DNS Resolver Log Error sending queries to 1.1.1.1
-
We have updated the blog post with Quad9 settings https://www.netgate.com/blog/dns-over-tls-with-pfsense.html
Hi,
First of all, thanks for the Tips&Tricks guide :)
DNS over TLS doesn't work for me. I run into this issue and lost Internet to.
Apr 5 18:29:19 unbound 7412:0 info: start of service (unbound 1.6.. Apr 5 18:29:19 unbound 7412:0 error: duplicate forward zone . ignored. Apr 5 18:29:19 unbound 7412:3 error: duplicate forward zone . ignored. Apr 5 18:29:19 unbound 7412:2 error: duplicate forward zone . ignored. Apr 5 18:29:19 unbound 7412:1 error: duplicate forward zone . ignored. Apr 5 18:29:19 unbound 7412:0 notice: init module 1: iterator Apr 5 18:29:19 unbound 7412:0 notice: init module 0: validator Apr 5 18:29:19 unbound 7412:0 notice: Restart of unbound 1.6.8. Apr 5 18:29:19 unbound 7412:0 info: server stats for thread 3: requestlist max 0 avg 0 exceeded 0 jostled 0 Apr 5 18:29:19 unbound 7412:0 info: server stats for thread 3: 0 queries, 0 answers from cache, 0 recursions, 0 prefetch, 0 rejected by ip ratelimiting Apr 5 18:29:19 unbound 7412:0 info: server stats for thread 2: requestlist max 0 avg 0 exceeded 0 jostled 0 Apr 5 18:29:19 unbound 7412:0 info: server stats for thread 2: 0 queries, 0 answers from cache, 0 recursions, 0 prefetch, 0 rejected by ip ratelimiting Apr 5 18:29:19 unbound 7412:0 info: server stats for thread 1: requestlist max 0 avg 0 exceeded 0 jostled 0 Apr 5 18:29:19 unbound 7412:0 info: server stats for thread 1: 0 queries, 0 answers from cache, 0 recursions, 0 prefetch, 0 rejected by ip ratelimiting Apr 5 18:29:19 unbound 7412:0 info: server stats for thread 0: requestlist max 0 avg 0 exceeded 0 jostled 0 Apr 5 18:29:19 unbound 7412:0 info: server stats for thread 0: 0 queries, 0 answers from cache, 0 recursions, 0 prefetch, 0 rejected by ip ratelimiting Apr 5 18:29:19 unbound 7412:0 info: service stopped (unbound 1.6.. Apr 5 18:29:19 unbound 7412:0 info: start of service (unbound 1.6.. -
So when your resolver does not know a host's IP because it is not cached, where does it forward the query?
The root servers, of course.
https://en.wikipedia.org/wiki/Root_name_server
-
So when your resolver does not know a host's IP because it is not cached, where does it forward the query? No need to get upset, I am just asking a question!
promo, just ignore the passive-aggressive tone. Don't worry about it :)
“Your greatness is measured by your kindness; your education and intellect by your modesty; your ignorance is betrayed by your suspicions and prejudices, and your real caliber is measured by the consideration and tolerance you have for others.” ~William J.H. Boetcker
Unbound is a DNS resolver, which means that it doesn't necessarily need to forward queries to another DNS resolver/forwarder such as Quad9, Google, Cloudflare, OpenDNS, etc. Instead it can query "root hints" servers by itself without any of the previously mentioned providers in between. There is a trade in that process, root hints can be really slow responding to queries. With that in mind, different providers (such as the ones above mentioned and others) put DNS servers closer to you to speed things up. Since their resources is so vast and their services is generally used by millions of users, chances are that your query will most likely hit their cache instead of having to go back to "root hints" to pull a record; which dramatically increases DNS resolution speed, translated into faster browsing experience and so on.
Implementing DNSSEC and querying "root hints" reduces the chances of getting poisoned or bogus responses. Yet it does not make your DNS immune to eavesdropping. Anyone (specially your ISP) "listening" on the network for DNS queries can see which sites you're visiting by looking at your DNS queries (DNS isn't encrypted by default), for example.
Using services such as Cloudflare, Quad9 and others, may in fact help you escape the eavesdropping by implementing DNS over TLS or HTTPS on top of speeding up your DNS resolution. Yet your DNS queries are at the mercy of the upstream provider. The trade in this case is basically a matter of "trust" in the provider you choose to forward your queries to.
