WAN /26 into 2x DMZ /27 and multiple LANs using vlan.
-
They need to give you a small interface network, like a /29 or /30, and route the /26 to you on that.
So I can get my ISP to make a /29 'transit network / link net'. So I guess I declare to the ISP which ip within my /26 that acts as the gateway/router for the /26? And then that gateway/router is assigned the ISP gateway of the /29 correct?
This gateway/router is in this case the pfsense firewall. But in practical terms how do I split/use my /26 so I get a firewalled DMZ with public ips and a non-firewalled DMZ with public ips using pfsense?
I have 4 interface on the pfsense firewall. Ideally I would use 1 for WAN, 1 for LAN, 1 for firewalled DMZ and 1 for non-firewalled DMZ. (Potentially also using vlans to isolate public ips from each other on the DMZs).
Best regards
-
Actually you (or your ISP) declare which IP address on the /29 the /26 is routed to.
Once you have the /26 routed to you you can do whatever you want with the addresses.
Just split it into two /27s and use those as the interface addresses for the DMZ networks and disable NAT for them.
Example (in Cisco-ish Speak):
Their Side:
Interface (transit) network:
interface ethernet 0/0
ip address 198.51.100.1 255.255.255.248Routed /26 Subnet:
ip route 192.0.2.0 255.255.255.192 198.51.100.2
Your side:
Interface (transit) network:
interface WAN
ip address 198.51.100.2 255.255.255.248DMZ Networks
/27
interface DMZ
ip address 192.0.2.1 255.255.255.224/27
interface DMZ1
ip address 192.0.2.33 255.255.255.224ip route 0.0.0.0 0.0.0.0 198.51.100.1
-
@Derelict Thanks for your recommendation. I can only agree that it is much more clean and easy to configure with a link/transit network.
(Due to some ISP issues with a new fiber it took forever to proceed with the case.)
Followed the guide here: https://docs.netgate.com/pfsense/en/latest/book/routing/routing-public-ip-addresses.html
