Can't access XG-7100
-
Did you check and follow https://docs.netgate.com/pfsense/en/latest/book/routing/routing-public-ip-addresses.html ?
-Rico
-
@Rico Ahh no I didn't see that! I just assumed the interfaces would be configured separately, although I'm not sure it would make any difference on the WAN port - I should still be able to access that shouldn't I?
This is more complicated than I was expecting. I really appreciate you taking the time to reply. Thank you.
The big question now is...
How do I get back into the 7100 to start again? Is there a "reset to default" sequence on the hardware?
-
You can factory reset via the Serial console.
Well for the WAN port any traffic entering the interface is blocked by the default Firewall Rules.
I would leave the default LAN as your management port, then you can't lock yourself out as happened now. Create a separate OPT Interface for your internal server network.-Rico
-
@Rico Ok thanks for the advice. This may sound like a dumb question but how do I get the second network on the switch? does it all go through ETH1 with this "OPT" interface? So I only need to connect ETH1 to the switch? what about my VLANs? Do I now need to configure the switch differently?
-
The switch config is very good explained by @jimp in this hangout: https://www.netgate.com/resources/videos/configuring-netgate-appliance-integrated-switches-on-pfsense-244.html
For example, I have all 8 switch ports as complete discrete ports for my XG-7100. But you can build any switch config you want. The VLANs are only used pfSense internally in this example.-Rico
-
@Rico Sorry I was referring to my network switch. I set up two VLAN's to accommodate this config but I'm not sure if that is relevant now you have advised about the OPT interface?
-
Assuming we talk about untagged VLANs (Port based) you don't need to change anything there.
If you work with tagged VLANs on this Cisco Switch...well maybe we found your culprit.
-Rico
-
@Rico They are just normal VLAN's
Can you explain what the OPT interface is for? I'm a little puzzled how I would connect the pfsense to my network switch if I'm not using ETH2?
Currently I have ETH1 connected to the first VLAN on my switch for outside - and ETH2 connected to the second VLAN on my switch for inside. If you are saying I should not use ETH2 and configure some sort of "virtual port" OPT1" - how can I connect my servers to it?
-
It's possible to trunk all the VLANs to pfSense across one connection if you need to but that doesn't sound like what you're doing.
There looks to be some confusion here between ports and interfaces. Eth1-8 are ports on the internal switch.
By default the XG-7100 has two interfaces defined:
WAN is connected (by internal VLANs) to port Eth1.
LAN is connected to ports Eth2-8.The way you describe connecting it in your first post seems correct for those defaults. But the fact the provider is seeing ARP replies for the routed subnet implies your Cisco switch is not correctly segregating those two sets of ports. I would check that first.
Because the XG-7100 has an internal switch you could just connect everything to it directly and not use VLANs on the Cisco (or eve at all until you need more ports).
You would have to reconfigure the 7100 switch ports so that WAN was then Eth1+2 to provide connections to both uplinks and LAN was Eth3-8 for connections on the routed subnet.
Let me know if you want to go that way and I'll set something up.
Steve
-
In your Switch assignment for VLANS if you are tagging traffic always ensure that you include ports 9T and 10T (uplink ports) in the port member list otherwise nothing will get through. I had this problem and although Jim Pingle's presentation is clear, this part is not...well it wasn't to me anyways. The XG7100 is different from other appliances because of the built-in switching which is complicated to understand at first.
-
@stephenw10 Thank you for your reply Stephen, I really appreciate it.
I have more than 40 servers to connect, so I need the cisco switch.
It's really hard work standing in the hot aisle trying to configure these on the fly, so I will bring back both the switch and the pfsense to the office and try again. I was sure I had set up the VLAN's correctly.
@claferriere Thanks for responding too. I don't believe I'm using VLAN tagging on the Cisco switch - I haven't set anything up to do that.
I believe the networks guy at the DC recommended I use VLANs in order to prevent running the pfsense in "transparent" mode - so while I'm dealing with two public networks, one is inside and one is outside as far as the firewall is concerned. If this isn't the best way to achieve it, I'm very open to suggestions, especially a configuration that is more simple. I can reset both these devices to factory defaults and start again. (not sure how to do that on the pfsense).
I can ask them to change the network to a single uplink for just the /25 I need (which is what I'm accustomed to).
-
@Chris-187 Not sure I understand the intricacies of your network design, I was just mentioning that on the XG7100 the Switch tab in the interface assignment is new and you need to pay attention to how the VLANs are assigned and how you identify members of that assignment. For me it was simply a question of adding ports 9 and 10 as they are part of the connection to the Denverton Soc. (From the manual: https://docs.netgate.com/pfsense/en/latest/solutions/xg-7100-1u/switch-overview.html) Without these members added to the switch config I could NOT access the internet.
-
@claferriere Ok thanks. The VLANs I created are on a separate switch, not the 7100 itself but I appreciate you taking the time to respond and for the info concerning the 7100 integrated switch.
-
Two uplinks for failover is a good idea, especially if they're not charging you for it.
It's the routed subnet that allows you to avoid transparent mode and that is also a very good idea.
You are going into the Cisco switch and back out into the XG-7100 switch unnecessarily though. Most firewalls do not have a built in switch so you would need to which is why you were instructed to do so but here you can just re-assign one of the Eth ports to WAN and connect both uplinks to it. Then use any of the other ports to connect to the Cisco switch which no longer needs to have any VLAN config on it.
