IPSec mobile VPN using IKEv2 with EAP-MSCHAPv2
-
Hello,
I have new appliance running v2.4.4-RELEASE-p2, clean install and a basic setup with WAN/LAN interfaces.
I am trying to setup a VPN for mobile clients and running into an issue with authentication.
I have followed the step by step instructions in both:
But always get a "User authentication failed" message on all three native clients; iOS 12.1.4, macOS 10.14.3, and Windows 10. CA certificate is installed on all devices per the instructions.
Below is the IPSec log (WAN IP and corresponding DNS name are masked, but both are properly setup and active):
Feb 19 04:38:42 charon 09[IKE] <2> IKE_SA (unnamed)[2] state change: CREATED => CONNECTING Feb 19 04:38:42 charon 09[CFG] <2> selecting proposal: Feb 19 04:38:42 charon 09[CFG] <2> no acceptable DIFFIE_HELLMAN_GROUP found Feb 19 04:38:42 charon 09[CFG] <2> selecting proposal: Feb 19 04:38:42 charon 09[CFG] <2> no acceptable DIFFIE_HELLMAN_GROUP found Feb 19 04:38:42 charon 09[CFG] <2> selecting proposal: Feb 19 04:38:42 charon 09[CFG] <2> no acceptable DIFFIE_HELLMAN_GROUP found Feb 19 04:38:42 charon 09[CFG] <2> selecting proposal: Feb 19 04:38:42 charon 09[CFG] <2> no acceptable ENCRYPTION_ALGORITHM found Feb 19 04:38:42 charon 09[CFG] <2> selecting proposal: Feb 19 04:38:42 charon 09[CFG] <2> no acceptable ENCRYPTION_ALGORITHM found Feb 19 04:38:42 charon 09[CFG] <2> received proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/ECP_256, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1536, IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024 Feb 19 04:38:42 charon 09[CFG] <2> configured proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1024 Feb 19 04:38:42 charon 09[CFG] <2> looking for IKEv2 configs for 39.###.###.136...172.56.40.67 Feb 19 04:38:42 charon 09[CFG] <2> candidate: %any...%any, prio 24 Feb 19 04:38:42 charon 09[CFG] <2> candidate: 39.###.###.136...%any, prio 1052 Feb 19 04:38:42 charon 09[IKE] <2> no matching proposal found, trying alternative config Feb 19 04:38:42 charon 09[CFG] <2> selecting proposal: Feb 19 04:38:42 charon 09[CFG] <2> proposal matches Feb 19 04:38:42 charon 09[CFG] <2> received proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/ECP_256, IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_1536, IKE:AES_CBC_128/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024, IKE:3DES_CBC/HMAC_SHA1_96/PRF_HMAC_SHA1/MODP_1024 Feb 19 04:38:42 charon 09[CFG] <2> configured proposals: IKE:AES_CBC_128/AES_CBC_192/AES_CBC_256/CAMELLIA_CBC_128/CAMELLIA_CBC_192/CAMELLIA_CBC_256/3DES_CBC/HMAC_SHA2_256_128/HMAC_SHA2_384_192/HMAC_SHA2_512_256/HMAC_SHA1_96/AES_XCBC_96/AES_CMAC_96/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_AES128_CMAC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048, IKE:AES_GCM_16_128/AES_GCM_16_192/AES_GCM_16_256/AES_GCM_12_128/AES_GCM_12_192/AES_GCM_12_256/AES_GCM_8_128/AES_GCM_8_192/AES_GCM_8_256/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_AES128_CMAC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048 Feb 19 04:38:42 charon 09[CFG] <2> selected proposal: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048 Feb 19 04:38:42 charon 09[IKE] <2> local host is behind NAT, sending keep alives Feb 19 04:38:42 charon 09[IKE] <2> remote host is behind NAT Feb 19 04:38:42 charon 09[IKE] <2> sending cert request for "CN=bcpivpnca, C=US, ST=Massachusetts, L=Boston, O=BCPI, OU=Datacenter" Feb 19 04:38:42 charon 09[ENC] <2> generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(FRAG_SUP) N(MULT_AUTH) ] Feb 19 04:38:42 charon 09[NET] <2> sending packet: from 39.###.###.136[500] to 172.56.40.67[58552] (473 bytes) Feb 19 04:38:42 charon 09[NET] <2> received packet: from 172.56.40.67[65496] to 39.###.###.136[4500] (528 bytes) Feb 19 04:38:42 charon 09[ENC] <2> unknown attribute type (25) Feb 19 04:38:42 charon 09[ENC] <2> parsed IKE_AUTH request 1 [ IDi N(INIT_CONTACT) N(MOBIKE_SUP) IDr CPRQ(ADDR DHCP DNS MASK ADDR6 DHCP6 DNS6 (25)) N(ESP_TFC_PAD_N) N(NON_FIRST_FRAG) SA TSi TSr ] Feb 19 04:38:42 charon 09[CFG] <2> looking for peer configs matching 39.###.###.136[bcp5.############.com]...172.56.40.67[2607:fb90:284b:50df:808:910:9e73:4625] Feb 19 04:38:42 charon 09[CFG] <2> candidate "bypasslan", match: 1/1/24 (me/other/ike) Feb 19 04:38:42 charon 09[CFG] <2> candidate "con-mobile", match: 20/1/1052 (me/other/ike) Feb 19 04:38:42 charon 09[CFG] <2> ignore candidate 'con-mobile' without matching IKE proposal Feb 19 04:38:42 charon 09[CFG] <bypasslan|2> selected peer config 'bypasslan' Feb 19 04:38:42 charon 09[IKE] <bypasslan|2> peer requested EAP, config unacceptable Feb 19 04:38:42 charon 09[CFG] <bypasslan|2> no alternative config found Feb 19 04:38:42 charon 09[IKE] <bypasslan|2> processing INTERNAL_IP4_ADDRESS attribute Feb 19 04:38:42 charon 09[IKE] <bypasslan|2> processing INTERNAL_IP4_DHCP attribute Feb 19 04:38:42 charon 09[IKE] <bypasslan|2> processing INTERNAL_IP4_DNS attribute Feb 19 04:38:42 charon 09[IKE] <bypasslan|2> processing INTERNAL_IP4_NETMASK attribute Feb 19 04:38:42 charon 09[IKE] <bypasslan|2> processing INTERNAL_IP6_ADDRESS attribute Feb 19 04:38:42 charon 09[IKE] <bypasslan|2> processing INTERNAL_IP6_DHCP attribute Feb 19 04:38:42 charon 09[IKE] <bypasslan|2> processing INTERNAL_IP6_DNS attribute Feb 19 04:38:42 charon 09[IKE] <bypasslan|2> processing (25) attribute Feb 19 04:38:42 charon 09[IKE] <bypasslan|2> received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding Feb 19 04:38:42 charon 09[IKE] <bypasslan|2> peer supports MOBIKE Feb 19 04:38:42 charon 09[ENC] <bypasslan|2> generating IKE_AUTH response 1 [ N(AUTH_FAILED) ] Feb 19 04:38:42 charon 09[NET] <bypasslan|2> sending packet: from 39.###.###.136[4500] to 172.56.40.67[65496] (80 bytes) Feb 19 04:38:42 charon 09[IKE] <bypasslan|2> IKE_SA bypasslan[2] state change: CONNECTING => DESTROYINGAny ideas as to what may be wrong?
Thanks in advance!
-
@bcpi
Hey
Check IKE proposal on the PFSense side
Error
Feb 19 04:38:42 charon 09[CFG] <2> ignore candidate 'con-mobile' without matching IKE proposalselected proposal: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/MODP_2048
It seems that PFSense (conn-mobile) does not have such
therefore, strongswan ignores mobile connection settings and tries to connect via bypasslan -
@konstanti Thank you.
It was indeed P1/P2 proposal issues. Adding 3DES/SHA1 to both allows the connection, thought I am not sure that's the ideal solution.
I am not using StrongSwan (yet), just trying the native macOS and iOS clients first. They can now connect, but I'd like to have a split VPN setup (only LAN traffic thru the tunnel), but both seem to be sending all traffic through. Any fixes for this you can suggest?
-
https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/ikev2-with-eap-tls.html?highlight=vpn
Check your P2 settings, bet you have local network = 0.0.0.0/0 set.
