Big DNS Problems *Illustrated*
-
@skalyx said in Big DNS Problems *Illustrated*:
Then, same problem after 10minutes. I really do not understand...
And in the log for unbound - did it restart, did unbound stop?
resolving should work out of the box!!!
Your on a 4G connection... Does your ISP only allow access to its own DNS? And shitty ass connections to anything else?
Make sure you turn OFF and to be honest just remove pfblocker for any sort of testing.
Working sometimes and not working others points to unbound restarting if you ask me.. Simple enough to see in the log..
-
@johnpoz
Yes, my ISP allows other DNS from what they told me.I just added to my post:
EDIT: I already have the following activated:
Prefetch DNS Key Support: DNSKEYs are fetched earlier in the validation process when a Delegation signer is encountered
Serve Expired: Serve cache records even with TTL of 0
I just, however, activated "Prefetch Support: Message cache elements are prefetched before they expire to help keep the cache up to date" and deactivated "Harden DNSSEC Data: DNSSEC data is required for trust-anchored zones" as DNSSEC Support must be activated for this.I will look in the logs whenever I get this issue again.
Thanks for the help! -
Did you also disable DNS over TLS? As far as I know that does nothing without forwarding enabled but it should be disabled for resolving anyway.
Steve
-
If unbound is actually running... Can you resolve say pfsense own name? When you do a nslookup on your machine does it come back with a name for the IP?
example
$ nslookup Default Server: sg4860.local.lan Address: 192.168.9.253If not then unbound is not running... Or you client its having an issue talking to pfsense for dns in the first place... Which also could be your problem.
-
@stephenw10
My current configuration is:-
No DNSSEC Support
-
Forwarding mode activated
-
Use SSL/TLS for outgoing DNS Queries to Forwarding Servers (DNS over TLS activated)
if I deactivate forwarding mode, nothing works. Maybe I should turn of DNS TLS when I deactivate forwarding mode?
-
-
Yeah you should turn off tls if resolving - since that option is not viable if resolving.
-
@johnpoz
I get the hostname and address with nslookup so my unbound is working, isn't it?I just activate DNSSEC Support, deactivated forwarding mode and DNS over TLS. Let us see how it goes!
-
This post is deleted! -
I just activate DNSSEC Support, deactivated forwarding mode and DNS over TLS.
It now works after having disable Harden DNSSEC Data: DNSSEC data is required for trust-anchored zones.
However, the problem still persists. I noticed in my log that :
May 27 19:25:38 unbound 84243:0 notice: Restart of unbound 1.9.1.Moreover, DNS resolving queries are slow. Much slower than usual. Please let me know if you have any idea.
Thanks,
-
And how often are you seeing unbound restart?
Resolving can be slower to start.. Sure it might be a few ms longer talking the authoritative ns vs just asking a forwarder what what it has cached.. But once is cached then its no different, and once you resolve to where the authoritative ns is for domainx, then you don't have to walk down the tree from roots again until the whole tree ttl expires.
Not sure how anyone could care about a few ms, when they are wanting to FORWARD over tls ;)
If unbound is restarting all the time your going to loose the advantage in caching be it you forward or resolve.
-
Haha yes I know, but it is abnormally slow.
Just found the cause. It restarts about every minute. Here is a sample of log:
May 27 21:25:24 unbound 84243:0 notice: Restart of unbound 1.9.1.
May 27 21:26:33 unbound 84243:0 notice: Restart of unbound 1.9.1.
May 27 21:27:17 unbound 84243:0 notice: Restart of unbound 1.9.1.
May 27 21:27:48 unbound 84243:0 notice: Restart of unbound 1.9.1.
May 27 21:28:18 unbound 84243:0 notice: Restart of unbound 1.9.1.
May 27 21:30:28 unbound 84243:0 notice: Restart of unbound 1.9.1.
.... samePutting DNS resolver in forwarding fixes the issues. I need to see if it causes problem (it normally does) and check the logs...
-
restarting that often is going to be make it useless.
Do you have it set to register dhcp or vpn clients? You prob want to bump its log level up to try and figure out why its restarting like that.. Which makes it useless.. how can it resolve or even forward if its restarting every few seconds. No wonder you having pain with dns.
-
Checkout the DHCP server log.
Every time a new lease comes in, you have many devices, some with very short lease times, know that unbound is restarted.