all great expect for the outbound NAT instructions. I had to change to "Manual Outbound NAT rule generation (AON - Advanced Outbound NAT)" and delete the auto generated rules. It was not enough to use the hybrid with NO NAT options.Link net/transit net /29 (WAN)
Inside net /28 split into two /27 (DMZ1 and DMZ2)
RFC1918 /16 (LAN)BR
-
@desrux2 said in WAN /26 into 2x DMZ /27 and multiple LANs using vlan.:
It was not enough to use the hybrid with NO NAT options.
That is enough. You should have posted what you had when it wasn't working because there was probably a mistake made.
-
@Derelict said in WAN /26 into 2x DMZ /27 and multiple LANs using vlan.:
@desrux2 said in WAN /26 into 2x DMZ /27 and multiple LANs using vlan.:
It was not enough to use the hybrid with NO NAT options.
That is enough. You should have posted what you had when it wasn't working because there was probably a mistake made.
Sure thing.
Not working:
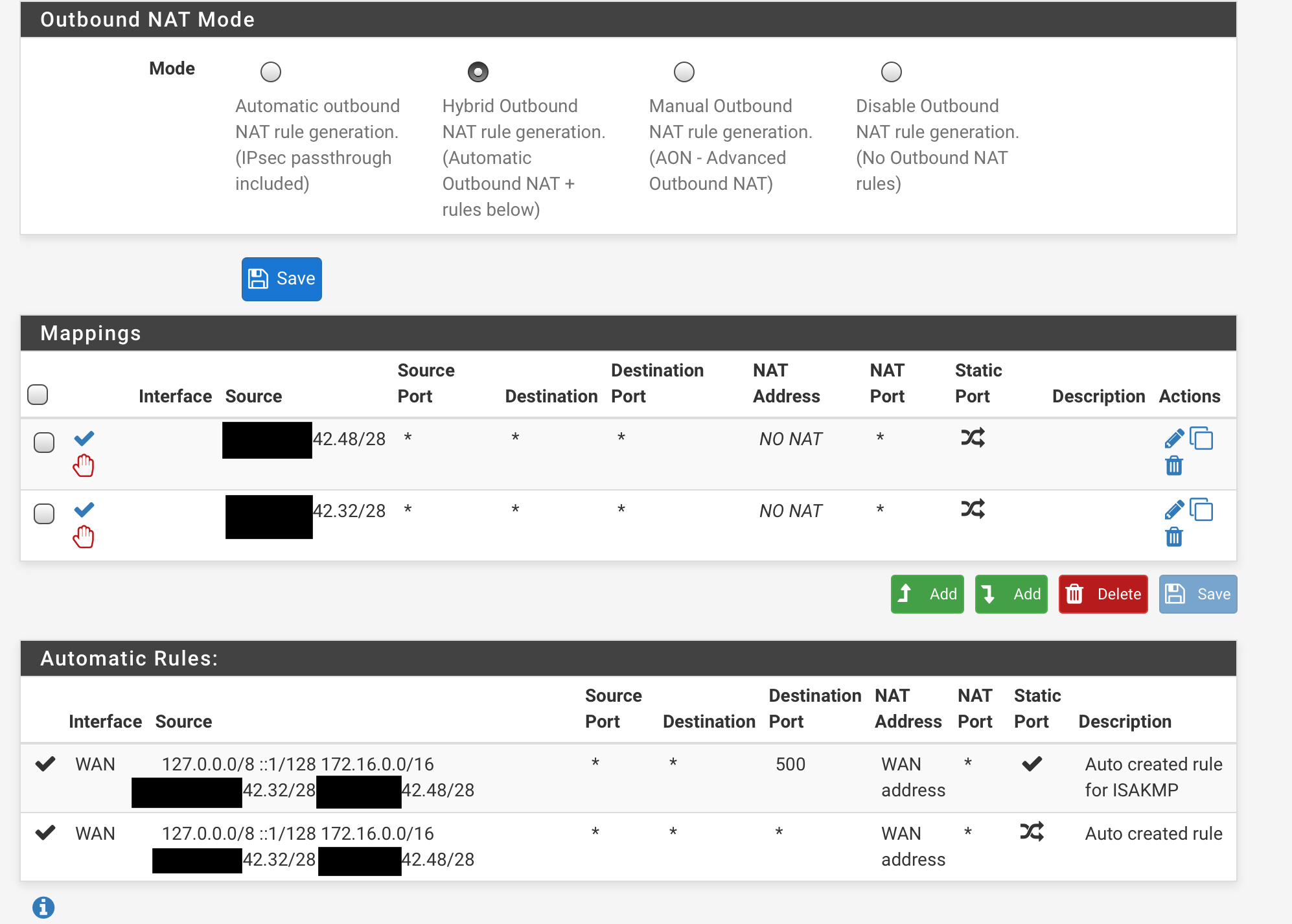
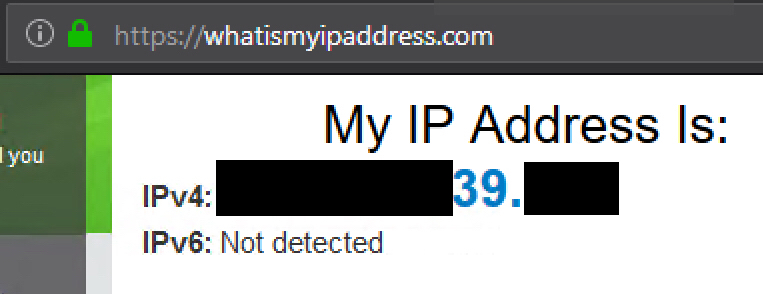
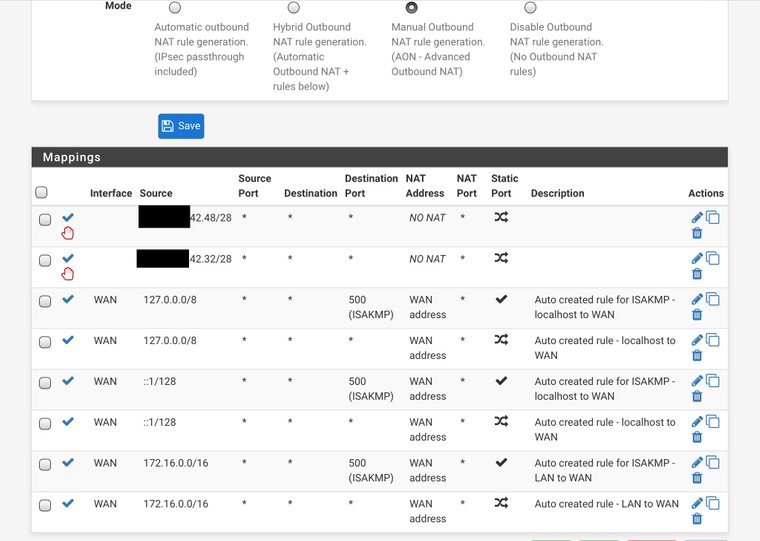
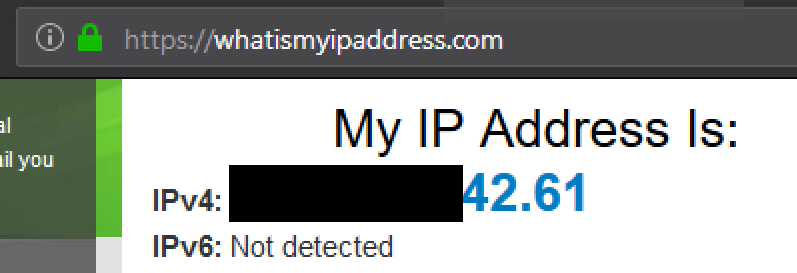
Working (I would assume I can also remove the NO NAT):
-
@Derelict
Found the issue. The NO NAT settings had somehow lost the interface assignment. It would look correct in the settings but not until clicking save (without changing anything) would the WAN show up in the menu.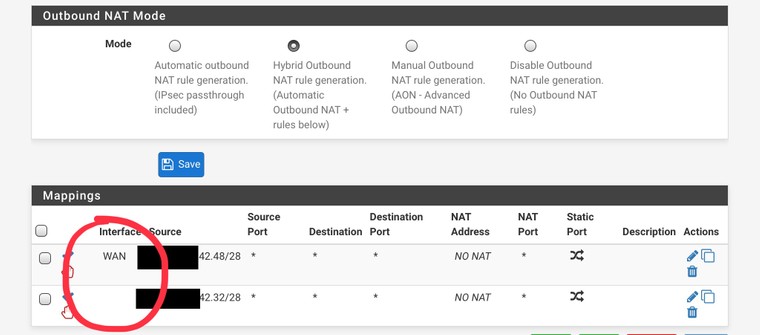
I wonder if this happens if the firewall has experienced at some point loosing said interface during boot?
-
I don't know. I have never seen that. booting after losing an assigned interface should trigger interface reassignment.
-
I'd not go with "no NAT" rules but instead switch to manually configuring NAT, delete the automatic copied entries that aren't needed (those on the IFs with public IPs) and be done :)
-
@JeGr Agreed!
-
In an HA environment where all NAT needs a custom rule I would agree.
I like the NO NAT rules in this case. The routed subnet is unlikely to change, leaving Automatic NAT in place.
Personal preference, of course.