-
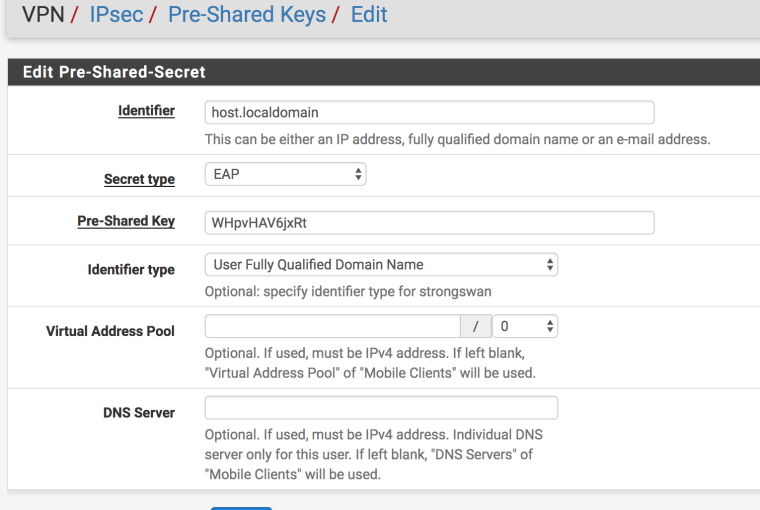
Hi, for the Windows 10 client, you might want to set up the connection via PowerShell (Add-VpnConnection, Set-VpnConnection). The crypto parameters cannot be specified via the GUI.
-
@nogbadthebad: I have it as "LAN subnet" only, which allows me to get to the local LAN ok. But it seems all other internet traffic is going thru the tunnel and ends up being blocked.
@Abbys: Thanks, will do.
-
Got it working finally...
-
Routing all traffic to VPN "issue" was actually something else... Specifying the local domain in Mobile Clients > DNS Default Domain, resolved the problem and now I have a split VPN. Found via this post.
-
The 3DES/SHA1/DH 2 requirement for macOS/iOS seems to only apply to the native clients when doing a direct configuration. If one uses the Apple Configurator 2 app to create a profile, other protocols can be specified. This way I was able to use AES268/SHA256 and drop 3DES/SHA1 -- An IKEv2 + Apple Configurator 2 blog post was helpful, though I ended up using for my *.mobileconfig EAP-MSChapv2 settings with only the CA certificate, instead of EAP-TLS and multiple certificates as that tutorial indicates.
-
-
Hi,
Registered especially for this issue ... I once had a working config for iOS and pfSense and all was good.
Now I'm trying to do what you did ... but it fails every time and I don't understand anymore. Can you perhaps share some screenshots of your configuration or list it so I can compare? It's prolly something stupid but I cannot get it to work on iOS. Works fine on Win10...
I have now tried the exact config of the last blog you referenced... now I'm getting a different error 'a configuration error occurred' on the iPhone.
I just want safe settings like that and be able to use a username and password. Let me know if you need anything from me.. I'll gladly provide it.
Part of the logfile... I seem to never get the 'con-mobile' config..
09[CFG] <2> looking for peer configs matching x.x.x.x[my.hostname.com]...x.x.x.x[10.216.103.237]
Feb 23 19:16:10 charon 09[CFG] <2> candidate "bypasslan", match: 1/1/24 (me/other/ike)
Feb 23 19:16:10 charon 09[CFG] <bypasslan|2> selected peer config 'bypasslan'
Feb 23 19:16:10 charon 09[IKE] <bypasslan|2> peer requested EAP, config unacceptableThanks!
-
@puijken I don't have access to pfSense environment at the moment, but go ahead and post your phase 1 and phase 2 setup screens. I'll see if I can spot anything that could help. Also, for your iOS devices, are you using the native VPN client and configuring it directly on the device or via Apple Configurator 2? Or are you using a 3rd party app like StrongSwan?
-
Hi @bcpi
Thank you! Here some screenshots from my config in pfSense... I will try and extract some screenshots from Apple Configurator too.. and an error log extract from pfSense when connecting with my iPhone.
https://imgur.com/a/sKUGgfv
I tried using the native client and Apple configurator.. both are not working. In the past I have used some settings but the config got lost. Now I tried with various settings as there are a lot of guides online.. however none seem to be working. I prefer a more safe config and not the pfSense guide config with 3DES/SHA1/DH2...
Currently when connecting with my iPhone the Apple Config VPN throws an "a configuration error occurred" and the native config shows "user athentication failed".The AES256/SHA384/DH20 config is working on my Windows portable after configuring the VPN connection through PowerShell.
In my logs I see only "bypasslan" as possible peer and not the "con-mobile" peer that shows in your log.. (don't know if this is normal or not). I only want to access my internal network and not have a vpn gateway from my mobile devices..
Cleaned up LOG files, PFSENSE_WAN_IP, PEER_IP and EAP_USER have replaced the sensitive information. For the sake of testing I have used the same user for my W10 as for my iPhone, in a working environment they would be 2 different users.
Succesful connection from W10
Feb 24 11:52:18 charon 05[NET] <13> received packet: from PEER_IP[18912] to PFSENSE_WAN_IP[500] (384 bytes) Feb 24 11:52:18 charon 05[ENC] <13> parsed IKE_SA_INIT request 0 [ SA KE No N(FRAG_SUP) N(NATD_S_IP) N(NATD_D_IP) V V V V ] Feb 24 11:52:18 charon 05[CFG] <13> looking for an IKEv2 config for PFSENSE_WAN_IP...PEER_IP Feb 24 11:52:18 charon 05[CFG] <13> candidate: %any...%any, prio 24 Feb 24 11:52:18 charon 05[CFG] <13> candidate: PFSENSE_WAN_IP...%any, prio 1052 Feb 24 11:52:18 charon 05[CFG] <13> found matching ike config: PFSENSE_WAN_IP...%any with prio 1052 Feb 24 11:52:18 charon 05[IKE] <13> received MS NT5 ISAKMPOAKLEY v9 vendor ID Feb 24 11:52:18 charon 05[IKE] <13> received MS-Negotiation Discovery Capable vendor ID Feb 24 11:52:18 charon 05[IKE] <13> received Vid-Initial-Contact vendor ID Feb 24 11:52:18 charon 05[ENC] <13> received unknown vendor ID: 01:52:8b:bb:c0:06:96:12:18:49:ab:9a:1c:5b:2a:51:00:00:00:02 Feb 24 11:52:18 charon 05[IKE] <13> PEER_IP is initiating an IKE_SA Feb 24 11:52:18 charon 05[IKE] <13> IKE_SA (unnamed)[13] state change: CREATED => CONNECTING Feb 24 11:52:18 charon 05[CFG] <13> selecting proposal: Feb 24 11:52:18 charon 05[CFG] <13> no acceptable ENCRYPTION_ALGORITHM found Feb 24 11:52:18 charon 05[CFG] <13> selecting proposal: Feb 24 11:52:18 charon 05[CFG] <13> proposal matches Feb 24 11:52:18 charon 05[CFG] <13> received proposals: IKE:AES_CBC_256/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/ECP_384 Feb 24 11:52:18 charon 05[CFG] <13> configured proposals: IKE:AES_GCM_16_256/PRF_HMAC_SHA2_384/ECP_384, IKE:AES_CBC_256/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/ECP_384 Feb 24 11:52:18 charon 05[CFG] <13> selected proposal: IKE:AES_CBC_256/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/ECP_384 Feb 24 11:52:18 charon 05[IKE] <13> remote host is behind NAT Feb 24 11:52:18 charon 05[IKE] <13> sending cert request for "C=US, O=Let's Encrypt, CN=Let's Encrypt Authority X3" Feb 24 11:52:18 charon 05[ENC] <13> generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(FRAG_SUP) N(MULT_AUTH) ] Feb 24 11:52:18 charon 05[NET] <13> sending packet: from PFSENSE_WAN_IP[500] to PEER_IP[18912] (313 bytes) Feb 24 11:52:18 charon 05[NET] <13> received packet: from PEER_IP[29811] to PFSENSE_WAN_IP[4500] (588 bytes) Feb 24 11:52:18 charon 05[ENC] <13> parsed IKE_AUTH request 1 [ EF(1/4) ] Feb 24 11:52:18 charon 