no internet on 3 vlans 3rd ok
-
Thanks for your reply.
Still cant get out to internet from either LAN, VLAN30 or VLAN40
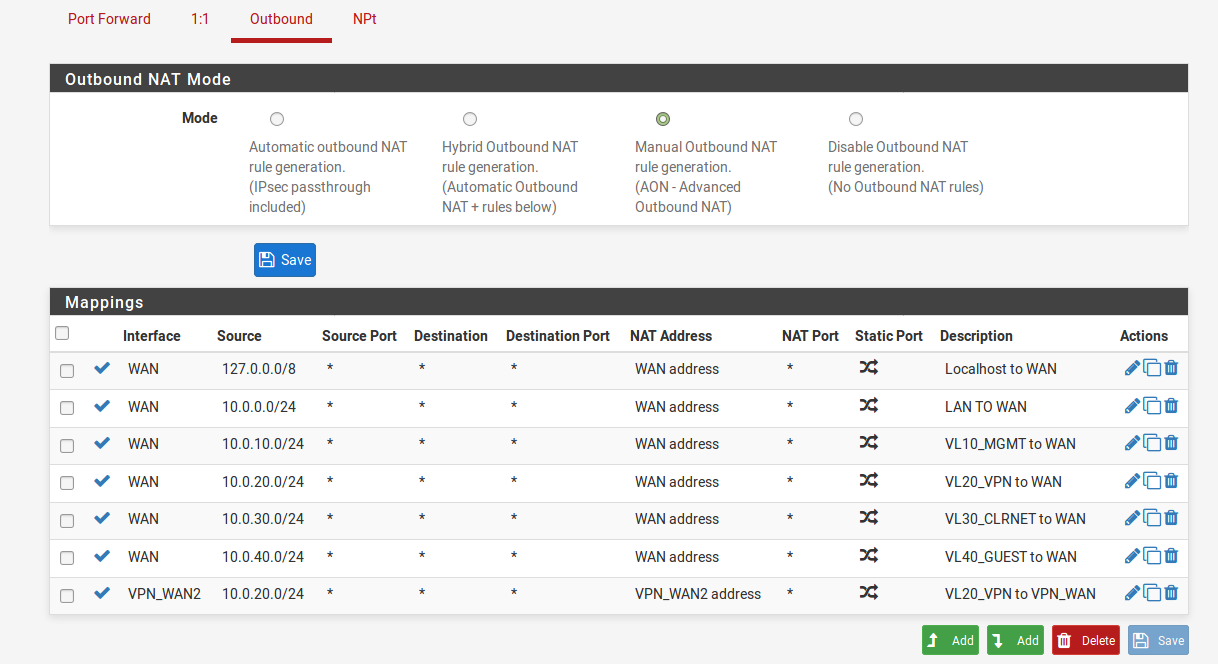
the NAT is set....
And a firewall log after attempting to connect to leaktest.com is
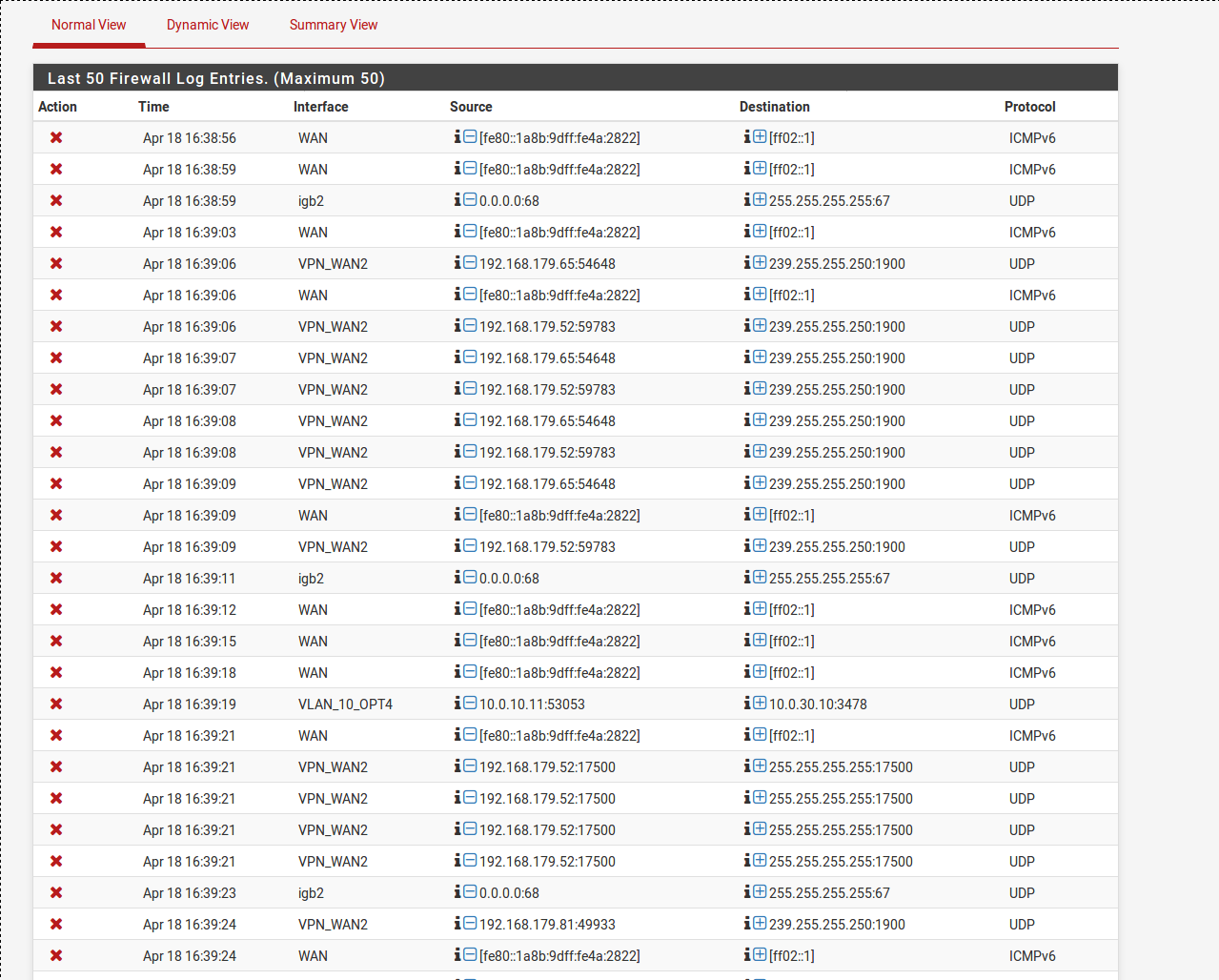
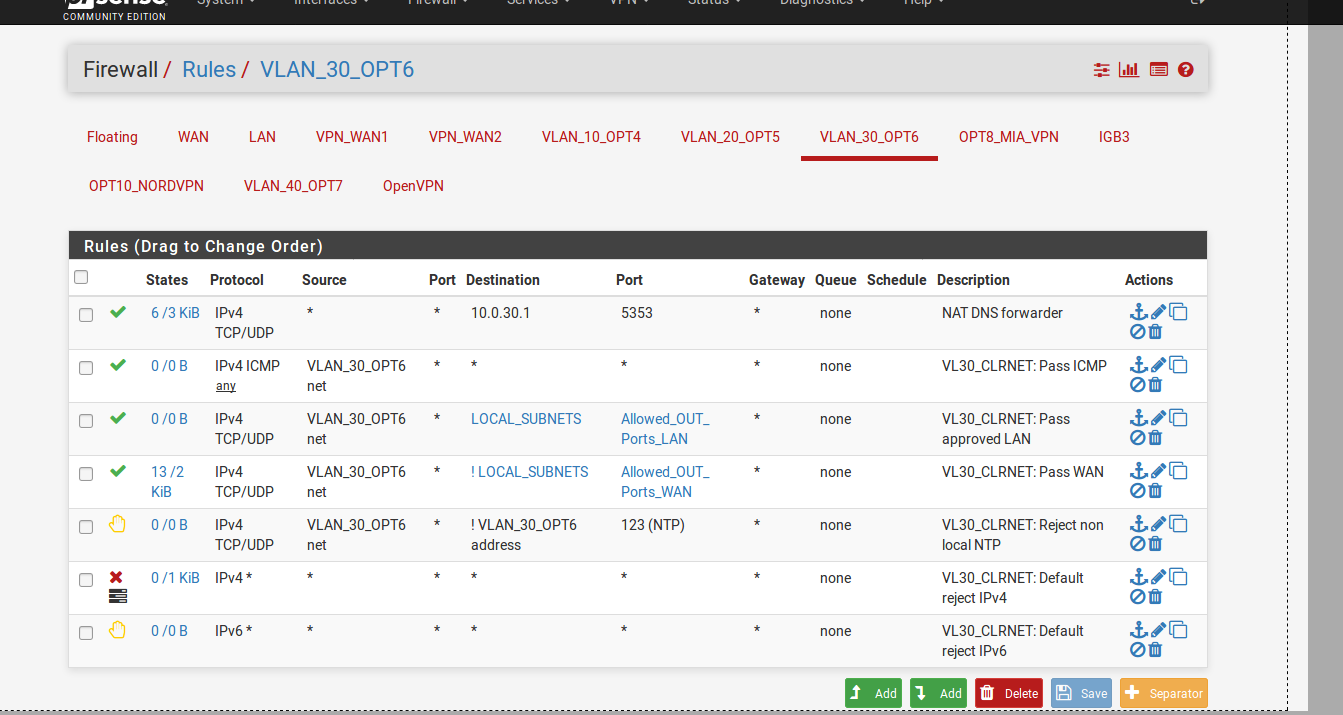
Cant ping to the outside on either LAN VLAN30 or VLAN40
seems odd as the subnets and NAT seem to be set okAll I require is
