Can I route internet traffic from site B through site A via Ipsec VTI?
-
Have you checked
https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/ipsec-routed.html
and
https://www.netgate.com/resources/videos/routed-ipsec-on-pfsense-244.html ?-Rico
-
Yes sir. I've looked at both and have a successful connection between site A and B. At site B I go to the Firewall -> rules -> LAN and set the gateway for my computer and my phone to the VTI gateway. I have the NAT at Site A to allow VTI and Site B subnet out through WAN. I am able to pass internet traffic but random sites such as fast.com won't work. Pics won't display in twitter. Ping times are a little high due to the distance 7000 mile distance between me and Site A, as well as the less than stellar internet service here sometimes. The firewall log for Site A show all sorts of rejections on the Ipsec interface, despite the fact that I have a allow all from any to any rule in place on the ipsec firewall rule tab. Even if I make an exception for the event (ip address, port) that is causing the issue and add it to the ipsec rule tab, it never seems to hit as the event will continue to be blocked by the firewall. I would instead expect to see evidence of state changes, as well as data passed. I just can't figure out why the firewall is stopping so many connection attempts and believe this is the source of the anomalies I am seeing. Thoughts?
Screenshot of NAT at Site A. 10.0.5.2 is the Site B VTI ip (10.0.5.1 is Site A), 192.168.2.0/24 is the Site B subnet on which my device resides. Don't worry about the 192.168.40.0/24
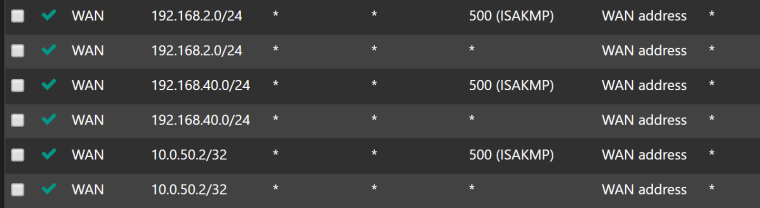
Screenshot of Ipsec firewall rule at Site A
Screenshot of firewall errors at Site A
-
@ngoehring123
Hey.
By default, all outgoing traffic is allowed.pass out on enc0 all flags S/SA keep state label "IPsec internal host to host"
pass in quick on enc0 inet all flags S/SA keep state label "USER_RULE"What I see means that the traffic is blocked at the output from the IPSEC interface. There may be a floating rule that blocks traffic. If you click on the red cross (FIREWALL LOG), what will PFSense show ?
-
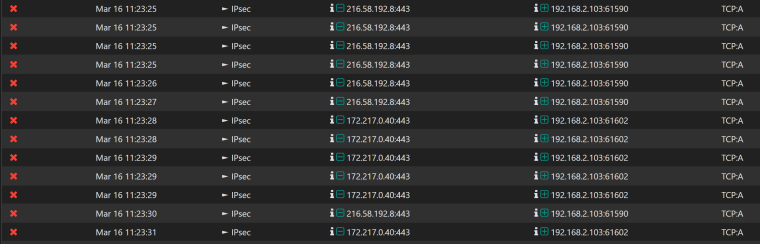
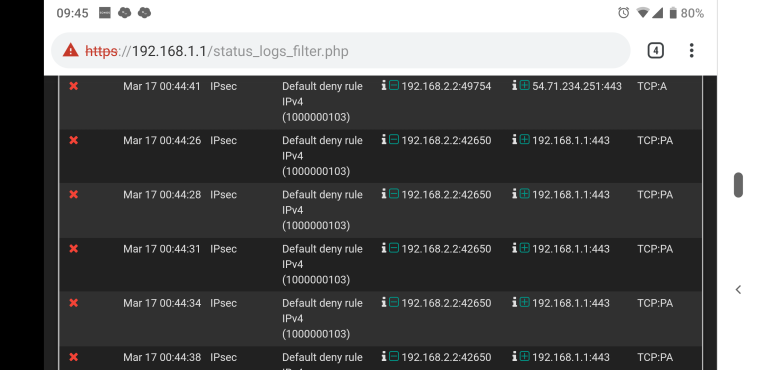
Here's the rule it says is cashing the event. Default deny though I'm confused how that is if I set an any to any rule.
-
Noticed that the screenshot I took had a lot of private to private network events. Here's one more that shows internet to device events. Same rule.