05[ENC] <13> received fragment #1 of 4, waiting for complete IKE message Feb 24 11:52:18 charon 11[NET] <13> received packet: from PEER_IP[29811] to PFSENSE_WAN_IP[4500] (588 bytes) Feb 24 11:52:18 charon 11[ENC] <13> parsed IKE_AUTH request 1 [ EF(2/4) ] Feb 24 11:52:18 charon 11[ENC] <13> received fragment #2 of 4, waiting for complete IKE message Feb 24 11:52:18 charon 11[NET] <13> received packet: from PEER_IP[29811] to PFSENSE_WAN_IP[4500] (588 bytes) Feb 24 11:52:18 charon 11[ENC] <13> parsed IKE_AUTH request 1 [ EF(3/4) ] Feb 24 11:52:18 charon 11[ENC] <13> received fragment #3 of 4, waiting for complete IKE message Feb 24 11:52:18 charon 05[NET] <13> received packet: from PEER_IP[29811] to PFSENSE_WAN_IP[4500] (332 bytes) Feb 24 11:52:18 charon 05[ENC] <13> parsed IKE_AUTH request 1 [ EF(4/4) ] Feb 24 11:52:18 charon 05[ENC] <13> received fragment #4 of 4, reassembled fragmented IKE message (1816 bytes) Feb 24 11:52:18 charon 05[ENC] <13> parsed IKE_AUTH request 1 [ IDi CERTREQ N(MOBIKE_SUP) CPRQ(ADDR DNS NBNS SRV ADDR6 DNS6 SRV6) SA TSi TSr ] Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 4b:da:32:09:af:b8:21:bb:9e:3a:63:58:7d:29:d4:06:56:11:14:ce Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 6e:01:b9:a1:c6:4e:b8:34:1a:e3:b6:48:9e:70:b4:6b:35:ec:5b:66 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 0e:ac:82:60:40:56:27:97:e5:25:13:fc:2a:e1:0a:53:95:59:e4:a4 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 8c:c4:dd:27:7b:16:78:95:36:e8:de:11:4f:47:09:70:11:a1:87:51 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 4b:da:32:09:af:b8:21:bb:9e:3a:63:58:7d:29:d4:06:56:11:14:ce Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid dd:bc:bd:86:9c:3f:07:ed:40:e3:1b:08:ef:ce:c4:d1:88:cd:3b:15 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 5d:fc:6d:71:b4:0f:e4:78:d2:57:0f:74:e2:c0:b3:03:31:3b:83:43 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 4a:5c:75:22:aa:46:bf:a4:08:9d:39:97:4e:bd:b4:a3:60:f7:a0:1d Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 5c:b8:69:fe:8d:ef:c1:ed:66:27:ee:b2:12:0f:72:1b:b8:0a:0e:04 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 6a:47:a2:67:c9:2e:2f:19:68:8b:9b:86:61:66:95:ed:c1:2c:13:00 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 1e:e6:e7:7e:76:cb:fc:31:f8:35:f3:68:44:44:18:74:ad:14:c1:f2 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 01:f0:33:4c:1a:a1:d9:ee:5b:7b:a9:de:43:bc:02:7d:57:09:33:fb Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 88:a9:5a:ef:c0:84:fc:13:74:41:6b:b1:63:32:c2:cf:92:59:bb:3b Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid f9:27:b6:1b:0a:37:f3:c3:1a:fa:17:ec:2d:46:17:16:12:9d:0c:0e Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 34:4f:30:2d:25:69:31:91:ea:f7:73:5c:ab:f5:86:8d:37:82:40:ec Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 44:18:5b:b7:ff:a4:8c:a1:a7:01:b9:31:dd:1c:5d:d3:2c:e8:76:7f Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 3e:df:29:0c:c1:f5:cc:73:2c:eb:3d:24:e1:7e:52:da:bd:27:e2:f0 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 8b:90:f4:58:49:86:13:85:20:e7:3a:e8:dc:c0:e6:c2:86:42:93:6a Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 7c:32:d4:85:fd:89:0a:66:b5:97:ce:86:f4:d5:26:a9:21:07:e8:3e Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 37:d7:52:53:4d:27:6e:3a:19:1c:37:41:cb:19:9a:7e:40:46:97:cb Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid ab:76:88:f4:e5:e1:38:c9:e9:50:17:cd:cd:b3:18:17:b3:3e:8c:f5 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid da:ed:64:74:14:9c:14:3c:ab:dd:99:a9:bd:5b:28:4d:8b:3c:c9:d8 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid f8:92:0b:e9:08:a9:c5:d5:a0:fb:f3:9a:aa:98:a5:74:37:49:ad:9f Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 5e:8c:53:18:22:60:1d:56:71:d6:6a:a0:cc:64:a0:60:07:43:d5:a8 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 86:26:cb:1b:c5:54:b3:9f:bd:6b:ed:63:7f:b9:89:a9:80:f1:f4:8a Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid c0:7a:98:68:8d:89:fb:ab:05:64:0c:11:7d:aa:7d:65:b8:ca:cc:4e Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid a8:e3:02:96:70:a6:8b:57:eb:ec:ef:cc:29:4e:91:74:9a:d4:92:38 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid f7:93:19:ef:df:c1:f5:20:fb:ac:85:55:2c:f2:d2:8f:5a:b9:ca:0b Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 30:a4:e6:4f:de:76:8a:fc:ed:5a:90:84:28:30:46:79:2c:29:15:70 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 48:e6:68:f9:2b:d2:b2:95:d7:47:d8:23:20:10:4f:33:98:90:9f:d4 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 90:e2:41:c2:11:41:8b:95:b1:a9:e0:9c:37:24:7e:84:9f:e4:be:a1 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 73:97:82:ea:b4:04:16:6e:25:d4:82:3c:37:db:f8:a8:12:fb:cf:26 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 69:c4:27:db:59:69:68:18:47:e2:52:17:0a:e0:e5:7f:ab:9d:ef:0f Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid ba:42:b0:81:88:53:88:1d:86:63:bd:4c:c0:5e:08:fe:ea:6e:bb:77 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 87:db:d4:5f:b0:92:8d:4e:1d:f8:15:67:e7:f2:ab:af:d6:2b:67:75 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 6e:58:4e:33:75:bd:57:f6:d5:42:1b:16:01:c2:d8:c0:f5:3a:9f:6e Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 4a:81:0c:de:f0:c0:90:0f:19:06:42:31:35:a2:a2:8d:d3:44:fd:08 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid d5:2e:13:c1:ab:e3:49:da:e8:b4:95:94:ef:7c:38:43:60:64:66:bd Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid f7:f3:01:94:50:ba:3e:69:ec:9a:50:f5:02:d1:38:45:cc:93:13:72 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 13:8f:7b:5d:6e:da:54:ee:84:4c:7c:78:d4:7e:3f:d0:2a:60:d5:ff Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 59:79:12:de:61:75:d6:6f:c4:23:b7:77:13:74:c7:96:de:6f:88:72 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 6c:ca:bd:7d:b4:7e:94:a5:75:99:01:b6:a7:df:d4:5d:1c:09:1c:cc Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid ab:30:d3:af:4b:d8:f1:6b:58:69:ee:45:69:29:da:84:b8:73:94:88 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 42:32:b6:16:fa:04:fd:fe:5d:4b:7a:c3:fd:f7:4c:40:1d:5a:43:af Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid f0:63:ba:7c:9a:16:74:4a:9c:db:54:ec:23:cd:67:29:8e:7c:49:4d Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid a5:9d:bf:90:15:d9:f1:f5:a8:d8:c0:1d:14:e6:f1:d8:c4:fe:57:17 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid