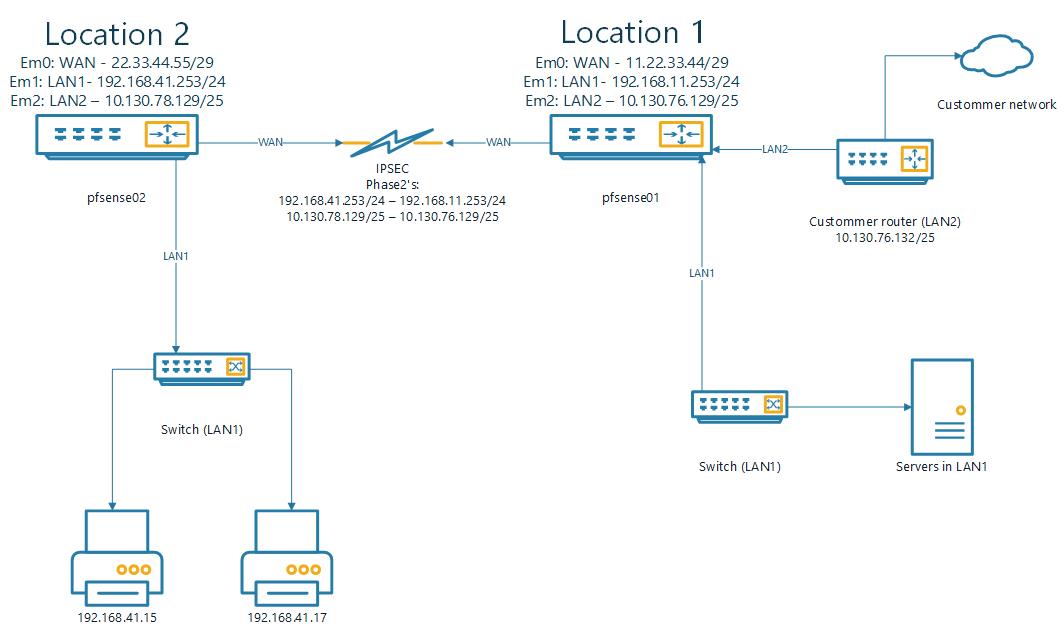
Access printer from foreign network over IPSEC (multiple locations)
-
i did create an static route on pfsense01 (location1):
(gateway: LAN2)
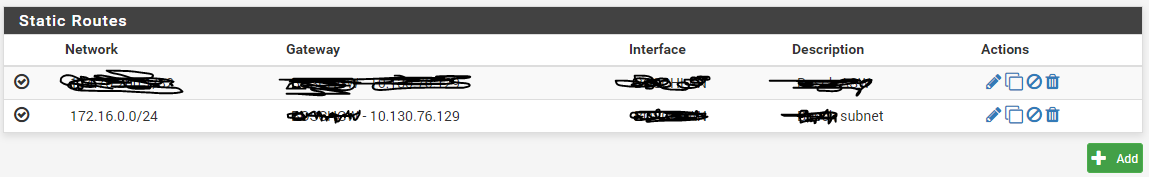
this wil route the traffic in location1 back to the costommer network. i think the problem is that Location2 is not knowing this interface.
I cannot add the route to pfsense02 (location2) because i cannot create an gateway on the ipsec interface to route the traffic to 172.16.0.0/24 back to pfsense01.
-
Your gateway is wrong though that should not be .129 but .132.
-
can you ping 10.130.76.129 from 172.16.0.0/24?
-
i run packet capturing on LAN2 (pfsense01) i see the following:
10:57:45.117448 IP 172.16.0.26 > 10.130.76.136: ICMP echo request, id 249, seq 27238, length 36
10:57:45.157610 IP 172.16.0.26 > 10.130.76.136: ICMP echo request, id 249, seq 27239, length 36
10:57:45.197928 IP 172.16.0.26 > 10.130.76.136: ICMP echo request, id 249, seq 27240, length 36
10:57:45.237965 IP 172.16.0.26 > 10.130.76.136: ICMP echo request, id 249, seq 27241, length 36
10:57:45.277946 IP 172.16.0.26 > 10.130.76.136: ICMP echo request, id 249, seq 27242, length 36no reply is comming back
-
@bashuis said in Access printer from foreign network over IPSEC (multiple locations):
I cannot add the route to pfsense02 (location2) because i cannot create an gateway on the ipsec interface to route the traffic to 172.16.0.0/24 back to pfsense01.
