Yet another ping problem with Virtual IPs
-
That is not 1:1 NAT. That is 2:1 NAT.
-
Yes. The port forwards should override that if there is some problem there but only inbound. There might still be conflicting outbound NAT causing an issue.
Try disabling the 1:1 NAT rules and using port forwards only there.
Steve
-
Or put another address on the target server and 1:1 NAT the VIPs to their own addresses.
-
Yes, you're right :/ ... I'll try either using port forwards or setting up another internal IP for the second 1:1 NAT (will report the result tomorrow as I have to do it overnight)
-
Actually ... isn't 1:1 NAT simply a more convenient way of port forwarding everything to the specified destination?
(BTW outbound NAT is set to "Automatic outbound NAT rule generation")Anyway, I've disabled 1:1 NATs and created separate HTTP/HTTPS/ICMP rules for each Virtual IP (without associated rules as these already exist). Unfortunately, I experience the very same behaviour, i.e. it still works just fine from my office network but alternating pings fail as per the description above from my home network.
-
I've just added a temporary local IP address on the reverse proxy VM (ip a add ...) and I've changed one of the ICMP port forwards to go to the new local IP address. I've also run iptraf on the VM to be sure that it's the VM which handles the ICMP replies, not pfSense.
With this configuration, as expected, everything works normally (even alternate pings from my home network).
Am I missing something from a conceptual point of view?
I should be able to port forward to the same internal IP, moreover it already works with HTTP/HTTPS traffic ... -
I suspect this is a state issue. pf is trying to open a state on the LAN interface with a source and destination IP that are identical to those of an existing state. With a TCP connection it also using the source and destination port and since the source port is random that will be different to any existing state.
1:1 NAT rules forward all ports the same as a 1-65535 port forward would but it also NAT's traffic outbound from the internal target to the external IP. Obviously that can't happen to two IPs so one rule will fail there. I believe the first 1:1 rule will win.
If you are doing this just to provide a ping target for external users it's probably easier to have pfSense respond to the pings on the VIPs directly and forward only TCP traffic to the proxy.
Steve
-
I don't believe this would be the cause ... ICMP packets should be routable just like TCP and UDP which work ok (well, technically I think ICMP is just an application protocol on top of IP which is routable). Also, if this was the case I would expect it to work intermittently but it works flawlessly from my office network.
As far as I understand, 1:1 NAT is all about incoming traffic and the part of the outgoing traffic that should go out from WAN originating from the associated VIP. Could it be that I need to change the "Automatic outbound NAT rule generation" to, say, "Hybrid Outbound NAT rule generation" and create a manual rule for ICMP? Anyway, I still don't get how it works from one place and not another ... does it work ok when you ping these IPs from your network?
As for the pfSense answering the pings, that simply defeats the purpose of having the ping as it will only let users know whether pfSense itself is working not the services behind it.
-
Having looked into this further I'm certain it's a state issue.
If you look at the failed packet capture the incoming ping requests are all using ICMP identifier number '1'. pf uses that in the state it opens in the same way it does ports for TCP/UDP. It can't open a state on LAN with the same source, destination and identifier as one that exists so nothing passes until the previous state times out.
If you test remotely from behind a difference pfSense it will randomise the ICMP identifier when it outbound NATs the traffic. That means when it arrives at the port forward the two pings have different identifiers and two states can be created. No problem.
It appears that when you are testing and seeing failures the client you are testing from is using the same identifier for all pings. And the router you are testing behind is not randomising the identifier on the way out.
Nothing we can do about that in the pfSense forwarding those pings.
Interesting. Never hit that before.
Steve
-
Hmm, you could maybe have it outbound NAT the traffic to a different internal IP for ICMP only. That would randomise the identifier and allow it.

Ugly but...might work. -
@stephenw10
Aaah, that makes sense now! Spot on!!! :)Could it be because of a double NAT? ... When I think about it, I have a GPON that handles fibre optic and an IPTV box plus my router are connected to that GPON. My router does have an internal IP on the WAN interface. I don't have access to that GPON ... at least legally (I know the account though), as it's controlled by my TV & Net provider. Probably the guys whom I asked to test do have similar setup.