Steve
-
To do that, change the PVID of port Eth2 to 4090 (the WAN internal VLAN) on the ports tab:
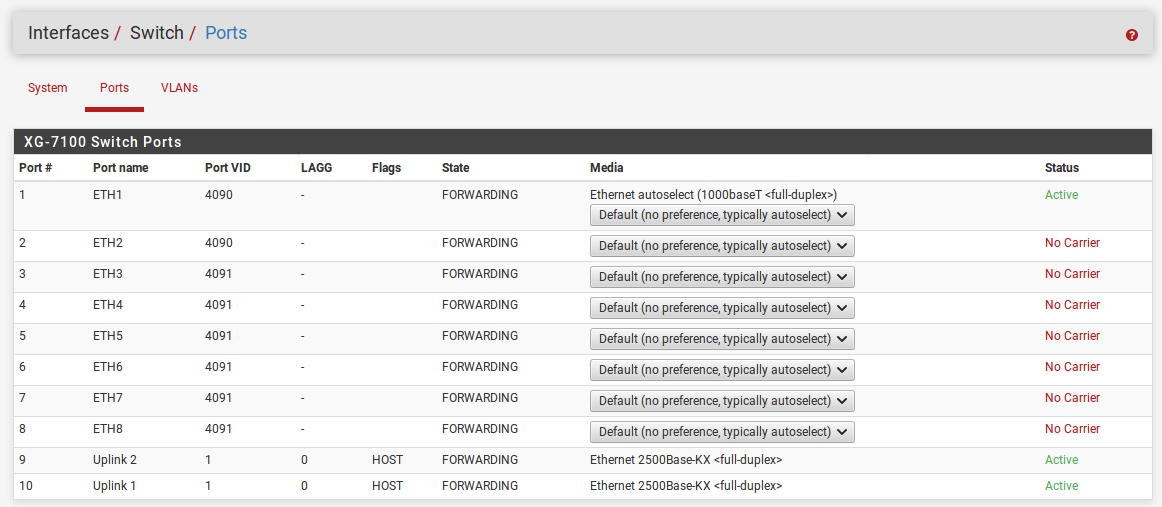
Then on the VLANs tab remove port 2 from LAN vlan group and add it to the WAN:
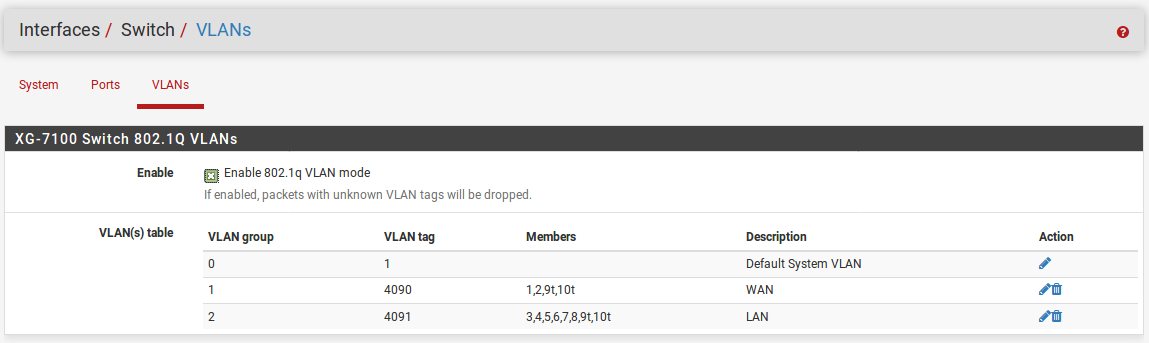
Now you can connect the two uplinks to Eth1 and Eth2 and everything else to the remaining ports.
Steve
-
@stephenw10 Thanks that's really helpful. My current predicament is that I can't connect to the 7100 at all. I need to be able to either connect to the web interface or reset it somehow. I think I can achieve this simply by connecting the uplink directly to the wan port ETH1, then it should spring into action hopefully.
-
By default there are no firewall rules to allow access on the WAN, you can only access it by connecting from the LAN side.
If you are unable to connect from either you can always connect to the serial console and add rules to allow you to connect to the GUI or reset the config and start over.
https://docs.netgate.com/pfsense/en/latest/solutions/xg-7100-1u/connect-to-console.htmlSteve
-
@stephenw10 I've connected one of the uplinks to ETH1 and my laptop to ETH2 by putting it on the same subnet. I can now access the pfsense GUI.
I've set up the WAN interface exactly as described. x.x.83.20/29 with gw x.x.83.17
I've set up the LAN interface to x.x.86.1/25 with a gateway of x.x.86.0I still can't access x.x.86.1 from outside.
-
I wonder if I can start this thread again....
I have an XG-7100 rack mount. It is now in my office to be pre-configured to be fitted in a data center.
My requirements are that I need to use the device to protect a bunch of servers that are on public IP's
I have two 1GB uplinks and my WAN is as follows...
x.x.83.20/29 with a gw x.x.83.17
I set up the WAN interface to a single uplink on ETH1as above for testing
My servers will need to be on the following network
x.x.86.1/25 with a gw of x.x.86.0 which has been statically routed to x.x.83.20
I set up the LAN interface as above on ETH2 but have been unable see the servers that are connected via a layer 2 switch to ETH2 and I can't connect to x.x.86.1 for the pfsense gui.
I couldn't get this to work after two attempts, so I have now removed the device from the data centre and brought it back to the office.
Any help greatly appreciated.
-
I still can't access x.x.86.1 from outside.
Have you added rules to allow that?
By default all inbound connections on WAN are blocked. Check the firewall logs Status > System Logs > Firewall
You have a laptop connected to Eth2. I assume that is still in the LAN at this point? You have not moved it to be the other WAN uplink yet?
Steve