site-to-site, cannot ping from one lan to other lan
-
hi to all and thanks for reading this,
in my home lan, I have netgate sg100 and the pfsense is running in azure cloud.from the server/negate.sg110 web interface I can ping virtual computers behind the azure.pfsense
from the azure.pfsense.client web interface, I can ping physical computers behind my netgate sg1110.however,
I cannot ping from a physical computer behind my netgate to a virtual computer behind the azure pfsense
I cannot ping from a virtual computer behind azure pfsense to a physical computer behind my netgate.sg1110I thought that since I had added the correct "IPv4 Remote network" on the server and client, that I should be able to ping from computer to computer.
Do I need a add a manual route somehow and if so, how might I do that?
or what do you suggest?thanks very much,
david -
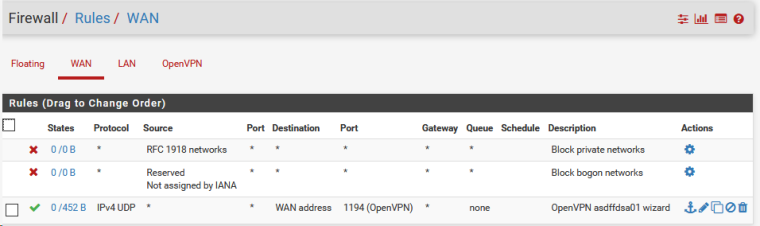
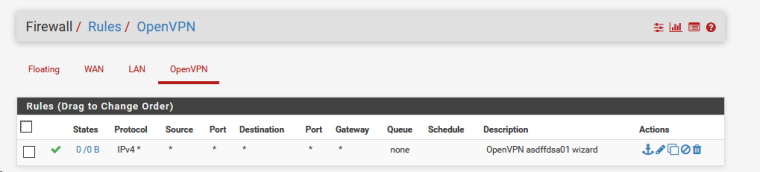
Show both sides OpenVPN and firewall settings (screenshots).
-Rico
-
hi rico, and thanks.
also, from the sg1110, i can ping 10.0.0.7, which is the ip address of the azure openvpn client's lan side ipaddress.
and from the azure openvpn client, I can ping 192.168.62.1, which is sg1100 server's ip address on its lan side.this is from the netgate sg1110 openvpn server, which I am really liking.
