PLEASE HELP!!! pfSense is slowing down my internet.
-
Is the WAN NIC there pass-through to the VM?
How is the LAN NIC configured in Hyper-V? You might try the legacy NIC type there instead.
I doubt it's an issue with Windows in HyperV but you could throw an Ubuntu client in there on the same subnet just to be sure.
I assume you read this:
https://docs.netgate.com/pfsense/en/latest/virtualization/virtualizing-pfsense-with-hyper-v.htmlSteve
-
Hey Steve,
Sorry for taking so long to respond. It's been a long headache with this thing.
So basically, you were right the issue was the VM. I tried the legacy adapter but I was getting unidentified network and in trying to troubleshoot that my host machine started blue screening on me. So I had to resolve that.
Anyhow after I was back up and running, I tried a new approach. I took an actual hard drive (the one I plan to install in my Mini PC) and set up a new pfsense VM to pass through to the hard drive. This way I can then take the hard drive and boot straight into pfsense without having to reinstall and reconfigure etc. I then used 4 NICs and bridged the hyper-v virtual switched to each of them so I can connect the NIC to actual switches and computers rather than using VMs internal or private networks. When I speed test in the VM using internal virtual switch the speed is slow. But when I use an actual device connected to an actual bridged network adapter, I get full speed coming off the pfsense. So i am think pfsense was not the issue but some misconfiguration in the hyper-v set up somewhere. So while I have not resolved the slow speed in the VM issue, I am sticking a pin in that for now, so I can get my pfsense up and running.
Before re-configuring the OpenVPN in this new hard drive, I decided to try bridging the 3 interfaces that will be used for the LAN side of things. As I said orignally, this whole exercise is to replace my DD-WRT router with pfSense so I can have 2 OpenVPN so i need pfSense to operate like a SOHO router with 1 WAN port and 3 LAN ports.
I have used the following 3 links (plus a fourth that I can't seem to find now) to help me configure the bridge but it is not working
https://www.cyberciti.biz/faq/how-to-pfsense-configure-network-interface-as-a-bridge-network-switch/
http://centosquestions.com/creating-bridge-lan-opt1-pfsense-firewall/
https://eengstrom.github.io/musings/configure-pfsense-bridge-over-multiple-nics-as-lanSo far I have:
- configured the system tunables and toggled the two .member and .bridge settings
- I have created a bridge - some sites said do not include LAN until afterwards and other included it the same time the bridge was created
- added bridge to interfaces
- created firewall rules
- created interface group
- set ip on bridge and configured dhcp server
etc
What is happening is that when I disable the IP on the original LAN port, the bridge interface is not coming up on none of the other NICs. it is not assigning an IP. Tried static and that did not work either.
I will keep trying but I wanted to give you an update of the Speed test issue. The VM is definitely causing an issue there but I will return to that later if need be.
I am new to the forum thing. Should I create a new post for this bridging issue or is it okay to continue troubleshooting it here?
-
@kovon it would be best to start a new thread. If a solution does come up, it'll be easier for someone to search for a term in the heading that applies to the actual issue. Whereas, if you continue in here they'll come to a solution to something they were not expecting.
-
Ok, so let me just say that bridging interfaces in pfSense because you want it to behave like a switch is a bad idea.
If you want a switch, like the switch inside a SOHO router, use a real switch. Or run the SG-3100/XG-7100 which actually have an internal switch.That said you can bridge interfaces and it usually works OK.
Probably going to need screenshots of what you have done. You don't usually need an interface group if you moved filtering off the member interfaces. The rules will all go on the assigned bridge interface.
It's better to try to do this whilst NOT connected to any interface you want to have on the bridge , it's very easy to get locked out. So maybe enable WAN side access or configure another interface to use whilst you do this.
Steve
-
Hey Steve, I responded to your bridging comments on my Bridging post. Please see.
Back to the internet speed issue on pfSense.
After installing pfSense on my mini PC and configuring the 2 OpenVPN Clients in a VPN group as Tier 1 and Tier 2, I have noticed that while the speed test with the VPNs off on pfSense itself is basically the same as on the my desktop computer, I am noticing different speeds when the VPN is on.