a5:06:8a:78:cf:84:bd:74:32:dd:58:f9:65:eb:3a:55:e7:c7:80:dc Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid e2:7f:7b:d8:77:d5:df:9e:0a:3f:9e:b4:cb:0e:2e:a9:ef:db:69:77 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 5b:bf:1f:74:4a:e0:51:bd:61:7b:20:0d:bb:74:dc:26:8b:d1:3a:02 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 6d:aa:9b:09:87:c4:d0:d4:22:ed:40:07:37:4d:19:f1:91:ff:de:d3 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 83:31:7e:62:85:42:53:d6:d7:78:31:90:ec:91:90:56:e9:91:b9:e3 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 75:b1:bc:dd:db:be:95:b8:7a:80:9c:b6:99:a1:44:d2:1b:74:eb:3d Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid fd:da:14:c4:9f:30:de:21:bd:1e:42:39:fc:ab:63:23:49:e0:f1:84 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 3e:22:d4:2c:1f:02:44:b8:04:10:65:61:7c:c7:6b:ae:da:87:29:9c Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 55:e4:81:d1:11:80:be:d8:89:b9:08:a3:31:f9:a1:24:09:16:b9:70 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid b1:81:08:1a:19:a4:c0:94:1f:fa:e8:95:28:c1:24:c9:9b:34:ac:c7 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 36:12:c2:39:c5:22:b9:1e:20:d4:8e:08:3c:be:69:e1:1d:a8:27:e5 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 21:0f:2c:89:f7:c4:cd:5d:1b:82:5e:38:d6:c6:59:3b:a6:93:75:ae Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid e6:ff:c3:94:e8:38:59:7f:51:d4:80:42:19:76:27:cf:db:94:8e:c6 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid bb:c2:3e:29:0b:b3:28:77:1d:ad:3e:a2:4d:bd:f4:23:bd:06:b0:3d Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid b0:19:89:e7:ef:fb:4a:af:cb:14:8f:58:46:39:76:22:41:50:e1:ba Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid c8:95:13:68:01:97:28:0a:2c:55:c3:fc:d3:90:f5:3a:05:3b:c9:fb Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid ee:e5:9f:1e:2a:a5:44:c3:cb:25:43:a6:9a:5b:d4:6a:25:bc:bb:8e Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 22:f1:9e:2e:c6:ea:cc:fc:5d:23:46:f4:c2:e8:f6:c5:54:dd:5e:07 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 67:ec:9f:90:2d:cd:64:ae:fe:7e:bc:cd:f8:8c:51:28:f1:93:2c:12 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 17:4a:b8:2b:5f:fb:05:67:75:27:ad:49:5a:4a:5d:c4:22:cc:ea:4e Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 68:33:0e:61:35:85:21:59:29:83:a3:c8:d2:d2:e1:40:6e:7a:b3:c1 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 9c:a9:8d:00:af:74:0d:dd:81:80:d2:13:45:a5:8b:8f:2e:94:38:d6 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 4f:9c:7d:21:79:9c:ad:0e:d8:b9:0c:57:9f:1a:02:99:e7:90:f3:87 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid c7:9f:3a:76:71:13:14:73:f6:da:c8:49:e6:09:d2:92:a1:db:d4:32 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 34:83:fa:fe:3f:b5:60:7d:1f:8b:35:f3:36:30:f9:6e:48:e6:d8:37 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 4b:da:32:09:af:b8:21:bb:9e:3a:63:58:7d:29:d4:06:56:11:14:ce Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 4b:da:32:09:af:b8:21:bb:9e:3a:63:58:7d:29:d4:06:56:11:14:ce Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 2c:c9:e2:f9:26:2a:75:41:62:79:85:17:0b:0f:79:f7:15:d7:03:91 Feb 24 11:52:18 charon 05[IKE] <13> received cert request for unknown ca with keyid 4b:da:32:09:af:b8:21:bb:9e:3a:63:58:7d:29:d4:06:56:11:14:ce Feb 24 11:52:18 charon 05[IKE] <13> received 75 cert requests for an unknown ca Feb 24 11:52:18 charon 05[CFG] <13> looking for peer configs matching PFSENSE_WAN_IP[%any]...PEER_IP[172.20.10.4] Feb 24 11:52:18 charon 05[CFG] <13> candidate "bypasslan", match: 1/1/24 (me/other/ike) Feb 24 11:52:18 charon 05[CFG] <13> candidate "con-mobile", match: 1/1/1052 (me/other/ike) Feb 24 11:52:18 charon 05[CFG] <con-mobile|13> selected peer config 'con-mobile' Feb 24 11:52:18 charon 05[IKE] <con-mobile|13> initiating EAP_IDENTITY method (id 0x00) Feb 24 11:52:18 charon 05[IKE] <con-mobile|13> processing INTERNAL_IP4_ADDRESS attribute Feb 24 11:52:18 charon 05[IKE] <con-mobile|13> processing INTERNAL_IP4_DNS attribute Feb 24 11:52:18 charon 05[IKE] <con-mobile|13> processing INTERNAL_IP4_NBNS attribute Feb 24 11:52:18 charon 05[IKE] <con-mobile|13> processing INTERNAL_IP4_SERVER attribute Feb 24 11:52:18 charon 05[IKE] <con-mobile|13> processing INTERNAL_IP6_ADDRESS attribute Feb 24 11:52:18 charon 05[IKE] <con-mobile|13> processing INTERNAL_IP6_DNS attribute Feb 24 11:52:18 charon 05[IKE] <con-mobile|13> processing INTERNAL_IP6_SERVER attribute Feb 24 11:52:18 charon 05[IKE] <con-mobile|13> peer supports MOBIKE Feb 24 11:52:18 charon 05[IKE] <con-mobile|13> authentication of 'CN=*.myhostname.com' (myself) with RSA signature successful Feb 24 11:52:18 charon 05[IKE] <con-mobile|13> sending end entity cert "CN=*.myhostname.com" Feb 24 11:52:18 charon 05[IKE] <con-mobile|13> sending issuer cert "C=US, O=Let's Encrypt, CN=Let's Encrypt Authority X3" Feb 24 11:52:18 charon 05[ENC] <con-mobile|13> generating IKE_AUTH response 1 [ IDr CERT CERT AUTH EAP/REQ/ID ] Feb 24 11:52:18 charon 05[ENC] <con-mobile|13> splitting IKE message (3448 bytes) into 3 fragments Feb 24 11:52:18 charon 05[ENC] <con-mobile|13> generating IKE_AUTH response 1 [ EF(1/3) ] Feb 24 11:52:18 charon 05[ENC] <con-mobile|13> generating IKE_AUTH response 1 [ EF(2/3) ] Feb 24 11:52:18 charon 05[ENC] <con-mobile|13> generating IKE_AUTH response 1 [ EF(3/3) ] Feb 24 11:52:18 charon 05[NET] <con-mobile|13> sending packet: from PFSENSE_WAN_IP[4500] to PEER_IP[29811] (1244 bytes) Feb 24 11:52:18 charon 05[NET] <con-mobile|13> sending packet: from PFSENSE_WAN_IP[4500] to PEER_IP[29811] (1244 bytes) Feb 24 11:52:18 charon 05[NET] <con-mobile|13> sending packet: from PFSENSE_WAN_IP[4500] to PEER_IP[29811] (1116 bytes) Feb 24 11:52:19 charon 05[NET] <con-mobile|13> received packet: from PEER_IP[29811] to PFSENSE_WAN_IP[4500] (104 bytes) Feb 24 11:52:19 charon 05[ENC] <con-mobile|13> parsed IKE_AUTH request 2 [ EAP/RES/ID ] Feb 24 11:52:19 charon 05[IKE] <con-mobile|13> received EAP identity 'EAP_USER' Feb 24 11:52:19 charon 05[IKE] <con-mobile|13> initiating EAP_MSCHAPV2 method (id 0xE0) Feb 24 11:52:19 charon 05[ENC] <con-mobile|13> generating IKE_AUTH response 2 [ EAP/REQ/MSCHAPV2 ] Feb 24 11:52:19 charon 05[NET] <con-mobile|13> sending packet: from PFSENSE_WAN_IP[4500] to PEER_IP[29811] (120 bytes) Feb 24 11:52:19 charon 05[NET] <con-mobile|13> received packet: from PEER_IP[29811] to PFSENSE_WAN_IP[4500] (152 bytes) Feb 24 11:52:19 charon 05[ENC] <con-mobile|13> parsed