General Questions
-
Why did you ask this question in a thread from 2016?
Moving your post to its own thread. You have MULTIPLE questions, so going to move it to general.
If you want to get to network behind pfsense then that would be a port forward. And you would also need to turn off the block rfc1918 address from the wan to allow the port forward to work.
that the management network of the pfsense has the same IP as the gateway of the VM´s (192.168.1.1)
Not sure what that even means.. Yes pfsense default lan IP is 192.168.1.1 - do you have something else on your network or vm host that is using that IP?
-
Hello John,
I turn off the rfc1918 but nothing happens. Please find enclosed a diagram with the current network setup fo a better understanding and also the current Firewall rules that are setup.
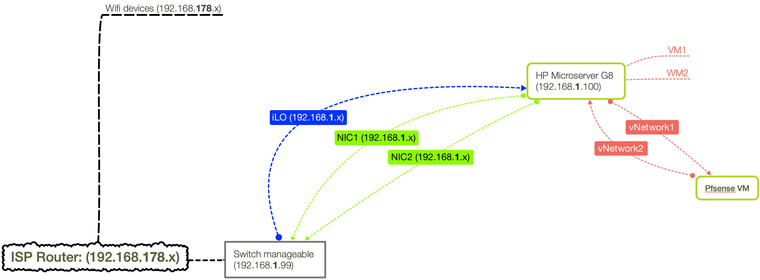
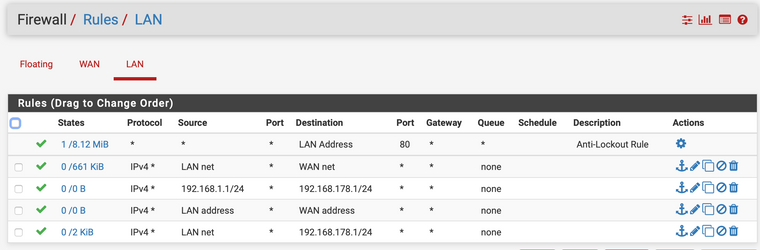
-
That drawing not making a lot of sense... Do not use pfsense lan network 192.168.1 if that is what is on the wan side of psfense..
So how exactly are you isolating the L2 that is pfsense lan from this other 192.168.1/24 network you have listed?
And your rules are messed up as well... Your clients on lan would never be able to get anywhere other than 192.168.178 from those rules..
And 192.168.178.1/24 is not even a valid cidr - that is HOST address.. not a network.
-
Can you please detail exactly what is the changes I have to make?
I don't understand nothing what you mention before.
Thanks. -
Reset pfsense to default... Change the pfsense lan network to something other than 192.168.1 or 192.168.178
192.168.178.1/24 is HOST address and not valid for a firewall rule.. The network would be 192.168.178.0/24 the IP would be 192.168.178.1/32
same goes for your rule with 192.168.1.1/24
Rules are evaluated as traffic enters the interface from the network its attached to, top down, first rule to trigger wins, no other rules are evaluated.
I can not tell you what to do on your wan because I can not tell what is what there you mention 192.168.178 but then also 192.168.1 - is this a different vlan, if so why even mention it? If pfsense is not routing through it, etc.
What VM software are you running on that G8, esxi, hyper-v, proxmox?? what?
Are you trying to use pfsense on your vm to route between 2 of your networks the 192.168.1 and the 178? If so how is that connected via your vm software?
From your drawing I don't see how 178 network is even connected to pfsense?
-
Pfsense now is reset to defaults and just have 1 NIC attached; in the console only has the WAN (192.168.178.8).
I don't know which other IP can/must have to set in this interface for example or if this one is ok.
The VM is on ESXi 6.5 does the other NIC needs to be in the same vSwitch or it must have to be in another? What I need is:
-
The VM´s on the ESXi server must have to be able to connect to the internet without changing all the IP configuration of all them; the IP they have are: 192.168.1.x and gateway 192.168.1.1
-
The physical computers that are connected by wifi obtaining the IP range 192.168.178.x must have to be able to reach the VMs that are on the 192.168.1.x
-
-
@thesharkgt said in General Questions:
Pfsense now is reset to defaults and just have 1 NIC attached
And how exactly do you think it could route between anything with 1 nic..