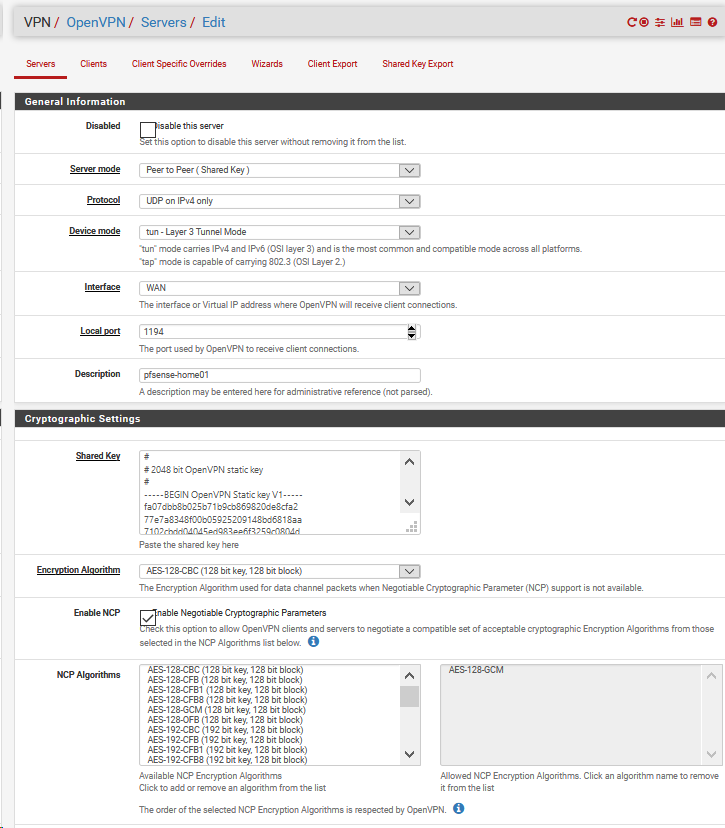
from azure pfsense openvpn client
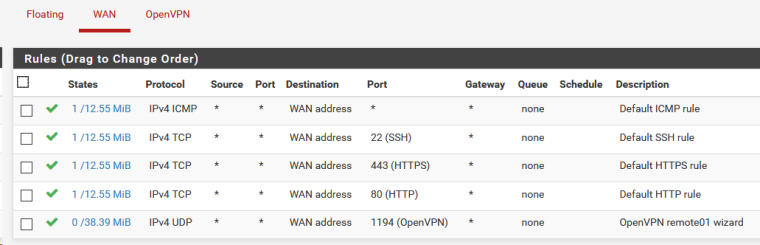
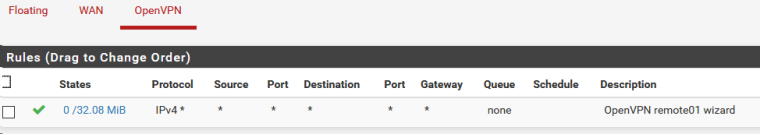
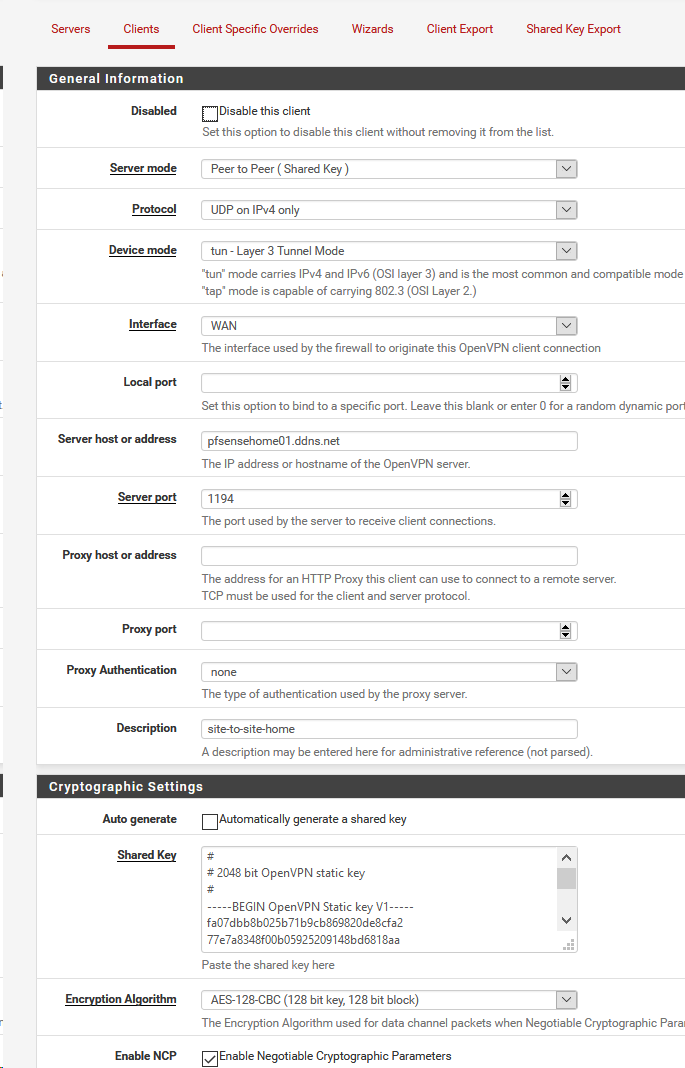
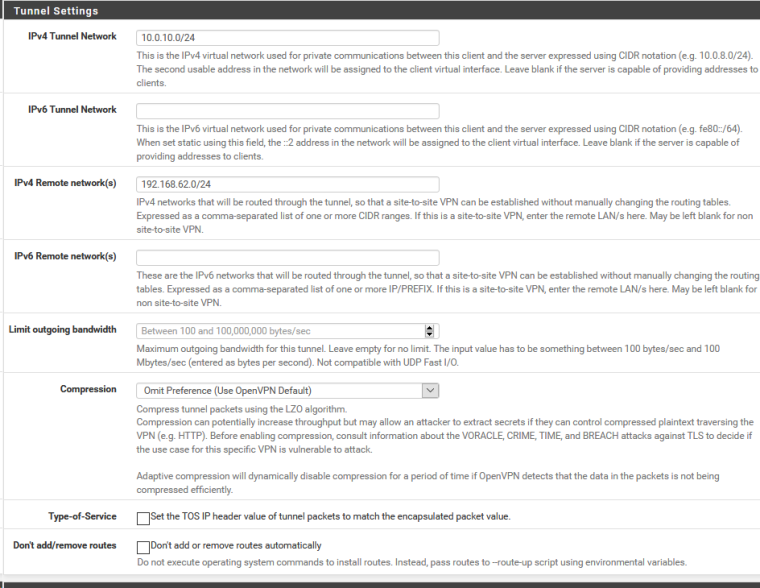
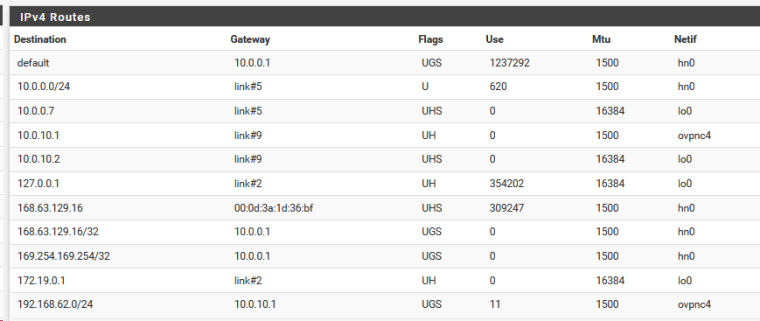
-
@asdffdsa6131
Hey
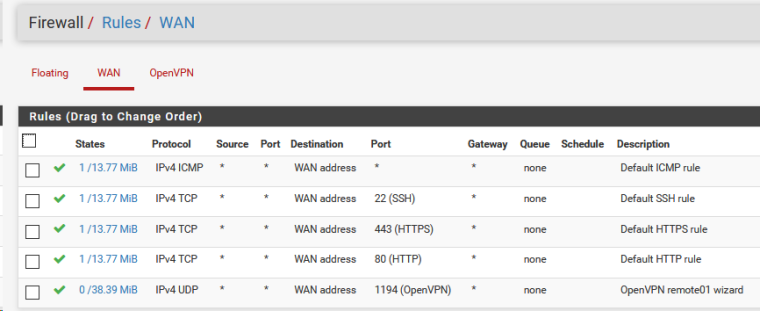
Try to check the rules on the WAN interface OPENVPN client. They are configured to only allow traffic for 10.0.0.7 .
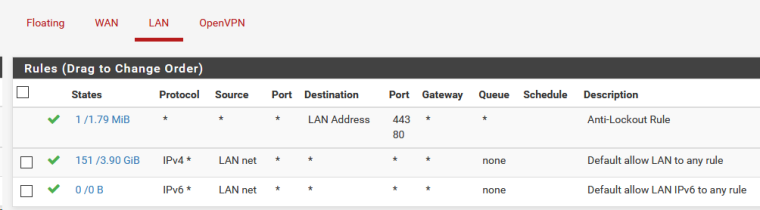
And show rules for Lan interface of OpenVPN serverCheck the firewall logs (status/system logs/Firewall) on both sides
Are there any blocked packets? -
Konstanti, thanks for the fast reply.
