XG7100-1U Multiple WAN to Multiple LAN
-
Please open a ticket with us at https://go.netgate.com if you are still having problems with that.
If you have an existing configuration we can help you convert that. We also have an alternative default config we can provide with all the port pre-configured as separate interfaces.
Steve
-
@Rico We've watched the video a number of times and while it seems informative, its not instructional on various configuration options.
-
@stephenw10 Thank you I believe this will need to be our course of action.
-
If you have something like a white paper or FAQ on how to do this type of configuration, I'd be interested in it as well. The switch port is presenting some challenges here as well, almost looks like we should have ordered the the PCIe network card at this point.
-
If you're configuring from scratch I'd first restore this config that will configure the switch and VLANs in pfSense to have all the ports separately assigned. Then you can treat them like individual interfaces.
If you have existing VLANs things get more complex but as I said above if you open a ticket with us we can help you with that. We've done lots of these conversions with numerous different configurations.
Steve
-
Hi @stephenw10 thank you again for helping with this the other day. I am sorry to bother but I have a question based on your prior assistance.
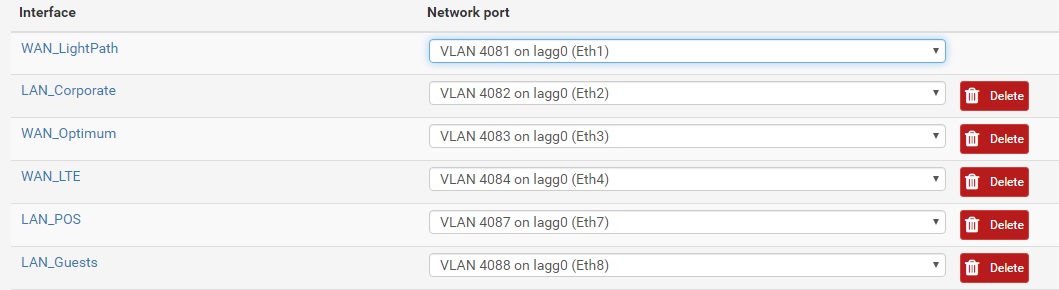
Eth1 4081 - WAN1
Eth2 4082 - LAN1
Eth3 4083 - WAN2
Eth6 4086 - LAN2
Eth7 4087 - WAN3
Eth8 4088 - LAN3Now I want to have each LAN # route outbound using the corresponding WAN # (eg; LAN1 to WAN1, LAN2 to WAN2, LAN3 to WAN3). I was able to get the config to the point where it's usable for our needs with regards to IPSEC tunnels and all, but as each WAN is a different ISP and each LAN is a different VLAN tag on the switches (the LAN ports are ACCESS to the switches ports where the switches then carry the traffic internally over the tagged VLAN's).
Is the best way to route the LAN's to the appropriate WAN's to use rules (eg; Rule - LAN1 / Rule - LAN2 , etc) or is there a better way to do this?
Thanks again.
-
Yes, use policy routing rules on the incoming LAN interfaces to route traffic via the correct gateway.
