pfBlockerNG overkill?
-
My network only has one port open from the WAN side. Since pf does not allow any inbound connections by default, is there really a need to have pfBlockerNG installed? The resources pfBlockerNG takes, would be an overkill IMHO. However, the question remains how to limit external connections to that one open port in terms of geolocation etc.
Thoughts?
-
What is the port forward for?
-
@johnpoz vpn
-
Ah your own inbound vpn.. Yeah I have that open - and just open to the public... vpn connection is pretty secure.. Traffic that doesn't pass the doesn't even get to the next level if you have auth and encryption set for you tls mode.
I would assume your not just using password ;)
-
@johnpoz indeed ;-)
Back to the original question though. 1) Is pfBlockerNG needed for a setup similar to mine? 2) How to limit inbound connectivity of that one port (ie: geolocation limitation/restriction)?
-
If you want to do geoblocking then yes you would have to use pfblocker.. OR create your own alias lists... But WHY?? There is little worry about so china or russian bot doing anything to your vpn server other then blip of noise in your log.
-
I agree with @johnpoz here. No need for geo-blocking if the only port you have open is VPN and you are using certificate-based authorization.
If you really, really want geo-blocking, besides pfBlockerNG, you can use the GeoIP rule option in Suricata. It uses the MaxMind free database by default. You would have to craft your own custom geo-blocking rules, but they are very easy to write. Just use the ISO-Country Code for the countries you want to block. Here is a quick example:
alert ip any any -> any any (msg:"GeoIP from JP,Japan "; geoip:JP; sid:55555555; rev:1;)For China, simply change the Country Code to "CN" like so:
alert ip any any -> any any (msg:"GeoIP from CN,China "; geoip:CN; sid:55555556; rev:1;)You can have as many rules are you want, just remember to increment the SID so each rule's SID value is unique. You can't have two rules with the same SID in Suricata (or Snort).
-
Or just grab a list and put it into an alias on pfsense, and put that above your allow rule on your wan.
For example... If I wanted to block say all of russia
Go here
https://www.ip2location.com/free/visitor-blocker
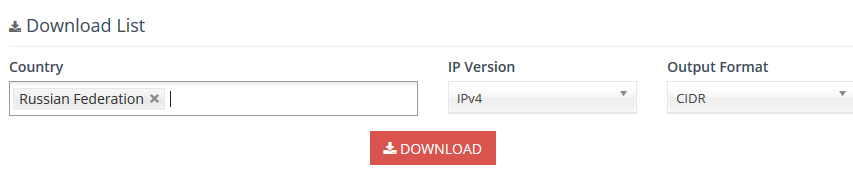
Download the countries you want to block.. Then use the bulk import.
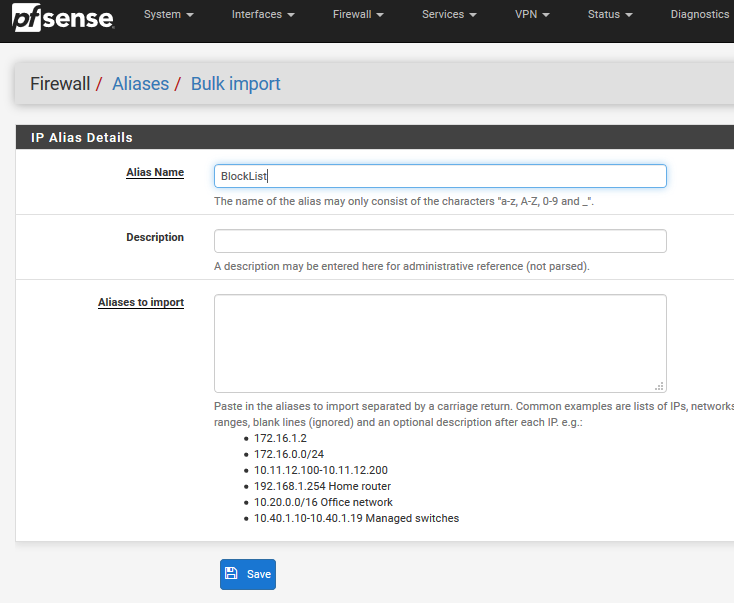
Or just grab the country or countries you want and create an alias with bulk and use it as your allow list on your firewall rule..
There are multiple places to go to get such lists - I just happened to find this place first on a google... No reason to run any packages be it pfblocker or such IPS, etc.