IKE_AUTH request 3 [ EAP/RES/MSCHAPV2 ] Feb 24 11:52:19 charon 05[ENC] <con-mobile|13> generating IKE_AUTH response 3 [ EAP/REQ/MSCHAPV2 ] Feb 24 11:52:19 charon 05[NET] <con-mobile|13> sending packet: from PFSENSE_WAN_IP[4500] to PEER_IP[29811] (152 bytes) Feb 24 11:52:19 charon 05[NET] <con-mobile|13> received packet: from PEER_IP[29811] to PFSENSE_WAN_IP[4500] (88 bytes) Feb 24 11:52:19 charon 05[ENC] <con-mobile|13> parsed IKE_AUTH request 4 [ EAP/RES/MSCHAPV2 ] Feb 24 11:52:19 charon 05[IKE] <con-mobile|13> EAP method EAP_MSCHAPV2 succeeded, MSK established Feb 24 11:52:19 charon 05[ENC] <con-mobile|13> generating IKE_AUTH response 4 [ EAP/SUCC ] Feb 24 11:52:19 charon 05[NET] <con-mobile|13> sending packet: from PFSENSE_WAN_IP[4500] to PEER_IP[29811] (88 bytes) Feb 24 11:52:19 charon 05[NET] <con-mobile|13> received packet: from PEER_IP[29811] to PFSENSE_WAN_IP[4500] (136 bytes) Feb 24 11:52:19 charon 05[ENC] <con-mobile|13> parsed IKE_AUTH request 5 [ AUTH ] Feb 24 11:52:19 charon 05[IKE] <con-mobile|13> authentication of '172.20.10.4' with EAP successful Feb 24 11:52:19 charon 05[IKE] <con-mobile|13> authentication of 'CN=*.myhostname.com' (myself) with EAP Feb 24 11:52:19 charon 05[IKE] <con-mobile|13> IKE_SA con-mobile[13] established between PFSENSE_WAN_IP[CN=*.myhostname.com]...PEER_IP[172.20.10.4] Feb 24 11:52:19 charon 05[IKE] <con-mobile|13> IKE_SA con-mobile[13] state change: CONNECTING => ESTABLISHED Feb 24 11:52:19 charon 05[IKE] <con-mobile|13> scheduling reauthentication in 28028s Feb 24 11:52:19 charon 05[IKE] <con-mobile|13> maximum IKE_SA lifetime 28568s Feb 24 11:52:19 charon 05[IKE] <con-mobile|13> peer requested virtual IP %any Feb 24 11:52:19 charon 05[CFG] <con-mobile|13> reassigning offline lease to 'EAP_USER' Feb 24 11:52:19 charon 05[IKE] <con-mobile|13> assigning virtual IP 10.0.0.1 to peer 'EAP_USER' Feb 24 11:52:19 charon 05[IKE] <con-mobile|13> peer requested virtual IP %any6 Feb 24 11:52:19 charon 05[IKE] <con-mobile|13> no virtual IP found for %any6 requested by 'EAP_USER' Feb 24 11:52:19 charon 05[CFG] <con-mobile|13> looking for a child config for 0.0.0.0/0|/0 ::/0|/0 === 0.0.0.0/0|/0 ::/0|/0 Feb 24 11:52:19 charon 05[CFG] <con-mobile|13> proposing traffic selectors for us: Feb 24 11:52:19 charon 05[CFG] <con-mobile|13> 192.168.1.0/24|/0 Feb 24 11:52:19 charon 05[CFG] <con-mobile|13> proposing traffic selectors for other: Feb 24 11:52:19 charon 05[CFG] <con-mobile|13> 10.0.0.1/32|/0 Feb 24 11:52:19 charon 05[CFG] <con-mobile|13> candidate "con-mobile" with prio 2+2 Feb 24 11:52:19 charon 05[CFG] <con-mobile|13> found matching child config "con-mobile" with prio 4 Feb 24 11:52:19 charon 05[CFG] <con-mobile|13> selecting proposal: Feb 24 11:52:19 charon 05[CFG] <con-mobile|13> proposal matches Feb 24 11:52:19 charon 05[CFG] <con-mobile|13> received proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/NO_EXT_SEQ Feb 24 11:52:19 charon 05[CFG] <con-mobile|13> configured proposals: ESP:AES_CBC_256/HMAC_SHA2_256_128/ECP_384/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_384_192/ECP_384/NO_EXT_SEQ, ESP:AES_CBC_256/HMAC_SHA2_512_256/ECP_384/NO_EXT_SEQ, ESP:AES_GCM_16_256/ECP_384/NO_EXT_SEQ, ESP:AES_GCM_16_256/ECP_384/NO_EXT_SEQ, ESP:AES_GCM_16_256/ECP_384/NO_EXT_SEQ Feb 24 11:52:19 charon 05[CFG] <con-mobile|13> selected proposal: ESP:AES_CBC_256/HMAC_SHA2_256_128/NO_EXT_SEQ Feb 24 11:52:19 charon 05[CFG] <con-mobile|13> selecting traffic selectors for us: Feb 24 11:52:19 charon 05[CFG] <con-mobile|13> config: 192.168.1.0/24|/0, received: 0.0.0.0/0|/0 => match: 192.168.1.0/24|/0 Feb 24 11:52:19 charon 05[CFG] <con-mobile|13> config: 192.168.1.0/24|/0, received: ::/0|/0 => no match Feb 24 11:52:19 charon 05[CFG] <con-mobile|13> selecting traffic selectors for other: Feb 24 11:52:19 charon 05[CFG] <con-mobile|13> config: 10.0.0.1/32|/0, received: 0.0.0.0/0|/0 => match: 10.0.0.1/32|/0 Feb 24 11:52:19 charon 05[CFG] <con-mobile|13> config: 10.0.0.1/32|/0, received: ::/0|/0 => no match Feb 24 11:52:19 charon 05[CHD] <con-mobile|13> CHILD_SA con-mobile{2} state change: CREATED => INSTALLING Feb 24 11:52:19 charon 05[CHD] <con-mobile|13> using AES_CBC for encryption Feb 24 11:52:19 charon 05[CHD] <con-mobile|13> using HMAC_SHA2_256_128 for integrity Feb 24 11:52:19 charon 05[CHD] <con-mobile|13> adding inbound ESP SA Feb 24 11:52:19 charon 05[CHD] <con-mobile|13> SPI 0xc4ec8c38, src PEER_IP dst PFSENSE_WAN_IP Feb 24 11:52:19 charon 05[CHD] <con-mobile|13> adding outbound ESP SA Feb 24 11:52:19 charon 05[CHD] <con-mobile|13> SPI 0x55a6ea2c, src PFSENSE_WAN_IP dst PEER_IP Feb 24 11:52:19 charon 05[IKE] <con-mobile|13> CHILD_SA con-mobile{2} established with SPIs c4ec8c38_i 55a6ea2c_o and TS 192.168.1.0/24|/0 === 10.0.0.1/32|/0 Feb 24 11:52:19 charon 05[CHD] <con-mobile|13> CHILD_SA con-mobile{2} state change: INSTALLING => INSTALLED Feb 24 11:52:19 charon 05[ENC] <con-mobile|13> generating IKE_AUTH response 5 [ AUTH CPRP(ADDR) N(ESP_TFC_PAD_N) SA TSi TSr N(AUTH_LFT) N(MOBIKE_SUP) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_4_ADDR) N(ADD_6_ADDR) N(ADD_6_ADDR) ] Feb 24 11:52:19 charon 05[NET] <con-mobile|13> sending packet: from PFSENSE_WAN_IP[4500] to PEER_IP[29811] (360 bytes)AES-256-CGM connection attempt (localid = fqdn from certificate)
Feb 24 12:22:02 charon 15[NET] <18> received packet: from PEER_IP[26398] to PFSENSE_WAN_IP[500] (272 bytes) Feb 24 12:22:02 charon 15[ENC] <18> parsed IKE_SA_INIT request 0 [ SA KE No N(REDIR_SUP) N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) ] Feb 24 12:22:02 charon 15[CFG] <18> looking for an IKEv2 config for PFSENSE_WAN_IP...PEER_IP Feb 24 12:22:02 charon 15[CFG] <18> candidate: %any...%any, prio 24 Feb 24 12:22:02 charon 15[CFG] <18> candidate: PFSENSE_WAN_IP...%any, prio 1052 Feb 24 12:22:02 charon 15[CFG] <18> found matching ike config: PFSENSE_WAN_IP...