Strange behavior with UDP protocol
-
You can't test UDP with
nclike that, it will always claim success.When you say the traffic doesn't arrive, did you check with a packet capture on WAN? Or on LAN? Or both?
If it doesn't arrive when you capture on WAN, then it has to be getting blocked somewhere between the client and the pfSense WAN, and there isn't anything pfSense can do about that.
If it arrives on WAN but doesn't reach the server on LAN, that would be a much different issue. We'd need to see the rules, the firewall logs, state table contents, etc.
-
I played around with this a little bit last night, and while I could see the udp packets hitting WAN, they weren't being forwarded to the internal LAN client. A packet capture on LAN showed no udp packets whatsoever regardless of which port was used.
Assuming I made a mistake somewhere, I'll try it again later when I have some time.
-
Not exactly sure how he is testing.. But sending a udp packet is not hard..
Here from one of my vps, just did a simple
root@ns1:~# echo "test" > /dev/udp/64.53.xx.xx/443
Where that 64.53 is my pfsense wan IP.. Bam it shows up
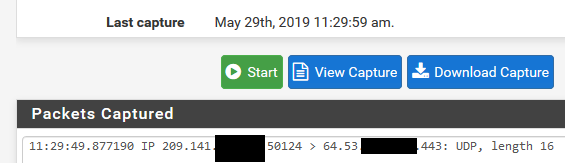
-
It hits WAN like I said, but doesn't get forwarded to LAN.
-
No problem forwarding UDP ports here.
: tcpdump -ni vmx1 port 444 tcpdump: verbose output suppressed, use -v or -vv for full protocol decode listening on vmx1, link-type EN10MB (Ethernet), capture size 262144 bytes 15:37:32.629457 IP 198.51.100.108.45514 > 10.6.0.122.444: UDP, length 1 : pfctl -ss | grep 444 vmx0 udp 10.6.0.122:444 (198.51.100.6:444) <- 198.51.100.108:45514 NO_TRAFFIC:SINGLE vmx1 udp 198.51.100.108:45514 -> 10.6.0.122:444 SINGLE:NO_TRAFFIC: grep 444 /tmp/rules.debug rdr on vmx0 proto udp from any to 198.51.100.6 port 444 -> 10.6.0.122 rdr on { vmx1 enc0 openvpn } proto udp from any to 198.51.100.6 port 444 -> 10.6.0.122 no nat on vmx1 proto udp from (vmx1) to 10.6.0.122 port 444 nat on vmx1 proto udp from 10.6.0.0/24 to 10.6.0.122 port 444 -> 10.6.0.1 port 1024:65535 no nat