Site to site tunnel routing through wrong VPN network half the time
-
Sorry viragomann but this is just not true.
@int0x1C8 : What happens if you disable your RAS ovpns1? The site to site is working stable in your testing then? Sounds more like a wrong configuration in your RAS somewhere.
A good starting point/checklist is https://docs.netgate.com/pfsense/en/latest/book/openvpn/troubleshooting-openvpn.html-Rico
-
Well of course it works if I disable the RAS, since then it doesn't have another tunnel to get routed into.Just tried it and it is still trying to route into the disabled server.It wasn't actually disabled, now it is and the site-to-site is working 100% in both directions. Anything in the RAS config that I should look at in particular? -
Show your complete config of both sides with screenshots.
-Rico
-
ovpns3 HQ site-to-site tunnel server config:
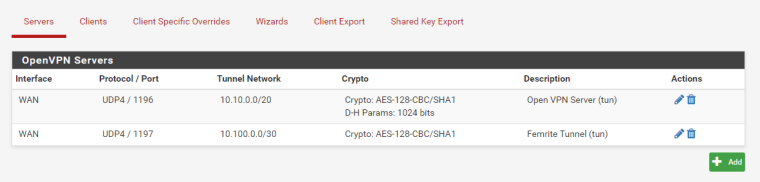
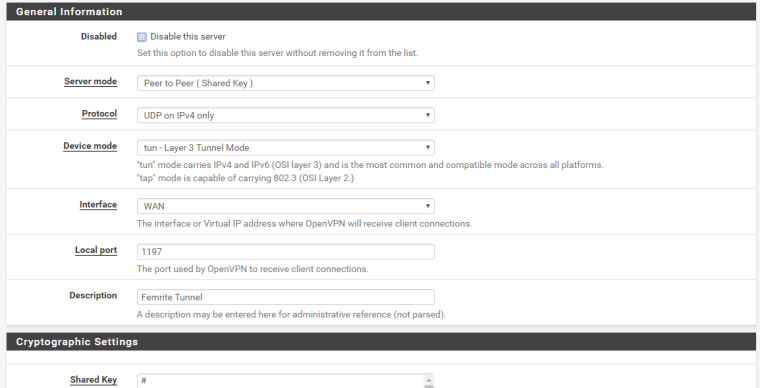
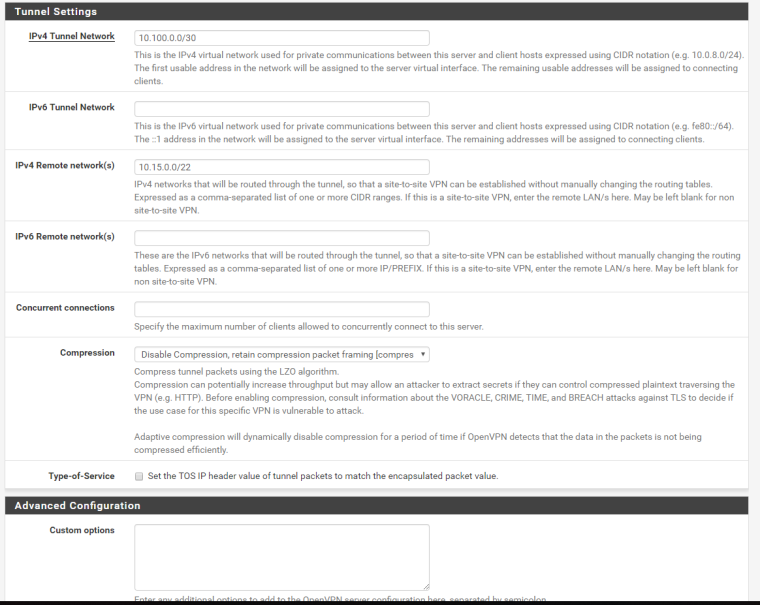
ovpnc1 site B site-to-site tunnel client config:
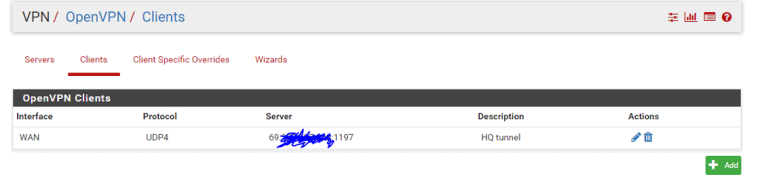
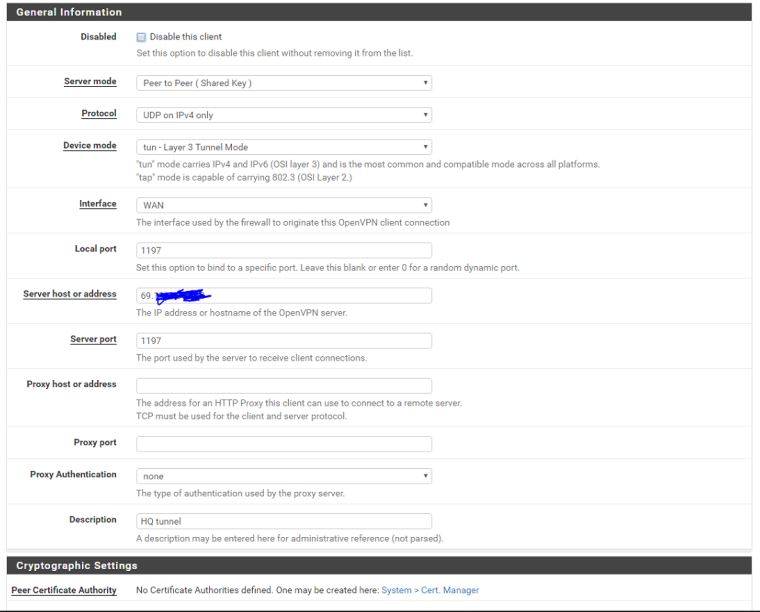
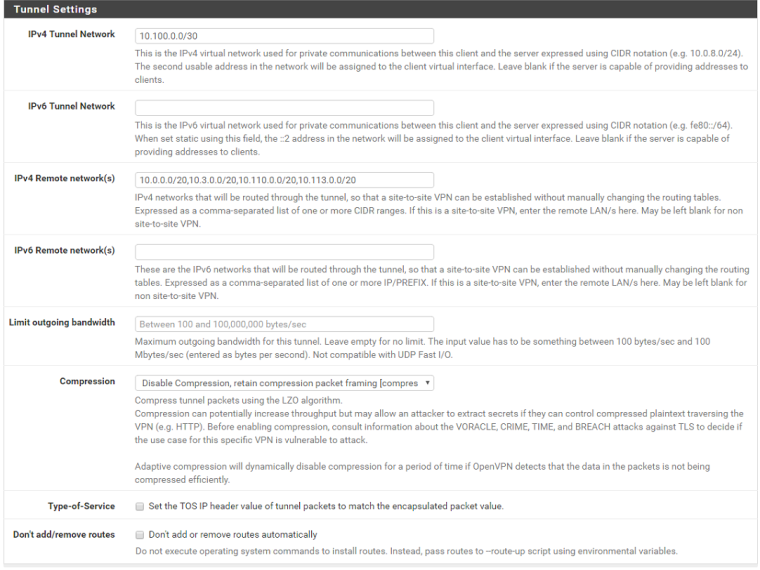
ovpns1 HQ remote access server config:
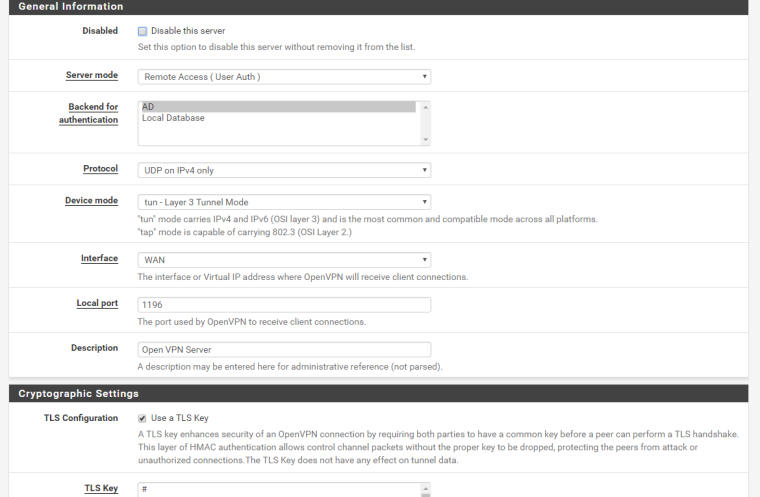
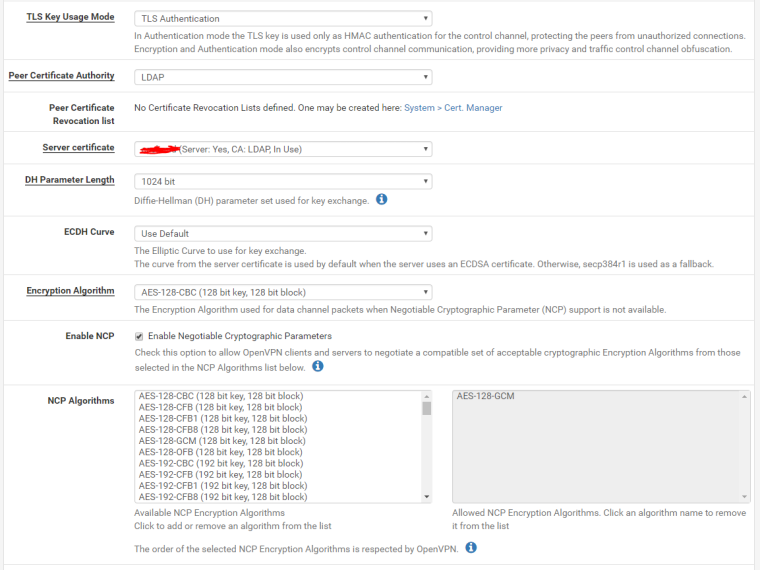
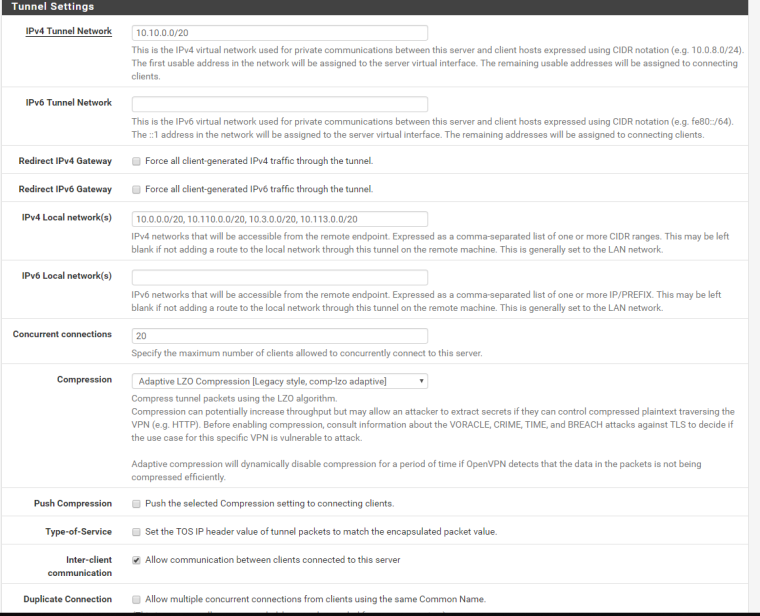
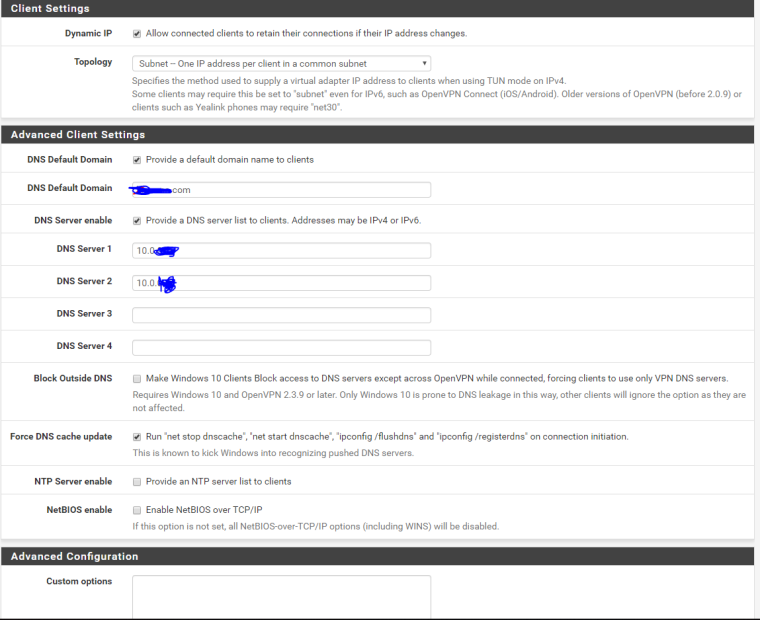
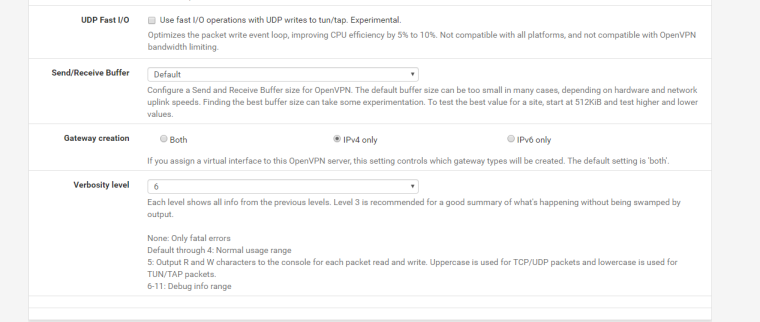
And here's the route table for pfsense at Site A:
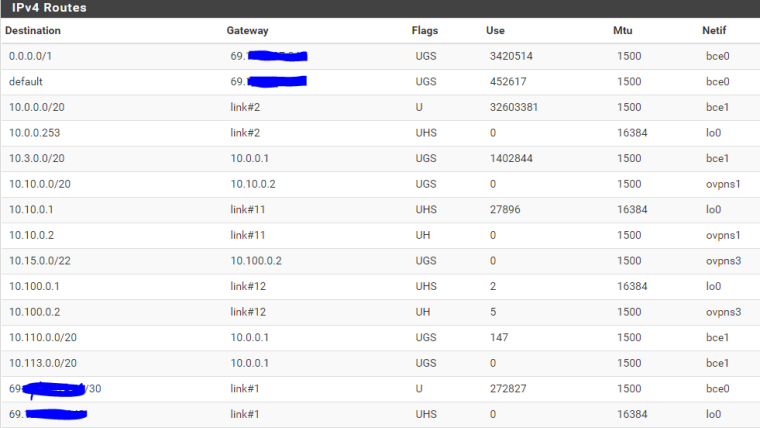
Here you can see states when routing correctly:
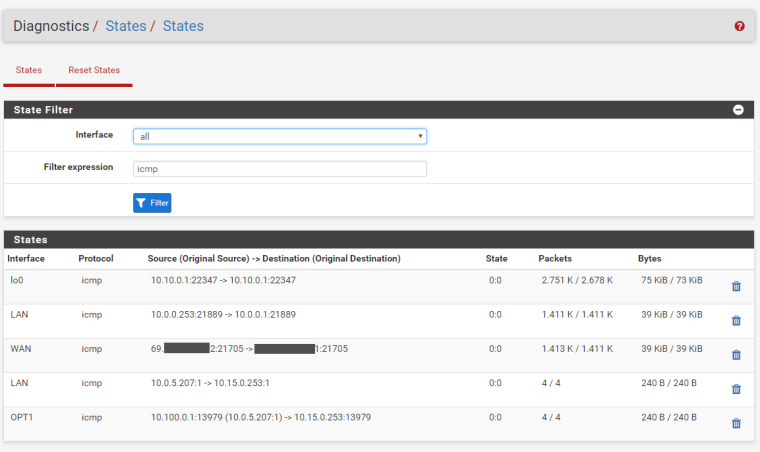
And failing: note in the first one, a state is opened up at first for both tunnels/interfaces, but they are switched around