%any with prio 1052 Feb 24 12:22:02 charon 15[IKE] <18> PEER_IP is initiating an IKE_SA Feb 24 12:22:02 charon 15[IKE] <18> IKE_SA (unnamed)[18] state change: CREATED => CONNECTING Feb 24 12:22:02 charon 15[CFG] <18> selecting proposal: Feb 24 12:22:02 charon 15[CFG] <18> proposal matches Feb 24 12:22:02 charon 15[CFG] <18> received proposals: IKE:AES_GCM_16_256/PRF_HMAC_SHA2_384/ECP_384 Feb 24 12:22:02 charon 15[CFG] <18> configured proposals: IKE:AES_GCM_16_256/PRF_HMAC_SHA2_384/ECP_384, IKE:AES_CBC_256/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/ECP_384 Feb 24 12:22:02 charon 15[CFG] <18> selected proposal: IKE:AES_GCM_16_256/PRF_HMAC_SHA2_384/ECP_384 Feb 24 12:22:02 charon 15[IKE] <18> remote host is behind NAT Feb 24 12:22:02 charon 15[IKE] <18> sending cert request for "C=US, O=Let's Encrypt, CN=Let's Encrypt Authority X3" Feb 24 12:22:02 charon 15[ENC] <18> generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(FRAG_SUP) N(MULT_AUTH) ] Feb 24 12:22:02 charon 15[NET] <18> sending packet: from PFSENSE_WAN_IP[500] to PEER_IP[26398] (305 bytes) Feb 24 12:22:02 charon 15[NET] <18> received packet: from PEER_IP[30491] to PFSENSE_WAN_IP[4500] (352 bytes) Feb 24 12:22:02 charon 15[ENC] <18> unknown attribute type (25) Feb 24 12:22:02 charon 15[ENC] <18> parsed IKE_AUTH request 1 [ IDi N(INIT_CONTACT) N(MOBIKE_SUP) IDr CPRQ(ADDR DHCP DNS MASK ADDR6 DHCP6 DNS6 (25)) N(ESP_TFC_PAD_N) N(NON_FIRST_FRAG) SA TSi TSr N(EAP_ONLY) ] Feb 24 12:22:02 charon 15[CFG] <18> looking for peer configs matching PFSENSE_WAN_IP[vpn.myhostname.com]...PEER_IP[vpn.myhostname.com] Feb 24 12:22:02 charon 15[CFG] <18> candidate "bypasslan", match: 1/1/24 (me/other/ike) Feb 24 12:22:02 charon 15[CFG] <bypasslan|18> selected peer config 'bypasslan' Feb 24 12:22:02 charon 15[IKE] <bypasslan|18> peer requested EAP, config unacceptable Feb 24 12:22:02 charon 15[CFG] <bypasslan|18> no alternative config found Feb 24 12:22:02 charon 15[IKE] <bypasslan|18> processing INTERNAL_IP4_ADDRESS attribute Feb 24 12:22:02 charon 15[IKE] <bypasslan|18> processing INTERNAL_IP4_DHCP attribute Feb 24 12:22:02 charon 15[IKE] <bypasslan|18> processing INTERNAL_IP4_DNS attribute Feb 24 12:22:02 charon 15[IKE] <bypasslan|18> processing INTERNAL_IP4_NETMASK attribute Feb 24 12:22:02 charon 15[IKE] <bypasslan|18> processing INTERNAL_IP6_ADDRESS attribute Feb 24 12:22:02 charon 15[IKE] <bypasslan|18> processing INTERNAL_IP6_DHCP attribute Feb 24 12:22:02 charon 15[IKE] <bypasslan|18> processing INTERNAL_IP6_DNS attribute Feb 24 12:22:02 charon 15[IKE] <bypasslan|18> processing (25) attribute Feb 24 12:22:02 charon 15[IKE] <bypasslan|18> received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding Feb 24 12:22:02 charon 15[IKE] <bypasslan|18> peer supports MOBIKE Feb 24 12:22:02 charon 15[ENC] <bypasslan|18> generating IKE_AUTH response 1 [ N(AUTH_FAILED) ] Feb 24 12:22:02 charon 15[NET] <bypasslan|18> sending packet: from PFSENSE_WAN_IP[4500] to PEER_IP[30491] (65 bytes) Feb 24 12:22:02 charon 15[IKE] <bypasslan|18> IKE_SA bypasslan[18] state change: CONNECTING => DESTROYINGAES-256-CGM connection attempt (localid = EAP_USER)
Feb 24 12:29:13 charon 04[NET] <22> received packet: from PEER_IP[25047] to PFSENSE_WAN_IP[500] (272 bytes) Feb 24 12:29:13 charon 04[ENC] <22> parsed IKE_SA_INIT request 0 [ SA KE No N(REDIR_SUP) N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) ] Feb 24 12:29:13 charon 04[CFG] <22> looking for an IKEv2 config for PFSENSE_WAN_IP...PEER_IP Feb 24 12:29:13 charon 04[CFG] <22> candidate: %any...%any, prio 24 Feb 24 12:29:13 charon 04[CFG] <22> candidate: PFSENSE_WAN_IP...%any, prio 1052 Feb 24 12:29:13 charon 04[CFG] <22> found matching ike config: PFSENSE_WAN_IP...%any with prio 1052 Feb 24 12:29:13 charon 04[IKE] <22> PEER_IP is initiating an IKE_SA Feb 24 12:29:13 charon 04[IKE] <22> IKE_SA (unnamed)[22] state change: CREATED => CONNECTING Feb 24 12:29:13 charon 04[CFG] <22> selecting proposal: Feb 24 12:29:13 charon 04[CFG] <22> proposal matches Feb 24 12:29:13 charon 04[CFG] <22> received proposals: IKE:AES_GCM_16_256/PRF_HMAC_SHA2_384/ECP_384 Feb 24 12:29:13 charon 04[CFG] <22> configured proposals: IKE:AES_GCM_16_256/PRF_HMAC_SHA2_384/ECP_384, IKE:AES_CBC_256/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/ECP_384 Feb 24 12:29:13 charon 04[CFG] <22> selected proposal: IKE:AES_GCM_16_256/PRF_HMAC_SHA2_384/ECP_384 Feb 24 12:29:13 charon 04[IKE] <22> remote host is behind NAT Feb 24 12:29:13 charon 04[IKE] <22> sending cert request for "C=US, O=Let's Encrypt, CN=Let's Encrypt Authority X3" Feb 24 12:29:13 charon 04[ENC] <22> generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(FRAG_SUP) N(MULT_AUTH) ] Feb 24 12:29:13 charon 04[NET] <22> sending packet: from PFSENSE_WAN_IP[500] to PEER_IP[25047] (305 bytes) Feb 24 12:29:14 charon 04[NET] <22> received packet: from PEER_IP[19142] to PFSENSE_WAN_IP[4500] (352 bytes) Feb 24 12:29:14 charon 04[ENC] <22> unknown attribute type (25) Feb 24 12:29:14 charon 04[ENC] <22> parsed IKE_AUTH request 1 [ IDi N(INIT_CONTACT) N(MOBIKE_SUP) IDr CPRQ(ADDR DHCP DNS MASK ADDR6 DHCP6 DNS6 (25)) N(ESP_TFC_PAD_N) N(NON_FIRST_FRAG) SA TSi TSr N(EAP_ONLY) ] Feb 24 12:29:14 charon 04[CFG] <22> looking for peer configs matching PFSENSE_WAN_IP[vpn.myhostname.com]...PEER_IP[EAP_USER] Feb 24 12:29:14 charon 04[CFG] <22> candidate "bypasslan", match: 1/1/24 (me/other/ike) Feb 24 12:29:14 charon 04[CFG] <bypasslan|22> selected peer config 'bypasslan' Feb 24 12:29:14 charon 04[IKE] <bypasslan|22> peer requested EAP, config unacceptable Feb 24 12:29:14 charon 04[CFG] <bypasslan|22> no alternative config found Feb 24 12:29:14 charon 04[IKE] <bypasslan|22> processing INTERNAL_IP4_ADDRESS attribute Feb 24 12:29:14 charon 04[IKE] <bypasslan|22> processing INTERNAL_IP4_DHCP attribute Feb 24 12:29:14 charon 04[IKE] <bypasslan|22> processing INTERNAL_IP4_DNS attribute Feb 24 12:29:14 charon 04[IKE] <bypasslan|22> processing INTERNAL_IP4_NETMASK attribute Feb 24 12:29:14 charon 04[IKE] <bypasslan|22> processing INTERNAL_IP6_ADDRESS attribute Feb 24 12:29:14 charon 04[IKE] <bypasslan|22> processing INTERNAL_IP6_DHCP attribute Feb 24 12:29:14 charon 04[IKE] <bypasslan|22> processing INTERNAL_IP6_DNS attribute Feb 24 12:29:14 charon 04[IKE] <bypasslan|22> processing (25) attribute Feb 24 12:29:14 charon 04[IKE] <bypasslan|22> received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding Feb 24 12:29:14 charon 04[IKE] <bypasslan|22> peer supports MOBIKE Feb 24 12:29:14 charon 04[ENC] <bypasslan|22> generating IKE_AUTH response 1 [ N(AUTH_FAILED) ] Feb 24 12:29:14 charon 04[NET] <bypasslan|22> sending packet: from PFSENSE_WAN_IP[4500] to PEER_IP[19142] (65 bytes) Feb 24 12:29:14 charon 04[IKE] <bypasslan|22> IKE_SA bypasslan[22] state change: CONNECTING => DESTROYING -
Previous post got to long... last log included here..
AES-256 connection attempt (localid = EAP_USER) - maybe not needed but while we are at it..