Solution for this issue :
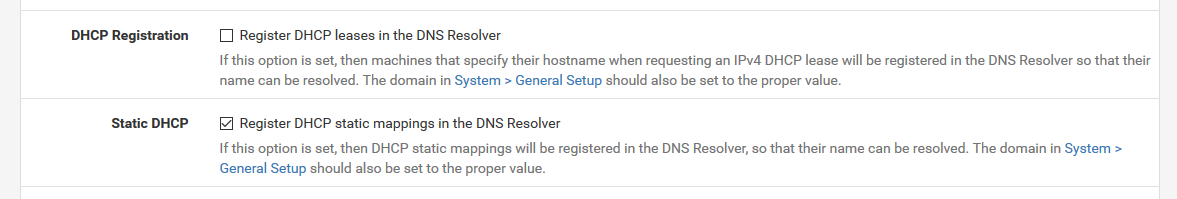
Uncheck DCHP Registration.
Where possible, leave all your devices on DHCP - but make static leases using their MAC addresses.On my pfSense installations, unbound restarts one a day, or less - other events can trigger a restart also. This means it keeps up it's DNS cache, and that's what's counts.
-
@johnpoz
Hmm. No VPN clients. Yes, I had register DHCP leases in the DNS resolver.
@Gertjan Thanks for your answer. I do not understand why it would restart nor how DHCP leases in a DNS resolver works but I just unchecked it according to your advice! I hope it will fix my issues.
I have about 80 clients at home (Google home, smartphones, etc.) where 10 of my clients such as my Synology NAS, smart switches, and access points are on static ips. Are you talking about this or about DHCP related to DNS? -
I have a question. It may sound stupid but I just am trying to understand things correctly.
So, now I have this config:-
DNSSEC Support activated
-
Forwarding mode, DNS over TLS, and Register DHCP leases in the DNS Resolver deactivated
However, will my PFSense router be able to encrypt my DNS queries with DNS over TLS with my current config? I want to limit my ISP eavesdropping on me as much as possible. Moreover, I would like to ask if my PFsense router is using DNSSEC with Cloudflare's DNS servers? I just activated DNSSEC support. If it does not use DNSSEC and DNS over TLS, what could I do?
Thanks,
-
-
I miss read that.
If your resolving then no you can not do dns over TLS.. for that to work every single NS on the planet would have to be listening and support dns over tls.
If you think your ISP is watching your traffic - for what possible reason you can only imagine... What do they get from knowing that you asked for pfsense.org ? Or p0rn.tld -- then tighten up your tinfoil hat and run everything, even your dns queries through a vpn.
Because clearly those vpn services are way more trust worthy than your ISP... I mean they state it right on their website that they don't log <rolleyes> ;)
-
@johnpoz Hahah. Yes. I saw your previous message ;p. I understood the forwarding mode does not require me to do anything.
So... The only way to get DNS over TLS for me would be to forward all my requests to DNS servers that accept it such as Cloudflare ones?
-
If you want to use dns over tls, then yes you have to "forward" to a dns provider that supports it. You can not resolve over tls.
-
@johnpoz
Hahah yes. I actually am studying security so I just want to learn. That's not my aim to be fully secured and so on. My ISP won't learn much but they can guess a lot ! It is good for me if things like DNS over TLS and so on can be activated easily. PFsense has such amazing capacities and I am still learning. :) -
Do you really think your isp is taking the trouble to snff all dns traffic that goes across their network? Compile it and parse it and put it some database to where billy went on tuesday ;)
Its one thing if you just going to hand them all your queries directly by asking their dns servers... But when you resolve you talk to roots, and specific authoritative ns all over the planet for the domains you look for.
Keep in mind that if they really wanted to spy on you, they can just look to see what is in your http headers for where your going.. And even if using https, the sni is going to contain where you were going, simple enough to look in the client hello packet and see where you were going..
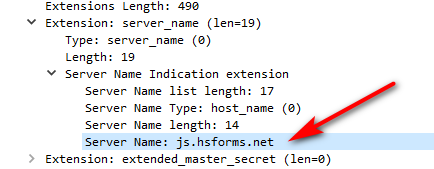
No need to sniff the dns ;)
If you think hiding your dns queries prevents your isp from knowing where your going.. No! All it does is make it a bit harder..