- a OPENVPN connection which has internet connection stopped if the vpn disconnects
- A clear route to the ISP
- and a Guest network of limited access
- a management net for maintenance etc
all of those on VLANS to a unifi AP and a hardwired port/s for each of those -this setup seemed to be what I was looking for and being a novice at networking stuff seemed ok
Any assistance would really helpful.
-
Do you have dhcp enabled on those VLANs and are clients connected to them pulling an IP from pfSense?
Steve
-
Yes, dhcp server is set for lan and vlan subnets as in the NAT outbound and when connected to them receives the appropriate ip address - can access webconig but not the outside neither ping (4.4.4.4) or http pages etc
-
pinging 9.9.9.9 gave this..... connected to 10.0.30.10
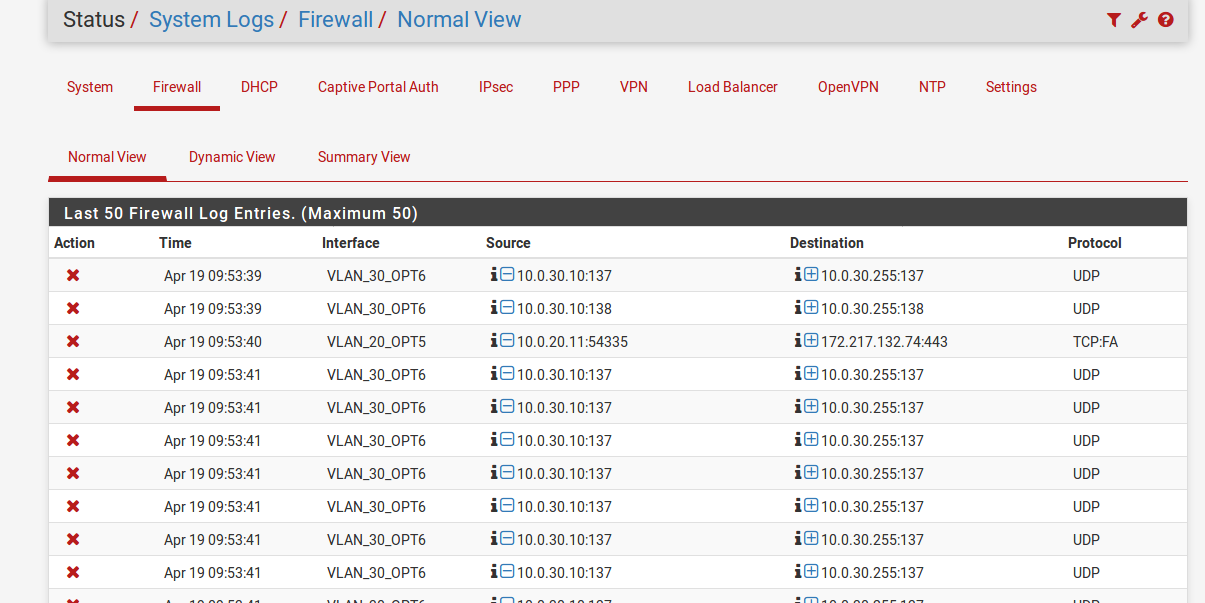
-
None of those blocks are ICMP so not blocking ping.
