(SOLVED) Problem with client connect through static IP cable internet
-
@KOM said in (SOLVED) Problem with client connect through static IP cable internet:
Wait, you have Snort installed?? I assumed that you were using a default config to get it going without installing any extra packages. If that is the case, please disable ALL packages that may interfere with traffic, such as Snort, Suricata, pfBlocker, squidguard.
I have nothing installed which is not in a fresh install. I added "OpenVPN Client Export" as a plugin just now - but apart from that I enabled/installed no package.
-
Oh OK. I saw references in the rules to snort2c sets and I jumped to conclusions. Those types of packages are notorious for causing LAN traffic problems when not configured properly. I'm not sure what else to add. It just works out of the box for literally thousands of people. Have you gone through the Connectivity guide I linked to step by step?
Also, my suggestion for packet capture is still valid.
-
@chpalmer said in (SOLVED) Problem with client connect through static IP cable internet:
@paprikawuerzung said in (SOLVED) Problem with client connect through static IP cable internet:
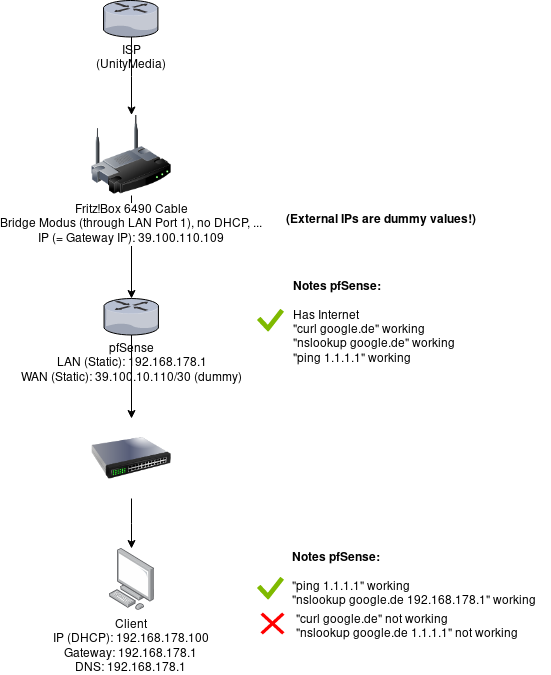
Fritz!Box 6490
Your modem is a Puma 6 powered model and AFAIC a piece of crap. But my guess is that you are stuck with it. (badmodems.com)
That model is a gateway model and is still routing as opposed to true bridge mode.
How many static addresses did they give you? The /30 surprises me a little.
Hi @chpalmer: I have 1 static IP assigned by the ISP. The other IPs in the subnet are the network IP, broadcast and gateway (4 hosts per /30 subnet) as far as I know.
-
@KOM said in (SOLVED) Problem with client connect through static IP cable internet:
Oh OK. I saw references in the rules to snort2c sets and I jumped to conclusions. Those types of packages are notorious for causing LAN traffic problems when not configured properly. I'm not sure what else to add. It just works out of the box for literally thousands of people. Have you gone through the Connectivity guide I linked to step by step?
I have gone through the connectivity guide before, yes. The answers to all the questions in the troubleshooting guide are scattered through this thread.
Also, my suggestion for packet capture is still valid.
I am not exactly positive that this will add more to our understanding. The WAN firewall rule allowing traffic from the WAN to the LAN network "fixes" the problem.
I guess my only question is: does this pose a security threat and how can I test it? If it does not create any further problems and does not compromise the security - I am really not that keen on investigating the problem further. Maybe it got anything to do with the ISP or a quirk of the modem or... or... or... -
Yes, having a rule on WAN that allows all traffic to LAN is certainly not best practice. It allows access to WebGUI from WAN, for one thing. A packet capture would tell you if LAN is even seeing the traffic, and the WAN capture would show if it's leaving for the Internet.
-
@KOM said in (SOLVED) Problem with client connect through static IP cable internet:
Yes, having a rule on WAN that allows all traffic to LAN is certainly not best practice. It allows access to WebGUI from WAN, for one thing. A packet capture would tell you if LAN is even seeing the traffic, and the WAN capture would show if it's leaving for the Internet.
