DNS Resolve Domain Overrides do not work after pfsense restart
-
So every single time I reboot my pfsense boxes (I have two and they are connected via a site-to-site openvpn connection with domain overrides setup with each other), the domain overrides stop working until I manually restart the DNS resolver service. Is this possibly because the DNS resolver boots up almost always first than when the openvpn client-server connection is established? That's the only I can think of but I highly doubt that's the case. But yeah, it's easily reproducible and I think is a bug.
What do you guys think?
-
Nobody? :(
-
Well if your trying to bind to an interface (your vpn connection) and this interface does not exist or is not up yet... How would unbound bind to it?
Not sure how that would be considered a bug?
How do you have unbound setup.. Are selecting all interfaces? Specific interfaces for listen/outgoing?
-
@johnpoz said in DNS Resolve Domain Overrides do not work after pfsense restart:
Well if your trying to bind to an interface (your vpn connection) and this interface does not exist or is not up yet... How would unbound bind to it?
Not sure how that would be considered a bug?
I understand that part but when the VPN connection is already up, why do I need to restart unbound so that it can bind to it? Why can't it bind automatically when the interface becomes up just like what it does with the local interfaces?
How do you have unbound setup.. Are selecting all interfaces? Specific interfaces for listen/outgoing?
Unbound listens on these interfaces:
OPENVPN ipv4/ipv6
1 LAN interface ipv4/ipv6
3 VLAN sub-interfaces ipv4/ipv6
LocalhostAnd outgoing:
WAN ipv4/ipv6
OPENVPN ipv4/ipv6 -
No it can not just restart on its own if it failed to bind... What does the log say.. It will tell you what it binds to when it starts...
Try ALL, vs specific - does that fix your issue?
-
@johnpoz said in DNS Resolve Domain Overrides do not work after pfsense restart:
No it can not just restart on its own if it failed to bind... What does the log say.. It will tell you what it binds to when it starts...
Try ALL, vs specific - does that fix your issue?
I see. Can you put set unbound to be dependent on the openvpn connection before trying to bind to it? Or maybe put a delay? I'm sure I'm not the first who has this problem, right?
I don't want unbound to listen on the WAN interface and I also don't want it to use the other LAN interfaces to query for requests. How would specifying ALL fix the issue though?
-
Just because it listens doesn't mean its reachable - you would have to allow for access via a firewall rule.
It's possible users have not run into this because the default is ALL, so how unbound does it binding in that fashion "could" allow for additional interfaces to be used as they come online..
I would suggest it for atleast test of your scenario. But sure you could create a script to restart unbound after your interface has had enough time to come online.
-
@johnpoz said in DNS Resolve Domain Overrides do not work after pfsense restart:
Just because it listens doesn't mean its reachable - you would have to allow for access via a firewall rule.
It's possible users have not run into this because the default is ALL, so how unbound does it binding in that fashion "could" allow for additional interfaces to be used as they come online..
I would suggest it for atleast test of your scenario. But sure you could create a script to restart unbound after your interface has had enough time to come online.
I see. So only the network interfaces should be set to all, correct? The outgoing interfaces can remain as they are?
-
Yeah try that and see if it fixes your problem - since your problem is that "clients" can not query you on your vpn interface.
Other solution could be to use the unbound normal interface IP as your dns... say the lan side IP vs the vpn interface IP.
edit... Oh wait this is unbound trying to query down the vpn connection as outgoing to hit your domain override right.. Set your outgoing to localhost and remove the vpn.... It should just be able to route then normally..
I have my outgoing interface as localhost, and unbound works just fine..
-
@johnpoz said in DNS Resolve Domain Overrides do not work after pfsense restart:
Yeah try that and see if it fixes your problem - since your problem is that "clients" can not query you on your vpn interface.
Other solution could be to use the unbound normal interface IP as your dns... say the lan side IP vs the vpn interface IP.
edit... Oh wait this is unbound trying to query down the vpn connection as outgoing to hit your domain override right.. Set your outgoing to localhost and remove the vpn.... It should just be able to route then normally..