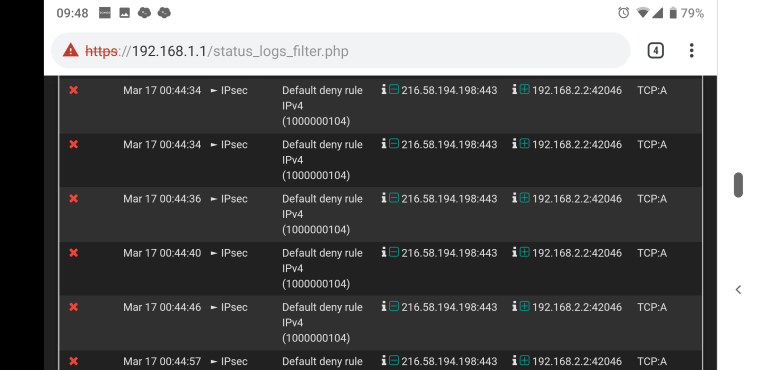
-
@ngoehring123 said
Very strange.
104 the rule blocks all outgoing traffic, but it should not work
Try to do that is a floating rule for the IPSEC or VTI interface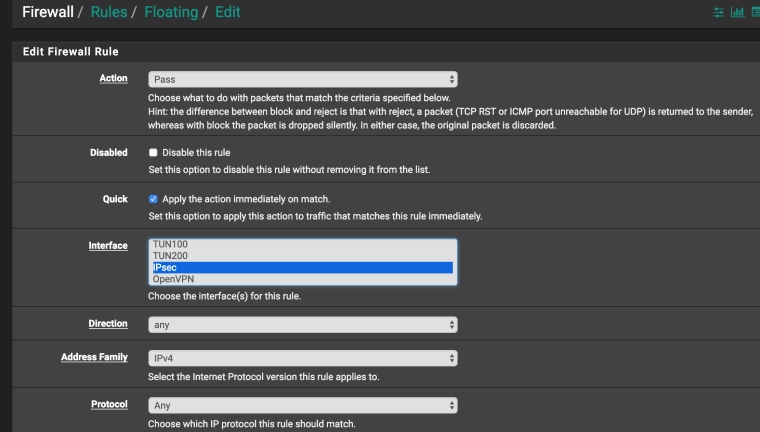
-
Done. See the below screenshots just to make sure I didn't do something wrong. No advance setting changes were made.
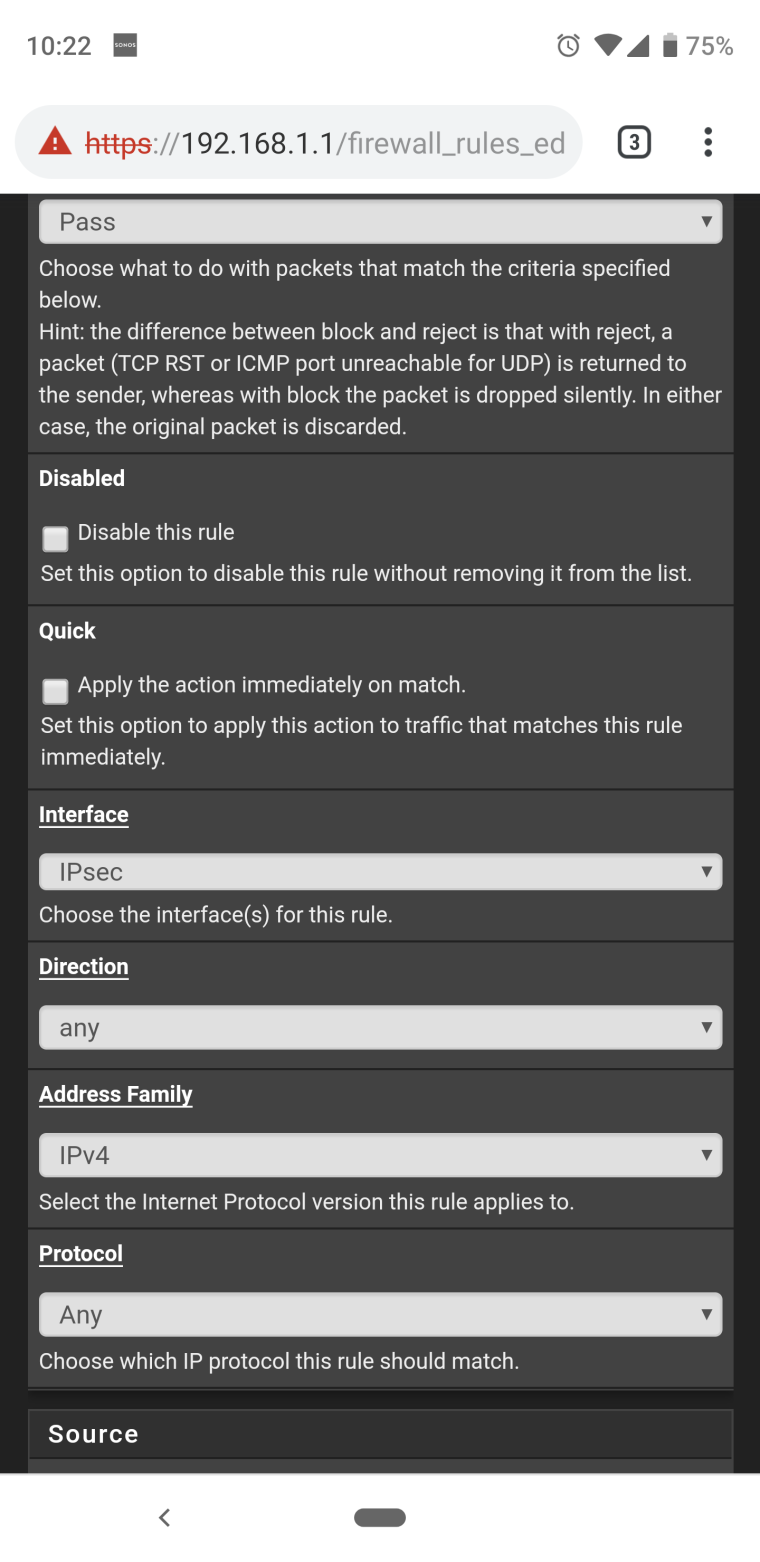
-
Still seeing the same issue flagging on the same rule.
-
@ngoehring123 said in Can I route internet traffic from site B through site A via Ipsec VTI?:
Still seeing the same issue flagging on the same rule.
And if you check QUICK ?
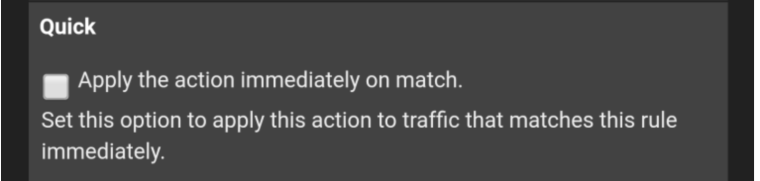
-
Same deal - logs are on fire. I really wonder if I'm trying something that isn't fully implemented in pfsense/freebsd. I've done a ton of web searches and haven't been able to find anything that matches. Part of me wonders if site A forgets or cannot remember/track the connection and so when something comes back from the internet the router at site A it says "what's this request for 192.168.2.2?" and then blocks it or parts of it.
-
@ngoehring123
The first time such see
Show me what the command shows
pfctl -sr | grep enc0
(WebGUI /Diagnostics/Command Prompt/) -
pass out on enc0 all flags S/SA keep state label "IPsec internal host to host"
pass quick on enc0 inet all flags S/SA keep state label "USER_RULE"
pass in quick on enc0 inet all flags S/SA keep state label "USER_RULE" -
@ngoehring123
And still try in floating rule put option TCP Flags - ANY Flags and State type None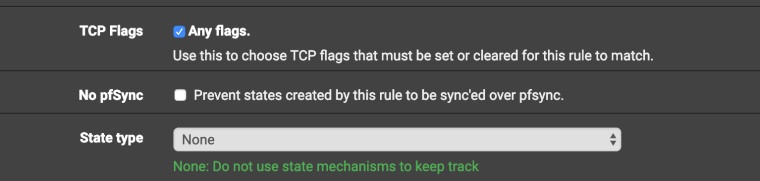
-
So firewall is still having events however now the interface has changed from ipsec to IPSEC_VTI. ???
