Tunnel is ok but not ping
-
Hi,
I made a vpn "site to site" with ipsec, on the one hand I have pfsense on the other a Netgate appliance.
The tunnel is established correctly and from the network behind pfsense I can ping and access the PC while from the remote network (Lan behind the netgate) you can not ping and you can not access in rdp protocol to the server behind pfsense.
the firewall rule I created on pfsense, about ipsec interface is:
protocol: ipv4*
source: any
port: any
destination: anyDo I have to create some other firewall rule?
Thanks. -
@sasa1
Hey
VTI or IPSEC ?
What is the IP address of the remote computer that needs access ?
What's the address of the RDP server ?
Show phase 2 settings for both sides of the tunnel -
Hi,
IPSec protocol.
The IP Address is:
192.168.2.2
the phase2 configuration (side pfsense) in attach.
On the remote side I haven't the ipsec configuration.
Thanks.
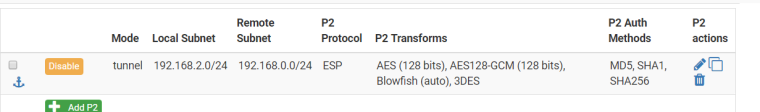
-
@sasa1
Ok
and the second ip address what ?
What are the rules on the LAN interface behind the netgate ? -
the second IP, behind Netgate, is:
192.168.0.1
and from rdp server (behind pfsense) the ping to:
192.168.0.1
is ok.
Side Netgate I haven't configuration file.
Thanks. -
Hi,
I'm sorry but I have provided incorrect information, on the other side there is a Fortigate.
When I try to ping from fortigate to pfsense the traffic I see on pfsense is:
15:18:07.524843 (authentic,confidential): SPI 0xcad9099b: IP 192.168.0.1 > 192.168.2.2: ICMP echo request, id 6656, seq 0, length 64
15:18:08.524267 (authentic,confidential): SPI 0xcad9099b: IP 192.168.0.1 > 192.168.2.2: ICMP echo request, id 6656, seq 256, length 64
15:18:09.524405 (authentic,confidential): SPI 0xcad9099b: IP 192.168.0.1 > 192.168.2.2: ICMP echo request, id 6656, seq 512, length 64
15:18:10.524713 (authentic,confidential): SPI 0xcad9099b: IP 192.168.0.1 > 192.168.2.2: ICMP echo request, id 6656, seq 768, length 64
15:18:11.524393 (authentic,confidential): SPI 0xcad9099b: IP 192.168.0.1 > 192.168.2.2: ICMP echo request, id 6656, seq 1024, length 64Thanks.
-
@sasa1
Hey
That means the tunnel is working.
I would check now the traffic on the PFSENSE LAN interface
Leave the packet in the direction of 192.168.2.2 and comes the answer ? -
Hi,
the problem was solved by modifying, in phase 2, the protocol and Auth Methods as the one configured on pfsense were not compatible with those used on the fortigate.
Thanks.