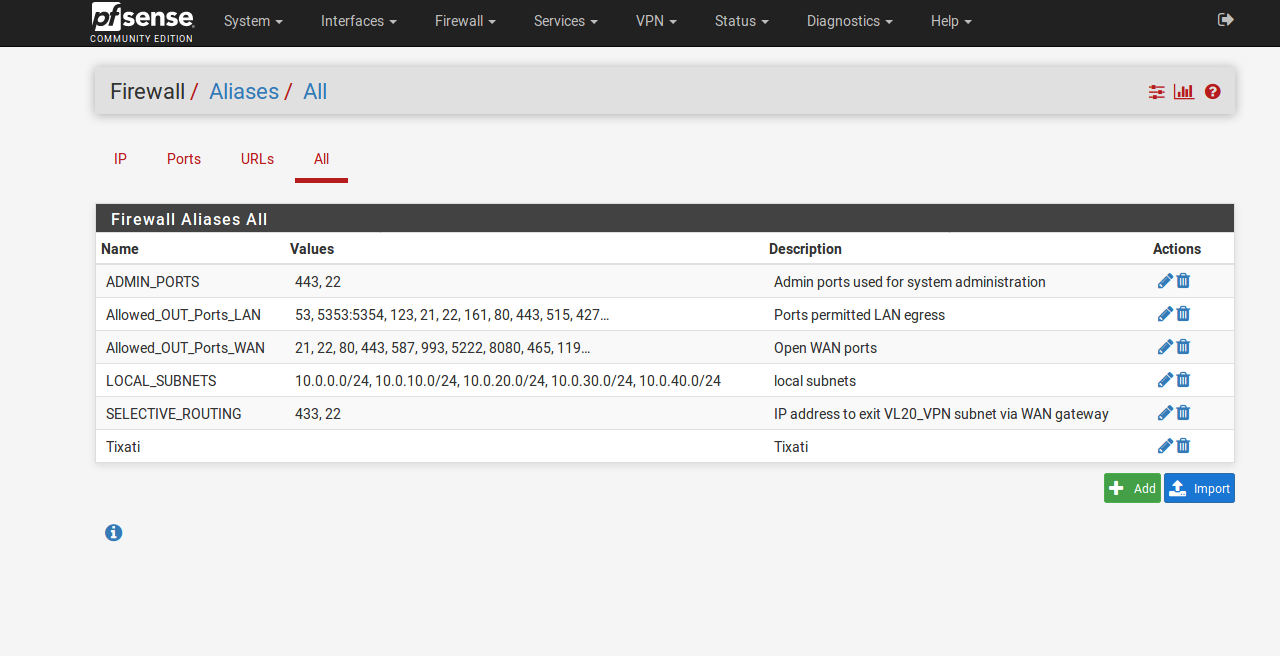
The UDP traffic is blocked because 137/138 are not in the allows out WAN alias.
Run a continuous ping to 9.9.9.9 then check the state table to make sure it is opening states on the vlan30 and wan interfaces.