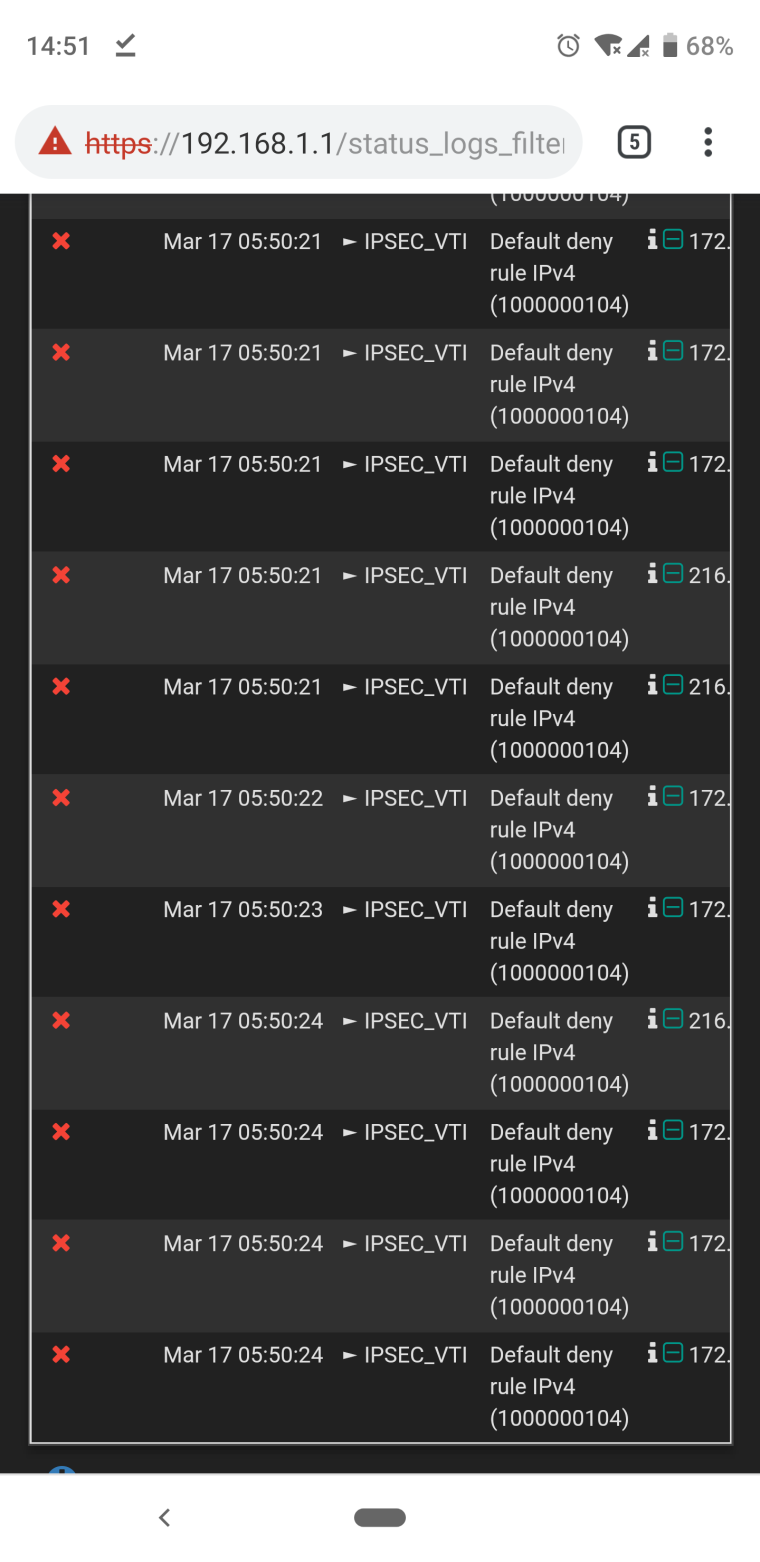
-
@ngoehring123 said in Can I route internet traffic from site B through site A via Ipsec VTI?:
IPSEC_VTI
That's the same floating rule , but for IPSEC_VTI ?
There will be two identical rules , one for IPSEC and the other for VTI -
I just have the one floating rule for ipsec. When I made those last changes you suggested the firewall errors started saying IPSEC_VTI instead of ipsec. I had to disable those last changes as they resulted in me losing access to the remote router. Thank goodness for openvpn.

-
@ngoehring123
Excuse. I didn't think there would be such a result. I have no more ideas )))
-
No worries my friend. Your time and effort is greatly appreciated. Here's to hoping this gets sorted out soon. I'll be sure to share the fix with you. Thanks again!
-
@ngoehring123
I would consider an option of the usual IPSEC tunnel, through it too it is possible to pass a traffic outside.
https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/routing-internet-traffic-through-a-site-to-site-ipsec-vpn.html
-
I had thought of doing that as well but really like the routed option more due to its flexibility and power. Perhaps @jimp has some tips for me.