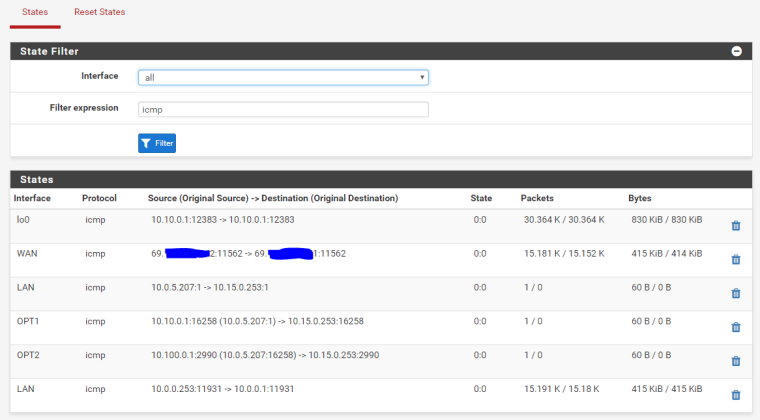
then one of the states disappears after a second:
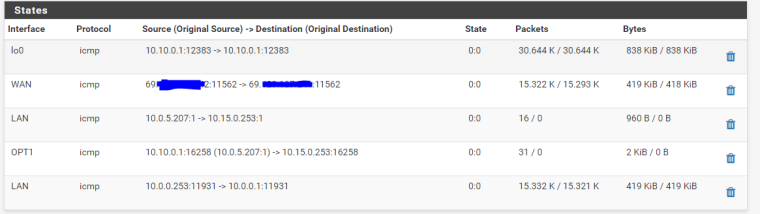
If you need anything else let me know.
-
Please disable Inter-client-communication and try again.
-Rico
-
I did and still seeing same behavior. Do I need to fully reboot pfsense? Also we have not yet re-exported the client for that VPN instance since upgrading to 2.4.x, would that have any effect?
-
Well trying a reboot with any strange behavior is always a good idea.
Exporting the client config file does not touch anything tho.-Rico
-
Ok it seems to be working now. The winning combination was to assign but not enable the ovpns3 interface as OPT1, disable ALL autogenerated NAT outbound rules that applied to VPN interfaces or networks, and then