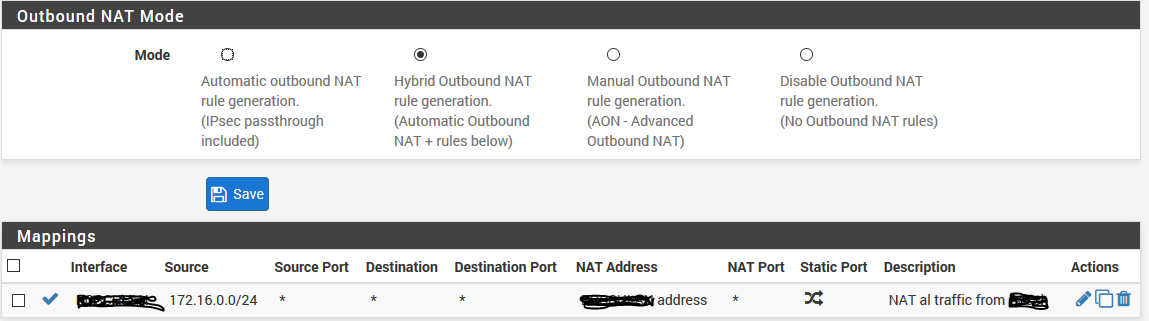
Then you simply create a outbound NAT on pfsense01 for the 172 network, but before you do that make sure that the LAN2 interface on pfsense01 can communicate with the 172 network first.
One problem at a time.
-
@bashuis
Disable the port forward for the ICMP for .136 and try again and see if it replies. -
@conor
i already have the outbound rule on pfsense01:
NAT address: 10.130.76.132/25
-
@bashuis
I have no idea if you have that set up right as you have covered up all the important bits. -
i disabled outgoing NAT + disabled icmp forwarding and still get no reply:
11:07:09.031164 IP 172.16.0.26 > 10.130.76.136: ICMP echo request, id 249, seq 40292, length 36
11:07:09.071096 IP 172.16.0.26 > 10.130.76.136: ICMP echo request, id 249, seq 40293, length 36
11:07:09.111122 IP 172.16.0.26 > 10.130.76.136: ICMP echo request, id 249, seq 40294, length 36
11:07:09.151517 IP 172.16.0.26 > 10.130.76.136: ICMP echo request, id 249, seq 40295, length 36
11:07:09.192282 IP 172.16.0.26 > 10.130.76.136: ICMP echo request, id 249, seq 40296, length 36
11:07:09.232982 IP 172.16.0.26 > 10.130.76.136: ICMP echo request, id 249, seq 40297, length 36
11:07:09.273003 IP 172.16.0.26 > 10.130.76.136: ICMP echo request, id 249, seq 40298, length 36 -
Ok then the first problem is that the .136 IP on pfsense01 can't reply to the 172 network.
- Make sure that the firewall rules permit traffic from the 172 network arriving on the LAN2 interface.
- The 172 network is being routed by the customer router what is the ip in the range 10.130.76.132 for that router. That IP will be your gateway for the 172 static route.
-
I'm able to ping from LAN2(location1) to the printer (10.130.76.136) if i use an source address in the range 10.130.76.129/25.
i think the problem is that the traffic is comming from 172.16.0.0/24 and the site: location2(pfsense02) is not knowing this subnet to route it back to location1
i added the following firewallrule on LAN2
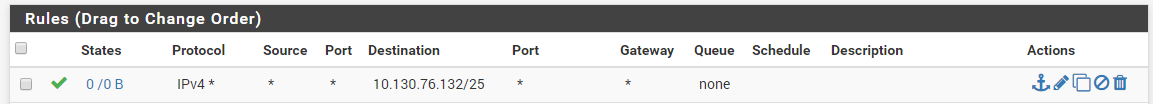
this should allow traffic from 172.16.0.0/24 to 10.130.76.136i disabled the ICMP portforwarding and disabled outgoing NAT
the address 10.130.76.136/25 is added als virtual IP, is this needed?
