Can't access XG-7100
-
Thanks, I'm a bit confused. For clarity, there is no actual LAN here - so unless I connect directly to the XG-7100 I have no access to this device.
Do I need to set up individual rules for individual ports on the WAN interface for access to the LAN interface?
I assume I've not been able to connect to the "LAN" IP's from outside, simply because there are no rules set up to allow that via the WAN firewall rules.
The point of this is to protect the so called "LAN" IP's and all traffic inwards has to come through the WAN first, so if for example, I want to connect to a server in the LAN network on port 53, Do I have to set the rule both on the WAN interface AND on the LAN interface? Or just on the WAN, with destination of "Lan Address".
This interface is not what I'm used to. In other software it's possible to provide a comma separated list of ingress and egress ports, rather than setting a rule for each one. Is that possible here?
-
WAN and LAN are just the default names there, you could use External and Internal equally. Because the subnet you are using is public that make less sense but it's just two interfaces.
You can just add an allow all rule and you could access everything but that's probably not what you want.

You can use Aliases in the firewall rules to simplify them. The Aliases can be lists of ports or IPs so you can have a rule that says 'pass traffic for destination "Server_Group1" to ports "Allowed_Ports3"` for example.
Those are configured in Firewall > Aliases.
https://docs.netgate.com/pfsense/en/latest/book/firewall/aliases.htmlYou will probably want to disable outbound NAT in this configuration (in Firewall > NAT > Outbound) so that servers behind the firewall use their own IP for outbound traffic.
Steve
-
Still no joy with this at all.
I've disabled packet filtering altogether and I still can't connect to anything from outside. Doesn't make any sense.
-
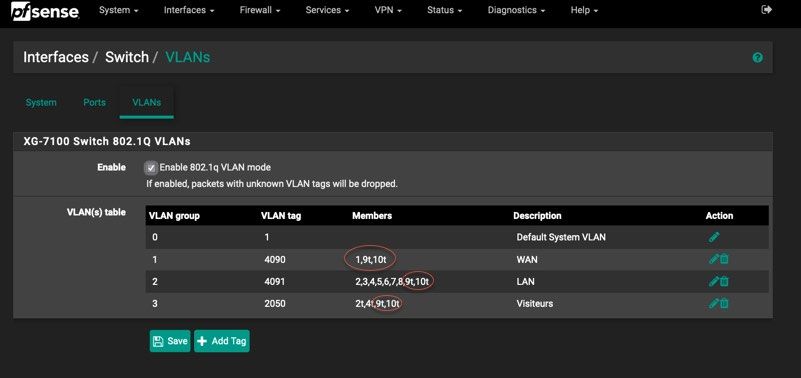
@Chris-187 I think you may need to look at your interface assignments, specifically the VLAN and Switch settings. I had similar problems and when creating VLANS, you MUST ensure that you include members 9T and 10T. These are the Denverton Soc. Check the manual as the Switching implemented on this unit has a Switch LAGG where ix2 and ix3 (switch uplink ports 9 and 10), are configured as a load-balanced LAGG. This provides an aggregate uplinkcapable of 5Gbps for ethernet switchports ETH1-8. So you cannot disregard them as members of your VLAN configuration.
Under the Switch tab for VLANs in the Interface assignments, you must list the members of a VLAN. IF you omit to include 9T and 10T, it will NOT pass anything through.
Manual Page 6 and 7:
https://docs.netgate.com/manuals/pfsense/en/latest/xg-7100-1u-security-gateway-manual.pdf
Check out an image of what I had to do (for a simpler setup) You see 9t and 10T in ALL assignments. If you miss this, it will NOT work...
-
@claferriere That's definitely not the problem. The VLAn's are set up exactly as @stephenw10 showed in his screenshots. All I did was remove eth2 from the LAN and add it to the WAN when setting it up for both uplinks.
I don't believe I have any settings wrong. I have configured the interfaces correctly and I've disabled the firewall but I can't access the LAN IP from outside. I wonder if the static routing hasn't been configured by the network team here. How can I test that?
-
Now that I've disabled the firewall shouldn't I at least be able to ping the WAN IP assigned to the pfsense?
-
Yes you should. Can you ping out from pfSense?
You can try running a packet capture on the WAN in pfSense whilst you ping it. You should see those pings arriving even if pfSense is unable to respond.
You might see ARP requests from the ISP if pfSense cannot respond to ARP.Try running a traceroute to the LAN side subnet from somewhere external. You should see that go through your WAN subnet.
Steve
-
@stephenw10 I've had to leave it installed at the data centre this afternoon so I can't do anything directly on the pfsense now. Would be good to know what questions to ask the networks guy.
