problems unblocking my sip provider
-
@nogbadthebad said in problems unblocking my sip provider:
Maybe try installing Siproxd
i don't think this is my solution as this seems to be a server that runs sip on my lan, when i already have a stand alone box that does it.
-
I agree, capture some SIP packets and see what's happening.
Sounds like it's registering it's internal IP maybe or something similar. SIProxd might actually help if that is the case.
Steve
-
Insert the :rolleys: smiley here.. SIP was not originally designed to be behind NAT!
It was written in later when services such as Vonage and a couple earlier started to look at the residential market. And it does not work all that well.. Double NAT is not in the spec. If you try your on your own.
In the SIP header you will find (normally) your NATted address. Yes. Building a WAN firewall rule will help in some cases depending on the carrier. Sometimes you need to pay attention to your states when you try to make a call and see what carrier your device is connecting to. SIP from your provider.. RTP from the carrier they use. It is truly a case by case basis.
Few SIP providers will also need static port enabled. Very few these days.
I never port forward to any client devices. All of my SIP customers work flawlessly.
-
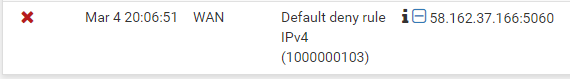
so for an incoming call
if i turn off all the rules i get this:
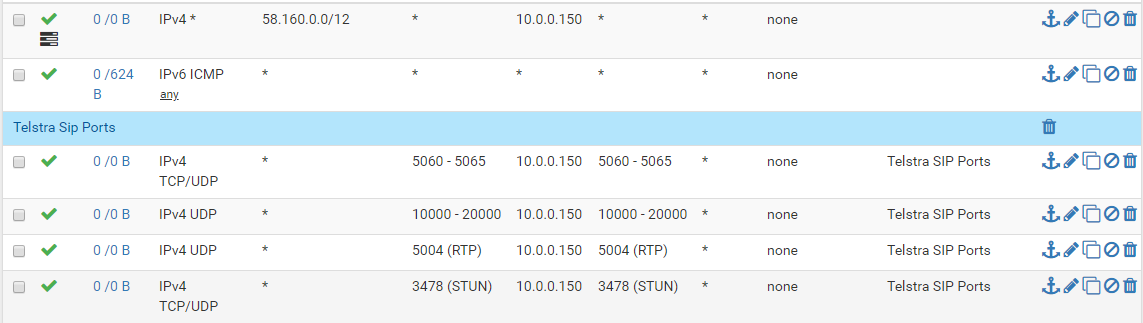
if i open just all the ports in my rules i get:
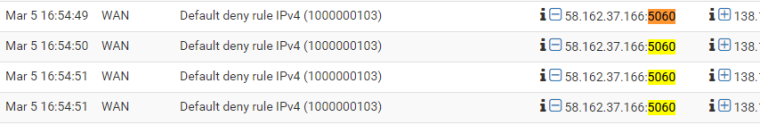
with
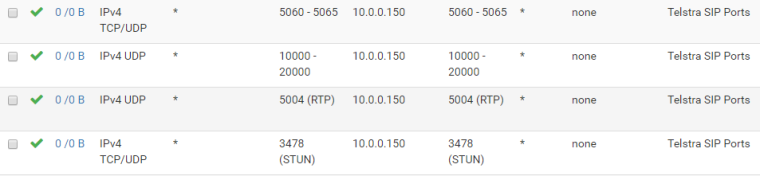
capturing a sip packet i get... a ringing phone? WTF?!?!?!
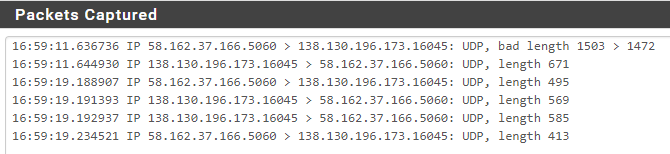
seems its a 1 off though as it didn't ring the next 3 attempts
-
What I expect to happen here is the phone connects out to the SIP server at port 5060. If you don't have static outbound NAT set for the phone IP the source port as that leaves the WAN will be randomised. The phone holds that state open with keepalive packets so that when the provider sends traffic to it for an inbound call it still passes through the firewall.