That's the watered down version :)
-
@rafaelr:
So when your resolver does not know a host's IP because it is not cached, where does it forward the query? No need to get upset, I am just asking a question!
promo, just ignore the passive-aggressive tone. Don't worry about it :)
“Your greatness is measured by your kindness; your education and intellect by your modesty; your ignorance is betrayed by your suspicions and prejudices, and your real caliber is measured by the consideration and tolerance you have for others.” ~William J.H. Boetcker
Unbound is a DNS resolver, which means that it doesn't necessarily need to forward queries to another DNS resolver/forwarder such as Quad9, Google, Cloudflare, OpenDNS, etc. Instead it can query "root hints" servers by itself without any of the previously mentioned providers in between. There is a trade in that process, root hints can be really slow responding to queries. With that in mind, different providers (such as the ones above mentioned and others) put DNS servers closer to you to speed things up. Since their resources is so vast and their services is generally used by millions of users, chances are that your query will most likely hit their cache instead of having to go back to "root hints" to pull a record; which dramatically increases DNS resolution speed, translated into faster browsing experience and so on.
Implementing DNSSEC and querying "root hints" reduces the chances of getting poisoned or bogus responses. Yet it does not make your DNS immune to eavesdropping. Anyone (specially your ISP) "listening" on the network for DNS queries can see which sites you're visiting by looking at your DNS queries (DNS isn't encrypted by default), for example.
Using services such as Cloudflare, Quad9 and others, may in fact help you escape the eavesdropping by implementing DNS over TLS or HTTPS on top of speeding up your DNS resolution. Yet your DNS queries are at the mercy of the upstream provider. The trade in this case is basically a matter of "trust" in the provider you choose to forward your queries to.
That's the watered down version :)
Exactly what I was leading up to! ;)
-
Just want to say that I niether could get Cloudflare to work when DNS over tls, but Quad9 works.
Haven't looked into logs yet, just that I seemed able to ping sites from within Pfsense, but not from my desktop and other.
-
Just want to say that I niether could get Cloudflare to work when DNS over tls, but Quad9 works.
Haven't looked into logs yet, just that I seemed able to ping sites from within Pfsense, but not from my desktop and other.
Same here.
-
I was reading a post on one of the forums and some there seems to think this is a pfsense issue with the Cloudflare certificate.
I'm not sure what you read, but Cloudflare person said clearly:
Thanks for the report! This is going to be fixed in the next upgrade that's being rolled out.
There was an interop issue in the last upgrade with Unbound as it sends the frame size and the actual DNS message in two separate packets instead of both at once.From: https://community.cloudflare.com/t/1-1-1-1-was-working-but-not-anymore/15136/4
Just to circle back, the above CloudFlare community post indicates a fix was pushed on the CF side to resolve the problem sometime on the 5th.
Indeed, as of today, I switched back to the CloudFlare resolvers on 853, and appear to be up and running now.
-
Since both provide a good service I left both in the config. Until I run into an issue it provides me with a backup. If you didn't know, the first line after server: is due to pfBlockerng.
server:
include: /var/unbound/pfb_dnsbl.*conf
forward-zone:
name: "."
forward-ssl-upstream: yes
forward-addr: 1.1.1.1@853
forward-addr: 1.0.0.1@853
forward-addr: 9.9.9.9@853
forward-addr: 149.112.112.112@853
forward-addr: 2606:4700:4700::1111@853
forward-addr: 2606:4700:4700::1001@853
forward-addr: 2620:fe::fe -
-
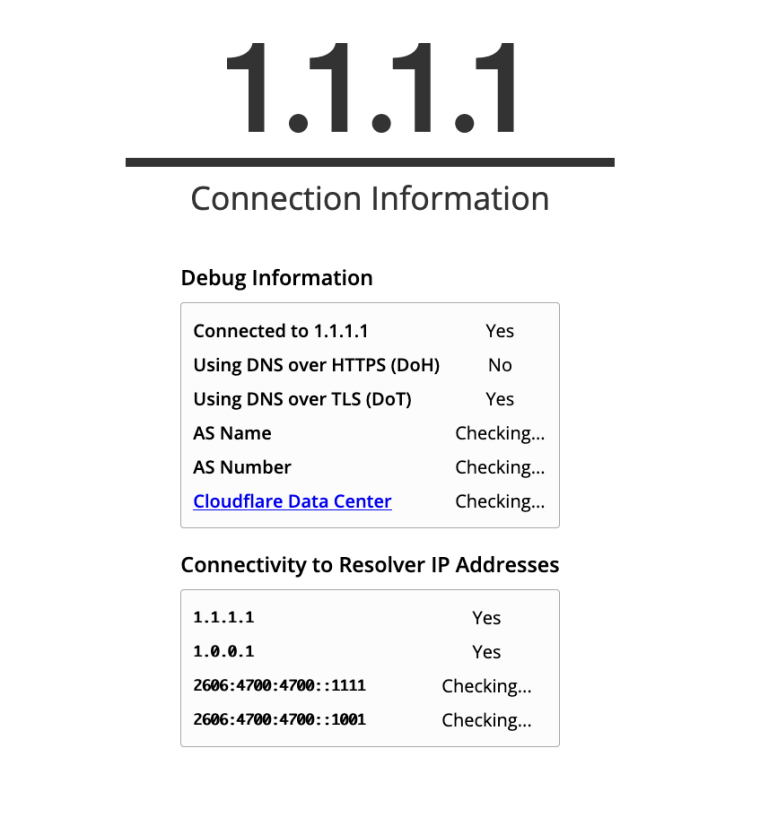
I'm trying to use DNS over TLS using Cloudflare's servers. DNS appears to work -- but Cloudflare's page indicates it isn't.
