sanity checking/verifying that my plan makes sense?
-
If there is a switch between the AP and the pfSense LAN port, YES, there need to be tags there too.
You can put that untagged 4090 traffic on any VLAN on the switch that you want. Just make the VLAN id the PVID on that switch port.
For consistency, it would be best if that is 4091.
You can either:
Run with different untagged VLAN IDs on the LAN network which should work fine.
If the switch really commandeers VLANs 4010 - 4094 you can make a new untagged VLAN on the pfSense switch, assign LAN to that, and make the same untagged VLAN on the switch port. -
@derelict Are there any downsides to creating another VLAN that has tagging on both the 0 member and the 2 member? It seems that the only way that I can get the VLANs to work is in that configuration.
-
Not really, you can add as many VLANs that way as you want, within reason.
You can reassign the LAN to that new VLAN once it's added there and it will be tagged out of the 'LAN' port on the 1100.
You will be locked out when you make that switch though so be sure to be connected via one of the other VLANs before you do it.
Steve
-
@stephenw10 After adding another VLAN named MainNet and adding the proper firewall rules, I still can't ping another network. In fact, somehow doing this leaves the communications worse off as now the VPN VLAN can't ping the new MainNet VLAN.
Same situation where the system pinging does not have a VLAN ID in the packet.
Any suggestion.
Below is the new switch configuration, VLAN assignments, and the new VLANs on the switch:
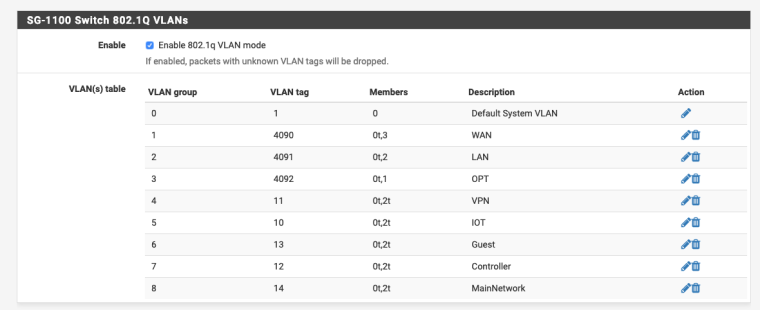
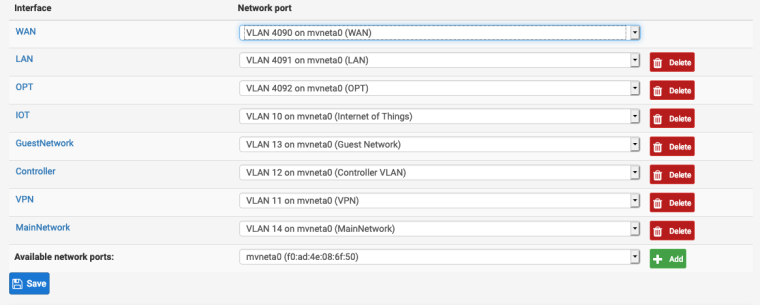
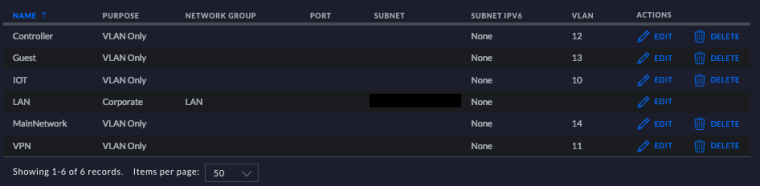
-
I went ahead and did a restart and that seems to work (the configuration of a new VLAN for the main network so it can be placed in the Switch's VLAN table. I think all should be good: I'm able to receive pings from other hosts on each network.
-
The new problem is, it does not seem that you can have a Unifi switch on a VLAN. I wasn't really expecting there to be so many caveats with the SG-1100 when I bought it.
-
@zachzez said in SG-1100 No VLAN Communication:
it does not seem that you can have a Unifi switch on a VLAN
Huh?? What exact switch are you running and what firmware. Their management vlan before had to be untagged but quite some time ago they changed firmware (atleast on their AP) to support tagged management vlans.. So have to assume you can do that with their switches as well.
And even if mangement vlan has to be untagged it simple enough to accomplish that.
Users scream they want switch ports switch ports on the router, how do I bridge I want more than 1 port in the same vlan.. Then they get what they ask for and what they really want is actual interfaces ;)
-
@johnpoz I can only speak for my short time in the industry so I don't think I was around when Unifi had a management VLAN. When I assigned a VLAN to the controller, everything began to fall apart (the switch and AP refused to acknowledge the controller and gradually went down hill from there) to the extent that I just started fresh: reset the switch, reset the firewall (god knows what else I messed up there so might as well) and put everything back to a flat network.
The controller works great on an untagged network, once I moved things to a tagged network is where it got a bit iffy. Also, now it seems that the LAN is functioning and routing properly after a reset of the firewall (full reinstall), so maybe something got misconfigured there as well.
Just my experience so far. I am running their 8 port POE with their most recent firmware.
I agree on the actual interfaces. I've never really been in the mindset of using a firewall as a switch as well. That's what a switch is for :D.
-
You can't please all the people all the time.

But this should work. It's clearly a bit more work setting it up for tagged traffic leaving the ports but certainly should be possible.
Steve
-
@zachzez said in SG-1100 No VLAN Communication:
The new problem is, it does not seem that you can have a Unifi switch on a VLAN. I wasn't really expecting there to be so many caveats with the SG-1100 when I bought it.
That has nothing to do with the SG-1100. By default all interfaces are untagged. If anything it's a limitation of the switch because you should be able to put the management interface on any VLAN you want.
If you want to start tagging management VLANs, ANY managed switch is going to have to be configured correctly, the one in the SG-1100 included.
-
@derelict Either way, I have it working on the untagged LAN after a reinstall of the pfSense software and all should be good.
-
So again unifi management vlan can be tagged or untagged.. They added it to the AP something like 6 months or more ago.. The switches could use a tagged management vlan before the AP could.
So your management vlan can be either tagged or untagged.. Before they made the change you could not set a tagged vlan and it had to be untagged. As long as your running somewhat current controller and switch firmware you can do it either way.