Dude no offense but I think you trying to do something that is just way over your skillset.. I will try and walk you through.. Draw up what you want.. Do you want pfsense to route/firewall between 2 local networks..
What exactly are you trying to accomplish here.. So you have this???
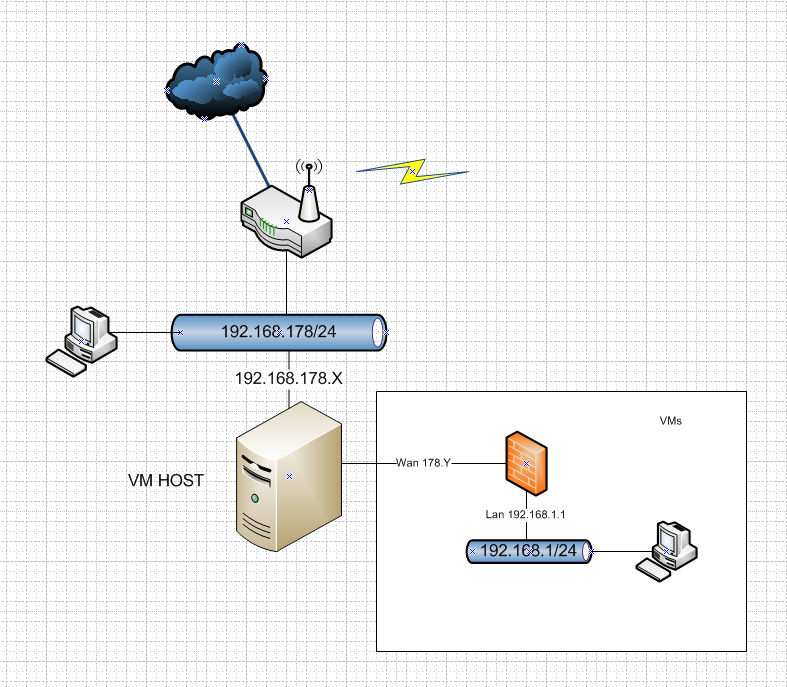
That will work just out of the box.. Connect pfsense wan via vswitch to your 178 network, and create another vswitch that its lan is connected to that you connect your other vms too.
-
The map you draw before its exactly how its setup. The pfsense now have 2 interfaces: (WAN 192.168.178.8) and (LAN 192.168.1.18) and I can access to the web interface just in the LAN; both interfaces are in different vSwitch where LAN is in the same of the VM´s and WAN is isolated. So what it remain to setup in the pfsense is:
-
The VM´s on the ESXi server must have to be able to connect to the internet without changing all the IP configuration of all them; the IP they have are: 192.168.1.x and gateway of they have is 192.168.1.1
-
The physical computers that are connected by wifi obtaining the IP range 192.168.178.x must have to be able to reach the VMs that are on the 192.168.1.x
-
-
So connect your vms to the lan vswitch you setup for pfsense.
For devices on yoru 178 network to get to stuff on the 192.168.1 network you would have to port forward.
-
The VM´s now have internet but only adding as a gateway the IP of the pfsense LAN (192.168.1.18) it is a way to instead this address they can go through 192.168.1.1?
