Specifying a gateway in a firewall rule breaks routing
-
I'm trying to configuring policy-based routing over a VPN connection.
I've configured the OpenVPN client and it's working.
I've configured the Outbound NAT rules and those appear to be working.
I've assigned the OpenVPN Client connection to an interface.
I've created Firewall Rules that sends an Alias of devices over the OpenVPN gateway
I've created a rule above that, that excludes traffic to local IPs from being routed to the VPNHere are my rules for the WIFI segment
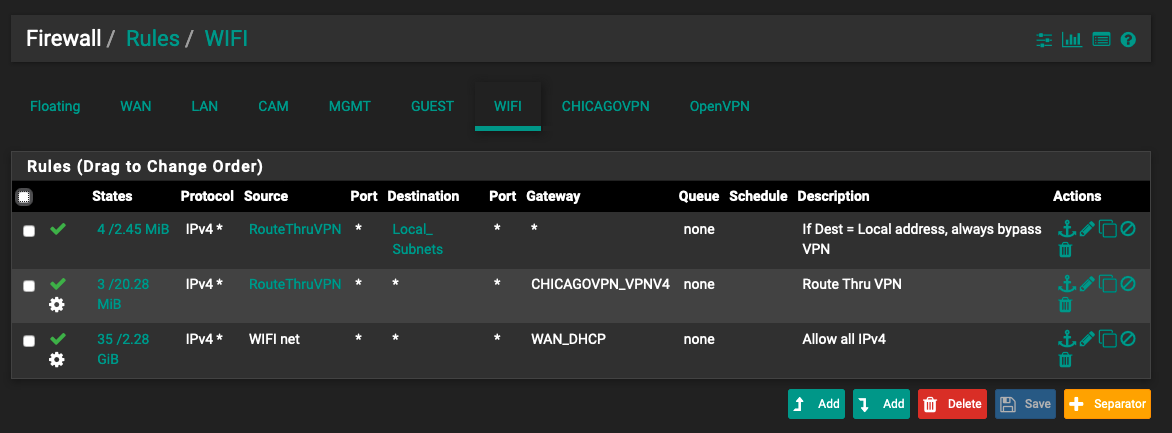
Notice the Gateway specified in the last rule. Without that, EVERYTHING goes through the VPN. With that, traffic from WIFI does not go through the VPN. However it breaks connectivity to all of the other segments. My laptop for example is not in the Alias of devices intended to go over the VPN. With the gateway as specified, I cannot ping or otherwise connect to any of the devices in the LAN segment and vise versa.
If I remove the WAN_DHCP and replace it with * (which should still default to WAN_DHCP), connectivity to other segments is restored but all of my internet traffic is now piped over the VPN.
I'm stuck. Help.
-
I guess the VPN server pushes the default route to you. If you only want to direct particular traffic over the VPN, this should be avoided.
To do so, go to the client settings and check **Don‘t pull routes **.
Then you can set the gateway in your Wifi rule to any.To avoid DNS leak, you will have to direct requests from ”routeThruVPN“ to an external server over the VPN additionally.
-
Thanks for your response. You know, sometimes you need to be told something three times before it sinks in. Every time I've seen this recommendation, I've read the settings as "Pull Routes" not as "Don't Pull Routes". I thought having the box unchecked was accomplishing this. After more careful examination I see that I had it backward. I checked this box and voila! It's now working as expected. Thank you!
Help me understand the DNS leak concern and how to avoid it?