I don't get a response from ping on the main IP or the LAN IP and tracert starts timing out after about 9 hops.
If I tracert to the uplink gateway IP, it gets there in 5 hops If I try the main IP of the pfsense, there are a further 4 hops before it starts timing out. Should I expect to see the gateway IP in one of the hops, or doesn't it work like that?
-
Yeah I would certainly expect the next hop after the gateway to be the pfSense WAN IP.
That requires the gateway to be able to contact the WAN IP though. Did the gateway status show as up in pfSense? That would indicate it can ping the gateway.
What actually is the next hop? There could be some loop, you sometimes see that if something redirects.
Steve
-
Sorry - what I'm saying is that I can't see the 83.17 gateway in the tracert. Should I see that?
-
Ah, OK then that does seem like a routing problem. I'd expect to see that there even if pfSense is not connected to it.
Steve
-
Yes, the gateway showed as up. It was also able to check for updates and showed it was the latest version - but then when I tried to resolve anything from the pfsense it couldn't .
-
Simple test. On Monday I'll take my laptop to the DC, plug one of the uplinks into my layer 2 switch and configure the laptop to 83.20/29 with a gw of 83.17 and run some tests. That will at least eliminate the XG-7100 as the possible cause.
-
Hmm, OK if it could check for updates then traffic was being routed back to it so the route must be present.
With pf disabled you should be able to reach it on the WAN IP externally unless something else upstream is blocking that.
Steve
-
@stephenw10 I got a reply from the networks guy. He said this...
You won't see that IP in an inbound traceroute, as routers reply to traceroutes from the IP Address the packet entered on, which in this case will be our core-facing interface.
The uplinks you have from us are directly connected to our routers, there is no switching of any kind at our side, so for any kind of next-hop-redundancy (HSRP, VRRP, CARP) there needs to be some form of working L2 path between all devices involved.
The important thing from our point of view is that the 2 uplinks that are provided to you must be connected to a common L2 Domain. (usually achieved with a switch but if the pfsense can do this then that's fine).
Right now, I'm not getting a clean L2 path between the 2 uplinks. I should be able to send a ping from 1 of the routers and it reach the other router, via those uplinks.
........................................
I have two comments on that. Firstly, it shouldn't matter if there is some issue with a "common L2 domain" - as long as the main WAN interface is configured correctly, even with just one uplink I should get a response from the XG7100 with packet filtering disabled. So while the redundancy might not be working - at least one of the uplinks should work.
My Second comment is more of a question. Is there anything special I need to do to make sure both uplinks are working in the pfsense? I've configured the ports exactly as advised - using a vlan on the pfsense to share the WAN port between the two uplinks. I changed the pvid and the vlan ports according to your screenshots and I'm confident that is correct.
My next move is to visit the DC tomorrow and test the uplinks independently to make sure everything is OK - then I will reset the XG7100 to factory defaults, configure the WAN port with just one uplink and then disable filtering. If I can't then ping the XG7100, would you say it is a faulty appliance?
-
Mmm, I would certainly expect it to work with just one link, otherwise there no redundancy. However there are somethings that will only initially establish with everything linked. I'm not aware of this being one but...
With the two ports, Eth1 and Eth2 in the WAN group as I showed the two uplinks connected to them will be in the same layer 2, yes.
If you still see nothing I would run a packet capture on WAN and see what you do see. At the very least I expect to see ARP requests from whatever is upstream.
Steve
-
@stephenw10 It does seem that these are not independent uplinks. It looks like that traffic is going out through one and in through the other. If I connect both uplinks to my layer 2 switch I get full connectivity. If I use one uplink I get nothing but timeouts.
I'm sure I configured the pfsense exactly as you mentioned. Perhaps the way these uplinks are set up is not compatible with the way the pfsense built in switch works?
I will reset it to defaults and set up the WAN again exactly as you advised.
-
@Chris-187 said in Can't access XG-7100:
It looks like that traffic is going out through one and in through the other.
Hmm, that seems suspect to say the least!
The switch in the 7100 is a switch like any other. It should provide layer 2 connectivity between those ports.
The only thing that might be an issue is that it won't pass VLAN tagged traffic unless it's configured to do so. That would also be true of any managed switch though.Steve
-
@stephenw10 What I've learned today is that if I use a single uplink connected to a simple switch, or direct to my laptop - I get no connectivity. If I connect both uplinks to my switch I get full connectivity. If I connect one or both uplinks to the pfsense, I get nothing.
-
I've lost my patience with this and I've asked them to just provide me with a single IP feed on my /25. Can someone possibly point me to a guide / details about using the XG7100 in transparent mode?