VLAN's not working with pfSense and HP1810-24G Switch.
-
Not that not a fan of them... Just much more experience with Cisco, and the few times I have had to deal with HP.. Not impressed with them compared to the cisco use to working with.
For the price of unifi - you could get a pretty much full featured L3 switch from cisco small business line. The sg300 or sg350 line.. I just saw a sg350-28 on amazon for $179.. Its feature set far exceeds the same sort of price point from unifi.
-
@herman said in VLAN's not working with pfSense and HP1810-24G Switch.:
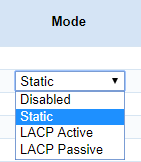
Those are LAGG modes, nothing to do with setting up VLANs.
-
@grimson said in VLAN's not working with pfSense and HP1810-24G Switch.:
@herman said in VLAN's not working with pfSense and HP1810-24G Switch.:

Those are LAGG modes, nothing to do with setting up VLANs.
Thanks for your reply @Grimson .
Gr. Herman
-
The link pippin gave calls out what you need to do
"In HPvania, the terminology used for a port that carries multiple VLANs is a tagged port. On an HP switch, the individual ports are rarely configured directly. Instead, the VLAN itself is configured and the ports are added to the VLAN configuration. "
-
Hi Guys,
Believe it or not, but my problem is solved. Thanks to all the expertise of you guys on here I finally get it going. There are still some issues regarding firewall rules but the VLAN part is working! Thanks to everybody who replied to this topic.
For the other users who might have a HP 18010-24G and a Hyper-V virtualized pfSense I write down what the solution is in my case:
- On the pfsense box create a VLAN10 with ID 10. Assign the interface VLAN10 with the LAN (hn0) interface as parent interface.
- on the Hyper-V host run in a elevated powershell the folowing line: Get-VMNetworkAdapter -VMName "name of vm" | Where-Object -Property MacAddress -eq "mac address of the LAN interface" | Set-VMNetworkAdapterVlan -Trunk -NativeVlanId 1 -AllowedVlanIdList "10". If you have more interfaces connected to the pfSense box for example LAN and WAN, the mac address will modify the right interface. In this case the LAN interface.
- on the HP 1810-24G switch set the port that is connected to the LAN port of the pfSense box for both vlan's to Tagged! In this case VLAN1 and VLAN10 need to be marked as Tagged.
- All the device you want to have in VLAN10 the physical switch port of that device need to be set to Untagged on VLAN 10. VLAN1 should then become Excluded automatically on that port.
- Last but not least create a VLAN10 firewall rule. Tip. Copy the "Default allow LAN to any" and modify the rule from LAN to VLAN10 there were needed.
- Voila! In my case all was working now.
In the above explanation I took VLAN10 and the networks 10.0.0.0/24 and 10.0.10.0/24 as example. Feel free to play around with other vlan's and subnets.
Take also a look at the info other members provided. For me it was a big help and learning curve.
Thanks again guys for all the help and patience.
Cheers Herman
-
If your setting vlan 1 as native - that would be an untagged vlan..
-
@johnpoz said in VLAN's not working with pfSense and HP1810-24G Switch.:
If your setting vlan 1 as native - that would be an untagged vlan..
Both vlans on port 1 set to (T)agged. This setup is working here.
-
Tagged VLAN 1

-
@derelict said in VLAN's not working with pfSense and HP1810-24G Switch.:
Tagged VLAN 1

