Azure LAN interface without gateway
-
Hello all,
I am trying to configure my LAN interface in an Azure instance and I am struggling with my LAN interface. My pfsense has 2 WAN interfaces and one LAN. The LAN interfaces have a static internal and public IP address and the LAN has only a static internal IP> All the interfaces belong to different subnets.
If you see the screenshot below, my WAN interfaces have a gateway the expected Azure default gateway which is the x.x.x.1
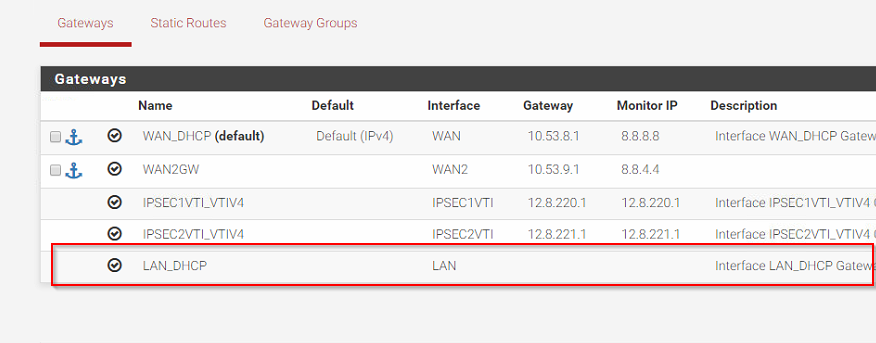
Though, my LAN interface does not get anything!!! The IP address of the LAN interface (if I set it as DHCP), is getting the IP address of the NIC that I configured in Azure. Though, if I set it as static, thenI cannot even ping it!
What I want to do is to use this VM as my router to connect my local network with Azure. So far I have created two router IPSec tunnels and I have configured FRR BGP. I also created a static route in Azure so all the traffic that is related to my local network can travel via the LAN interface of my Azure pfsense.
The traffic from my Azure servers towards my local network (after I created the static route) work fine and I have ping replies. Though, the traffic from my local network towards Azure stops in the LAN interface of the Azure pfsense. I can ping the LAN interface, but I cannot ping any other VM in azure.
Any idea what am I doing wrong?
Thanks in advance.
-
It is probably NATing out if the LAN since it is DHCP. I would switch to manual outbound NAT and remove any rules created for LAN.
You can also probably disable the LAN DHCP gateway.
Doing those things mighyt break the traffic from pfSense to the Azure VMs if they have a missign route. That would explain why you see traffic one way only currently. Adding the route should allow traffic both ways though.
Steve
-
@stephenw10 Thanks Stephen.
The thing is that I do not need a LAN Gateway for my LAN interface, except the default gateway of the pfsense (the WAN default gateway). Even if I disable the LAN GW, the problem persists. The connection between the LAN interface and the instances that belong in the same subnet should work. The traffic for the onpremise subnet is routed with BGP via the IPSec tunnels.
Also, from my Azure pfsense I can ping a Linux server which belongs in the LAN subnet but at the same time I cannot ping a Windows server, again in the same subnet.
Not sure if I have to configure anything else in Azure. The truth is that only my pfsense knows about the existence of my on premise network. Azure doesn't know anything about it except a static route that I specified which send all the traffic via the pfsense.
-
Hmm, the usual reason for Windows refusing pings like that is the Windows firewall blocking requests from outside it's own subnet. However if you're pinging from the LAN interface that should not apply.
You will need to have IP forwarding enabled on the pfSense LAN interface to reach the on-premise subnet from Azure:
https://docs.microsoft.com/en-us/azure/virtual-network/virtual-network-network-interface#enable-or-disable-ip-forwardingSteve
-
@stephenw10 Holly crap! It was the windows firewall in the Azure server!!! And sorry, I thought I was able to ping it from the Azure pfsense but no, finally I wasn't able to do this.
Thank you so much and sorry for bothering you.
-
Ha, no problem.