on vmx1 proto udp from (vmx1) to 10.6.0.122 port 444 nat on vmx1 proto udp from 10.6.0.0/24 to 10.6.0.122 port 444 -> 10.6.0.1 port 1024:65535 no nat on vmx1 proto udp from (vmx1) to 10.6.0.122 port 444 nat on vmx1 proto udp from 10.6.0.0/24 to 10.6.0.122 port 444 -> 10.6.0.1 port 1024:65535 pass in quick on $WAN reply-to ( vmx0 198.51.100.1 ) inet proto udp from any to 10.6.0.122 port 444 tracker 1559158506 keep state label "USER_RULE: NAT " -
yeah no problem here either
Here is forward and firewall rules
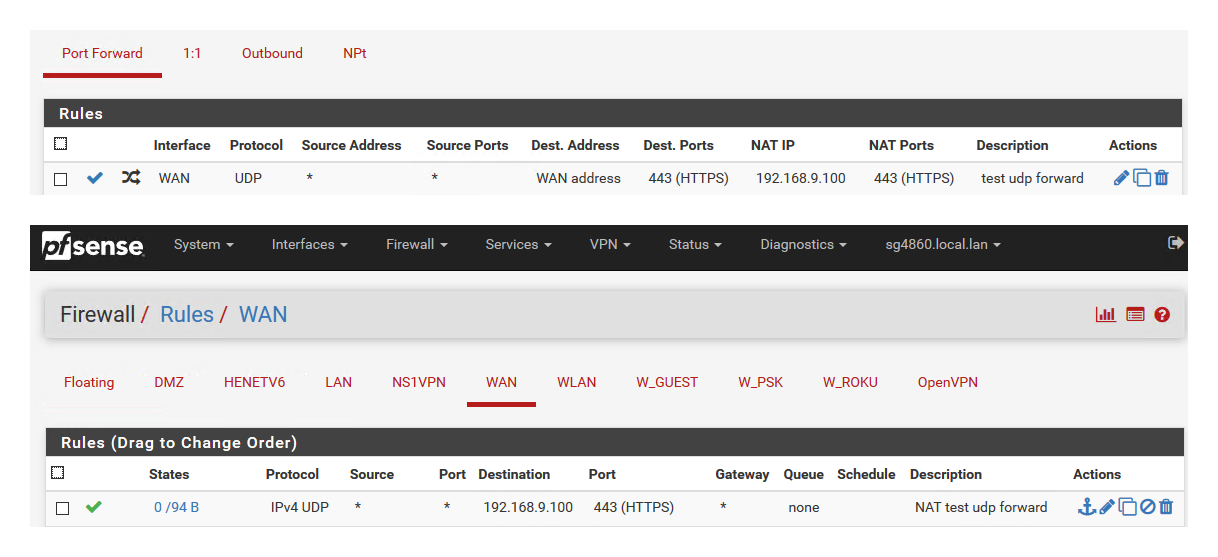
Here is sniff of it you can see it sending to 9.100
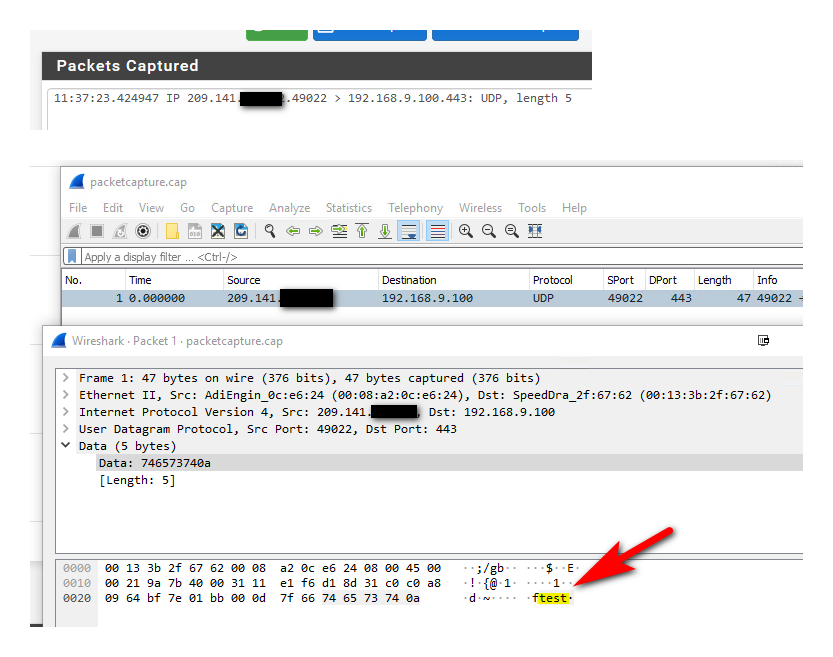
-
Good to know. I tried it several times last night with nc. I was aware that it always reports success but I was capturing packets. Everything was virtualized within Virtualbox. I was forwarding to a host that didn't exist. I expected the packets to be seen on the LAN interface. Nothing was captured. If pfSense has no entries in its ARP cache for that non-existent address, will it still try to forward? That might explain why I didn't see anything.
While it's possible I got something wrong, I tried this several times last night and could never make it work.
-
Why would a router deliver a packet to a host that doesn't exist?
If ARP fails it won't send a packet.
-
@jimp See, I'm smart enough to realize my stupidity after only 20 hours. I'm getting better all the time (bettah, bettah, BETTAH!)
-
Hi everyone
thanks for your proactivity :) in the coming days I will do other tests and I am attaching the report I get.
for now I am attaching screenshots with my WAN rules, port forwarding rules and lan rule
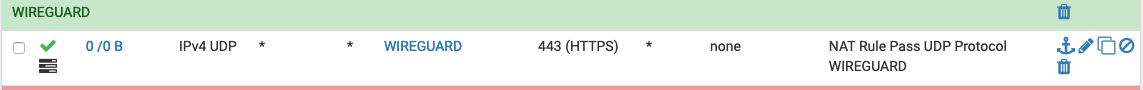
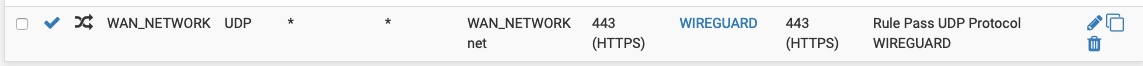

-
And what is in that alias? It must only contain one entry, an IP address. Do the contents of the table show up under Diag > Tables?
Does it work if you remove the alias and put the IP address in directly?
The rules have no matches, so there must not be any traffic arriving which matches.