This is not a problem since pfSense is behind the gateway which in turn does not expose pfSense (and therefor the WebGUI is not seen) to the outside. I already did a full port scan with
nmapon both the gateway and the pfSense IPs - no ports open (of course there are hidden ports - but no response from them).I assume that especially since the Fritz!Box 6490 Cable does not simply do bridging but instead also some routing/firewalling by itself, this setup is not more insecure than a normal Fritz!Box setup. But of course I am not entirely sure about that.
I will try a packet capture tomorrow - but I strongly suspect that the packet leaves pfSense but the firewall blocks the response. Why it only does this when using TCP/UDP (layer-4) traffic and not ping is beyond my knowledge.
I will provide the results tomorrow. -
@paprikawuerzung said in (SOLVED) Problem with client connect through static IP cable internet:
this setup is not more insecure than a normal Fritz!Box setup. But of course I am not entirely sure about that.
It is. You are passing all - ALL - TCP traffic from internet to your inside LAN without filtering. You could simply add any instead of TCP or remove pfsense alltogether as your solution is opening the firewall completely so you have no filtering at all. The whole (one of the) reason of a firewall is filtering what should and should not enter/leave your network. You are frustrated that it isn't working like it should in your mind. I can understand that. But your solution is no solution at all but to simply remove the firewall. Also being angry at us pointing out that in exactly default case it isn't necessary and should never be the solution to even add such a rule is understandable but not helpful to your case. If you had such a rule on DSL setup is even more astonishing as it's not necessary at all to even let something in on WAN if you have no services to reach via WAN (host your own website, NAS etc.). So besides ICMP which is arguable anything else on WAN should be default and block only.
I'd take a hard look at tcpdump, the state table and outbound NAT to check how and what arrives on the outside of the internet. E.g.
- do a
curl ifconfig.me/ipon pfSense diagonstics/run command - activate your "solution" rule and do the same from a PC - you read the same IP?
- if so, what's the IP on the WAN interface of pfSense (status/interfaces -> check WAN)
- if your client PC works with that strange rule, surf to a specific site where you know its IP and then check Diagnostic/States and filter for the client PC's IP - there should be two states for the website your called, one on LAN, one on WAN with the outbound NATted IP in brackes (). Check that if that makes sense. If it has none pfSense is not NATting properly. Check again without your rule and after flushing states or giving the ruleset time to reload and the state to expire otherwise you could have the effect that it works without the rule because the state is still active.
- also uncheck block bogons/private networks on WAN and check again if anything works without that pass any rule on WAN. Quite a few cable providers are using formerly unassigned IP space now and if pfSense hasn't refreshed the bogus list, it could be blocked because of that!
It'd be possible that the strange setup with your cable box actually let's pfSense think it has another IP as it really has and for that matter NAT's to the wrong IP. Something like that. But hear us when we are trying to tell you: in no proper setup is there a need for a WAN to LAN pass any rule to exist. There definetly is something bogus going on.
This is not a problem since pfSense is behind the gateway which in turn does not expose pfSense (and therefor the WebGUI is not seen) to the outside. I already did a full port scan with nmap on both the gateway and the pfSense IPs - no ports open (of course there are hidden ports - but no response from them).
I assume that especially since the Fritz!Box 6490 Cable does not simply do bridging but instead also some routing/firewalling by itself, this setup is not more insecure than a normal Fritz!Box setup. But of course I am not entirely sure about that.And after the next provider driven update of your Fritz!Box, something changes, the bridging suddenly works and you are exposed to the internet. Want to bet on that? I wouldn't. Also that happened in southern Germany. Recent updates of cable provider's FBs suddenly activated the long lost bridging feature of the consumer boxes that hadn't worked before. Even if the ISP itself states, switching to bridging won't work as they have to do some internal magic, too, I wouldn't bet at that. A simple error in ISPs configuration could expose your whole network as in your setup the box shouldn't do routing at all but simply passing the IP to pfSense's WAN interface. That's a risk I wouldn't take.
- do a
-
@JeGr said in (SOLVED) Problem with client connect through static IP cable internet:
@paprikawuerzung said in (SOLVED) Problem with client connect through static IP cable internet:
this setup is not more insecure than a normal Fritz!Box setup. But of course I am not entirely sure about that.
