site-to-site, cannot ping from one lan to other lan
-
@asdffdsa6131
As far as I understand , now PFSense - an internal host in a network 10.0.0.0/24 on which port 1194 from the main router is forwarded . Right ?I think you should do this.
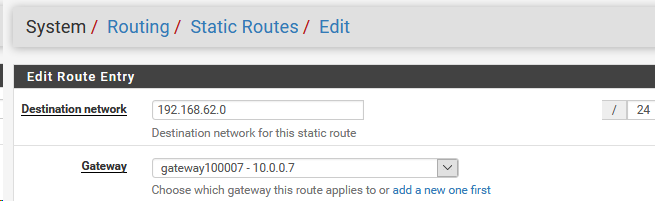
1 configure static routes on virtual machines for network 192.168.62.0 / 24 through 10.0.0.72 create rules on wan interface 10.0.0.7 to allow traffic for network 192.168.62.0 / 24
-
@konstanti hi there,
correct, pfsense server is an internal host of 10.0.0.0/24 and its ip address is 10.0.0.7
and from my computer, 192.168.62.181, behind the sg1110, I can ping 10.0.0.7. -
ok. can you please be a little more specific as to what needs to be done on the openvpn server and openvpn client.
I am new to linux, pfsense and azure, I have been many days getting this far and I am growing from the experience.
I am not asking you for exactly what needs to be done, in 100% detail but a more detailed outline?
thanks again. -
@asdffdsa6131
This is easily explained, it is a feature of PFSense, an icmp packet that has passed through The OpenVPN client interface rule , is considered good and it is not blocked . But you can not ping , for example, 10.0.0.4 from your local computer , because the computer 10.0.0.4 knows nothing about the network 192.168. and sends the answer to 10.0.0.1 ( if you create the NAT OUTBOUND rule on the wan interface 10.0.0.7 for the network 192.168 , you can ping the entire network 10.0.0.0/24.
And in the opposite direction there is no (10.0.0.0 - >192.168.)
As much as I did , I wrote above
1 static routes
2 an allow rule for the network 192.168 on the WAN interface 10.0.0.7 -
ok. i will work on that thanks much
-
@asdffdsa6131
what is the guest operating system on the virtual machines ? For example, 10.0.0.4 ? -
ms.windows.10
-
@asdffdsa6131
1.From windows cli
route add 192.168.62.0 mask 255.255.255.0 10.0.0.7
2 Create an allow rule for the network 192.168 on the WAN interface 10.0.0.7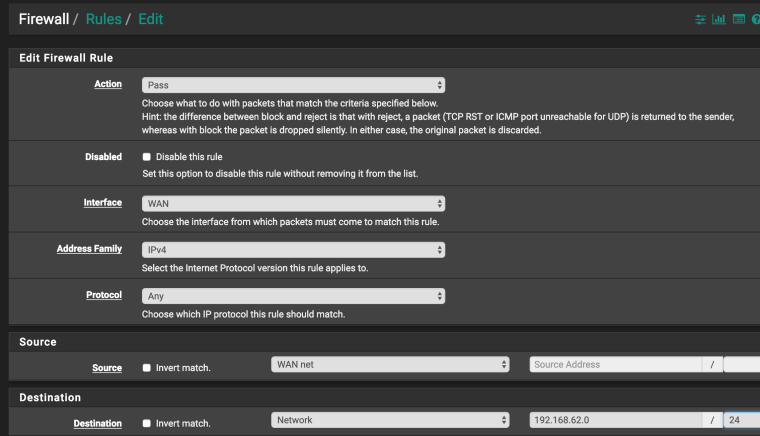
-
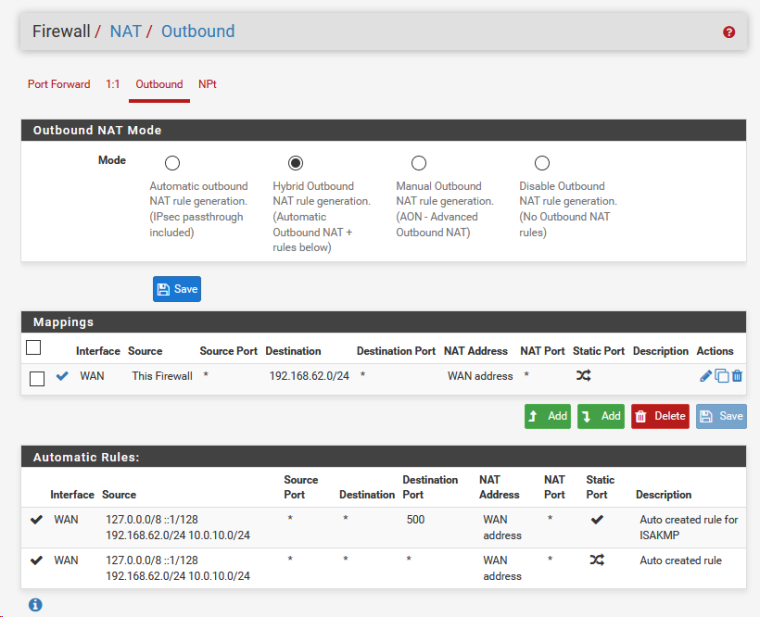
newbie question, on 10.0.0.7, the openvpn client, the outbound nat rule mode is automatic outbound nat rule generation and there is no option for adding rules, but I can add a mapping.
should I add a mapping or do I need to change the outbound nat mode? -
@asdffdsa6131
Do not create a NAT OUTBOUND rule yet
Try to do as I wrote in the previous postIf I understand everything correctly, you will be able to ping 10.0.0.4 from a network 192.168.62.0 / 24 and Vice versa
-
on the openvpn client, I did
on 10.0.0.7, the openvpn client, the outbound nat rule mode is automatic outbound nat rule generation and there is no option for adding rules, but I can add a mapping.