Anyway, I'm extremely grateful that you, guys, put a lot of effort into dealing with my problem!
Thanks and have a great week!
-
No problem. Interesting case.
I'd be interested to see if that outbound NAT workaround allows the pings. That would confirm itYou would see the identifier numbers changed in the state table.
Steve
-
I didn't quite get the workaround idea (BTW using "Automatic outbound NAT rule generation" at the moment). What rule do I have to create and will it take precedence, i.e. do I need to switch the Outbound NAT Mode?
As for the pings, I've just confirmed it's definitely the ICMP identifier as I downloaded something called hrping (googled it) which allows setting the ICMP Id. Whenever I set one and the same ICMP Id I have the problem and once they're different (hrping does this by default) there's no problem ... bloody routers! ... though one could blame Windows as well! Here's an excerpt from Wikipedia I've just read: "The Identifier and Sequence Number can be used by the client to match the reply with the request that caused the reply. In practice, most Linux systems use a unique identifier for every ping process, and sequence number is an increasing number within that process. Windows uses a fixed identifier, which varies between Windows versions, and a sequence number that is only reset at boot time."
-
Yes, blame all around there.

So pf can't create the state because everything is the same. If we add an outbound NAT rule on the LAN that then chnages the states to include the NAT but more importantly pf randomises the identifier making it unique.
So first switch outbound NAT to hybrid mode so you can add manual rules. The add a rule like:
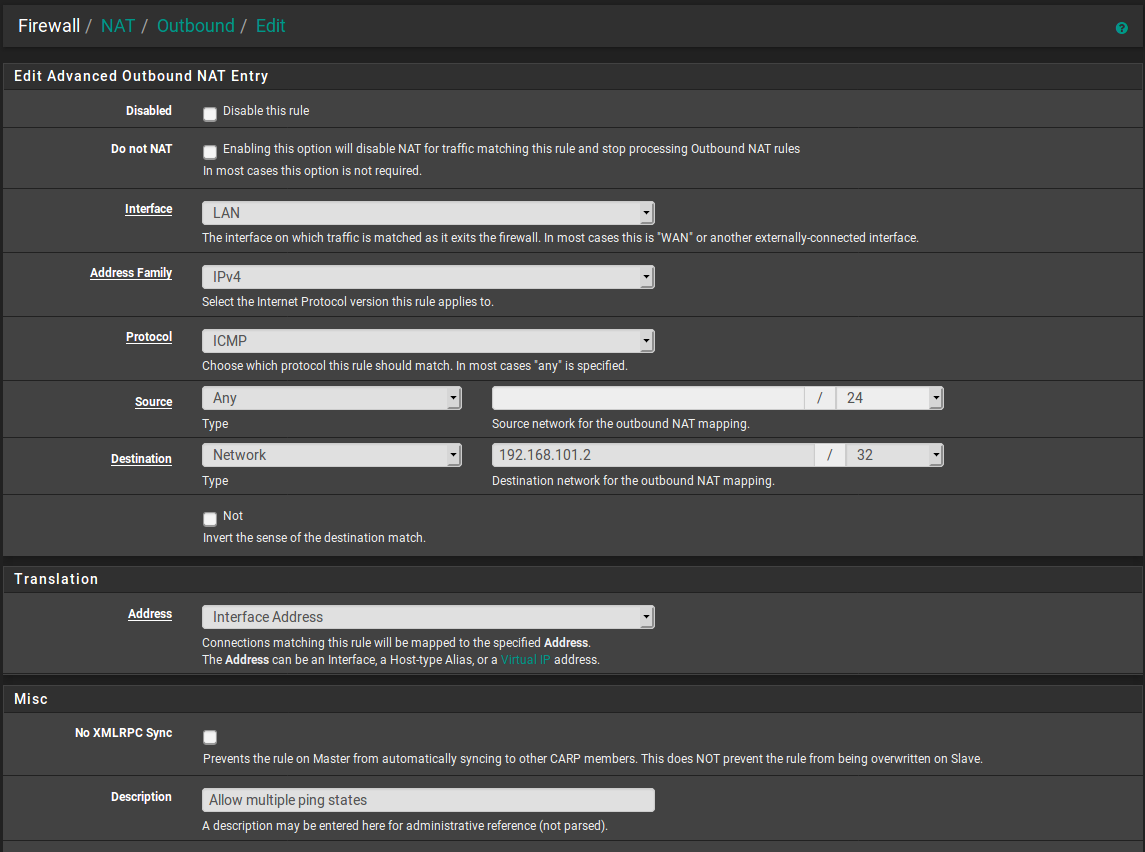
It would be better to specify the source or use !this_firewall but that's not available. As it is if you try to ping the proxy VM from the firewall itself it will NAT that too. But that may not be an issue, certainly not as a test.