packet capturing on interface LAN2 (pfsense01) give no reply:
11:25:30.561151 IP 172.16.0.26 > 10.130.76.136: ICMP echo request, id 250, seq 281, length 36
11:25:30.601003 IP 172.16.0.26 > 10.130.76.136: ICMP echo request, id 250, seq 282, length 36
11:25:30.640925 IP 172.16.0.26 > 10.130.76.136: ICMP echo request, id 250, seq 283, length 36
11:25:30.680956 IP 172.16.0.26 > 10.130.76.136: ICMP echo request, id 250, seq 284, length 36
11:25:30.720877 IP 172.16.0.26 > 10.130.76.136: ICMP echo request, id 250, seq 285, length 36
11:25:30.760985 IP 172.16.0.26 > 10.130.76.136: ICMP echo request, id 250, seq 286, length 36
11:25:30.801084 IP 172.16.0.26 > 10.130.76.136: ICMP echo request, id 250, seq 287, length 36
11:25:30.841004 IP 172.16.0.26 > 10.130.76.136: ICMP echo request, id 250, seq 288, length 36 -
now i get een reply back:
11:27:44.554463 IP 172.16.0.26 > 10.130.76.136: ICMP echo request, id 250, seq 3382, length 36
11:27:44.554492 IP 10.130.76.136 > 172.16.0.26: ICMP echo reply, id 250, seq 3382, length 36so the connection from pfsense01(LAN2) to the custommer is ok.
-
You have a pile of things to fix, stop trying to guess it all in one go. First fix the fact that the pfsense01 can't communicate with the 172 network. You probably don't need the Virtual IP and could ping the LAN2 interface directly but eiteher way you first need to make sure the pfsense01 can talk with the 172, otherwise no matter what you do with the pfsense02 it won't work.
-
@bashuis said in Access printer from foreign network over IPSEC (multiple locations):
now i get een reply back:
11:27:44.554463 IP 172.16.0.26 > 10.130.76.136: ICMP echo request, id 250, seq 3382, length 36
11:27:44.554492 IP 10.130.76.136 > 172.16.0.26: ICMP echo reply, id 250, seq 3382, length 36
so the connection from pfsense01(LAN2) to the custommer is ok.Good now you need to add a P2 entry to your IPSEC on both sides for the 172 network so they know how to talk to each other good explaination here: https://docs.netgate.com/pfsense/en/latest/vpn/ipsec/ipsec-with-multiple-subnets.html
-
should that like this?
pfsense01
172.16.0.0/24(local) --> 192.168.41.0/24(remote)pfsense03
192.168.41.0/24(local) --> 172.16.0.0/24(remote) -
yes
-
@conor
OK, i created the P2.
it is not UP, but that could be because there is no traffic going over it..several other P2's over the samen P1 are online..
location 1 (pfsense01):
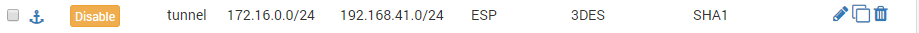
location 2 (pfsense02):

Should i disconnect and reconnect the whole IPSEC connection?
-
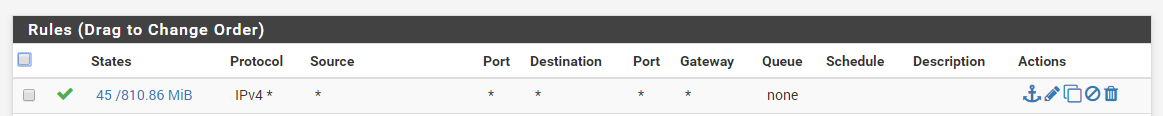
on pfsense 02 for the sake of testing goto Firewall > Rules > IPSEC
add an allow all rule for this interface, you can fine tune it later this is just for testing -
@bashuis said in Access printer from foreign network over IPSEC (multiple locations):
Should i disconnect and reconnect the whole IPSEC connection?
if the down time isn't going to bother you probably best.
-
@conor said in Access printer from foreign network over IPSEC (multiple locations):
sake of testing goto Firewall > Rules > IPSEC
add an allow all rule for this interface, you can fine tune it later this is just for testingthis rule was already active (for testing) on the IPSEC interface