It is. You are passing all - ALL - TCP traffic from internet to your inside LAN without filtering. You could simply add any instead of TCP or remove pfsense alltogether as your solution is opening the firewall completely so you have no filtering at all. The whole (one of the) reason of a firewall is filtering what should and should not enter/leave your network. You are frustrated that it isn't working like it should in your mind. I can understand that. But your solution is no solution at all but to simply remove the firewall. Also being angry at us pointing out that in exactly default case it isn't necessary and should never be the solution to even add such a rule is understandable but not helpful to your case. If you had such a rule on DSL setup is even more astonishing as it's not necessary at all to even let something in on WAN if you have no services to reach via WAN (host your own website, NAS etc.). So besides ICMP which is arguable anything else on WAN should be default and block only.
I'd take a hard look at tcpdump, the state table and outbound NAT to check how and what arrives on the outside of the internet. E.g.
- do a
curl ifconfig.me/ipon pfSense diagonstics/run command - activate your "solution" rule and do the same from a PC - you read the same IP?
- if so, what's the IP on the WAN interface of pfSense (status/interfaces -> check WAN)
- if your client PC works with that strange rule, surf to a specific site where you know its IP and then check Diagnostic/States and filter for the client PC's IP - there should be two states for the website your called, one on LAN, one on WAN with the outbound NATted IP in brackes (). Check that if that makes sense. If it has none pfSense is not NATting properly. Check again without your rule and after flushing states or giving the ruleset time to reload and the state to expire otherwise you could have the effect that it works without the rule because the state is still active.
- also uncheck block bogons/private networks on WAN and check again if anything works without that pass any rule on WAN. Quite a few cable providers are using formerly unassigned IP space now and if pfSense hasn't refreshed the bogus list, it could be blocked because of that!
It'd be possible that the strange setup with your cable box actually let's pfSense think it has another IP as it really has and for that matter NAT's to the wrong IP. Something like that. But hear us when we are trying to tell you: in no proper setup is there a need for a WAN to LAN pass any rule to exist. There definetly is something bogus going on.
This is not a problem since pfSense is behind the gateway which in turn does not expose pfSense (and therefor the WebGUI is not seen) to the outside. I already did a full port scan with nmap on both the gateway and the pfSense IPs - no ports open (of course there are hidden ports - but no response from them).
I assume that especially since the Fritz!Box 6490 Cable does not simply do bridging but instead also some routing/firewalling by itself, this setup is not more insecure than a normal Fritz!Box setup. But of course I am not entirely sure about that.And after the next provider driven update of your Fritz!Box, something changes, the bridging suddenly works and you are exposed to the internet. Want to bet on that? I wouldn't. Also that happened in southern Germany. Recent updates of cable provider's FBs suddenly activated the long lost bridging feature of the consumer boxes that hadn't worked before. Even if the ISP itself states, switching to bridging won't work as they have to do some internal magic, too, I wouldn't bet at that. A simple error in ISPs configuration could expose your whole network as in your setup the box shouldn't do routing at all but simply passing the IP to pfSense's WAN interface. That's a risk I wouldn't take.
Ok, thanks a lot for your thorough explanation and sorry for the frustration I showed - I am very grateful for all your input/help!
I will have to debug it more throughly and will post the results of it as soon as I do it. That said: I called UnityMedia because we do not just have this firewall problem but the Fritz!Box 6490 Cable itself seems to have problems with the speeds and a little load. It switches from 100Mbit on the LAN port (it should be 1000Mbit but this somehow does not work at all) to 10Mbit. Sometimes packets just get lost under load. The technician said that this most likely is due to a faulty Fritz!Box or some poor cabling in the building - which is somehow curious since the first Fritz!Box the technician installed was also faulty - he had to get a new one since it did not boot (maybe they are recycling old products?). The whole charade is deeply unsatisfactory... I switched to the Telekom DSL internet again - which works also through pfSense but with a bought modem - DrayTec Vigor 130 - absolutely no hassles there at all. The UnityMedia cable internet was only bought to temporarily have faster internet - we will get fibre internet in half a year or something. I am not sure how my experience relates to other customers but this is just.....
But again - a thousand thanks, especially to you @JeGr, for helping me through this process!

PS: I did the Telekom DSL configuration of pfSense from scratch again and saw that the WAN rule is indeed not needed. I only had an additional OpenVPN rule.
- do a
-
@paprikawuerzung said in (SOLVED) Problem with client connect through static IP cable internet:
It switches from 100Mbit on the LAN port (it should be 1000Mbit but this somehow does not work at all) to 10Mbit.