The better option here if your that worried is to know where your going to be coming from... Say your cell phones networks - you could pull that from AS number.. Or say your place of work, or your fav remote pub or somethings wifi, etc.
But again - if your vpn is properly setup, its not an issue.
Here is snippet of the RU netblocks from site above
# ------------------------------------------------------- # Free IP2Location Firewall List by Country # Source: https://www.ip2location.com/free/visitor-blocker # Last Generated: 25 Mar 2019 01:00:35 GMT # [Important] Please update this list every month # ------------------------------------------------------- 212.45.224.0/19 212.46.0.0/19 212.46.192.0/18 212.47.201.55/32 212.47.201.200/32 212.48.32.0/19 212.48.128.0/19 212.48.192.0/19 212.48.224.0/20Just grab those in your fav text reader and paste them in your alias your creating.
Here is another location to grab CIDR listings
http://www.ipdeny.com/ipblocks/ -
@johnpoz @bmeeks -- Epic!! Thanks for your responses!! Much appreciated!
Though, I must say that @bmeeks has opened up a can ;-) when he mentioned Suricata as the IPS/IDS subsystem. I've used Snort in the past, but had too many issues with it in terms of getting it configured properly so it is in "usable" state. In other words, too many things were getting blocked and it felt like it would take a lifetime to get things properly configured in Snort. That said, I wonder how does Suricata compare to Snort?
Thanks fellas!!
-r
-
This general advice applies to suricata too:
https://forum.netgate.com/post/831808
In other words, don't turn on blocking until you've tuned your rule set.
-
@rsaanon said in pfBlockerNG overkill?:
Back to the original question though. 1) Is pfBlockerNG needed for a setup similar to mine? 2) How to limit inbound connectivity of that one port (ie: geolocation limitation/restriction)?
Just wanted to chime in a few cents ;)
I agree that with only a single port inbound either IDS or pfBlockerNG may be overkill. BUT pfBlockerNG brings additional benefit to rule configuration IMHO. Of course you can add the country IP list like @johnpoz explained. Or you could use pfBlockerNG-devel (way newer and handier in many regards) and let it handle the auto-update of geoIP lists, add needed lists like russian IP block to an Alias and use said alias in your rules. With the pfBlockerNG widget on your dashboard you have an eye on those lists if they fail to update.
In addition to that you can also create tables/aliases for blocking external IPs from your LAN. Why? Because pfBlockerNG(-devel) has a lot of preconfigured lists (or you can add your favorites yourself) that have known virus, trojans, cryptolocker, botnets etc. -malware as an IP table, that you can use and block outgoing for your LAN.In a few cases that saved a customer of ours his 'behind' as someone on his network brought an infected laptop and hooked it on the WiFi. As we configured pfBlockerNG with those lists a few weeks earlier, the infected laptop hit the brick wall of PF and pfBlocker as it tried to contact the malware control host but the IP was blocked and as the WiFi was compartmentalized, no other device was infected or added to the bot net (it was also running a nasty backdoor that phoned home to allow remote login).
So depending on what you wanna achieve, pfBlockerNG(-devel) - and IDS too - can add an additional layer of protection besides brain, AV and a patched OS ;)
-
There are many ways to do this... pfBlockerNG also has deduplication such that if you are using GeoIP and other IP Feeds, it will deduplicate the IPs that are already being blocked via GeoIP since they are in CIDR format. So if you are already blocking say RU, then no need for any other IP feed to include other RU IPs. So it ends up being more efficient. Not to mention the ease of use, and devel has Alert reporting and Statistic pages.
Thanks a @JeGr ... Good to hear some other success stories....
-
I’m in awe for the level & substance of the responses this thread has generated. Special thanks to @BBcan177 @bmeeks @Derelict @JeGr @johnpoz.
For one or another I’m not able to contribute (i.e. helping others) to the forum as I would like to; however, I can certainly contribute monetarily. That said, I would like two “buckets” that I would like to contribute towards: 1) Folks like @johnpoz, @bmeeks @Derelict @JeGr who give their valuable time towards genuinely helping others 2) Folks like @BBcan177 who develop such great projects like pfBlockerNG. May be these bucket categories already exist. Regardless, how can I contribute to these categories?
Thanks so much each and everyone!
-
@rsaanon said in pfBlockerNG overkill?:
May be these bucket categories already exist. Regardless, how can I contribute to these categories?
https://forum.netgate.com/topic/122665/support-pfblockerng-development
-
https://www.freebsdfoundation.org/donate/
-
I agree with @Grimson and and @Derelict. It's nice to read positive feedback though :)