should I add a mapping or do I need to change the outbound nat mode? -
are you running a different version of pfsense, as your screenshot look visually different
-
@asdffdsa6131
- 10.0.0.7 already knows about this network

No need to create another static route on 10.0.0.7 for network 192.168.62.0 / 24
Don't need to configure OUTBOUND NAT now
Need to, for example- on host 10.0.0.4, run the route add command ( see previous post)
- create allow rule (see previous post)
Then you can ping the host 10.0.0.4 from the network 192.168.62.0/24
and the host 10.0.0.4 will be able to ping the network 192.168.62.0/24https://forum.netgate.com/topic/140925/site-to-site-cannot-ping-from-one-lan-to-other-lan/17
- 10.0.0.7 already knows about this network
-
thanks but i added the firewall rule in openvpn client and the route add 192.168.62.0 mask 255.255.255.0 10.0.0.7 on 10.0.0.4
but no pinging.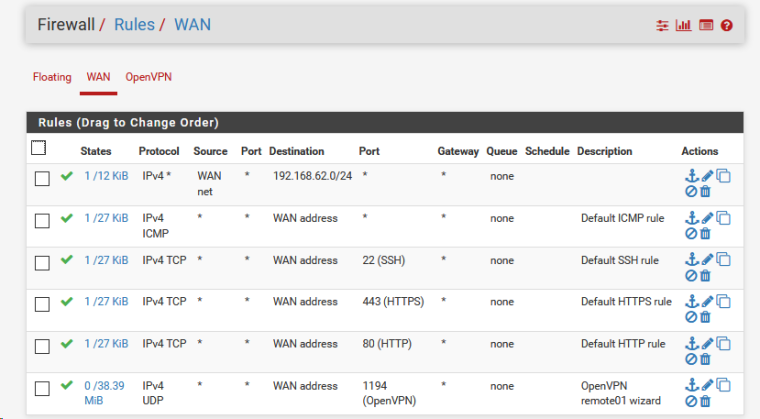
and added the "route add 192.168.62.0 mask 255.255.255.0 10.0.0.7"C:\Users\user01>route print
Interface List
7...00 0d 3a 1c 73 51 ......Microsoft Hyper-V Network Adapter
8...00 ff e3 05 f1 eb ......TAP-ProtonVPN Windows Adapter V9
6...00 ff d6 ca 59 0c ......TAP-Windows Adapter V9
1...........................Software Loopback Interface 1IPv4 Route Table
Active Routes:
Network Destination Netmask Gateway Interface Metric
0.0.0.0 0.0.0.0 10.0.0.1 10.0.0.4 10
10.0.0.0 255.255.255.0 On-link 10.0.0.4 266
10.0.0.4 255.255.255.255 On-link 10.0.0.4 266
10.0.0.255 255.255.255.255 On-link 10.0.0.4 266
127.0.0.0 255.0.0.0 On-link 127.0.0.1 331
127.0.0.1 255.255.255.255 On-link 127.0.0.1 331
127.255.255.255 255.255.255.255 On-link 127.0.0.1 331
168.63.129.16 255.255.255.255 10.0.0.1 10.0.0.4 11
169.254.169.254 255.255.255.255 10.0.0.1 10.0.0.4 11
192.168.62.0 255.255.255.0 10.0.0.7 10.0.0.4 11
224.0.0.0 240.0.0.0 On-link 127.0.0.1 331
224.0.0.0 240.0.0.0 On-link 10.0.0.4 266
255.255.255.255 255.255.255.255 On-link 127.0.0.1 331
255.255.255.255 255.255.255.255 On-link 10.0.0.4 266Persistent Routes:
NoneIPv6 Route Table
Active Routes:
If Metric Network Destination Gateway
1 331 ::1/128 On-link
1 331 ff00::/8 On-linkPersistent Routes:
None -
@asdffdsa6131
Hmmm.
Let's check.
I see that packets went in the direction 192.168.62.0/24
Check to see if the numbers appear in this place ?
This is a rule on the OpenVpn server interface
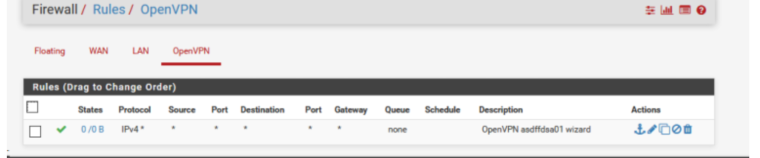
Can host 10.0.0.4 ping 192.168.62.1 ?
Can host 192.168.62.1 ping 10.0.0.4 ? -
hi again,
I have a continuous ping from 10.0.0.4 to 192.168.62.1 and it is 'request time out' -
@asdffdsa6131
On the Openvpn server side
In WEBGUI
/Diagnostics/Packet Capture /
Interface Openvpn
Protocol ICMP
Startwhat is the result ?
-
thank much,
18:05:09.356421 IP 192.168.62.181 > 10.0.0.4: ICMP echo request, id 1, seq 15875, length 40
18:05:11.355996 IP 192.168.62.181 > 10.0.0.4: ICMP echo request, id 1, seq 15876, length 40
18:05:13.344929 IP 192.168.62.181 > 10.0.0.4: ICMP echo request, id 1, seq 15877, length 40 -
@asdffdsa6131
Now the same is on the Openvpn client side
WAN interface only
we continue to ping 192.168.62.181 > 10.0.0.4 -
192.168.62.181 is my windows 10 laptop