@Derelict, you are screaming... Please tell me why?
-
And again.. If vlan 1 is native and default which is almost always is.. Since its the default vlan it would be untagged.
There is ZERO reason to tag vlan 1 as you have it designed. That its working is telling me the hyper-v setting is stripping it so pfsense sees it as untagged. Or it wouldn't work.
-
Depending on tagged VLAN 1 will cause you grief from now until forever because vendors do not agree on how that should be handled.
In your position I would fix Hyper-V to understand that VLAN 1 is the untagged, default VLAN.
Or I would cease using VLAN 1 with Hyper-V.
-
Sorry guys, I do not understand it completely. Are you guys saying I should not use VLAN1 (default) at all? Because when I set port 1 in VLAN1 to Untagged, port 1 on VLAN10 will automatically switch to Exclude! When I create an additional VLAN20, then I am able to set port 1 for VLAN10 and 20 to Untagged. Could you please en light me here?
Gr. Herman
-
You can use vlan 1 all you want as native untagged vlan - this is the default vlan on all switches.. But you wouldn't tag it..
Please post the output of
Get-VMnetworkAdaptersVlanAnd the exact setup of pfsense.. Do you have more than 1 vm interface in pfsense? What vswitches is it connected too.. You have different types of vswitches in hyper-v.. Do I really need to fire that crap they call hyper-v back up? ;)
You can use any vlans you want on your switch for your connections to pfsense.. Does not have to be vlan 1..
Derelicts point is you almost never vlan 1 tagged... Why do you think you should tagg it in your switch if you set it as native (or untagged) in your vswitch settings? And how do you have it setup in pfsense.. I you do not have it tagged in pfsense, and you don't have it tagged in your vswitch... Why would you tag it on your physical switch?
-
@johnpoz said in VLAN's not working with pfSense and HP1810-24G Switch.:
And again.. If vlan 1 is native and default which is almost always is.. Since its the default vlan it would be untagged.
There is ZERO reason to tag vlan 1 as you have it designed. That its working is telling me the hyper-v setting is stripping it so pfsense sees it as untagged. Or it wouldn't work.
Sorry Johnpoz, I don't understand. On the HP switch I only can both vlans set to tagged. When I set vlan1 to untagged, vlan10 is set to exclude...
The output results of Get-VMNetworkAdapterVlan ;
This is the LAN interface of the pfSense box.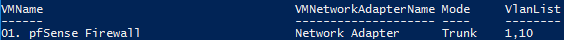
My setup of pfsense box;
Both interfaces are Hyper-V virtual switches.
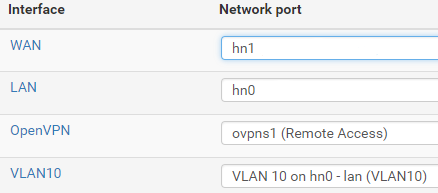
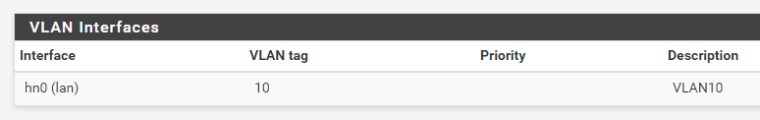
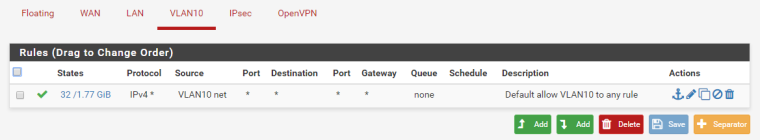
Hope this helps? Let me know if you need more input.
Gr. Herman
-
As far as I know, the HP switches were derived from Brocade.
On the Brocade, if you wish to mix tagged and untagged traffic on a switch port you would set the port to dual-mode.
If you want the PVID to be the default VLAN 1, you would do this:
# vlan 223 # tagged eth 1/1/6 # int eth 1/1/6 # dual-modeVLAN 1 is now the untagged PVID and 223 is tagged
If you want the PVID to be other than VLAN 1, you would do this:
# vlan 223 # tagged eth 1/1/6 # vlan 224 # tagged eth 1/1/6 # int eth 1/1/6 # dual-mode 224VLAN 224 is now the untagged PVID and 223 is tagged.
Both configurations assume a starting point of eth 1/1/6 being a member of only the default VLAN 1.
This is an example of why mixing tagged and untagged traffic on an interface always contains disclaimers stating that different vendors handle things in different ways there.
-
As an aside, adding ports, tagged or untagged, to VLAN 1 is not allowed at all on that switch. A port is a member of untagged VLAN 1 if it is not a member of any other VLAN, or if dual-mode is set as in example 1 above. As far as I know there is no way to tag VLAN 1 at all.
-
@derelict said in VLAN's not working with pfSense and HP1810-24G Switch.:
As an aside, adding ports, tagged or untagged, to VLAN 1 is not allowed at all on that switch. A port is a member of untagged VLAN 1 if it is not a member of any other VLAN, or if dual-mode is set as in example 1 above. As far as I know there is no way to tag VLAN 1 at all.
Hi Derelict,
Thaks for your input. Please have patience with me. I am not a guru like you guys. I wish to have all that knowledge!
This is how I configured the HP switch.
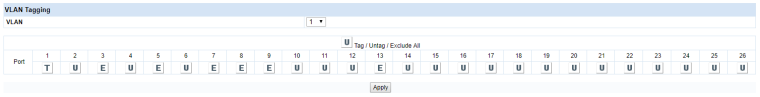
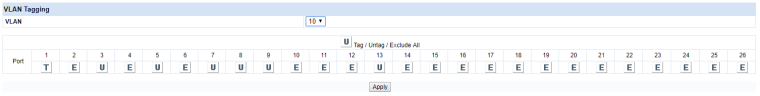
Gr. Herman
-
What port are we talking about?
-
@derelict said in VLAN's not working with pfSense and HP1810-24G Switch.:
What port are we talking about?
Port 1 is connected to the LAN interface of the pfSense. Is that what you mean?
-
So set VLAN 1 on port 1 to Untagged.