Disable Snort rule
-
@moelharrak said in Disable Snort rule:
Hi all ,
I have Pfsense 2.4.4 ,recently I installed snort ,it start generating alerts , I disabled many rules to make it works fine.
I have an issue with my IPTV , snort blocked it. I tried to find which rule cause this issue but can't find it.
Even I have disabled the rule from the alert but still can't work.
any idea how to find a rule and disabled ?13:40:56 3 TCP Unknown Traffic x.x.x.x 37284 x.x.x.x 80 120:8 (http_inspect) INVALID CONTENT-LENGTH OR CHUNK SIZE
Your post is a little confusing. You say you can't find the rule that blocked, but then at the end you say you found the rule in an alert and disabled the rule. I'm guessing the rule you listed in your post is the issue if it contains the IP address of your IPTV. Did you go to the BLOCKED tab and remove the IP of your IPTV device? Once it blocks, you will need to manually remove the block.
To make block removal automatic after a period of time, go to the GLOBAL SETTINGS tab and set the "Remove Blocked Hosts Interval" value to something like 30 minutes or 1 hour. That is what I recommend users do. That way you get the block on potential nefarious activity, but then the block clears after a period of time so any internal host can function again.
You might also want to browse through this archived thread about creating a Master Suppress List that takes care of a number of the rules known to false positive in many home environments: https://forum.netgate.com/topic/50708/suricata-snort-master-sid-disablesid-conf.
-
Hi all,
I need to find the rule that cause issue and remove it for all.
what I share with you is an alert picked from the snort log.
I know that I need to remove the IP from the blocked hosts but this is not the solution , I can't each time the IP blocked go and remove it.I need to find the rule and disabled -
@moelharrak said in Disable Snort rule:
Hi all,
I need to find the rule that cause issue and remove it for all.
what I share with you is an alert picked from the snort log.
I know that I need to remove the IP from the blocked hosts but this is not the solution , I can't each time the IP blocked go and remove it.I need to find the rule and disabledIt is very simple to find the alerting rule that is causing the problem. Look for the IP address of your IPTV device in the alerts. If you don't see the IP of your IPTV, then Snort is not what is causing your problem. If your IPTV has IP address 1.2.3.4, then look through the ALERTS tab on Snort and find any and all rules where the SRC or DST IP is 1.2.3.4; that's likely your problem rule.
-
I do have a generated alert :
13:40:56 3 TCP Unknown Traffic x.x.x.x 37284 x.x.x.x 80 120:8 (http_inspect) INVALID CONTENT-LENGTH OR CHUNK SIZE
My question now is how to find the rule that generate this alert and disabled completly -
@moelharrak said in Disable Snort rule:
I do have a generated alert :
13:40:56 3 TCP Unknown Traffic x.x.x.x 37284 x.x.x.x 80 120:8 (http_inspect) INVALID CONTENT-LENGTH OR CHUNK SIZE
My question now is how to find the rule that generate this alert and disabled completlyHover your mouse over the red X under the SID column and you will have your answer ...

You can also tell from reading the text of the rule message. This rule is from the HTTP_INSPECT preprocessor. The GID is 120 for that preprocessor. The specific rule you listed is SID 8 (that's what the 120:8 represents in the rule). HTTP_INSPECT rules are part of the built-in Snort preprocessor rules. You can view those by going to the RULES tab and choosing Preprocessor Rules in the drop-down selector.
-
I've already done it ,it worked for other rules but not this one.even I see now that it's on yellow (mean rule disabled) but snort still block the server.
That why I asked where can I find this rule and disabled it completely.I looked for it using GID:SID (120:8) but can't find it. -
@moelharrak said in Disable Snort rule:
I've already done it ,it worked for other rules but not this one.even I see now that it's on yellow (mean rule disabled) but snort still block the server.
That why I asked where can I find this rule and disabled it completely.I looked for it using GID:SID (120:8) but can't find it.The only other issue you may have is dual instances of Snort running on the same interface. If that happens, one becomes a zombie sort of and ignores configuration changes. If other rule disables are working, though, then I would not think a zombie instance is your problem. Easy to fix that, though. Simply reboot pfSense. That will clear any zombie process.
There may be more than one rule blocking your server. Also, are you running any other packages such as pfBlockerNG? That package can block a lot of stuff as well and cause issues with streaming.