You may want to add rules above that on each interface to allow traffic to the pfSense DNS and NTP services on the LAN interface itself if they are using that.
Steve
-
Here is what I have so far, not sure if this was done correctly. Showing in order of work performed:
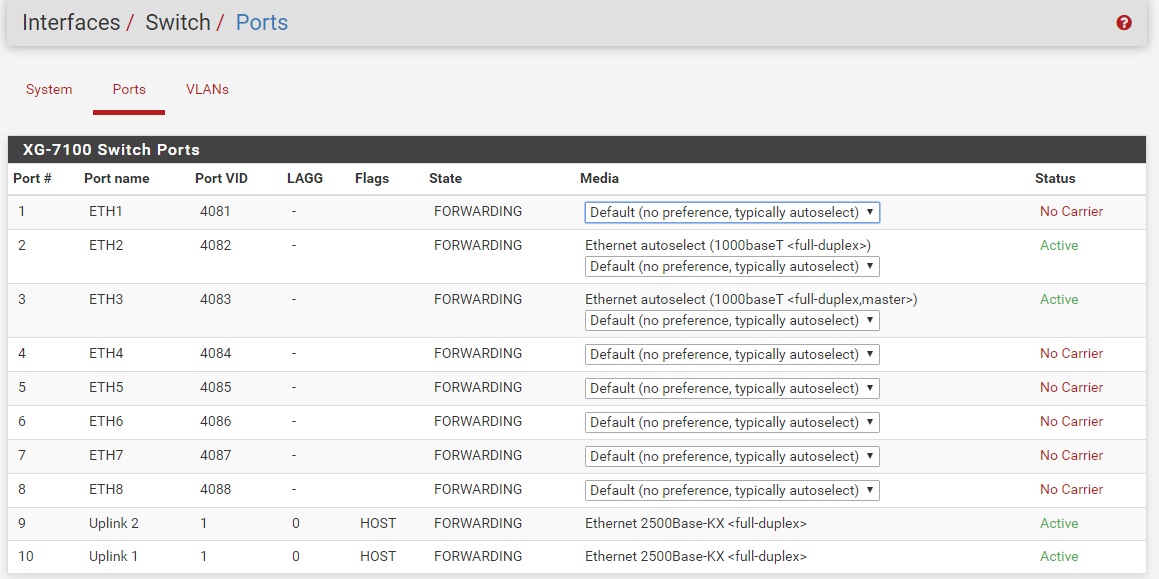
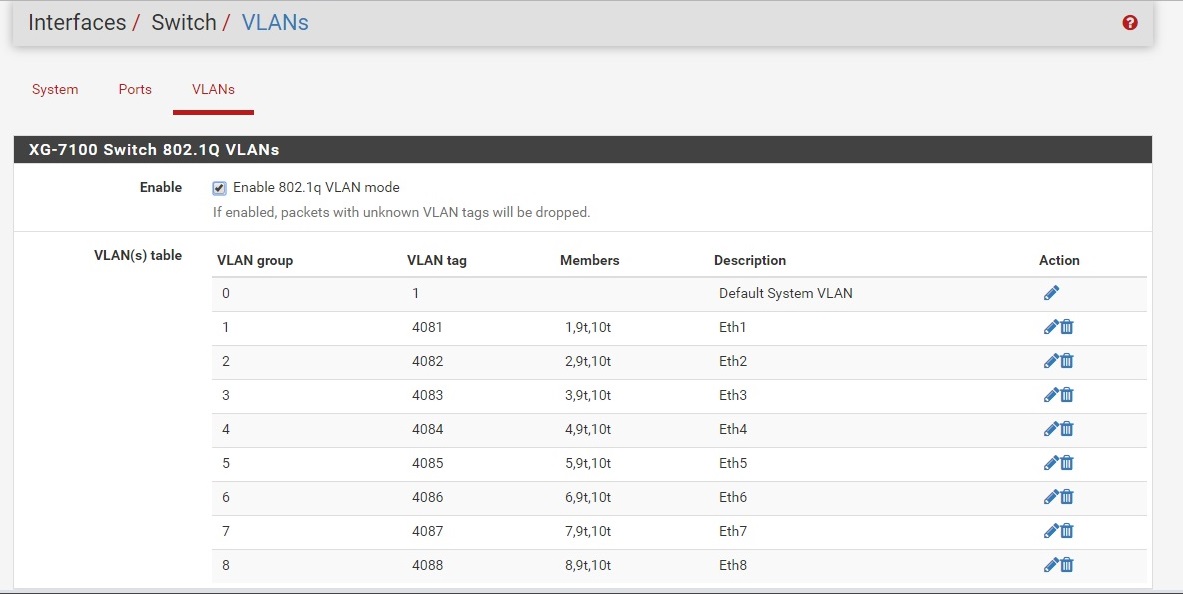
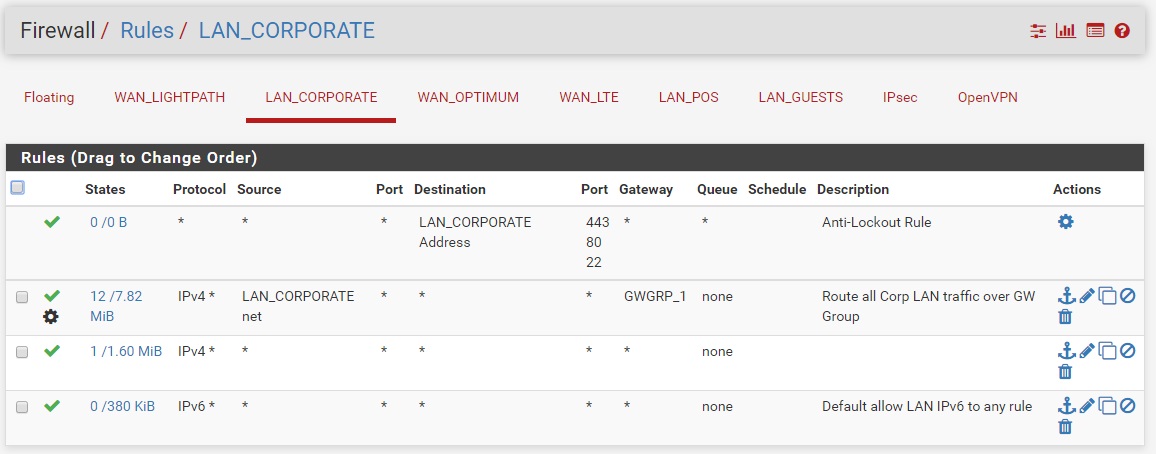
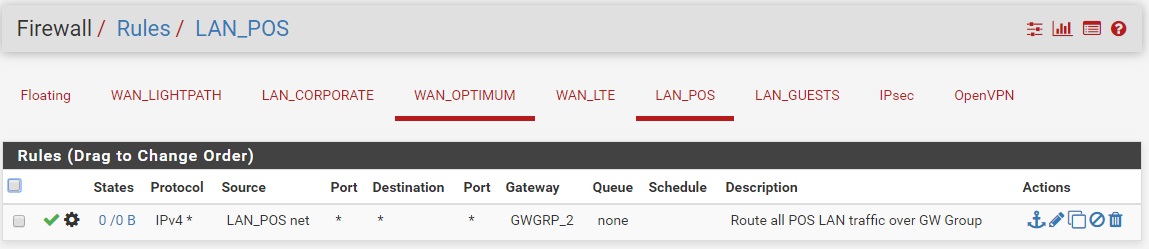
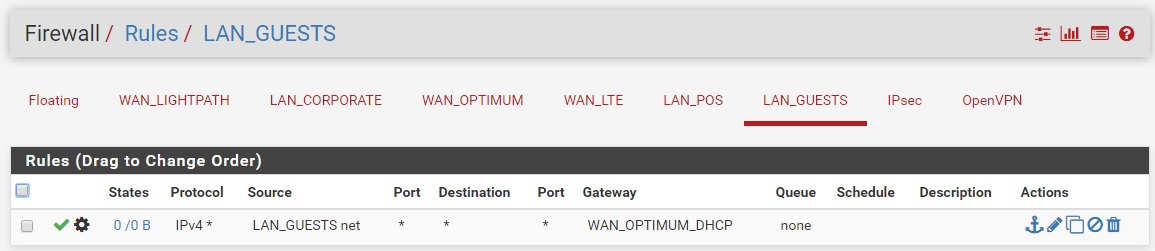
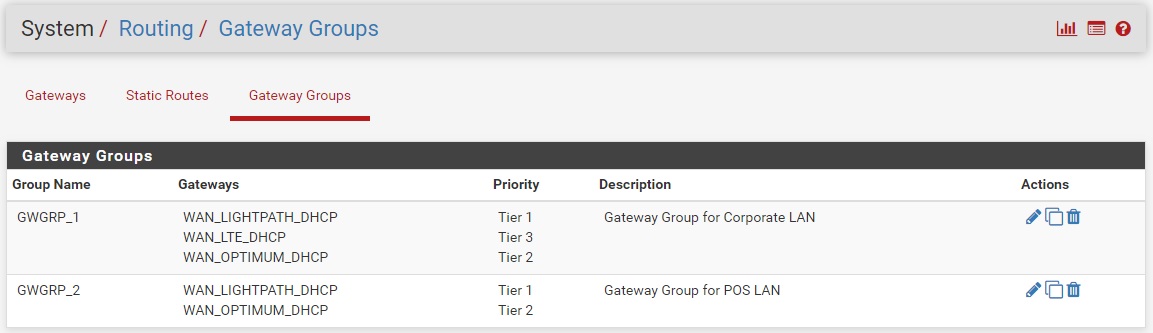
Thanks again.
-
And to be clear, we do not yet know if it is working, we wish to go live next week and are hoping to get the configuration correct from the start.
-
Yeah that looks OK but you will probably want rules above those policy routing rules to allow clients there to access DNS and NTP on the firewall. Otherwise all traffic matched by the policy rule will be forced to leave via the gateway group including dns and ntp. You might also want a rule to prevent devices access the GUI on the WAN IP.
Something like: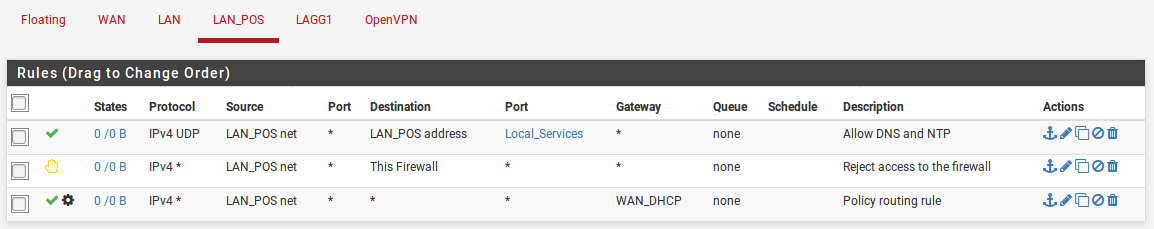
Steve
-
@stephenw10 you really are awesome! that is exactly what i did yesterday. Thank you so much!