here are the rules for wan interface of the openvpn client
and here are the rules for the lan interface of the openvpn server
I am confused as I think the values for IPv4 Remote network(s) for both server and client are correct.
thanks so much
-
@asdffdsa6131
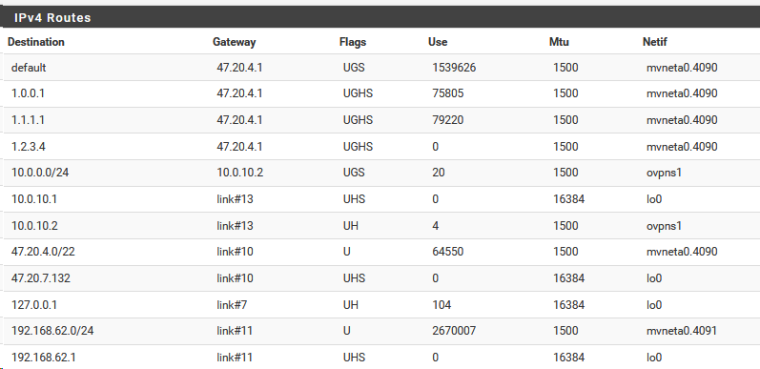
The problem , I think, is not routing
According to the routing tables, it seems that everything is correct
Look at the firewall logs on the Openvpn client side -
thanks, I tried I cannot find where to look for the logs for the firewall.
and should I do someting like a continuous ping from the a computer on the server side to a computer on the client side, so as to trigger someting useful in the firewall logs?
again thanks -
@asdffdsa6131
What is host 10.0.0.1 ??
How to set up routing from virtual machines ?
They know, that network 192.168.62.0 / 24 need to seek through 10.0.0.7 ?
And on wan interface 10.0.0.7 you need allow traffic to 192.168.62.0/24I think you should do this.
1 configure static routes on virtual machines for network 192.168.62.0 / 24 through 10.0.0.7
2. create rules on wan interface 10.0.0.7 to allow traffic for network 192.168.62.0 / 24 -
thanks, this is not making sense, as I am no expert in linux and new to pfsense but all the settings look correct, the openvpn server settings, the openvpn client settings, the firewalls and routes.
but what has me confused is that the pfsense server in azure, only has a single interface of WAN, but there is not a lan interface. for me that makes no sense and is confusing.
10.0.0.1, that is the default gateway for my azure virtual machines
here is the ipconfig /all from a windows.10 virtual machine
Ethernet adapter HyperV:
Connection-specific DNS Suffix . : llb4b2ht4myejjazjx4yah4a0c.bx.internal.cloudapp.net
Description . . . . . . . . . . . : Microsoft Hyper-V Network Adapter
Physical Address. . . . . . . . . : 00-0D-3A-1C-73-51
DHCP Enabled. . . . . . . . . . . : Yes
Autoconfiguration Enabled . . . . : Yes
IPv4 Address. . . . . . . . . . . : 10.0.0.4(Preferred)
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Lease Obtained. . . . . . . . . . : Thursday, February 21, 2019 2:46:26 PM
Lease Expires . . . . . . . . . . : Wednesday, April 2, 2155 10:51:01 PM
Default Gateway . . . . . . . . . : 10.0.0.1
DHCP Server . . . . . . . . . . . : 168.63.129.16
DNS Servers . . . . . . . . . . . : 168.63.129.16
NetBIOS over Tcpip. . . . . . . . : Enabled -
@asdffdsa6131
As far as I understand , now PFSense - an internal host in a network 10.0.0.0/24 on which port 1194 from the main router is forwarded . Right ?I think you should do this.