I have my outgoing interface as localhost, and unbound works just fine..
Ok, I just did your suggestion and I guess I would need to monitor if I'll still encounter the issue. But I don't understand though, isn't the VPN connection supposed to be an outgoing interface because the domain override on one side is using the VPN interface IP of the other side "through that VPN connection"? Same reason why you need the WAN connection as an outgoing interface, right?
EDIT: Removing the VPN connection as outgoing totally made the domain override not work, as I've expected. I had to put it back and kept the localhost as outgoing too but I can't get my head around as to why you need localhost to be an outgoing interface.
-
if you use localhost as outgoing it will be natted to interface it uses to get to where your going..
What IP do you have set in your domain override... What is the dest... I can for sure fire this up as sim on a couple of VM pfsenses..
Does yoru domain override point to the pfsense on the other side IP or dns internal to the other site?
Don't point your override to vpn IP, it should just be say your pfsense lan IP on the other end.
-
@johnpoz said in DNS Resolve Domain Overrides do not work after pfsense restart:
if you use localhost as outgoing it will be natted to interface it uses to get to where your going..
So then that goes without saying that you also don't need to specify the WAN as an outgoing interface for unbound as long as you have localhost because pfsense will know how to route the DNS request properly out of the correct interface based on the routing table? And is it generally a good idea to include localhost to the outgoing interface?
What IP do you have set in your domain override... What is the dest... I can for sure fire this up as sim on a couple of VM pfsenses..
Does yoru domain override point to the pfsense on the other side IP or dns internal to the other site?
Don't point your override to vpn IP, it should just be say your pfsense lan IP on the other end.
Correct, my domain override is pointing to the vpn interface on the other side of the tunnel. But yes, I can easily change it to the pfsense LAN IP. How is this different though? The VPN IP and the LAN IP on the other side will approximately be up at the same time anyway (when the tunnel is up)?
-
Did you have time to check on this?
-
Oh dude my bad... I forgot all about this thread.. I should have some time today and hope to sim this.
Dont point to the vpn IP... and yeah you should use local host as your outgoing.
-
@johnpoz said in DNS Resolve Domain Overrides do not work after pfsense restart:
Oh dude my bad... I forgot all about this thread.. I should have some time today and hope to sim this.
Dont point to the vpn IP... and yeah you should use local host as your outgoing.
No worries, I figured to just follow-up :)
What's the difference between using the VPN IP vs. the LAN IP though?
And if I use localhost as the sole outgoing interface, does that mean I can remove the WAN interface from the list as well? What's the advantage of using localhost?
-
If you just use localhost, then it will nat to the interface it needs to use to get somewhere... Be it your wan IP to talk to public servers.. Or your vpn interface IP to talk down your vpn..
On the listening end, if when unbound starts and the vpn is not up - how could it bind to that IP? It might work with any.. But why point to the vpn IP as destination in your domain overide... This IP could change, and your route doesn't point to vpn tunnel network, it points to the remote lan network, etc.
If you do these 2 things you shouldn't have any issues - as long as the tunnel is actually up when you try and query.
-
@johnpoz said in DNS Resolve Domain Overrides do not work after pfsense restart:
If you just use localhost, then it will nat to the interface it needs to use to get somewhere... Be it your wan IP to talk to public servers.. Or your vpn interface IP to talk down your vpn..
And when unbound nats to the interface it needs to use, that's a good thing? Why not use the interfaces directly? Sorry, I'm still not getting the point. I mean I know both of these work but I'm curious about the differences.
On the listening end, if when unbound starts and the vpn is not up - how could it bind to that IP? It might work with any.. But why point to the vpn IP as destination in your domain overide... This IP could change, and your route doesn't point to vpn tunnel network, it points to the remote lan network, etc.
If you do these 2 things you shouldn't have any issues - as long as the tunnel is actually up when you try and query.
Right but won't it be the same thing? When unbound starts and vpn is not up, then how can it bind to the lan IP on the other side of the tunnel too? If you think of it, the vpn IP will always go up first compared to the lan IP on the other side of the tunnel.