Urgh, that sounds a lot like bad hardware. Never saw that behavior on our boxes in homelab or customers even if they had faulty hardware in other places.
which is somehow curious since the first Fritz!Box the technician installed was also faulty
Hmm perhaps power or cabling issues that knocks them out? Perhaps some short circuit problem via bad coaxes or power lines?
The UnityMedia cable internet was only bought to temporarily have faster internet - we will get fibre internet in half a year or something. I am not sure how my experience relates to other customers but this is just.
Definetly on the lower end ;) Can't say I know a case that fits your problem description and as I'm working and living in an area that also has UM as ISP (one of the three states they cover in germany) we never had quite that problems. Of course much of their support depends on third party contractors doing HW service on site which can be top or flop.
PS: I did the Telekom DSL configuration of pfSense from scratch again and saw that the WAN rule is indeed not needed. I only had an additional OpenVPN rule.
Yeah, that's how it should run :) That's also why we are very curious, why the other box won't work that way...
Also as that whole case sounds like a "company" issue (or do you get fibre to the home?), if it stays a problem, you can think about the 2nd line of my sig ;)
-
@JeGr said in (SOLVED) Problem with client connect through static IP cable internet:
@paprikawuerzung said in (SOLVED) Problem with client connect through static IP cable internet:
It switches from 100Mbit on the LAN port (it should be 1000Mbit but this somehow does not work at all) to 10Mbit.
Urgh, that sounds a lot like bad hardware. Never saw that behavior on our boxes in homelab or customers even if they had faulty hardware in other places.
which is somehow curious since the first Fritz!Box the technician installed was also faulty
Hmm perhaps power or cabling issues that knocks them out? Perhaps some short circuit problem via bad coaxes or power lines?
The UnityMedia cable internet was only bought to temporarily have faster internet - we will get fibre internet in half a year or something. I am not sure how my experience relates to other customers but this is just.
Definetly on the lower end ;) Can't say I know a case that fits your problem description and as I'm working and living in an area that also has UM as ISP (one of the three states they cover in germany) we never had quite that problems. Of course much of their support depends on third party contractors doing HW service on site which can be top or flop.
PS: I did the Telekom DSL configuration of pfSense from scratch again and saw that the WAN rule is indeed not needed. I only had an additional OpenVPN rule.
Yeah, that's how it should run :) That's also why we are very curious, why the other box won't work that way...
Also as that whole case sounds like a "company" issue (or do you get fibre to the home?), if it stays a problem, you can think about the 2nd line of my sig ;)
So, the internet seems to be working. I installed OPNSense instead of pfSense and used another machine for the firewall.
With OPNSense, everything is working as intended and without any configuration hassle at all. True plug and play, no additional WAN rule, ... The initial reason I looked into OPNSense was that pfSense could not even be installed on the new machine - there were some cryptic "unregistered use of fpu in kernel" error on bootup - before even starting to install... I believe you if you say my experience is on the lower end.To all who posted here: thanks a lot for your help!

-
It's working now that you've changed everything? I'm wondering if the hardware was the problem all along.
-
@KOM Yeah, its working just fine without hassle. Would be very strange if the hardware would actually block traffic instead of pfSense OR pfSense would block certain traffic because of different hardware OR ... I would have tested it on the new hardware - but as I said before: pfSense somehow is not installable on this machine (I tried a lot of different BIOS settings, ...). I still guess it's a problem of pfSense since the changes I made to the default OPNSense installation are (for all that matters) exactly the same as the ones I tried with pfSense - no special rules, nothing.
-
Both pfSense and OPNsense are based on FreeBSD, 11.1 and 11.2 respectively. It doesn't make sense that you could install OPNsense based on 11.1 but not pfSense based on 11.2 on the same hardware.
Oh well, at least it's working for you.
-
@KOM said in (SOLVED) Problem with client connect through static IP cable internet:
Both pfSense and OPNsense are based on FreeBSD, 11.1 and 11.2 respectively. It doesn't make sense that you could install OPNsense based on 11.1 but not pfSense based on 11.2 on the same hardware.
Oh well, at least it's working for you.
11.1 and 11.2 respectively.
A lot of things did not make sense in this whole process
 Maybe it was the hardware, maybe it was pfSense. Same to me if I am honest since OPNSense with the new machine installed/worked just fine and from the functionality they seem to overlap quite heavily. Works for me.
Maybe it was the hardware, maybe it was pfSense. Same to me if I am honest since OPNSense with the new machine installed/worked just fine and from the functionality they seem to overlap quite heavily. Works for me.