With my Tier 2 VPN on :
On my Desktop:
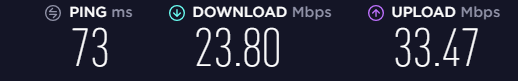
On pfSense:
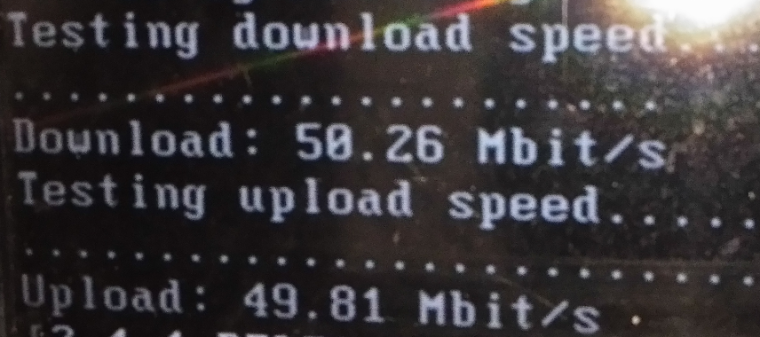
As you can see, pfSense is reporting faster speed than what the client is getting. Can you tell me how to fix that? I want the client to get full speeds to whatever pfSense is capable of.
Another strange issue, When my Tier 1 VPN is on and I try to run speedtest-cli on pfSense, it is picking up my ISP internet as if the VPN is off. So the Client sees the VPN and Tier 1 speed is slower than Tier 2 but pfSense is testing as if the VPN is off. Any ideas as to what I have misconfigured?
Thanks in advance
Kevin
-
What probably happens :
speedtest is using your WAN, not some "VPN WAN".
Clients on your LAN are forced to pas through the/a VPN.Run
speedtest -hand you'll see
... --source SOURCE Source IP address to bind to ...So, bind speedtest the IP of your VPN to force using that interface.
I couldn't test this myself - I have no outgoing VPN.Btw : it's normal that VPN connections are slower then non VPN connections.
Also : speedtest running on your pfSense does not pas through your LAN interfaces (you bridged them). -
Thanks for your response.
I think I understand what you are saying but this is my challenge:
I had my Tier 2 VPN configured on my DD-WRT router and the speed test on my desktop was around the same 60Mbps down 50 Mbps up when the VPN was enabled which is the same speed I am getting on pfSense itself using speedtest-cli. But now the very same VPN configured on pfSense using the exact same hardware is testing barely in the 20s from the very same desktop. The only thing that has changed is the firmware.
So based on what you are saying, on DD-WRT, the VPN traffic my desktop got was using the WAN interface on the router (since I guess there was only one WAN on the routet) and pfSense speedtest-cli is using the same WAN, which is why their speed tests are the same. But now, my desktop is using a different WAN because of these VPN gateway interfaces that had to be created on pfSense.
But the service I am using the VPN for requires a minimum of 20Mbps in order for it to work properly. On DD-WRT, it worked but now on pfSense it is poor.
So my question is how can I reconfigure my VPN to use the WAN interface like pfSense is using and like how my dd-wrt did? And if it cannot, because pfSense is a firewall and everything is now different on a firewall, what changes can I make on the VPN WAN, to make it faster?
The reason I switched to pfSense was to use the 2 VPNs to toggle between them seemlessly and for failover without having to reconfigure a new VPN whenever I needed to switch since I could not have multiple VPNs on DD-WRT via the gui but I never imagined that I would lose speed in the process. I can't lose speed for what I am doing. So how can I get this speed back?
Also, I want to be clear, I know the speed on the VpN is slower than the speed on non-vpn. That's not my issue. The issue is my clients are getting a slower VPN speed on pfSense than they got on DD-WRT. If I can't get back the same speed I got before when the VPN is running, I will have to go back to DD-wrt and forget about having multiple VPNs configured which at this point I was starting to warm up to the idea of having a firewall protect my home network and was prepared to learn it inside out to even help improve my firewall skills at work. So it would be a bummer if I have to switch back.
And also, I have not bridged the LAN interfaces. I abandoned that plan.
I really hoping I can resolve this favourably.
-
What CPU do you have in that firewall? What ping times do you see to the VPN gateway? What encryption settings are you using?
If you are using UDP, which is the default for OpenVPN, then make sure you have fastIO enabled. Increase the send/recv buffers to 512K.