Steve
-
This post is deleted! -
This post is deleted! -
This post is deleted! -
Made a few errors in checking pings but here is states for VLAN_30 that should just go out to clear isp ping to 9.9.9.9
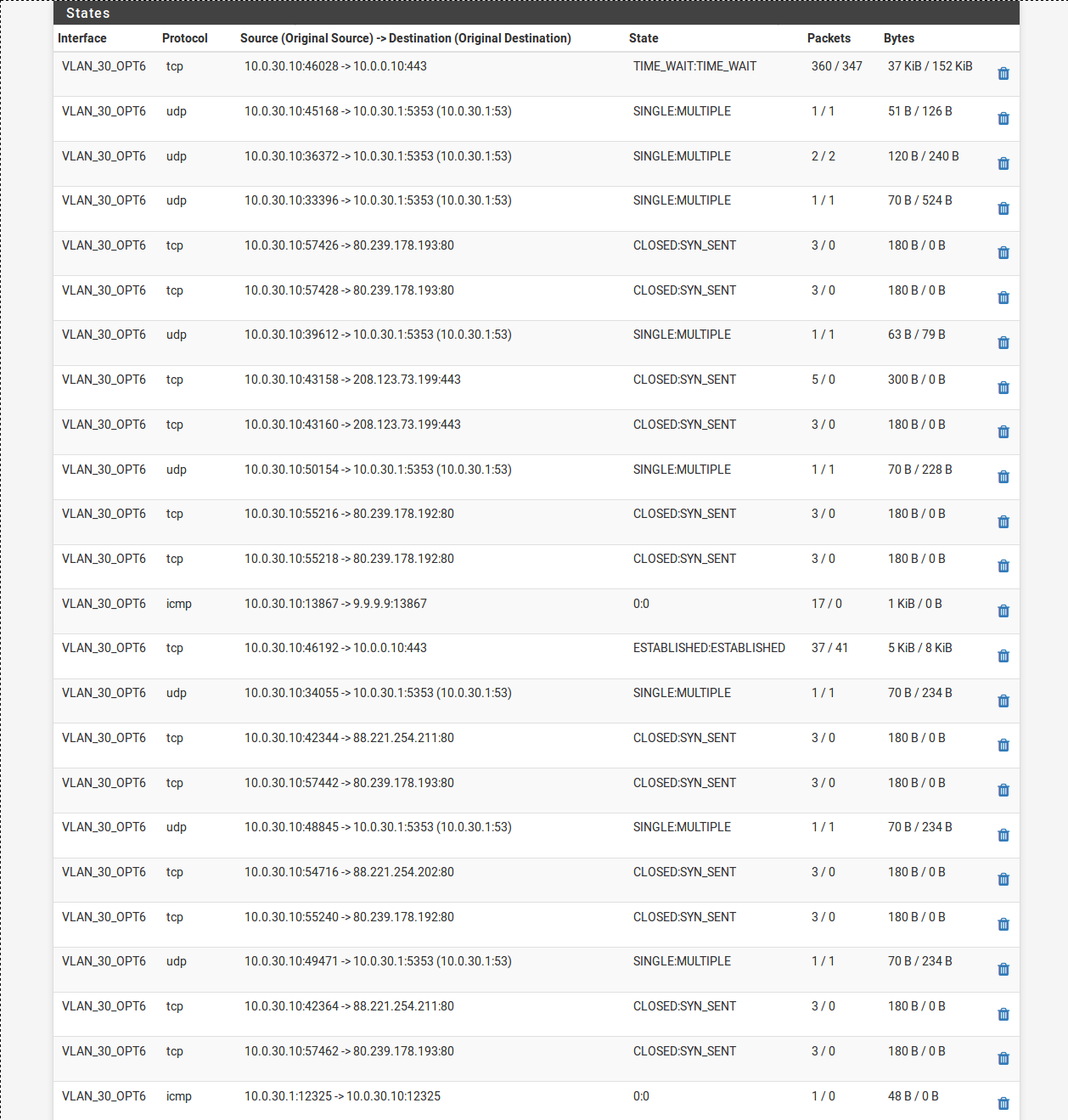
Getting packets going out on icmp nothing back (if I understand it correctly)
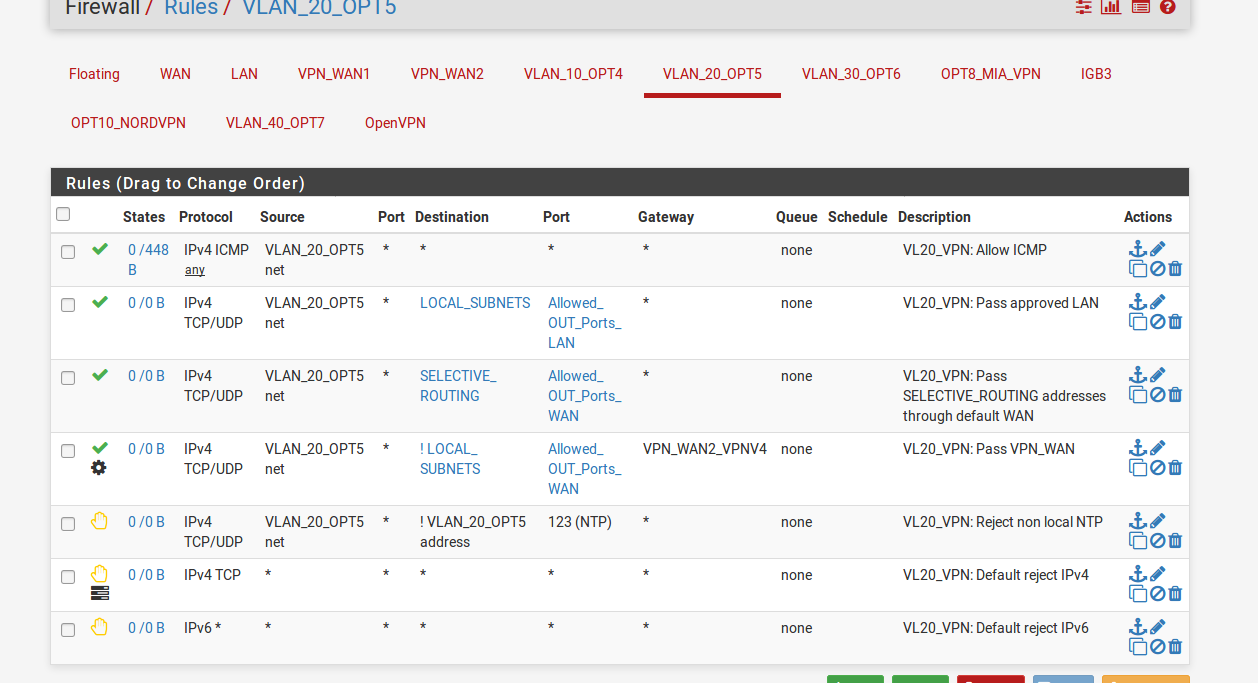
On VLAN20 equal in and out -
Yes but you should leave the state table set to all interfaces and filter by 9.9.9.9 so you can see all the states created.
You should see a state on VLAN_30_OPT6 and another state, with NAT, on WAN.
Steve
-
Sorry not really knowing what to do here.
OK so this is connected to VLAN30 wifi -interface all - filtered to 9.9.9.9 whilst pinging 9.9.9.9
VLAN_30_OPT6 icmp 10.0.30.10:17324 -> 9.9.9.9:17324 0:0 72 / 0 6 KiB / 0 B
VPN_WAN2 icmp 10.0.30.10:17324 -> 9.9.9.9:17324 0:0 72 / 0 6 KiB / 0B
is that 72 out nothing back?
-
Yes it is but more importantly is that it's leaving via VPN_WAN2 which seems like that's not what you intended.
I think your VPN connection is pushing a new default route when it connects so all the traffic without a gateway set will then use it. And since you don't have outbound NAT rules for that it leaves with the internal, unroutable, source IP and sees no replies.
Edit your VPN client and set 'Don't pull routes' to prevent the remote server setting a new default route. Check the routing table when it connects to be sure.
Steve
-
Many thanks Steve! You're a genius! adding route-nopull worked.
VLAN30 is clear to isp and VLAN20 on VPN and does not go outside when the VPN connection is dead.
Problem sorted!! Thanks again!!