Since you are seeing it blocked that state is either not being held open or the provider is replying to the wrong port.
Check your state table for the phones IP. See what source port it is using, is it port 5060?
Is it holding open a SIP state at all?It could be you need a static outbound NAT rule.
Can we see that actual packet capture file? The SIP packets there likely contain useful info.
Steve
-
You have ovcercomplicated this and now your troubnleshooting is going to be far more complicated.
I am running a Cisco SIP phone behind pfSense and have been doing it for years with no issues. I also run a SIP client (Bria) on my iOS phone as well as my Mac. All three of them have no issues running behind pfSense.
Your SIP phone will initiate a connection from itself to the SIP provider. Since that connection is initiated on pfSense’s LAN, it also manages the incoming connection back to the phone with no additional configurations required. If you installed a default pfSense box as your router with no additional configurations (other than the ones you need to get your LAN to communicate with the Internet), your phone will work with no issues. The problem is the complexity of your configuration and trying to acutely manage this traffic. Let pfSense do it’s job and when the outgoing connection starts, pfSense will manage the inflow too.
I was on hours of conference calls yesterday with no issues whatsoever. I have a minimal pfSense installation with very few rules in order to reduce the complexity of the installation to ensure that stuff works without me having to go in and continually tweak stuff.
So try ratcheting back all of the features and config you have first. Reduce the complexity and then build up rules from there. When you enable the rule or config that’s killing your SIP connection, you’ll find it this way.
IMHO, YMMV...
-
@randomaustralian said in problems unblocking my sip provider:
I got it to work easily enough last time. i have used a 3rd party router since i got FTTP NBN cause its all PPOE. They don't at all support what i'm doing. I'm putting my ISP supplied router behind my 3rd party router so i can still use all the ISP features that require my ISP supplied router to be used.
But it think pfSense is more secure then IPFire. even when i try to allow the ports and IP addresses in my firewall rules i still can't get incoming calls to work.
I just realized i didn't answer your question properly.
telstra don't expect this to work. the sip host is on their provided edge router and they do not support what i am trying to do...
the thing is I got it to work easily on ipfire. I'm having troubles with pfsense because it seems pfsense is more secure/intelligent with what is allows through. -
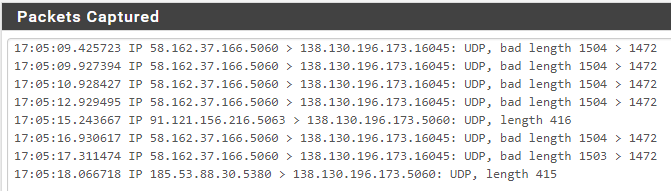
0_1551907391062_packetcapture.7z @stephenw10 said in problems unblocking my sip provider:
What I expect to happen here is the phone connects out to the SIP server at port 5060. If you don't have static outbound NAT set for the phone IP the source port as that leaves the WAN will be randomised. The phone holds that state open with keepalive packets so that when the provider sends traffic to it for an inbound call it still passes through the firewall.
Since you are seeing it blocked that state is either not being held open or the provider is replying to the wrong port.
Check your state table for the phones IP. See what source port it is using, is it port 5060?
Is it holding open a SIP state at all?It could be you need a static outbound NAT rule.
Can we see that actual packet capture file? The SIP packets there likely contain useful info.
Steve
i have tried a LAN rule that allows all outbound from the static address i have assigned to the sip controller device to any wan address. makes no difference.
I'm still pretty sure that pfsense is killing off connections after 15 minutes cause my call cuts out to the second.