Feb 24 12:33:24 charon 10[NET] <23> received packet: from PEER_IP[26871] to PFSENSE_WAN_IP[500] (272 bytes) Feb 24 12:33:24 charon 10[ENC] <23> parsed IKE_SA_INIT request 0 [ SA KE No N(REDIR_SUP) N(NATD_S_IP) N(NATD_D_IP) N(FRAG_SUP) ] Feb 24 12:33:24 charon 10[CFG] <23> looking for an IKEv2 config for PFSENSE_WAN_IP...PEER_IP Feb 24 12:33:24 charon 10[CFG] <23> candidate: %any...%any, prio 24 Feb 24 12:33:24 charon 10[CFG] <23> candidate: PFSENSE_WAN_IP...%any, prio 1052 Feb 24 12:33:24 charon 10[CFG] <23> found matching ike config: PFSENSE_WAN_IP...%any with prio 1052 Feb 24 12:33:24 charon 10[IKE] <23> PEER_IP is initiating an IKE_SA Feb 24 12:33:24 charon 10[IKE] <23> IKE_SA (unnamed)[23] state change: CREATED => CONNECTING Feb 24 12:33:24 charon 10[CFG] <23> selecting proposal: Feb 24 12:33:24 charon 10[CFG] <23> no acceptable ENCRYPTION_ALGORITHM found Feb 24 12:33:24 charon 10[CFG] <23> selecting proposal: Feb 24 12:33:24 charon 10[CFG] <23> no acceptable INTEGRITY_ALGORITHM found Feb 24 12:33:24 charon 10[CFG] <23> received proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/ECP_384 Feb 24 12:33:24 charon 10[CFG] <23> configured proposals: IKE:AES_GCM_16_256/PRF_HMAC_SHA2_384/ECP_384, IKE:AES_CBC_256/HMAC_SHA2_384_192/PRF_HMAC_SHA2_384/ECP_384 Feb 24 12:33:24 charon 10[CFG] <23> looking for IKEv2 configs for PFSENSE_WAN_IP...PEER_IP Feb 24 12:33:24 charon 10[CFG] <23> candidate: %any...%any, prio 24 Feb 24 12:33:24 charon 10[CFG] <23> candidate: PFSENSE_WAN_IP...%any, prio 1052 Feb 24 12:33:24 charon 10[IKE] <23> no matching proposal found, trying alternative config Feb 24 12:33:24 charon 10[CFG] <23> selecting proposal: Feb 24 12:33:24 charon 10[CFG] <23> proposal matches Feb 24 12:33:24 charon 10[CFG] <23> received proposals: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/ECP_384 Feb 24 12:33:24 charon 10[CFG] <23> configured proposals: IKE:AES_CBC_128/AES_CBC_192/AES_CBC_256/CAMELLIA_CBC_128/CAMELLIA_CBC_192/CAMELLIA_CBC_256/3DES_CBC/HMAC_SHA2_256_128/HMAC_SHA2_384_192/HMAC_SHA2_512_256/HMAC_SHA1_96/AES_XCBC_96/AES_CMAC_96/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_AES128_CMAC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048, IKE:AES_GCM_16_128/AES_GCM_16_192/AES_GCM_16_256/AES_GCM_12_128/AES_GCM_12_192/AES_GCM_12_256/AES_GCM_8_128/AES_GCM_8_192/AES_GCM_8_256/PRF_HMAC_SHA2_256/PRF_HMAC_SHA2_384/PRF_HMAC_SHA2_512/PRF_AES128_XCBC/PRF_AES128_CMAC/PRF_HMAC_SHA1/ECP_256/ECP_384/ECP_521/ECP_256_BP/ECP_384_BP/ECP_512_BP/CURVE_25519/MODP_3072/MODP_4096/MODP_6144/MODP_8192/MODP_2048 Feb 24 12:33:24 charon 10[CFG] <23> selected proposal: IKE:AES_CBC_256/HMAC_SHA2_256_128/PRF_HMAC_SHA2_256/ECP_384 Feb 24 12:33:24 charon 10[IKE] <23> remote host is behind NAT Feb 24 12:33:24 charon 10[IKE] <23> sending cert request for "C=US, O=Let's Encrypt, CN=Let's Encrypt Authority X3" Feb 24 12:33:24 charon 10[ENC] <23> generating IKE_SA_INIT response 0 [ SA KE No N(NATD_S_IP) N(NATD_D_IP) CERTREQ N(FRAG_SUP) N(MULT_AUTH) ] Feb 24 12:33:24 charon 10[NET] <23> sending packet: from PFSENSE_WAN_IP[500] to PEER_IP[26871] (313 bytes) Feb 24 12:33:24 charon 10[NET] <23> received packet: from PEER_IP[22973] to PFSENSE_WAN_IP[4500] (368 bytes) Feb 24 12:33:24 charon 10[ENC] <23> unknown attribute type (25) Feb 24 12:33:24 charon 10[ENC] <23> parsed IKE_AUTH request 1 [ IDi N(INIT_CONTACT) N(MOBIKE_SUP) IDr CPRQ(ADDR DHCP DNS MASK ADDR6 DHCP6 DNS6 (25)) N(ESP_TFC_PAD_N) N(NON_FIRST_FRAG) SA TSi TSr N(EAP_ONLY) ] Feb 24 12:33:24 charon 10[CFG] <23> looking for peer configs matching PFSENSE_WAN_IP[vpn.myhostname.com]...PEER_IP[EAP_USER] Feb 24 12:33:24 charon 10[CFG] <23> candidate "bypasslan", match: 1/1/24 (me/other/ike) Feb 24 12:33:24 charon 10[CFG] <bypasslan|23> selected peer config 'bypasslan' Feb 24 12:33:24 charon 10[IKE] <bypasslan|23> peer requested EAP, config unacceptable Feb 24 12:33:24 charon 10[CFG] <bypasslan|23> no alternative config found Feb 24 12:33:24 charon 10[IKE] <bypasslan|23> processing INTERNAL_IP4_ADDRESS attribute Feb 24 12:33:24 charon 10[IKE] <bypasslan|23> processing INTERNAL_IP4_DHCP attribute Feb 24 12:33:24 charon 10[IKE] <bypasslan|23> processing INTERNAL_IP4_DNS attribute Feb 24 12:33:24 charon 10[IKE] <bypasslan|23> processing INTERNAL_IP4_NETMASK attribute Feb 24 12:33:24 charon 10[IKE] <bypasslan|23> processing