Why can't i access my pfsense box over OpenVpn
-
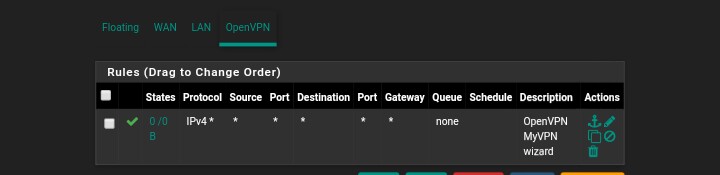
This is the OpenVpn rule that was setup by the Wizard -
Describe how you are trying to connect. What OS? What VPN software, if not using OpenVPN native client? What does your local client log say? What does pfSense Status - System Logs - OpenVPN say? It looks like no traffic has made it to your VPN interface.
-
@KOM i am using Windows 10,and when i try to connect it show TLS key negotiation failed to occur within 60 seconds(check your network connectivity)
019 TLS Error:TLS handshake failed -
I asked you several questions and you answered two of them. You're not really making it easy to help you.
-
Yeah, that error just means the client never sees any response from the server.
Since the firewall rule has no traffic on it either some rule above that is blocking it or the client traffic never reaches the server.
So how it the client setup to reach the server? By IP directly? Using FQDN? Is that resolving to ten correct IP?
Steve
-
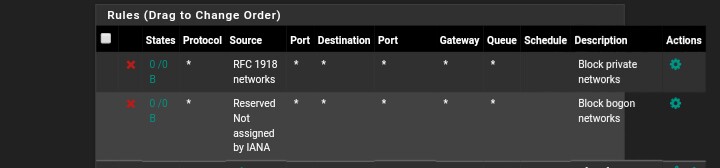
@stephenw10 Does the default Wan rule(Block private networks) and (Block bogon networks) also affect the accessibility to the pfsense box because they are the first by order.
-
-
Those have no effect unless you're testing from a local IP that is in a private network or something in the bogons list which is unlikely.
Steve
-
@stephenw10 then what is the problem?kindly help posting firewall logs in a minute
-
We've asked you how the client is resolving the server a number of times here but it seems to be a secret!

That's the first thing I would check. Is the client trying to connect to the correct IP?
If it is then why are the packets not reaching the server? Is there something between them blocking it?
Steve
-
@stephenw10
And No! The client is connecting to the correct Ip via the dynamic Dns.... -
@stephenw10 21:20 Unrecognized option or missing or extra parameter(s) in /data/user/0/de.blinkt.openvpn/cache/android.conf:38: block-outside-dns (2.5_master)
21:20 OpenVPN 2.5-icsopenvpn [git:icsopenvpn/v0.7.8-0-g168367a5] arm64-v8a [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [MH/PKTINFO] [AEAD] built on Feb 22 2019
21:20 library versions: OpenSSL 1.1.1a 20 Nov 2018, LZO 2.10
21:20 TCP/UDP: Preserving recently used remote address: [AF_INET]xxx.xxx.xxx.xxx:1194
21:20 UDP link local (bound): [AF_INET][undef]:1194
21:20 UDP link remote: [AF_INET]xxx.xxx.xxx.xxx:1194
21:20 read UDP [ECONNREFUSED]: Connection refused (code=111)
That is how it shows on my vpn client log on Android.Note:xxx is the Ip address -
@OpenWifi this right now
-
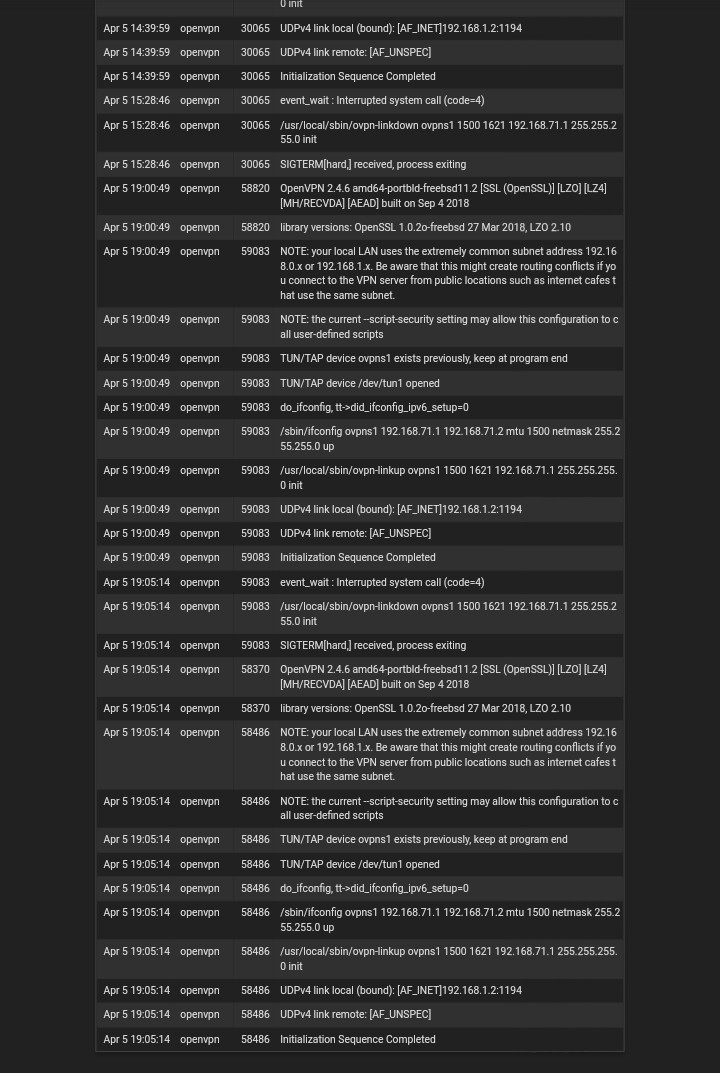
Ok, so nothing logged on the server end and that's expected since the firewall rule shows no passed traffic.
Looks like an Android issue I would guess. Can you test from a desktop client to confirm that?
Steve
-
@stephenw10

That is on the desktop -
Ok so failing the same way from the desktop client. I assume you still see no traffic on the WAN OpenVPN rule and nothing in the server logs to show 'peer initiating'?
So something is blocking that traffic before it gets to the pfSense WAN. Or it's being sent to the wrong IP/port by the client.
You could run a packet capture on WAN and filter by UDP port 1194 to be sure.
How is the WAN connected? What sort of connection is it?
Steve
-
Oh, wait the OpenVPN server appears to be listening on 192.168.1.2. Is that behind another router? Have you setup port forwards in that router?
Steve
-
Double NAT is my guess as well..
-
@stephenw10 yes it is behind the main router that my isp provided
-
@stephenw10 No! I havent setup any port forwards should i set it on the main router or the pfsense box