-
Use the Filter function on the ALERTS tab to find all alerts with your IPTV device IP address in them.
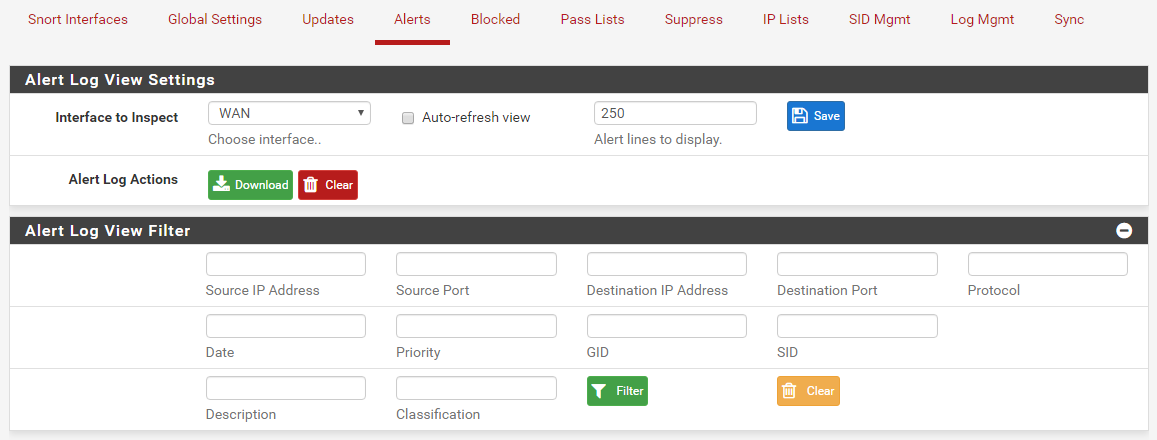
Put the IPTV address in one of the IP address boxes and filter your alerts on that IP to bring up all alerts that fired with that host. Any already disabled rules will have the yellow X under the SID column. Currently active rules will have a red X.
-
Nope I have no pfBlockerNG enabled.only pfsense enabled on WAN interface.
I didn't find Preprocessor Rules.
meanwhile I will reboot my pfsense and see the result -
@moelharrak said in Disable Snort rule:
Nope I have no pfBlockerNG enabled.only pfsense enabled on WAN interface.
I didn't find Preprocessor Rules.
meanwhile I will reboot my pfsense and see the resultIf you go to the RULES tab for your WAN interface, then you should be able to click the drop-down selector and choose the Preprocessor Rules from the list as shown below:
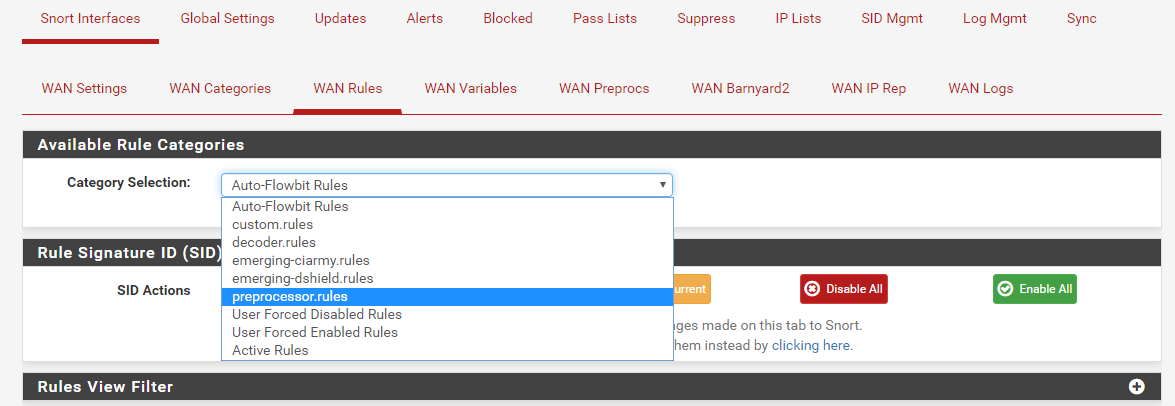
What version of the Snort package are you running? Is it 3.2.9.8_5?
-
I think the reboot solved the issue, still working for now.
will monitor it and return if there is something new.
Thank you for your help :)