Cannot ping through AWS pfSense Instance
-
We are busy evaluating pfSense for our requirements and have spent 2 days attempting to resolve an issue:
- We have 2 instances on AWS: SERVER1 and PFSENSE
- We connect to an external network, SERVER2 via an IPSec Tunnel (Tunnel is connected)
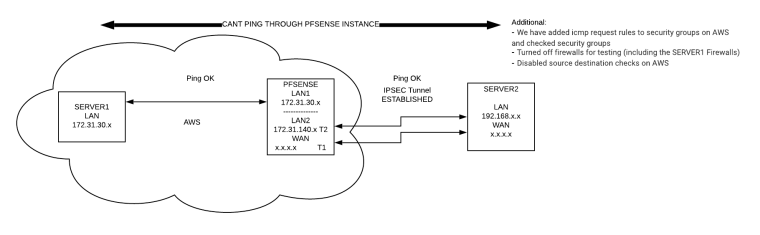
PFSENSE AWS Instance can ping SERVER2 (ipsec) and can ping SERVER1 (eth):
SERVER 1 <--- PFSENSE can ping---> SERVER2SERVER1 Can Ping PFSENSE
SERVER2 can Ping PFSENSESERVER1 cannot ping through PFSENSE to SERVER2: SERVER1 cant ping ------> SERVER2
SERVER2 cannot ping through PFSENSE to SERVER1: SERVER2 cant ping ------> SERVER1We have added icmp request rules to security groups on AWS and checked security groups
Turned off firewalls for testing (including the SERVER1 Firewalls)
Disabled source destination checks on AWSIssue is pinging through the AWS / PFSENSE Instance
Any assistance would be greatly appreciated - thanks
-
I, for one, am going to need a diagram with more specifics to even hazard a guess as to where the problem is. Please be as specific as possible including subnets, what host IP addresses cannot connect to what, etc.
-
In AWS, by default, an instance cannot act as a router (forward traffic). To change this, right-click the instance in EC2, mouse over Networking, then click "Change Source/Dest. IP Check". A window will come up. Click "Yes, disable". This just allows different IPs to come from the instance than the one(s) assigned.
-
Thanks for the prompt responses - I have attempted a diagram, please find attached - does this assist?
Thanks
-
Does the VPC know to route traffic for 192.168.X.X to the pfSense LAN1 interface?
-
@derelict said in Cannot ping through AWS pfSense Instance:
192.168.X.X
Thanks Derelict,
On the VPC I have the following Routes:
Destination =Target172.31.0.0/16 = local
0.0.0.0/0 = IGW
SERVER2 IP (192.168.x.x) = PFSENSE LAN2 ENI (LAN2)Does that look right?
Thanks
-
Seems right. So packet capture on the pfSense LAN2 and see what you see when you ping both ways.
Be sure source/dest check isn't enabled on the interface too. It has always been a little unclear to me what happens when it is enabled on the instance and not on the interfaces, vice versa, etc. I generally just disable it everywhere I see it.
-
3 days of troubleshooting, you are a legend!! The issue was source/dest on the interface level (thought it was only on instance level).
Thanks heaps - much appreciated!