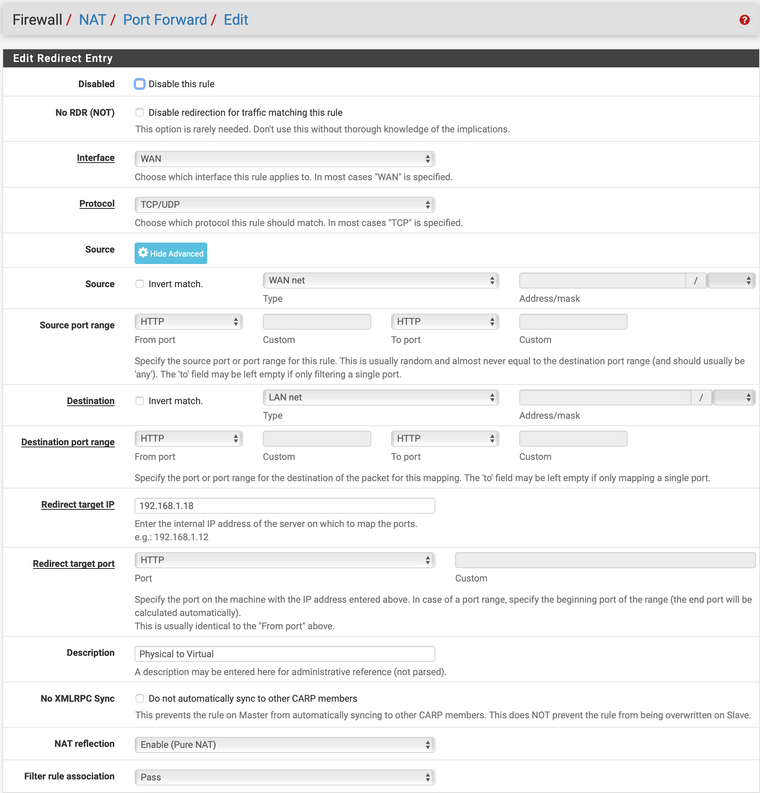
Regarding the physical computers, Im not able to setup the port forward, (Firewall/NAT/Port Forward/Edit):
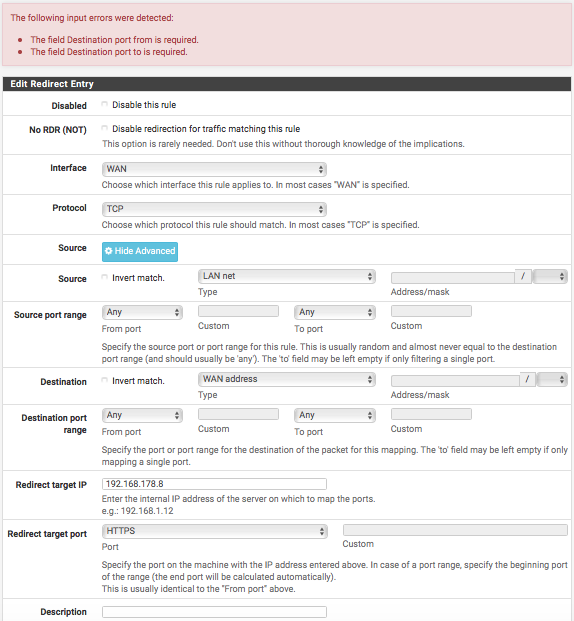
What I am missing here?
-
Your missing the whole point of port forward... When would lan net be a source on your wan?
Lets say you have 192.168.1.100 on pfsense lan.. And you want to get to its web server on 80..
Then on your port forward, source would be any, or your wan net in your case since all devices on your wan nat 192.168.178
Your dest yes would be wan address which is 192.168.178.8 it seems?
dest port would be 80 (http) for our web server example.And you would redirect to this 192.168.1.100 address - not pfsense own wan ;)
And then yes the redirection port would be the same http.. Unless!! Say it was listening for http on 8080 or something and you want to use 80 ad dest in for your clients out on your 192.168.178 network.
Keep in mind if your clients behind pfsense are pointing to a different gateway... Your configuration is already pretty borked up.. If want to get to the internet or something via a different path, then that router should be connected to pfsense via transit network, and you can policy route out...
Please add to my drawing where this 192.168.1.1 router is?? In our setup the 192.168.1 network is host only and not tied to the real world, so how is there a 192.168.1.1 already?
-
I am not able to configure it with your previous instructions, the only point is missing is that from the physical devices that are in the 192.168.178.x can be able to access to the VM´s that are in the 192.168.1.x This is what I setup and it doesn't work:
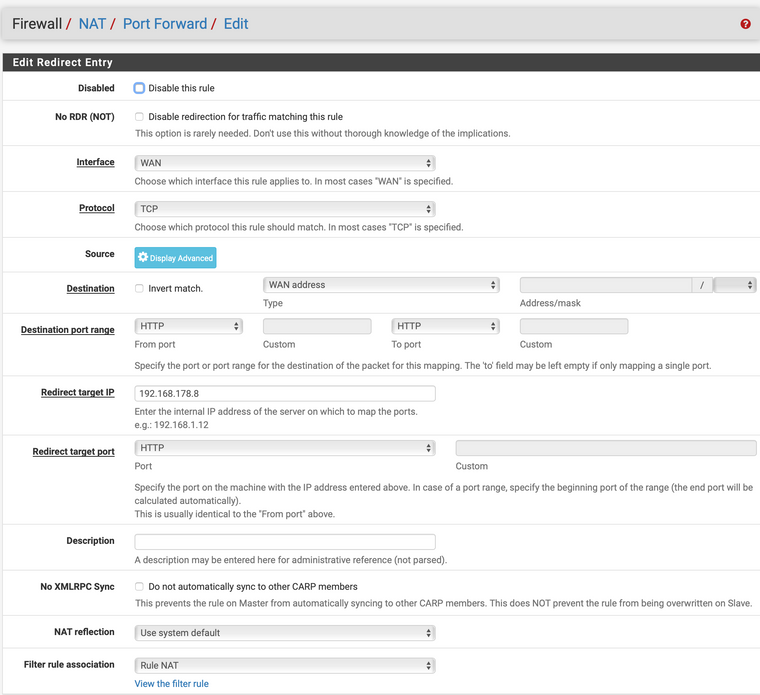
Can you please detail me what must have to be the fields in order to achieve this?
