Cascading pfSense Routers
-
So,
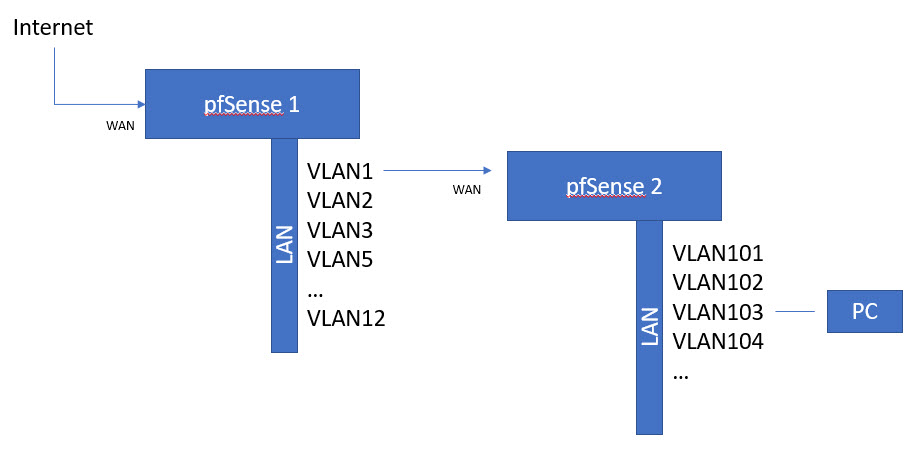
I have a pretty sophisticated pfSense configuration at home wherebyI have multiple VLAN's haing off a couple of LAN interfaces of pfSense. I use Aliases to create isolation between these VLAN's and that works well, but mainly as I only have 8 VLAN interfaces to deal with.
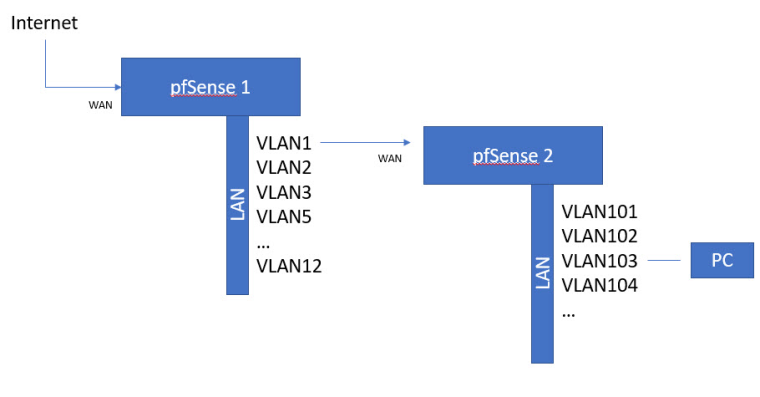
I want to add pretty much an entirely new set of VLANS, which will each need sets of isolation rules between each other and those VLAN's upstream, so I'm thinking to better manage these new VLAN's it makes sense to group them under a cascaded router. That way I can manage these Alisases independently of the ones upstream.
I have configured my first router with 192.168.x.x VLANs, one of which 192.168.20.x will be on the same network as the WAN interface of the cascaded router. And the LAN interface ( that I will host the new VLAN's on ) is 172.16.100.x.
I have setup some basic pass rules, and I have a server on 172.16.100.11 that is able to reach the internet ok as you can see by this tracert log;
1 <1 ms <1 ms <1 ms router-external.mwaa.com.au [172.16.100.1]
2 <1 ms <1 ms <1 ms 192.168.20.1
3 <1 ms <1 ms <1 ms 192.168.0.1
4 * * * Request timed out.
5 15 ms 8 ms 9 ms *** IP ADDRESS MASKED ***
6 10 ms 15 ms 9 ms bundle-ether4.chw-edge901.sydney.telstra.net [3.50.12.108]
7 11 ms 10 ms 9 ms bundle-ether13.chw-core10.sydney.telstra.net [3.50.11.98]
8 9 ms 16 ms 8 ms bundle-ether1.chw-edge903.sydney.telstra.net [3.50.11.177]
9 10 ms 11 ms 12 ms 74.125.49.138
10 * * * Request timed out.
11 8 ms 9 ms 9 ms google-public-dns-a.google.com [8.8.8.8]**I can't work out how to route traffic to this 172.16.100.x subnet from a server on one of the LAN interfaces of the first router. Given the tracert replyies come back to the server I'm assuming it's not a firewall issue.
I'm thinking I need to somehow create some sort of route that defines how addresses on the 192.168.x.x subnets get to the 172.16.x.x networks - I just can't figure out how to do it!!!**
Obviously from the internet, I will need to NAT ports through to the WAN interface of the second router, then implement NAT on the second router to pass traffic to servers on those downstream LAN/VLANs.