Also, my site-to-site vpn IP network uses static IP's so those won't change.
-
dude if you tell unbound to use interface X, and interface X is not UP when unbound starts - then you have issue... If you tell unbound to use loopback.. Which is going to be UP!! then doesn't matter if the other interface goes up down, up down, etc.. As long as its up - you will be able to use it for outbound query.
Same thing for when unbound starts... The LAN IP should always be up.. .But will your site2site be up when unbound starts and wants to bind to your vpn IP??
You don't bind to a remote IP..
edit: Ok got baseline setup sim your setup.
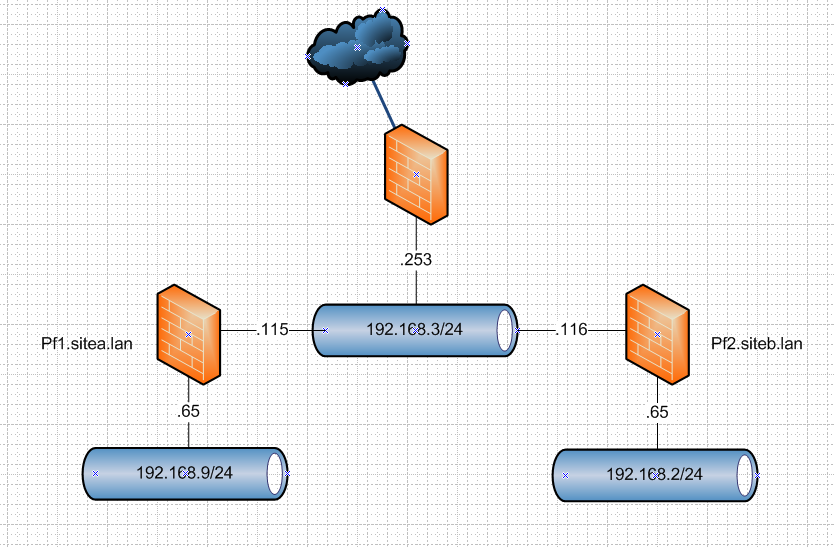
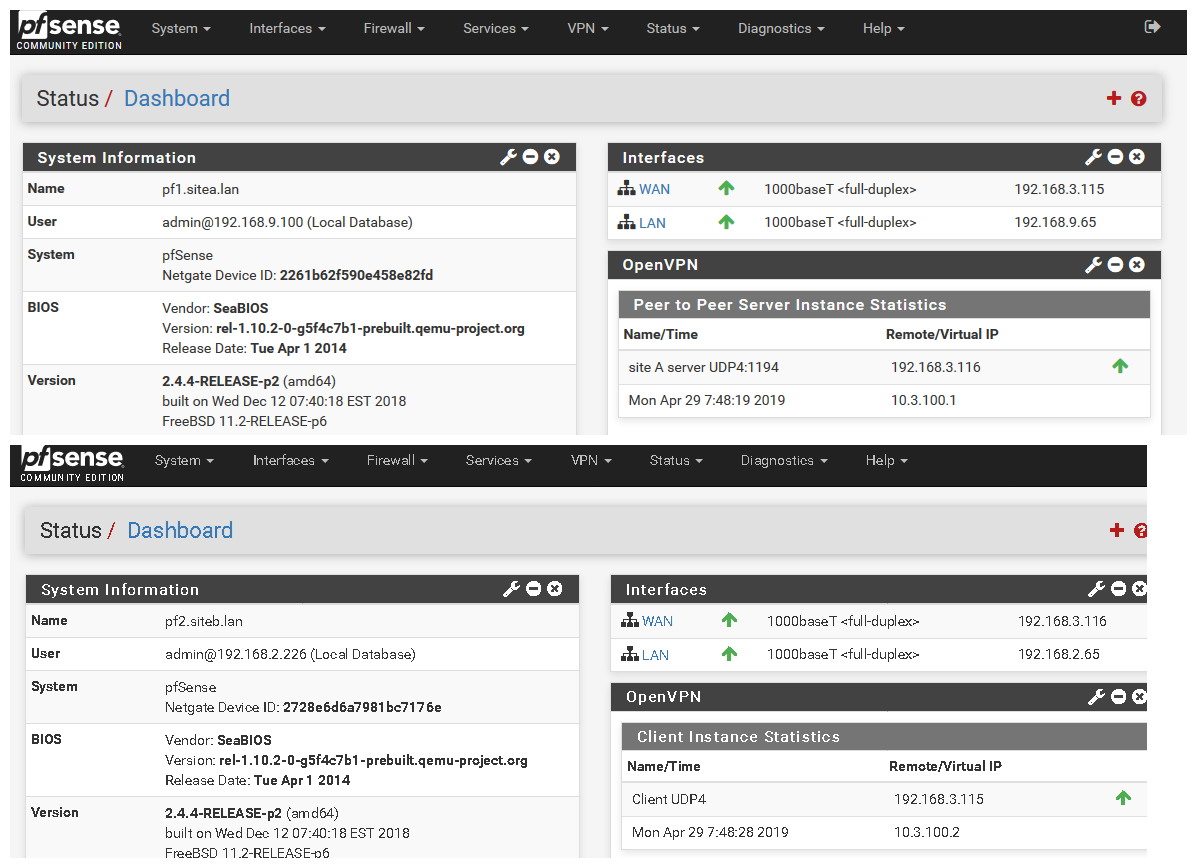
So I will fire up a s2s vpn between these 2 vms (2.4.4p2) over their wan networks (192.168.3/24) and then create domain overrides pointing to the other domain sitea or b, and create some records in there and validate the can be queried after reboot of them, etc.
But I will use what I think is correct way to do this and that is use localhost for outbound, and override pointing to the lan IP in my test setup that would be 192.168.9.65 for sitea, and 2.65 for site b.
edit2: ok up and running
using this guide
https://docs.netgate.com/pfsense/en/latest/book/openvpn/site-to-site-example-configuration-shared-key.html
-
I'm having this issue as well; though no domain overwrite. Just a simple OpenVPN connection; I need the interface for some firewall rules.
I was able to test choosing different interfaces, including all, specific and localhost.
Basically to get mine working after a reboot; (restarting the service doesn't appear to work) I have to assign the default gateway to WAN and then back to OPENVPN interface