Steve
-
@stephenw10
Just tested this and it's the same. I've changed the NAT mode and added this rule:
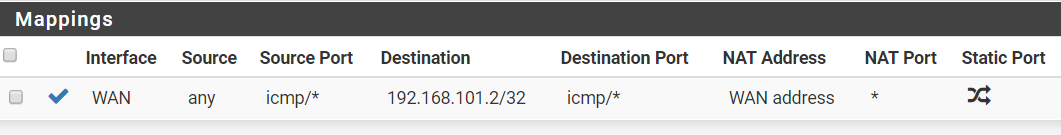
-
@rebi said in Yet another ping problem with Virtual IPs:
@stephenw10
Just tested this and it's the same. I've changed the NAT mode and added this rule:

@stephenw10 said in Yet another ping problem with Virtual IPs:
If we add an outbound NAT rule on the LAN that then chnages the states to include the NAT but more importantly pf randomises the identifier making it unique.
He said on LAN and you created it on WAN.
-
@Grimson
 my bad ... here it is but still doesn't work:
my bad ... here it is but still doesn't work:
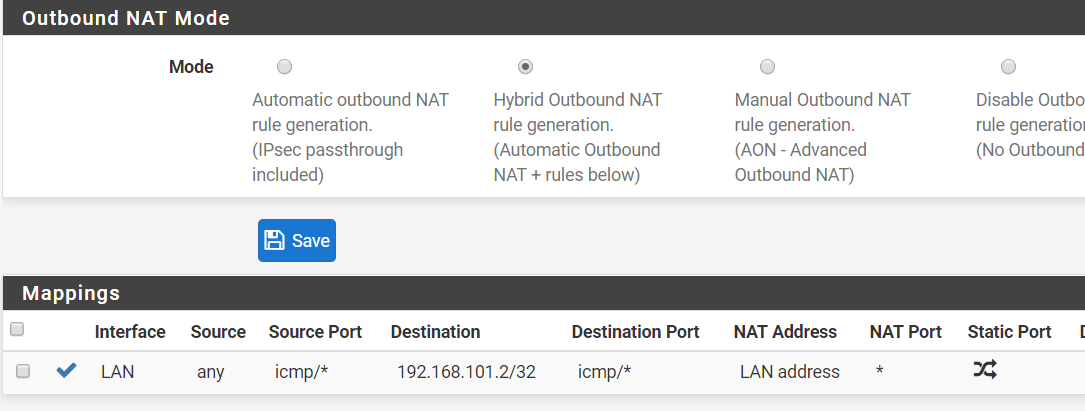
-
What happens when you try to ping? Any change at all?
Check the states in Diag > States, filter by icmp.
Steve
-
Nope, exactly the same as before. Until the old state is cleared, the next ping doesn't go through. hrping works flawlessly but it changes ID on every ping request.
Anyway, now that I know what the problem is, I'll simply adapt to the reality and will use another internal IP address for the second ICMP port forward.
I'm happy to test any ideas though ... out of curiosity what would make it work :)
-
I'd be interested to see the states on the LAN side. I expect it to show the NAT and the identifier chaging.
But, yeah, it may simply not be possible in which case just move forward with what works.
Steve