How to script rules on OpenAppID to block torrents
-
Hello guys, can someone help me to script a rule that would block torrents on my network. I currently have snort running plus OpenAppID. It detects torrents but i can't seem to block all torrents,without blocking the host
-
@OpenWifi said in How to script rules on OpenAppID to block torrents:
Hello guys,can someone help me to script a rule that would block torrents on my network. I currently have snort running plus OpenAppID.It detects torrents but i can't seem to block all torrents,without blocking the host
Do you need to change to DST on the LAN interface?
-
@NogBadTheBad Thank you for the answer. I am new to pfSense. Kindly elaborate the difference between DST and SRC?
I would only like to block the application not the host using it. -
On your local LAN SRC ( source ) would be your PC and DST ( destination ) would be the P2P server.
You have just enabled OpenAppID on the LAN havent you ?
-
@NogBadTheBad Yes, i did
-
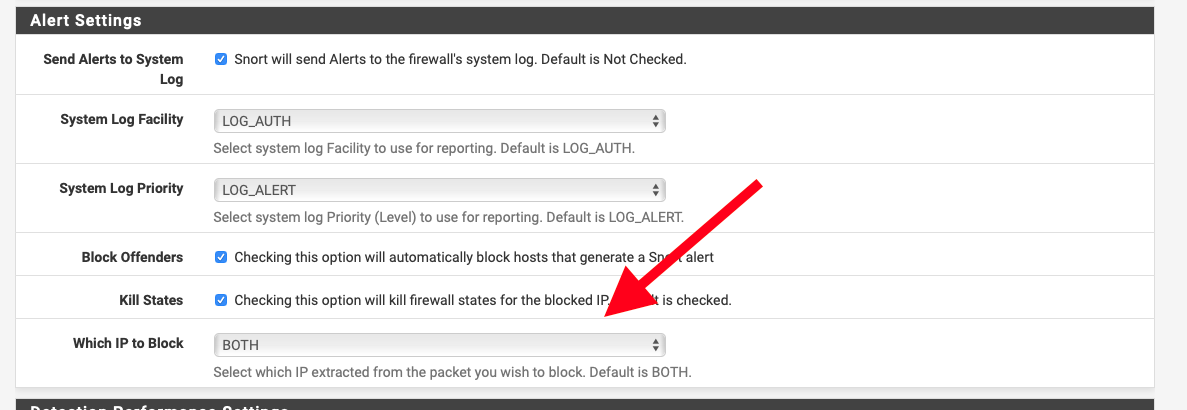
You also want to be sure the Remove Blocked Hosts Interval is set to something other than none.
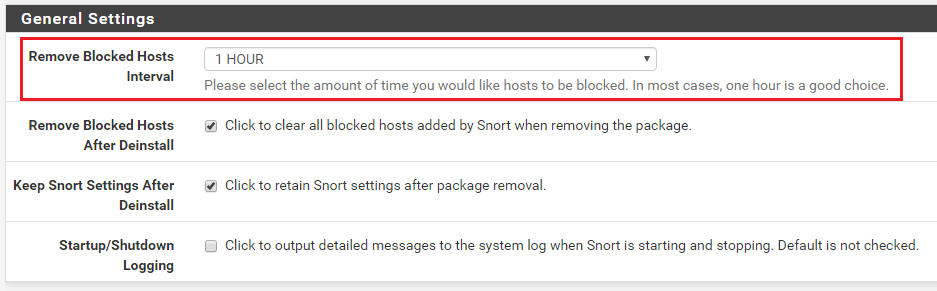
I suggest 1 HOUR as a good compromise. This will remove a host from the block list after the time period specified if that host has not triggered another block during the interval.
I gather you don't want Torrent traffic on your network, so this will allow you to "punish" the offending host by blocking them for some period of time (but not forever). You can even notify them that any attempt at Torrent connections will result in a block.
