wifi hotspost capitive portal
-
Hi everyone, I have a 2.4.4 pfsense, I have two Wifi on my network so structured:
1 AP wifi connected directly to a switch and through the classic wifi password we access the company network.
but I wanted to create a Wifi for the clients / guests who come to the venue so as not to have to spread the wifi password to everyone, so I weighed a new one, I connected it on an (physical) interface of the pfsense and I configured it with a different subnet of course
then I followed the quido of pfsenseitaly (even if dated) to create an interface with the Voucher management, and I must say that it works very well so thanks.
but I have two problems that I want to list:although I made the rule to block all wifi_host accesses on the LAN, I see it anyway and don't understand why
When you are on the wifi from a PC and I try to open a site I get the mask of the capitive portal that asks for the various passes or the voucher and here everything is ok but if the site I try to open is not a normal site but it is gmail.com or google.com (I think of the https sites) this mask does not appear for voucher insertion but after a while we think it says invalid page
according to you how do I solve these two annoying problems?thank you
-
@miami71it said in wifi hotspost capitive portal:
although I made the rule to block all wifi_host accesses on the LAN, I see it anyway and don't understand why
What do you mean ? A rule on what interface ? Show your settings.
@miami71it said in wifi hotspost capitive portal:
When you are on the wifi from a PC
What wifi ? The captive portal network or your company's network ?
@miami71it said in wifi hotspost capitive portal:
but if the site I try to open is not a normal site but it is gmail.com or google.com (I think of the https sites) this mask does not appear for voucher insertion but after a while we think it says invalid page
That's normal. No one can intercept an SSL connection. I've explained in this part of the forum already many times why this is actually not a problem. And thus this 'issue' doesn't need a solution : it is already resolved.
See here : https://forum.netgate.com/topic/142197/redirect-problem-with-ssl-certificate/2What do you mean by "a normal site" ? All sites are SSL or https these days. A non https site is quiet rare these days.
Have a look at the official captive portal videos, published by Netgate https://www.youtube.com/channel/UC3Cq2kjCWM8odzoIzftS04A/videos
-
@Gertjan
although I made the rule to block all wifi_host accesses on the LAN, I see it anyway and don't understand whyWhat do you mean ? A rule on what interface ? Show your settings.
I did the blocking rule on WIFI_GUEST
block ip4 * source WIFI_GUEST port = * destination LAN_NET port = *
pass ip4 * source WIFI_GEST port = * destination = * port = 80
pass ip4 * source WIFI_GEST port = * destination = * port = 443these are the rules made on the WIFI_GUEST interface
how mail lan_net is still reachable?for the other answers, now I look at the links you gave me
-
@miami71it said in wifi hotspost capitive portal:
I did the blocking rule on WIFI_GUEST
block ip4 * source WIFI_GUEST port = * destination LAN_NET port = *
pass ip4 * source WIFI_GEST port = * destination = * port = 80
pass ip4 * source WIFI_GEST port = * destination = * port = 443Not clear - not enough.
I'll show you mine : very clear :
My PORTAL interface (== your WIFI_GUEST) can not connect to LAN and its devices using these rules.
These rules are tested during the last ... 10 years.
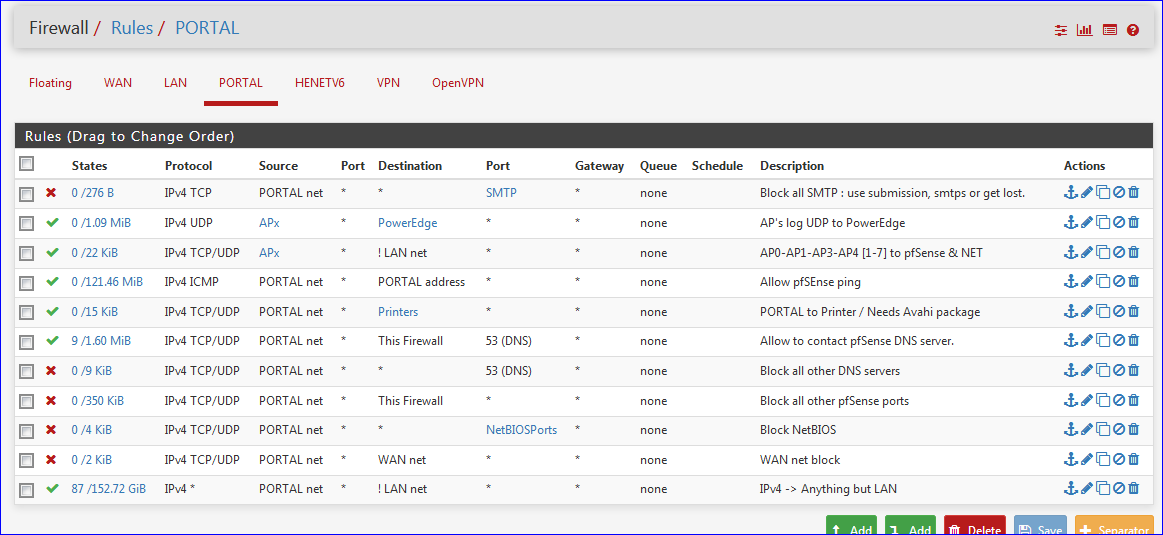
I advise you to use the same rule sequence.
Let's say "Block all SMTP ..." is rule 1.
You could skip rules 2 - 3 and 5 which are pass-troughs to LAN for my equipment .NetBiosPorts are 135-137-139-445
-
I made the rules as you told me but if I don't set a PASS rule on http and https the internet doesn't go but the LAN continues to be visible to users who connect with WIFI_GUEST, WIFI_GUEST users only need to be able to navigate and not go on the LAN
-
See my last line :
It let out visitors to everything except LAN.
Using every protocol and ports except the ones blocked above.
edit : as you can see, this rule has a huge 152 GB usage counter in front of it. Most traffic goes out using this rule. -
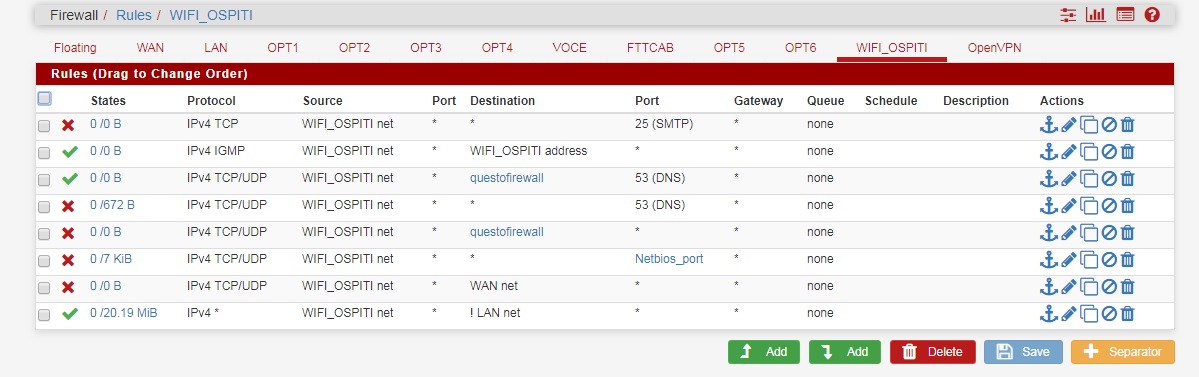
I executed the rules you described to me literally but I continue to access the LAN
I attach screenshot
-
sorry I solved I had forgotten activating a floating rule that was used to see wifi_ospiti to lan_net
everything works now
THANK YOU SO MUCH