-
@burny02 said in DNS Resolve Domain Overrides do not work after pfsense restart:
ult gateway to WAN and then back to OPENVPN
That is has ZERO to do with this sort of setup... Your default gateway should NEVER be your openvpn interface..
Please create your own thread with your own details of what you think is a problem... Using some vpn service has nothing to do with a site2site setup and dns overrides.
I have to run for work -- but using localhost doesn't seem to work for going down the vpn... But if set it to all it works... When set it to localhost get servfail...
$ dig @192.168.9.65 test.siteb.lan ; <<>> DiG 9.14.1 <<>> @192.168.9.65 test.siteb.lan ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: SERVFAIL, id: 49807 ;; flags: qr rd ra; QUERY: 1, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;test.siteb.lan. IN A ;; Query time: 2 msec ;; SERVER: 192.168.9.65#53(192.168.9.65) ;; WHEN: Mon Apr 29 09:06:17 Central Daylight Time 2019 ;; MSG SIZE rcvd: 43But if set to any as outgoing then works..
$ dig @192.168.9.65 test.siteb.lan ; <<>> DiG 9.14.1 <<>> @192.168.9.65 test.siteb.lan ; (1 server found) ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 31728 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;test.siteb.lan. IN A ;; ANSWER SECTION: test.siteb.lan. 3600 IN A 192.168.2.222 ;; Query time: 5 msec ;; SERVER: 192.168.9.65#53(192.168.9.65) ;; WHEN: Mon Apr 29 09:05:06 Central Daylight Time 2019 ;; MSG SIZE rcvd: 59But now that have this test best setup... Can see what is going on... And figure out best configuration for this...
Did you actually create an interface for your openvpn? The guide I linked does have you assign and interface to your openvpn s2s..