-
Dude your redirect IP is the wan IP - how do you think that could ever work???
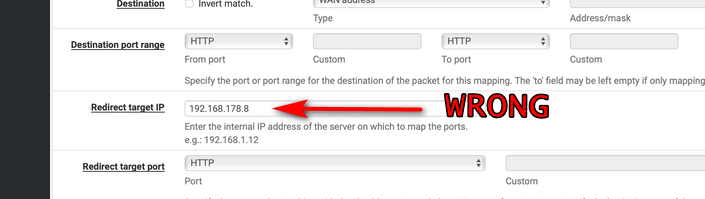
This port forward says hey any traffic that his 178.8 - send it to 178.8 ;)
If you want traffic that hits 178.8 to be forward to something on 192.168.1 then that is what the reidrect IP would be!!! 192.168.1.?
Keep in mind that that IP you send it to needs to use pfsense as its gateway to get back to the 192.168.178 network.
With a port forward if you want get to say 192.168.1.100, then you go to 192.168.178.8 it gets forwarded to 192.168.1.100..
This is a PITA if you have lots different ports that you want to talk to different devices on 1 with.. If that is the case you want to route and not nat..
-
I made the changes, tested in different configurations in previous days in the following screen and I'm still unable to access from the physical machine that is in the 192.168.178.x to the machines that are in the 192.168.168.x
I don't know what else do, to be able that this works.
-
Why did you use WAN net as source? And why the hell did you configure HTTP as source port restriction? Web traffic isn't flowing from port 80 -> port 80 but from any random high port >1023 to port 80 server side. Your source address/port setup is bonkers, that's why it won't match your incoming traffic. Set source to any and source port to any and try again. @johnpoz never wrote anything about setting source restrictions, so why do you come up with that suddenly?
-
@JeGr said in General Questions:
suddenly
Can you please specify in each field what I must have to be choose? Keep in mind that Im beginner as you can see in all the previous conversations.
-
@johnpoz explained it more than once and wrote exactly what you need, but you tend to completely ignore what he writes and throw everything together in chaos.
- NO source address or source port. Choose ANY
- Destination is your WAN ADDRESS, not a network, not LAN it is the IP that you try to access that you want forwarded to your internal host!
- Redirect IP is your internal server/host that you are trying to reach via that WAN IP
- Destination Port and Redirect Port should match your service that you want to access. I assume HTTP (Port 80).
- filter rule assoc.: "add associated firewall rule". Not simply PASS. Let the system add a rule.
- save
- apply
- test
-
What is needed in this case is that any service, program, protocol or any that is in the network 192.168.178.x where able to communicate 192.168.1.x, for example RDP, SSH, web interface etc.
Those your previous instructions are valid to achieve this or it have to be in another configuration? -
I found it finally, here you can find the way how I achieve it:
https://community.spiceworks.com/topic/2210103-access-to-same-network-in-different-ip?page=1#entry-8386216
For the next time, keep in mind that we don't come here with an expertise background, the forms that both moderators reply are not the properly way to provide solutions.
Not only is necessary to have a good knowledge, it's also important to be polite.
I wish you the best, and (even it can sounds "weird"), thanks for all.