INTERNAL_IP6_ADDRESS attribute Feb 24 12:33:24 charon 10[IKE] <bypasslan|23> processing INTERNAL_IP6_DHCP attribute Feb 24 12:33:24 charon 10[IKE] <bypasslan|23> processing INTERNAL_IP6_DNS attribute Feb 24 12:33:24 charon 10[IKE] <bypasslan|23> processing (25) attribute Feb 24 12:33:24 charon 10[IKE] <bypasslan|23> received ESP_TFC_PADDING_NOT_SUPPORTED, not using ESPv3 TFC padding Feb 24 12:33:24 charon 10[IKE] <bypasslan|23> peer supports MOBIKE Feb 24 12:33:24 charon 10[ENC] <bypasslan|23> generating IKE_AUTH response 1 [ N(AUTH_FAILED) ] Feb 24 12:33:24 charon 10[NET] <bypasslan|23> sending packet: from PFSENSE_WAN_IP[4500] to PEER_IP[22973] (80 bytes) Feb 24 12:33:24 charon 10[IKE] <bypasslan|23> IKE_SA bypasslan[23] state change: CONNECTING => DESTROYING -
@puijken
Hey
Do not pay attention to the Russian language ( the pictures are clear)
On the test machine configured access using Apple Configurator ( see pictures)
1 . Create CA / Server certificate
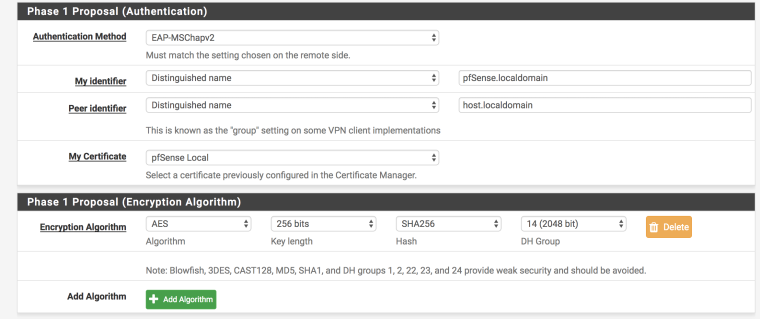
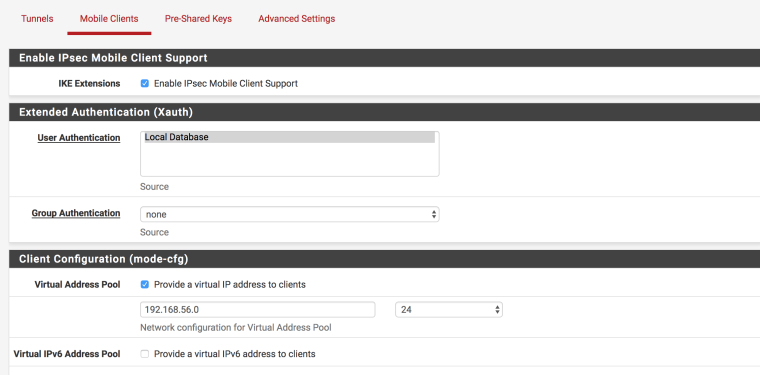
2. Configure Mobile IPSEC
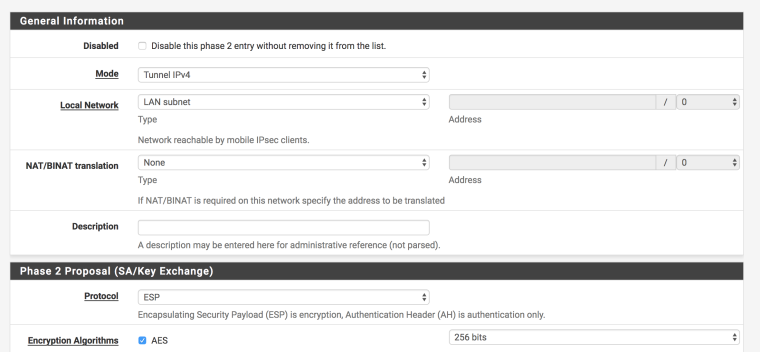
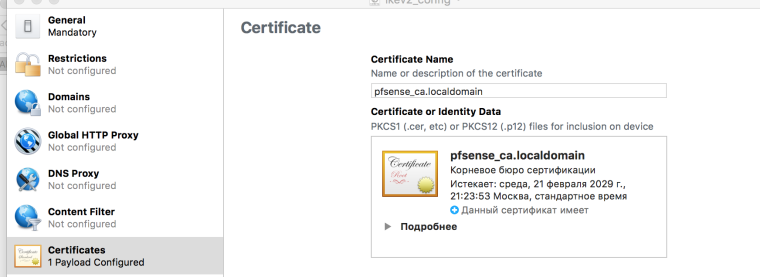
3 Upload server CA without key
4 Apple Configurator
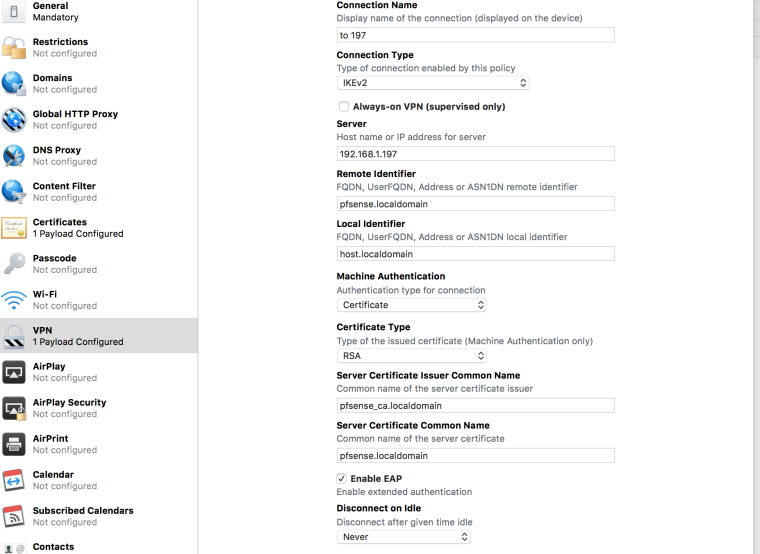

5 Set the profile
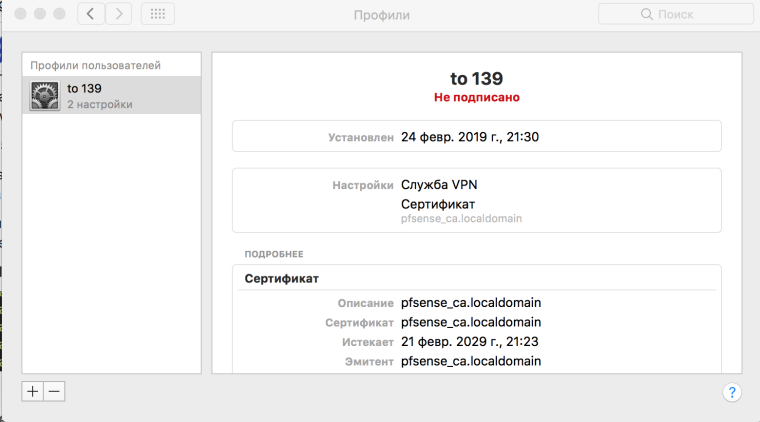
6 Check the connection

-
It looks like your Apple Configurator 2 profile is missing the certificate setup.
I'll point out some differences from your setup and mine:
Phase 1
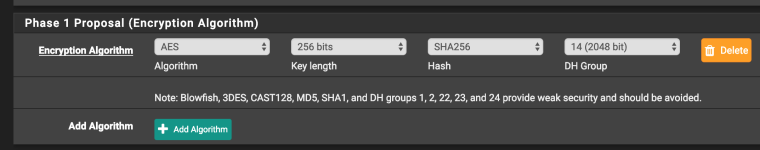
- I only have one
Encryption Algorithmentry: AES / 256 bits / SHA256 / 14 (2048bit) Enable DPD10 / 5 (you probably have this, but didn't see in image)- Note: Make sure
My Certificateis the server certificate, and not the webConfigurator certificate.
Phase 2
- I only have one
Encryption Algorithmentry: AES / Auto PFS key groupdisabledLifetime3600
Mobile Clients
- Same setup. Just remember the pool should not overlap with anything you have in your LAN, which looks like the case.
Apple Configurator 2
Certificates section:
- Make sure you drop the CA certificate here. Download by clicking the "seal" icon in the
CAsection of System > Certificate Manager
VPN section:
Local Identifier0.0.0.0 (any mobile client IP)Machine Authentication: CertificateCertificate TypeRSAServer Certificate Issuer Common Name(the name of your CA)Server Certificate Common Name(FQDN as in server certificate)EAP AuthenticationUser name/PasswordAccount(leave blank for user to setup, or pre-fill)Password(leave blank for user to setup, or pre-fill with user's shared key)IKE SA ParamsAES-256 / SHA2-256 / 14 / Lifetime: 1440 / Proxy setup: noneChild SA Params(same as IKE SA Params above)
Server certificate note: Be sure to have FQDN or IP in
Common Name, and ALSO add both FQDN and IP inAlternative Names. For other settings I used defaults or what was suggested in the how-to's linked in the original post. - I only have one
-
Hi guys,
Thank you for the provided information. As I have had a very busy week with training and courses I was not able to do some in depth tests yet.
I did some quick and dirty testing with the information in these last 2 posts provided by you. I've tried various settings and combinations but all seem to fail.
I think the problem is somewhere in the Apple Configurator profile, as everything is working very well on my W10 machine. I have also tried on a Macbook but was also unable to connect. I will provide a more detailed log later when I have some more time at home.
Only thing what seems to be different in my setup is that I'm not using a self-signed certificate from a pfSense CA. There I was thinking it was not necesarry to add this certificate into the Apple Configurator profile. I'm using a Let's Encrypt wildcard certificate on my setup -> ACME installation in pfSense with auto-renewal, etc.. So I was thinking, like on my W10 it should work out of the box. However I did some quick tests with the settings provided by you guys (Machine Authentication, Server Certificate Issues Common Name, Server Certificate Common Name, etc..) but all with the same result.
Anyway I justed wanted to let you know I'm not inactive but currently have no time to perform further troubleshooting. I will update this topic further this weekend with more screenshots and error logs.
Thanks!