disable inter-client communication on the RAS config as Rico said above. My theory on why this worked is that in pfsense any OpenVPN server is in the OpenVPN interface group, so NAT rules applied to OpenVPN instead of the OPTx interfaces specifically affect all VPN traffic. In addition, perhaps having inter-client communication configured on one of the VPN instances made pfsense think that all OpenVPN interfaces could inter-communicate. Thus it didn't matter which VPN instance it sent the traffic out, it was expecting it could get from one to the other (which is something we want to enable, but I'm just happy enough it's working for now). Can anyone confirm/deny?
In conclusion to any future seekers of information: if you're seeing the same kind of behavior in routing and state tables, look into NAT outbound rules.
-
@int0x1c8 said in Site to site tunnel routing through wrong VPN network half the time:
In addition, perhaps having inter-client communication configured on one of the VPN instances made pfsense think that all OpenVPN interfaces could inter-communicate
I don't think that's the case because inter client com is internal to (each seperate instance of) OpenVPN. In other words, The host (pfS) does not see the packets travelling between clients. Enabling it should not affect normal routing.
Tried to enable it again? (If you need it)
P.S.
Better not use inter client com (no way to firewall) but instead use firewall rules to control (even selective) traffic between clients. -
I enabled it again and it continues to work which confuses me since one of the first things I tried was to disable NAT rules so I don't know why it didn't work then.