1 configure static routes on virtual machines for network 192.168.62.0 / 24 through 10.0.0.72 create rules on wan interface 10.0.0.7 to allow traffic for network 192.168.62.0 / 24
-
@konstanti hi there,
correct, pfsense server is an internal host of 10.0.0.0/24 and its ip address is 10.0.0.7
and from my computer, 192.168.62.181, behind the sg1110, I can ping 10.0.0.7. -
ok. can you please be a little more specific as to what needs to be done on the openvpn server and openvpn client.
I am new to linux, pfsense and azure, I have been many days getting this far and I am growing from the experience.
I am not asking you for exactly what needs to be done, in 100% detail but a more detailed outline?
thanks again. -
@asdffdsa6131
This is easily explained, it is a feature of PFSense, an icmp packet that has passed through The OpenVPN client interface rule , is considered good and it is not blocked . But you can not ping , for example, 10.0.0.4 from your local computer , because the computer 10.0.0.4 knows nothing about the network 192.168. and sends the answer to 10.0.0.1 ( if you create the NAT OUTBOUND rule on the wan interface 10.0.0.7 for the network 192.168 , you can ping the entire network 10.0.0.0/24.
And in the opposite direction there is no (10.0.0.0 - >192.168.)
As much as I did , I wrote above
1 static routes
2 an allow rule for the network 192.168 on the WAN interface 10.0.0.7 -
ok. i will work on that thanks much
-
@asdffdsa6131
what is the guest operating system on the virtual machines ? For example, 10.0.0.4 ? -
ms.windows.10
-
@asdffdsa6131
1.From windows cli
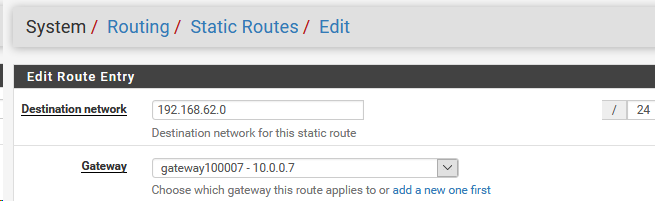
route add 192.168.62.0 mask 255.255.255.0 10.0.0.7
2 Create an allow rule for the network 192.168 on the WAN interface 10.0.0.7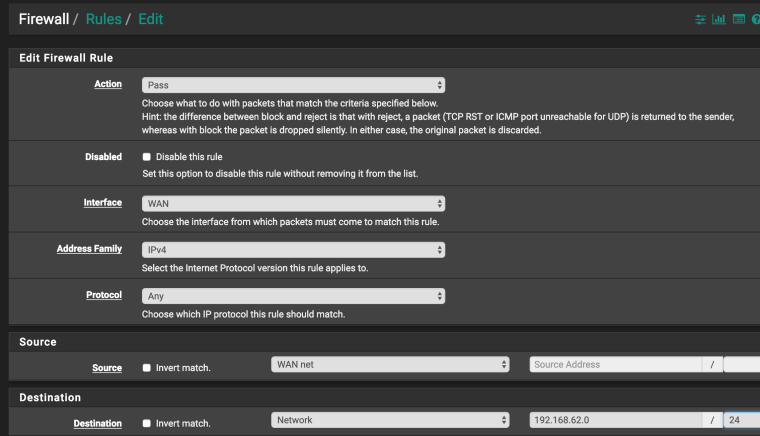
-
newbie question, on 10.0.0.7, the openvpn client, the outbound nat rule mode is automatic outbound nat rule generation and there is no option for adding rules, but I can add a mapping.
should I add a mapping or do I need to change the outbound nat mode? -
@asdffdsa6131
Do not create a NAT OUTBOUND rule yet
Try to do as I wrote in the previous postIf I understand everything correctly, you will be able to ping 10.0.0.4 from a network 192.168.62.0 / 24 and Vice versa
-
on the openvpn client, I did
on 10.0.0.7, the openvpn client, the outbound nat rule mode is automatic outbound nat rule generation and there is no option for adding rules, but I can add a mapping.
should I add a mapping or do I need to change the outbound nat mode?