If you don't want to block the local host, then you will need to create a firewall alias and assign the host to that alias. Then create a custom Pass List and add the alias to it. Finally, you would go to the INTERFACE SETTINGS tab for the interface and select the custom alias and apply it to the Pass List drop-down for the interface.
-
@OpenWifi said in How to script rules on OpenAppID to block torrents:
Hello guys,can someone help me to script a rule that would block torrents on my network. I currently have snort running plus OpenAppID.It detects torrents but i can't seem to block all torrents,without blocking the host
Snort works by blocking hosts with firewall rules. The rule is a special hidden rule that you don't see displayed in the GUI. That rules gets lists of IP addresses to block. It is not selective with the type of traffic. Once a Snort rule triggers, the blocking code extracts the IP addresses from the traffic that triggered the rule and blocks those IP addresses. It can be selective and block only the Source IP, the Destination IP or Both. The default is BOTH. Who is "Source" and who is "Destination" changes as packets flow back and forth between two hosts. A good analogy is a regular snail-mail letter. When you send the letter, you put the recipient's address in larger print in the center and your return address in smaller print at the upper left. That reverses when the recipient replies to you. When you send the letter, your address is the "source" and the recipient's address is the "destination". When they reply back to you with another letter, then suddenly they are the "source" and your address is now the "destination".
-
@bmeeks Thank you. So in short, i cannot block the torrent application without blocking the internal Ip address
-
@OpenWifi said in How to script rules on OpenAppID to block torrents:
@bmeeks Thank you. So in short, i cannot block the torrent application without blocking the internal Ip address
True. The Snort application works by blocking host IP addresses using a custom blocking module compiled into the binary. The blocking module blocks an IP address, so once a host is added to the Snort blocking rule, all traffic to/from that host is blocked until the IP is removed from the blocking rule.
You can still probably implement what you want by creating that firewall alias I mentioned and using it in a custom Pass List for the interface. A Pass List is a collection if IP addresses that Snort will not block even if they trigger a rule. You will get an alert on the traffic, but the IP addresses listed in a Pass List will not get blocked when the alert fires. Here is a link to the documentation for managing Pass Lists: https://docs.netgate.com/pfsense/en/latest/ids-ips/setup-snort-package.html#managing-pass-lists.
Suricata can function as a true inline IPS that can "drop" offending packets as they traverse the firewall, but without inserting a firewall block rule that will block all other of the host's traffic. Unfortunately Suricata does not have the OpenAppID feature as the upstream developers have not included that option.
-
@bmeeks can i not use custom rules in Snort such as alert and drop to block the apps? Found it in this link http://blog.snort.org/2014/04/openappid-application-rules.html
Kindly confirm, so that i dont end up doing the wrong thing -
@OpenWifi said in How to script rules on OpenAppID to block torrents:
@bmeeks can i not use custom rules in Snort such as alert and drop to block the apps? Found it in this link http://blog.snort.org/2014/04/openappid-application-rules.html
Kindly confirm, so that i dont end up doing the wrong thingNo, you can't block just the "app". You can detect the app and trigger a block rule when the app is used, but that rule will block a host's IP address and will block ALL future traffic to and from that host's IP address until the IP address is removed from the block table.
There is no support in Snort on pfSense for the DROP keyword. That only works with inline IPS mode, and that mode is not currently supported on pfSense. Using DROP in a rule will do nothing in Snort on pfSense.
-
@bmeeks Thank you. Although disappointed with pfSense. How i wish i could do that.
-
@bmeeks Some clients use bittorrent alot which often make the internet slow
-
I will clarify my statement by saying you can't do this on pfSense using the Snort GUI package.
You can potentially set something up if you go totally command-line with Snort and do not use the GUI at all. The GUI package cannot support inline IPS mode.
If you use the standalone binary, you can configure DAQ to use netmap IPS mode, but only if you are willing to use two actual physical interfaces and bridge them with a cross-over cable, or else put Snort and DAQ on a separate box that sits between your LAN and pfSense. None of this is easy to set up, and it would be something you would be on your own to configure and support.