Steve
-
Good Morning Steve
The CPU:
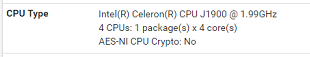
Ping Times and Speed Tests
Ping Times and speeds on desktop at home with all VPNs off:
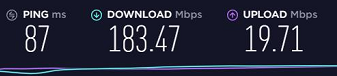
Ping times and speeds on desktop at home with VPN Tier 1 on pfSense:
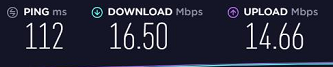
Ping times on desktop at home with VPN Tier 2 using pfSense (WOW!! I have never seen this speeds before. On DD-wrt, max was 65-69 Mbps and last night it was maxing out at 23Mbps. Don't know what is happening this morning.):
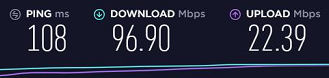
Tested Tier 2 again to be certain (Wow.):
As a comparison, I did speed test at work using VPN clients running on my work desktop.
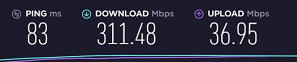
Ping Times of desktop at work with no VPN running:
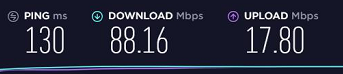
Ping times on desktop at work with VPN Tier 1 using SoftEther VPN CLient:
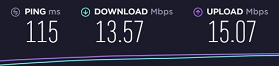
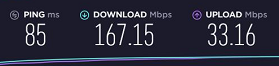
Ping times on desktop at work with VPN Tier 2 using vendor's VPN client (The vendor must have made a change because I never got this sort of speeds at work before. I hope this keeps up):
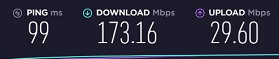
Tested Tier 2 at work again to verify (Speechless):
With the sudden jump in Tier 2 speeds, I don't know what to make of it.
Anyhow to answer the rest of your questions:
My Tier 2 vendor provided guides for configuring openvpn on DD-WRT and pfSense. On their DD-WRT guide, they said to use Blowfish CBC but on their pfSense guide they said to use AES-128-CBC. Last night, I tried changing the encryption of the pfSense to BF-CBC but there was not much difference, now this morning it has boosted up significantly. Other differences in the vendor's configuration was DD-WRT said LZO-Comp No while pfSense was Adaptive. Also, custom options were completely different. I email my Vendor's support last night to ask them about the differences in their configuration guides but they said they forwarded it to their technical department so I am yet to hear back from them. I wonder if the boost in the VPN on pfSense is as a result of my query or if it coincidental?My Tier 1 VPN is a VPN I built myself on a VPS I recently got. So that configuration is basically me "trial-and-error-ing" until I got it to work. I did how configured it exactly like my Tier 2 vendor's configuration and then tweaked until it worked.
On the Tier 2, I enabled FastIO and increased the buffer size to 512KiB. But the speed test on my desktop at home went back to last night's speeds:
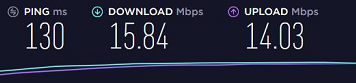
I disabled FastIO and set the buffer size back to Default and the steed test on my desktop at home was this:
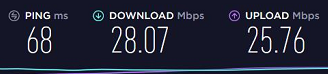
So I am now uncertain what to do to get back those blistering VPN speeds I got earlier. Or maybe they were indeed flukes.
I did a speedtest again on my desktop at work with the Tier 2's vendor's vpn client and the speeds are still extremely high:
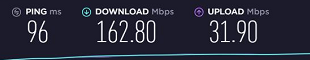
So its definitely some configuration in pfSense that makes the speeds inconsistent. I will leave it as is and see if it goes back high after a few hours.
Regards
-
FastIO will only help if the provider is using UDP, which they probably are.
I would expect to see around 100Mbps from that CPU in a local test. The latency will reduce that and the encryption may not be optimal but that 96Mbps figure doesn't seem unreasonable.
If the tier 1 gateway is completely under your control you should be able to optimise that for best throughput.
100ms is a high latency though for both of those. I assume they are both far away from you.
Steve
-
Wow Ok.
Well I never saw those kinds of speeds with the VPN on. I saw them on my WIFI with the VPN off. But via ethernet with the VPN on is new for me. I like though. I would very much like to replicate and make it the standard.
Yes the Tier 1 I created as a proof of Concept to see if it would give me access to some stuff, I am not able to access on my Tier 2. Hence why I want to make it my Tier 1. The only issue is that I suspect I may be limited by the internet speed available to the VPS. I have to contact the vendor to see what speeds should be expected on the VPS. So I don't know if I will get the same speeds as my Tier 2. However, 20Mbps is the minimum of my heaviest bandwidth services so if I can at least get double that at 40Mbps as a standard, I will be content.
I am new to creating your own VPN server, so I will now have to look into things such as throughput etc.
as it relates to the high latency, yes both gateways are over 2,000 Miles from me give or take.