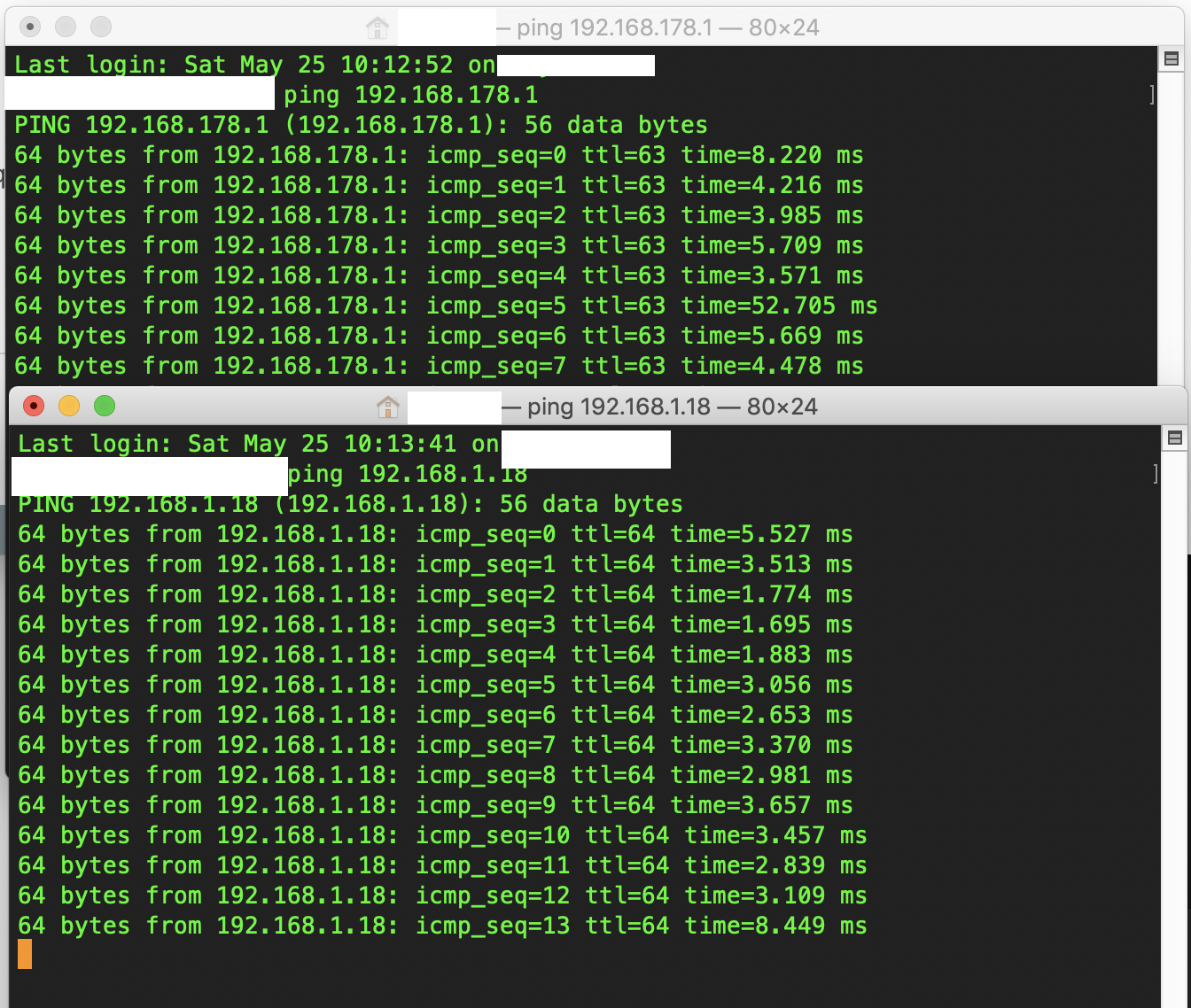
-
So you enabled outbound NAT on LAN for traffic hitting the port forwards?
If you still had pf enabled you would have to that to avoid asymmetric routing. You would have seen blocked traffic in the firewall log: https://docs.netgate.com/pfsense/en/latest/firewall/troubleshooting-blocked-log-entries-due-to-asymmetric-routing.html
It's a bit of an ugly solution though. It would be better to put those other VMs 'behind' pfSense such that they use the pfSense LAN as their gateway. That avoids the problem.
Steve