-
I am also no longer confident that outbound just "works" cause i've realized i have to call the one number multiple times and the call only goes through after 2 or 3 attempts some times. i didn't realize it before because i got the engaged noise and just thought they were already on the phone. i only noticed now because i have been calling my own mobile/cell so much for generating logs to see whats going on.
-
So you tried an outbound NAT rule with static ports? Not a static IP?
IPFire includes a SIP ALG, do you recall if it needed to be enabled?
If so SIProxd might work for you here.Steve
-
@stephenw10 said in problems unblocking my sip provider:
So you tried an outbound NAT rule with static ports? Not a static IP?
IPFire includes a SIP ALG, do you recall if it needed to be enabled?
If so SIProxd might work for you here.Steve
Someone mentioned SIProxy before. i had a quick look at it and i've never seen anything like it before. and as i keep saying....
i never had to use more then the settings i'm using now on my previous configuration and never had issues.
-
is there a way to can make pfSense stop blocking anything incoming on that port. i know its a security risk i want to try it temporarily and see if it solves my problem
-
So i have added so many firewall rules now that nothing shows up in my logs to do with any incoming or outgoing call attempts. I have also tried disabling snort cause i read a post from 3 years ago that "pfSense works perfectly with snort disabled"
but i am still having the same problems.
-
Try adding a 1:1 NAT rule to the SIP device. Then add a firewall rule on WAN allowing all traffic to that internal IP.
Yes, that's a big risk it exposes the SIP device completely. But that will add static outbound NAT and will pass everything.
If it still doesn't work there's some NAT issue like it's sending it's internal IP. That can only be solved by configuring the SIP device not to do that or using a SIP ALG that translates that.
Steve
-
are you sure its a 1:1 nat rule? i cant specify ports
isnt this what i want?
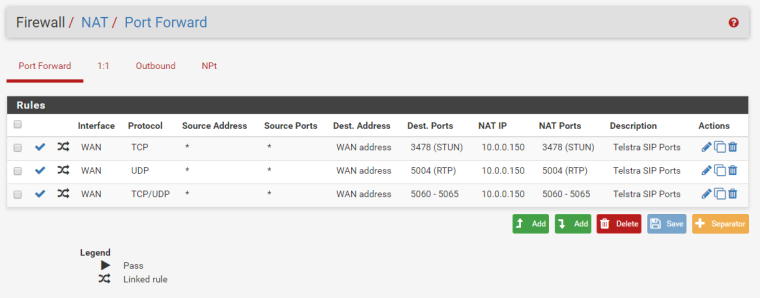
its doesn't work though
-
With a 1:1 rule all ports are forwarded. All incoming traffic will be sent to the SIP device. All outgoing traffic will leave using the same source ports the SIP device sets. That eliminates a number of possible problems.
1:1 NAT rules do not automatically open firewall rules though so you need to add a rule to pass what you need. As a test I suggest just passing everything.
However that will not help if, for example,m the SIP device is using it's private IP is SIP packets as the response address. Only looking at those packets will tell you that. If it is SIProxd could help.
Steve
-
Is there a nice guide for setting up siproxy?
as this is my second dabble with connecting sip devices i really have no idea what i am doing -
Not other than this: https://docs.netgate.com/pfsense/en/latest/packages/siproxd-package.html
That really doesn't tell you much but generally it is discouraged.
The 1:1 NAT did nit help at all? Did you still see blocked traffic?
Have you tried looking at the SIP packets yet to see what IPs the device is sending?
Steve
-
i haven't tried the 1:1 NAT because the incoming IP address in not static, and at one point i had added so many rules added into the firewall that there was nothing appearing in the logs.
i still have the issue were outgoing calls drop after 15 minutes too
-
Might need to review at this point. What exactly do you have in place right now in terms of port forwards and firewall rules and SIProxd?
What VoIP issues are you now seeing?
Steve