Thoughts?
-
What's URL to this test page ?
-
"page" is a link in my post above.
-
It was blocked by pfbNG for some reason
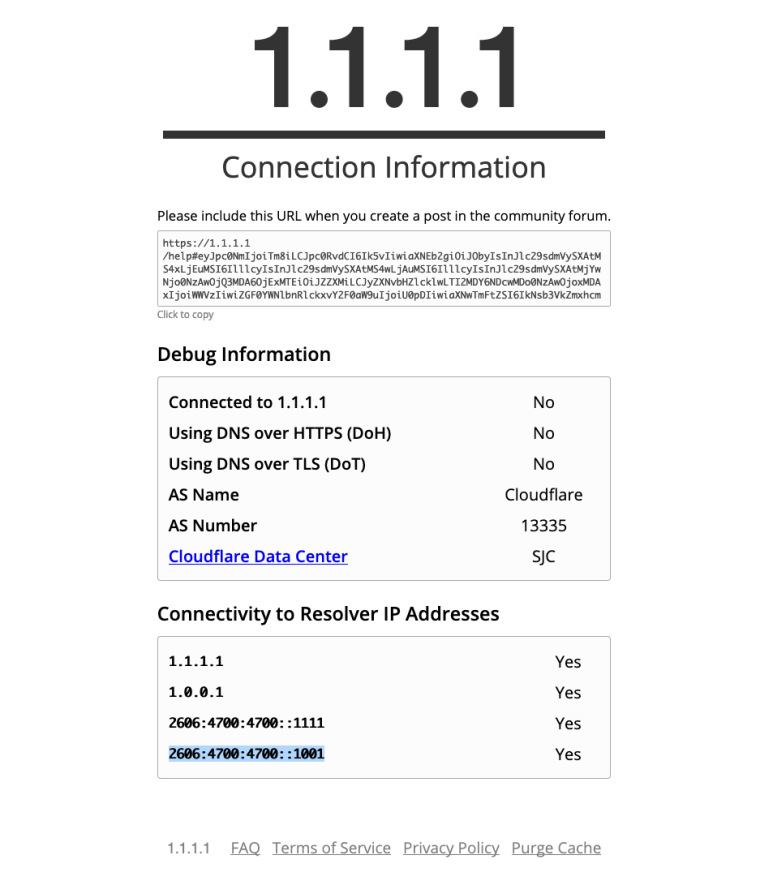
I see that page work for me https://snag.gy/oNvPsI.jpg
-
Steve W. had me turn off "Enable DNSSEC" in the resolver, and it works for me now too. But that's not a solution. I'm perplexed -- because in my previous router, I was using DoH (through dnscrypt-proxy) and DNSSEC (through pihole), and that page looked fine. I certainly don't want to give up DNSSEC. If Cloudflare's page is just broken for some reason, ok -- I'd like to undertstand what's going on here. And also the proper way to verify DoT and DNSSEC are working. I can see traffic on port 853 to the external DNS servers, I suppose that's enough? But when I use "dig +dnssec" on a local client (with DNSSEC enabled on the resolver of course), I'm not seeing any of the DNSSEC parts of the response that I used to see.
-
Perplexing is that the following link indicates DNSSEC is working even when it's disabled in the resolver:
https://dnssec.vs.uni-due.de/
-
If I shut down dnssec in the resolver :
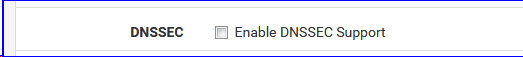
the little guy isn't happy anymore :

Please note that I use the resolver as a resolver. I'm not forwarding anything to anybody.
-
See comments from this thread https://forum.netgate.com/topic/140545/tcp-error-for-address-xxxx-port-853/4
"2nd you have dnssec enabled in forwarding mode - zero reason to do that.. whole thread about it recently where someone put together guide on setting up dns and tls.. When you forwarder to a resolver, if it supports dnssec its already doing it.. So you do not have to click that check box."
-
@gertjan If you're not forwarding to anybody, I presume that means you're talking directly to the root servers for queries you can't resolve directly? And if so, how are you doing so securely, since "Use SSL/TLS for outgoing DNS Queries to Forwarding Servers" appears to only be for forwarding servers?
-
@chudak Any pointers to the " guide on setting up dns and tls" that thread references?
-
And while I'm seeing DoT working now, that Cloudflare page takes a long time to come back with answers for AS Name, AS Number and the Cloudflare Data Center -- and eventually indicates that it has no connectivity to Cloudflare's IPv6 resolver IP addresses.